XSRFProbe toolkit can find and exploit Cross Site Request Forgery (CSRF) vulnerabilities in web applications. The toolkit can scan the following types of CSRF vulnerabilities.
- Referrer based requests
- Origin based requests
- Cross-site cookie validation check
- Session cookies persistence check
- POST-Based Request Forgery Detection
Apart from the above listed CSRF vulnerabilities, XSRFProbe can also detect
- Anti-CSRF tokens in POST queries
- Tokens strength
- Tokens encoding
- Randomness of anti-CSRF tokens
XSRFProbe can also exploit the discovered CSRF vulnerabilities by generating exploitable Proof of Concepts (PoCs).
XSRFProble Installation
XSRFProbe is a Python3 toolkit that is supported by all major OS (Linux, Window, Mac). The toolkit requires requests, bs4, stringdist, tld, and yattag packages to operate. The requests package is required for generating HTTP requests; bs4 is used for HTML parsing; stringdist is a fuzzy matching library; tld is required for domains extraction and yattag for PoC generation.
XSRFProbe can be cloned from Github using the following command.
git clone https://github.com/0xinfection/XSRFProbe.git
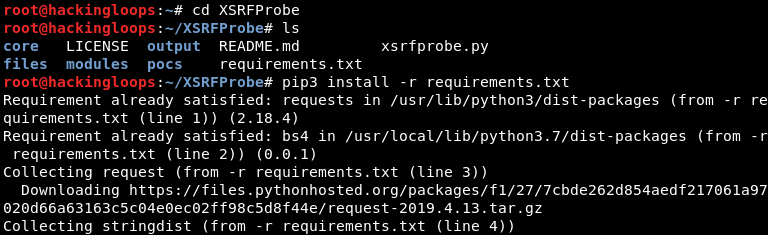
Navigate to the toolkit’s directory to install the dependencies using the following commands.
cd XSRFProbe pip3 install -r requirements.txt
How XSRFProbe Works
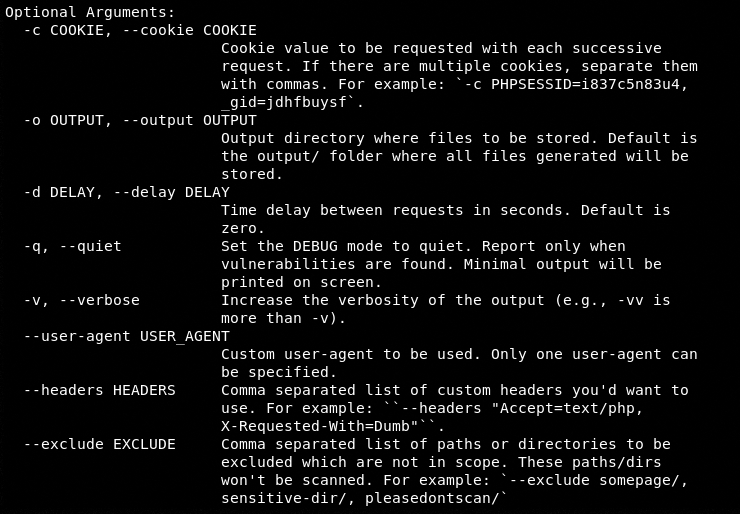
Running the following command showcases all the mandatory and optional arguments of XSRFProbe.
python3 xsrfprobe.py
XSRFProbe allows scanning of CSRF vulnerabilities in all or specific endpoint in target web application. The following command crawls all the endpoints in a target web application and tests the possibility of CSRF attacks.
python3 xsrfprobe.py -u <target website> --crawl
Crawling whole websites to scan all end points requires considerable amount of time. We can also scan a specific endpoint (url) in the target web application using the following command.
python3 xsrfprobe.py -u <target website>
Let’s assume http://webscantest.com/csrf/csrfpost.php is the desired endpoint of target web application. We can initiate the single endpoint CSRF query as follows.
python3 xsrfprobe.py –u http://webscantest.com/csrf/csrfpost.php
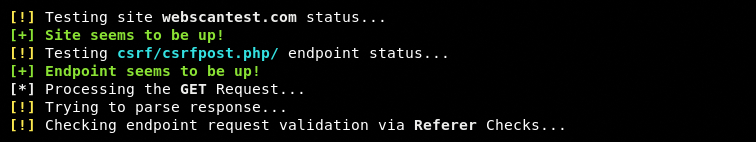
XSRFProbe first validates the status of the target domain and the specified endpoint before moving on to the next steps.
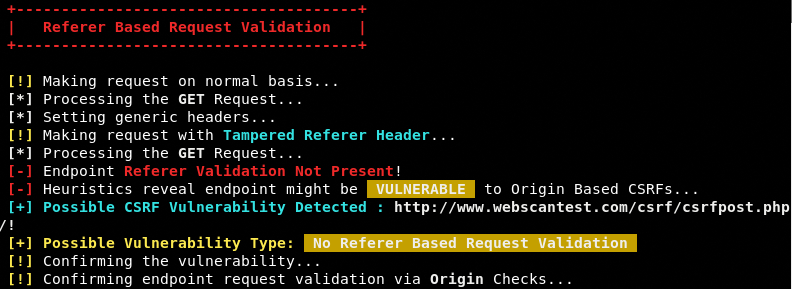
After validating the target domain and endpoint, XSRF initiates the GET and POST processes to run all the CSRF validation tests including Referer, Origin, Cookies, Token, and POST requests. All the tests are performed automatically. The toolkit starts with the Referer based request validation. The requests made during this test can be seen in the following screenshot.
