Reconnaissance is an important phase in penetration testing. The gathered information not only helps in unfolding vulnerabilities in target hosts but also sets a direction for the rest of the penetration testing cycle. This tutorial shows two quick ways of automating web reconnaissance with greater accuracy.
FinalRecon is an open-source intelligence tool used for web-based reconnaissance projects. The tool can automatically detect and collect useful information about target domains. The tool has a modular structure with the following expandable reconnaissance features.
- WHOIS Information
- Header Information
- SSL Certificate Record
- DNS Enumeration
- Subdomains listing
- Trace-route information
- Directory Search
- Ports scanning
- Web crawling
Each reconnaissance feature produces a handful of information that can help penetration testers in identifying the potential injection points in target hosts.
How to Install FinalRecon
FinalRecon can be downloaded either by cloning the source files from Github or making a Docker pull request. The following Docker commands pull the package and take care of all the dependencies.
docker pull thewhiteh4t/finalrecon docker run -it --entrypoint /bin/sh thewhiteh4t/finalrecon
FinalRecon can be cloned from Github using the following command.
git clone https://github.com/thewhiteh4t/FinalRecon.git
The dependencies can be installed by running the following commands.
cd FinalRecon python3 –m pip install –r requirements.txt
How FinalRecon Works
The following command presents the basic syntax to initiate the reconnaissance process.
python3 finalrecon.py <optional arguments> <target URL>
The essential command parameters including the optional arguments can be explored through the following help command.
python3 finalrecon.py -h
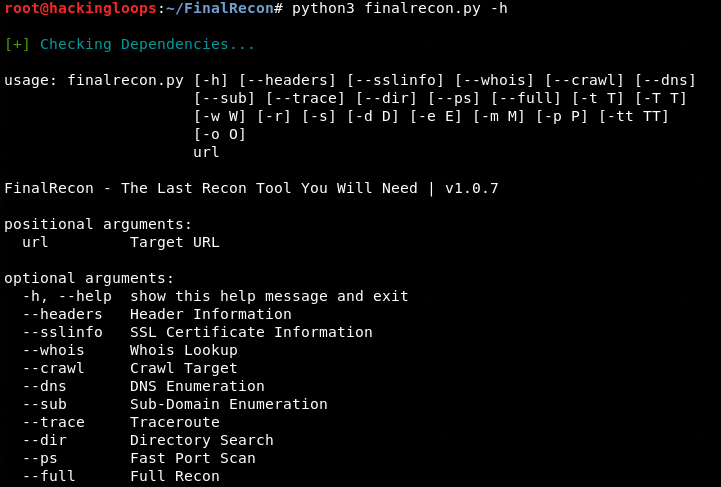
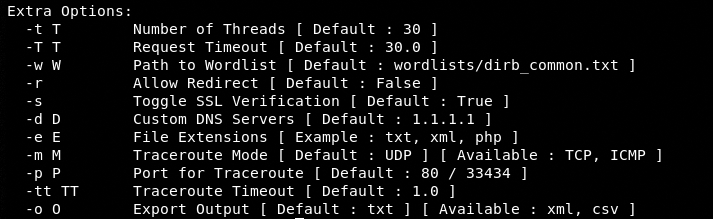
The help command also displays the following additional options to customize the scanning process.
Let’s explore the reconnaissance capabilities of FinalRecon by executing the aforementioned optional arguments against a test web application.
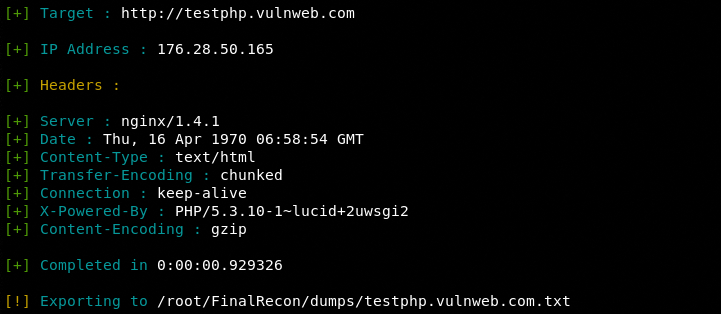
Header Information
python3 finalrecon.py --headers http://testphp.vulnweb.com
The tool managed to get valuable header records, such as server information, scripting language, and content-encoding technique.
