
Cowpatty: disgusting name, serious network tool. Authored by Joshua Wright, Cowpatty provides hackers, attackers, and network administrators with a way to implement offline dictionary-based attacks against wireless system. It allows its users to break WPA and WPA2 systems by taking advantage of authentication based on the PSK (PreShared Key) model. If you don’t understand these terms, don’t worry; we’ll shortly dig into the nuts and bolts of these algorithms.
Prerequisites
Unfortuantely, Cowpatty is a little difficult to use – especially if you’re new to Linux. It is a command-line utility, and as such, you should have a certain degree of comfortability and experience working from the BASH shell. If you haven’t ever worked from the BASH shell before, but you’re just rearin’ to get started, proceed with caution. We will go through the step-by-step usage instructions for this tool; however, you’ll first need a Linux system on your computer. Though we won’t get into the installation methods of the Kali software, understand that there are three options to installing Kali on your hardware.
First, you can opt to use VMWare to run a virtual machine of the Kali code. Secondly, you can even create a bootable USB version of Kali, though you may need to change the boot order of system devices in your BIOS. Lastly, you can opt to either wipe out your old operating system (to be replaced by Kali) or shrink a partition so that you have the ability to dual boot. At any rate, Kali is rather small and lightweight, so it won’t take massive amounts of disk space.
If you didn’t include the wireless penetration testing packages during the installation of your Kali system, you’ll need to download the source code from their website, compile it, and install the program. But if it’s a fresh system and you’re a new user, it’s highly advisable to reinstall Kali with the appropriate packages for the sake of ease and simplicity.
Also, you’re going to need a wireless interface that is capable of being run in monitor mode. If you opted to run Kali as a virtual machine with VMWare, your only option is to use a wireless USB dongle. For users that use a live boot USB or actually installed the software, you can use the wireless card in your system with only a few caveats. Not all wireless cards and chipsets are capable of running in monitor mode, so just look up your wireless hardware on your system and run a quick Google search. Again, if your hardware lacks this capability, just buy a cheap wireless USB device.
In summary, before proceeding, a penetration testing novitiate will need the following:
- A computer running the Kali operating system
- The Cowpatty software (which is packaged with Kali)
- The source code if you didn’t install the wireless tools package (not recommended)
- A wireless device that you own and control to conduct the testing, as well as other wireless clients on the networks
- A wireless interface that is capable of running in monitor mode
Understanding PSK’s
So, what the heck is a PSK, you ask? Well, a PSK is a Pre-Shared Key, and they are frequently used in security algorithms such as WEP, WPA, and WPA2. This is the key that is manually entered to gain access to the network, and after it has been entered, the security algorithm (WEP or WPA) will autmatically take over and use the key to encrypt and secure data communications.
The idea is to bar unauthorized users and eavesdroppers from seeing what data is being sent between two wireless hosts. You see, there’s a massive problem that exists with wireless technologies that doesn’t exist with Ethernet. Wired communications can (for the most part) only be read by the hosts on each end of the cable. But wireless technologies broadcast their data through the air, and anyone within a certain range has the ability to capture the wireless radio signals.
I don’t think anyone wants to broadcast their personal data through the air in an unencrypted format, especially in a public setting like an Internet café or airport. Hence, the need for wireless encryption algorithms was born. PSKs are only one method of securing wireless communications, though they are one of the most often employed techniques. The problem is that there are some security flaws in the underlying algorithm that make it possible for an attacker to crack the key if they have the right tools. And that’s where cowpatty comes into play. Before we start running commands to crack a wireless security key, we need to review the various options and flags.
Finding the Cowpatty Help Screen
The very first thing you’re going to need to do is to actually located the Cowpatty software. As mentioned previously, it is included in the Kali packages. However, instead of being placed in the obvious /pentest/wireless folder, where you would expect to find it, it has been placed in the /usr/local/bin folder. Go ahead and browse to this directory with the change directory command as follows:
- cd /usr/local/bin
This directory needs to be in your PATH environment variable in order for you to run the program. So, after you have changed your current working directory to /usr/local/bin (you can see this by using the pwd command), you should be able to run the software. Let’s start by keeping things simple and pulling up the help screen. From the aforementioned directory, issue the following command:
- cowpatty
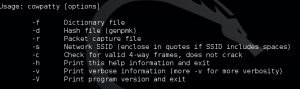
This should display a screen that shows all of the different flags and options for the command syntax as follows:
- -f Dictionary file: this option specifies the file and directory location of the dictionary you want to use in a password attack.
- -d Hash file: used to indicate the file and directory location of a hash file, which can greatly decrease the length of time it takes to crack a wireless system.
- -r Packet capture file: this specifies the file that stores all of the stored packets after a capture has been run. If a cracking attempt fails, you can save the collected packets and later try different dictionaries against the set of captured packets.
- -s Network SSID: specifies the Service Set Identifier (e.g. the wireless network’s name). Note that if it includes spaces, you must enclose the characters in quotations.
- -h Help: prints the help screen, but then exits the cowpatty prompt.
- -v Verbose: runs the command in verbose mode, which will display all of the background processes and information in the terminal window.
- -V Version: note that the flag is a capital V, and it will simply display the version information for your cowpatty software.