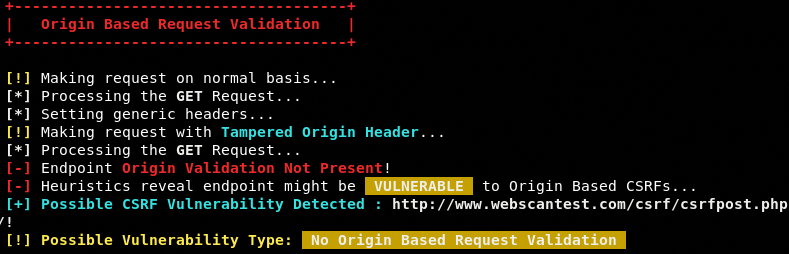
If the target is not vulnerable to Referer based CSRF attack, the toolkit moves on to the next scan, which is Origin based request validation test.
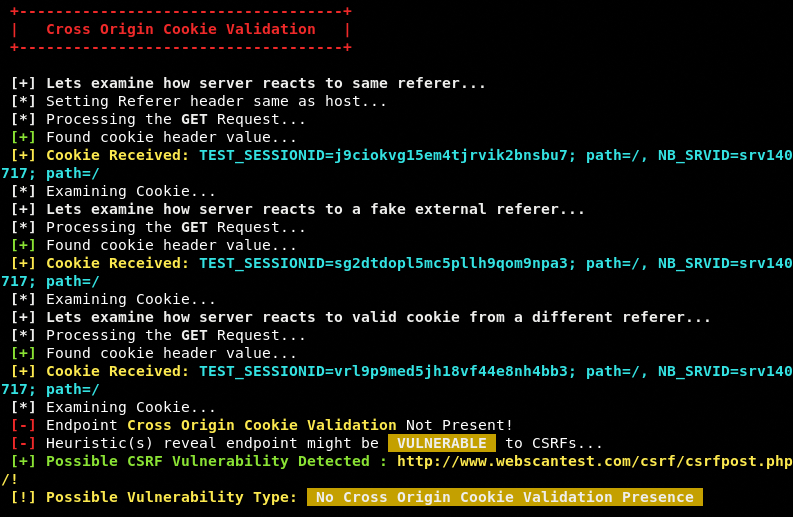
The same approach is applied for Cookies (Cross Origin and Persistence) validation.
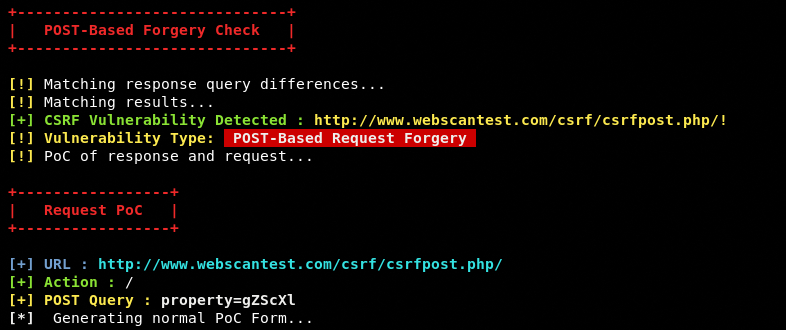
After completing the GET techniques, XSRFProbe initiates the POST queries to find out the possible CSRF vulnerabilities. If the target end point is vulnerable to POST based forgery attack, the results are displayed on the screen in the following format.
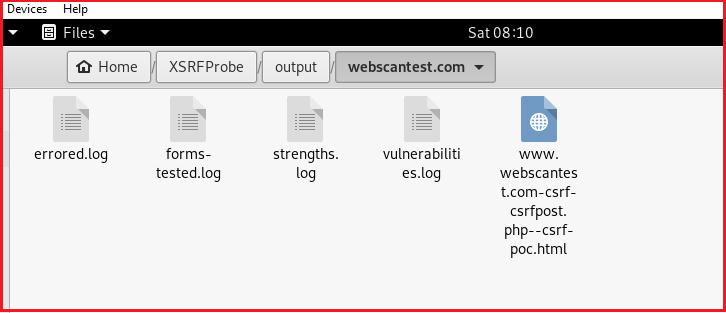
The toolkit also generates the PoCs to exploit the discovered CSRF vulnerability. The log files created during the scanning process are automatically stored to the default output folder inside the toolkit directory. We can also specify a different storage path through -o or –-output argument.
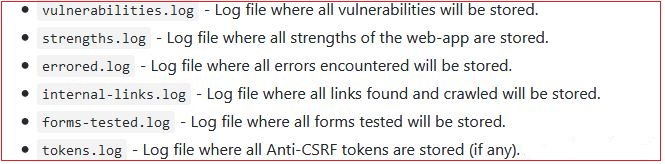
The output folder may contain different types of log files as shown in the following screenshot.
Summary
XSRFProble not only helps in detecting different types of CSRF attack but it can also provide the exploitable Proof of Concept (PoC) to help understand the malicious codes that can be used to target the web applications.