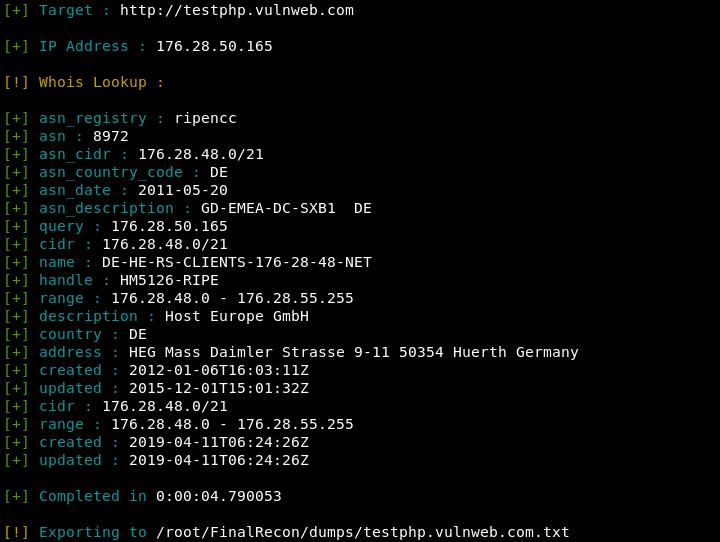
WHOIS Record
python3 finalrecon.py --whois http://testphp.vulnweb.com
The screenshot shows an important geographical and Classless Inter-Domain Routing (CIDR) record of the target host. The CIDR information is important in understanding the IP allocation and IP routing of the target host’s network.
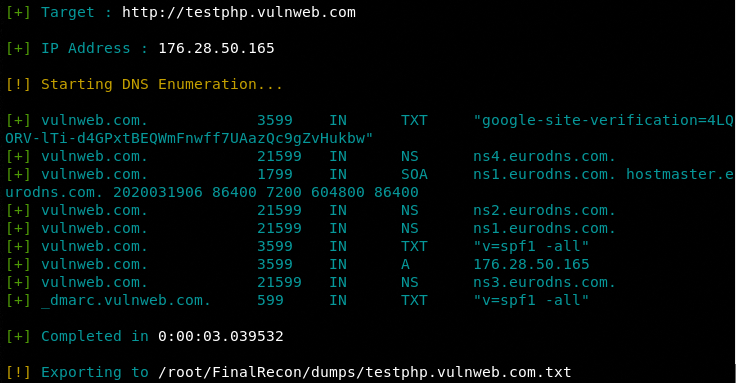
DNS Record
python3 finalrecon.py --dns http://testphp.vulnweb.com
The primary feature of the Domain Name System (DNS) is usability instead of security. DNS converts the human-friendly domain names into IP addresses through DNS resolvers. DNS information can help attackers in launching a number of DNS-related attacks, such as cache poisoning, DNS hijacking, DNS tunneling, and Denial of Service (DoS) attacks.