 Next, take a moment to look at your command prompt. To verify that you are indeed within the cowpatty software, your prompt should end in cowpatty#. However, before we enter any more cowpatty commands, we’ve got a bit of legwork to do first. You see, cowpatty really only serves as a method of cracking the wireless security protocols.
Next, take a moment to look at your command prompt. To verify that you are indeed within the cowpatty software, your prompt should end in cowpatty#. However, before we enter any more cowpatty commands, we’ve got a bit of legwork to do first. You see, cowpatty really only serves as a method of cracking the wireless security protocols.
That is to say, it doesn’t really have any tools that help us gather the required data. Instead, we first need to capture packets (as we’ll discuss shortly), and then we’ll just plug all of the data into cowpatty and let it do all the heavy lifting. Basically, cowpatty needs three separate pieces of information to successfully crack a wireless key. First, it’s going to need a dictionary (sometimes called a word list). In addition, it’s going to need a file that contains password hashes. Lastly, it’s going to need to know the SSID of the target AP.
Gathering Packets
So, as stated previously, you’re going to need to put your wireless interface in monitor mode to start capturing packets. Unfortunately, not every wireless chipset and network interface is capable. We’ll be using airmon-ng to capture wireless packets, and they have a great page on their site that guides users through the details of determining whether or not their wireless card is capable of running in monitor mode.
Assuming your interface is capable, you’re going to need to start by placing the interface in monitor mode. The command will use the name of your wireless interface as one of its parameters, so it’s best to double check this information with the ifconfig command. Users who have multiple wireless cards or are using a external USB wireless interface may notice that their wireless hardware is labeled wlan1. However, the vast majority of users will note that the name of their interface is wlan0. Once you know the name of your interface, issue the following command:
- airmon-ng start wlan0
This should look very similar to the tutorial we did for cracking wireless with airmon-ng. And the first steps are identical, because the first step is almost always capturing packets and wireless frames. After the command has been entered, you should notice that the terminal fills up with a myriad of information regarding the details of every wireless network signal in range. We are going to need to pull some data from this output and use them as parameters in the next command.
Next, we are going to create a capture file, which is where the password hash will be saved when we successfully capture the 4-way handshake. We will explain the options shortly, but the command syntax is as follows:
- airodump-ng –bssid [BSSID] -c [CHANNEL] -w cowpatty mon0
There are three pieces of this command that I want you to focus on more closely. First, the BSSID parameter needs the hexadecimal address (this is a layer 2 address) of a valid wireless network. Simply look through the previous command’s output to find the BSSID of a target network you are trying to crack (which should be your own wireless router!). Second, find the channel that your target BSSID is transmitting on, as indicated in the CH column. Channels 1, 6, and 11 are the most common, but it could be any number in between.
Lastly, I want you to take note of the mon0 syntax at the very end of the command. The preceding command’s output should have identified your monitoring interface with a unique name. Most often, it will assign the name of mon0. However, this can change if you’ve made a configuration error or you have enabled an additional interface in monitor mode. Just make sure that you choose the appropriate monitoring interface. Lastly, name the dump whatever your wish, just remember where you stored it and what you named it, since we will be using this file with the next command.
Capturing the Handshake
When that’s all said and done, our next step is to actually capture the handshake. This can be a bit tricky, because in order for a handshake to present itself, we’re going to need another wireless client to connect to the wireless network. In a real world scenario, this could take some time. Fortunately, since you’re doing this within the comfort of your own home, all you need to do is connect one of your other devices to your wireless router. Airdump-ng will display the successful capture of a handshake in the upper right hand corner of the terminal output upon completion.
Cracking the Hash
Not it’s time to leverage cowpatty to actually crack the hash. To do so, we’re going to feed cowpatty the hash as well as the wordlist. Use the following command:
- cowpatty -f /pentest/passwords/wordlists/[WORDLIST.LST] -r [PACKET_CAPTURE_FILE.CAP] -s [SSID]
There are three notable parameters here that need to be addressed. First off, note that the -f parameter needs to be supplied with the directory and name of the wordlist you are using. Sometimes a wordlist may not successfully crack a wireless system, but there are plenty of different wordlists that can be found and downloaded with a quick Google search.
Secondly, note that you need to plug in the directory and name of your packet capture file for the -r command. And lastly, note that the -s command takes input as a character representation of the SSID (e.g. the wireless networks actual name), and not the BSSID you entered before. Cowpatty is then going to create a hash computation for us and spit out a lot of key data. Be forewarned: it can take quite a long time to complete.
Cracking the Password
And now, at long last, we can finally crack the password. Use the following command:
- cowpatty -d [HASH_FILE] -r [PACKET_CAPTURE_FILE] -s [SSID]
Voilà! You have now just successfully hacked into your own wireless router.
Final Thoughts
It cannot be stressed enough: trying to hack into other wireless systems that you don’t control for nefarious purposes is not only illegal, it’s downright unethical. Remember not to try this on your neighbor’s Wi-Fi or a corporate network. Though you neighbor may not know what’s going on, you might land yourself in some hot water if you get caught trying to break into a business’s Wi-Fi (though their security department should have ways of mitigating these kinds of attacks and threats). Do unto others’ Wi-Fi networks as you would have them do to your Wi-Fi networks. And as always, happy hacking and penetration testing with cowpatty!

Lokesh Singh says
Awesome tutorial.