Zeebsploit is a web application penetration testing tool used for information gathering, scanning, and exploiting vulnerabilities. Zeebsploit can perform the following information gathering tasks.
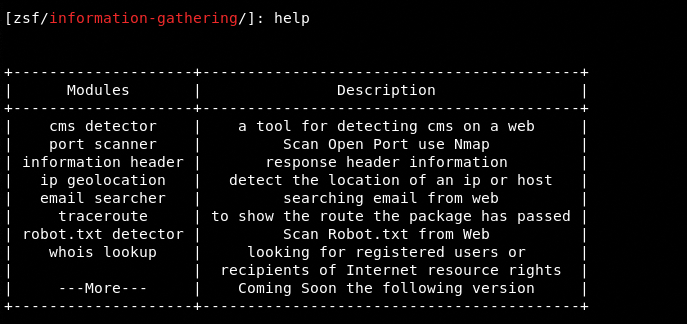
- Content Management Information (CMS) identification
- Port scanning
- Header information
- IP geolocation
- Email finding
- Traceroute information
- WHOIS record
- txt record
Zeebsploit can find the following web related vulnerabilities.
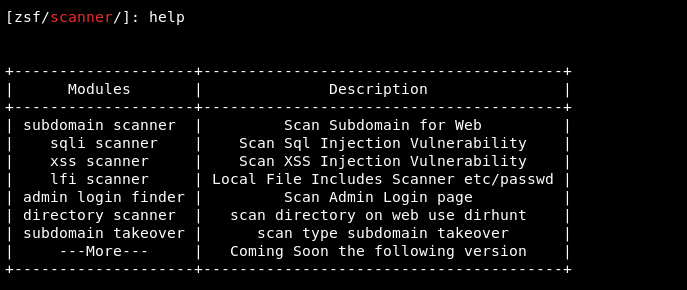
- Sub-domains
- Sub-domain takeover vulnerabilities
- SQLi vulnerabilities
- Cross Site Scripting (XSS)
- Directory scanning
- Admin pages
- Local File Inclusion (LFI) vulnerabilities
Similarly, Zeebsploit can take over WordPress, Joomla, and Drupal CMS through following exploits.
- WordPress content injection (currently exploits only version 4.7 and 4.7.1)
- WordPress file upload through Revsilder, Learndash, and Showbiz plugins
- Joomla file upload
- Joomla auto shell upload
- Joomla auto get config through component manager
- Drupal remote command execution
Zeebsploit Installation
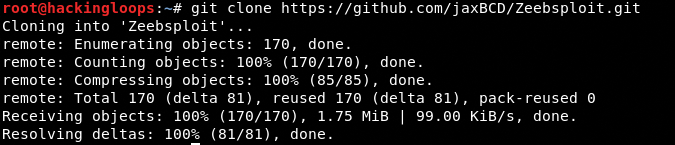
To install Zeebsploit, clone the tool using the following command.
git clone https://github.com/jaxBCD/Zeebsploit.git
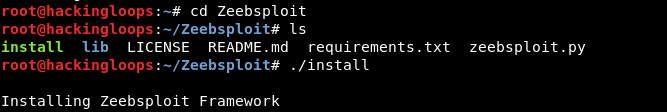
Navigate to the tool’s directory and complete the installation process by following these commands.
cd Zeebsploit chmod +x install ./install
The above commands automatically install all the packages required by Zeebsploit.
How Zeebsploit Works
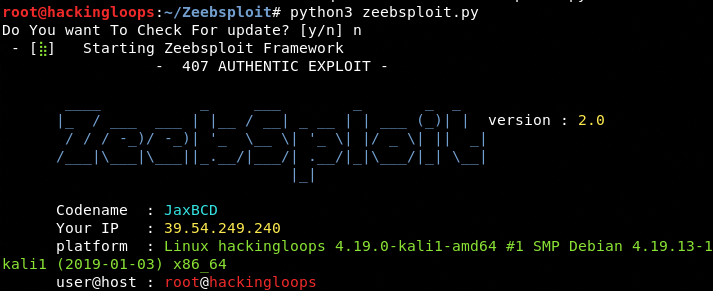
Zeebsploit can be set into action by running the following command.
python3 zeebsploit.py
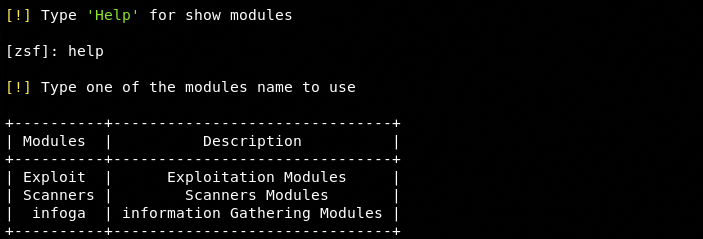
The tool has built-in modules to perform the aforementioned tasks. These modules are divided into three categories that can be seen by typing help in the command line.
As we can see in the above screenshot, there are three categories namely exploit, scanner, and infoga. Select the desired category by typing its name in the terminal. Following is a brief description of each category containing the respective modules.
Information Gathering Modules
The information gathering modules can be set into action by typing the following command.
infoga
The help command shows all the modules available in this category.
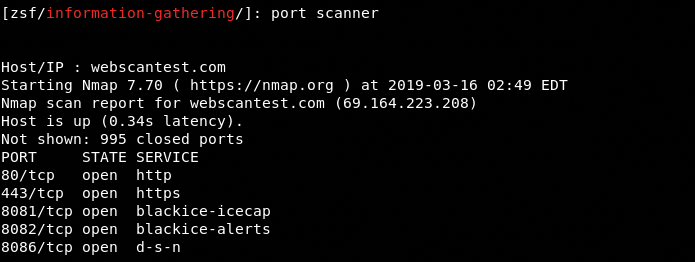
The available modules can be selected by typing their names in the command line. For example, we can select the port scanner module by typing the same in the command line.
port scanner
The tool asks for the host /IP address to start scanning the target. The ports information gathered by the module can be seen in the following screenshot. The tool scans the open TCP ports and shows the running services.
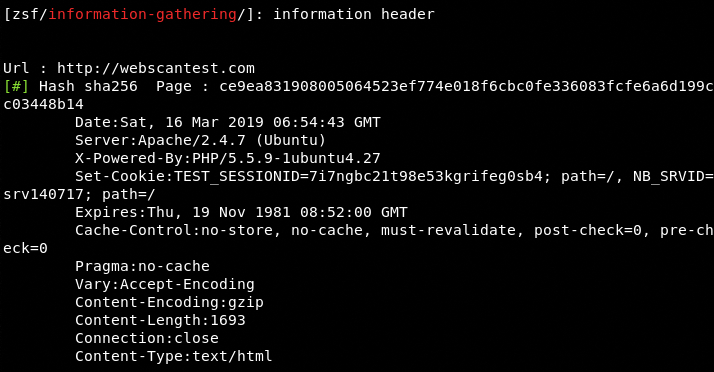
Similarly, we can get the header information by using the information header module. The header information gathered by the tool can be seen in the following screenshot.
Scanner Modules
The following command loads Zeebsploit in scanner mode. The help command shows all the modules that can be used to scan the vulnerabilities mentioned in the description section of the following screenshot.
scanner
The process of using the scanner modules is similar to the information gathering modules. Type the desired module name and target host url or IP address to run the scanner. For example, we can run the cross site scripting module in the following way.
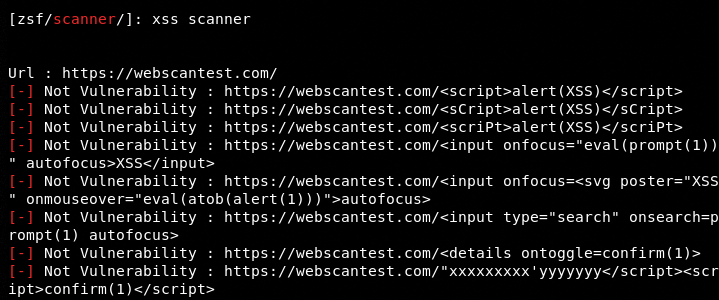
xss scanner
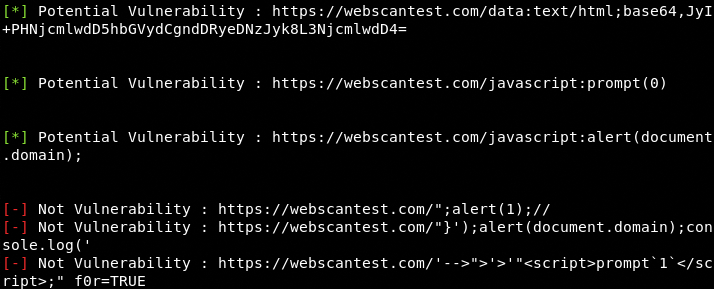
Once the target host/IP is provided, the tool scans all the links associated with the target host to find out the xss vulnerabilities.
The following screenshot shows the vulnerable links found on a test host by the tool.
Exploit Modules
The following command is used for the exploit modules.
exploit
The available exploit modules can be seen by typing the help command.
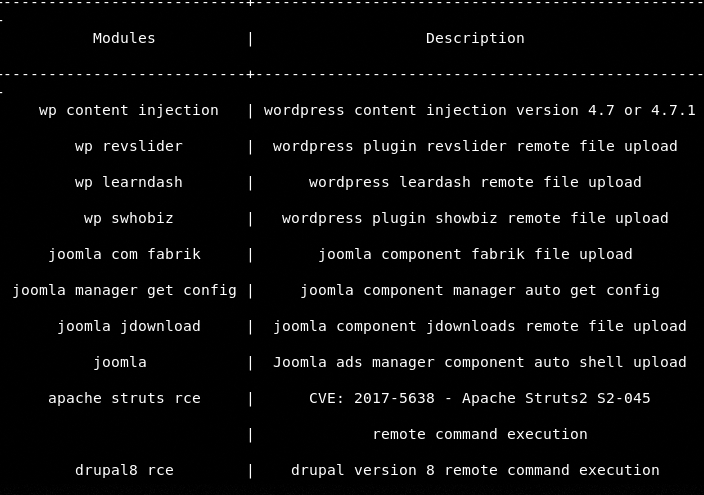
The process of running the exploit modules is similar to the information gathering and scanning modules.
Conclusion
Zeebsploit is a decent penetration testing tool that can perform most of the tasks required by red teamers. The current scope of scanning and exploitation is limited as the tool does not support all the major vulnerabilities. The tool can become very handy with the addition of more scanning and exploitation modules.