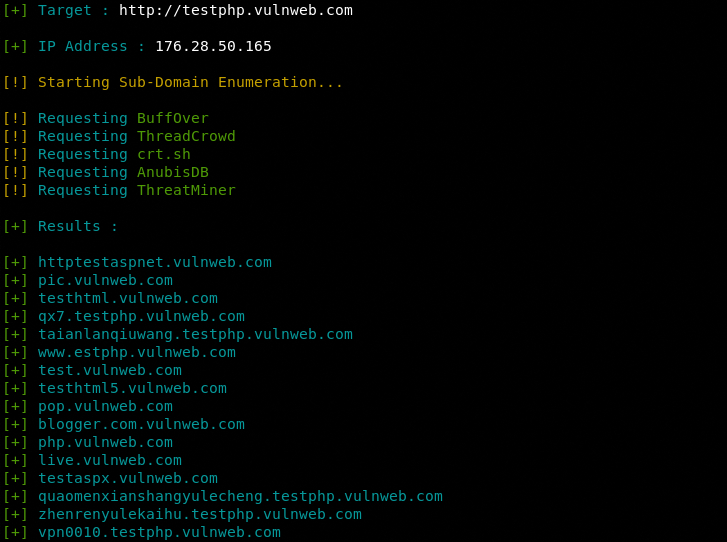
Sub-domain Enumeration
python3 finalrecon.py --sub http://testphp.vulnweb.com
FinalRecon uses the following data resources to find the subdomains associated with the target domain.
- Buff0ver
- Threadcrowd
- AnubisDB
- ThreatMiner
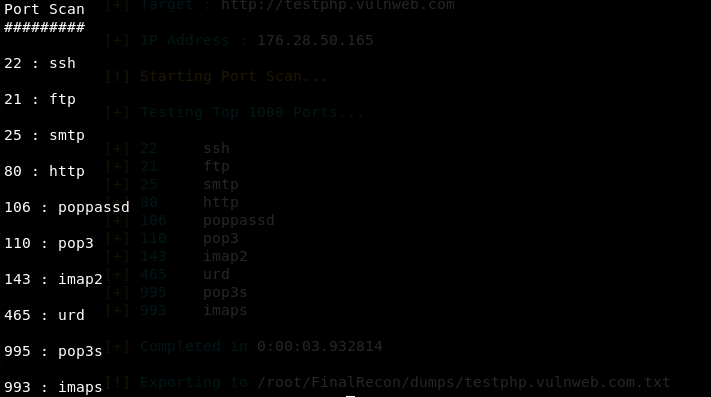
Port Scan
python3 finalrecon.py --ps http://testphp.vulnweb.com
The port scanning module scans the top 1000 ports and presents the results in the following format.
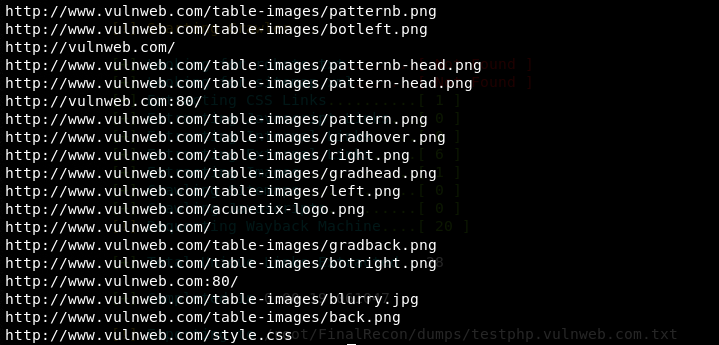
Web Crawler
python3 finalrecon.py --crawl http://testphp.vulnweb.com
The web crawling feature of FinalRecon is not as impressive as the other information gathering features. If the target host is a subdomain, the tool crawl links for the parent domain instead of the target subdomain.
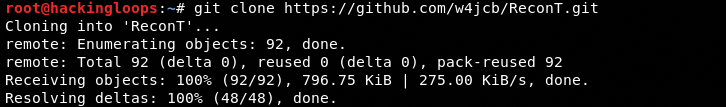
ReconT
The ReconT is another Python tool that can perform similar tasks like FinalRecon. Web Application Firewall (WAF) and banner grabbing are two additional features of the ReconT tool.
ReconT Installation
The tool can be downloaded using the following command.
git clone https://github.com/w4jcb/ReconT
The tool’s requirements can be fulfilled by executing the requirments.txt file from the tool’s directory.
cd ReconT python3 –m pip install –r requirements.txt
How the ReconT Works
Unlike FinalRecon, the ReconT runs all the reconnaissance tests through the following single command.
python3 reconT.py <target url>
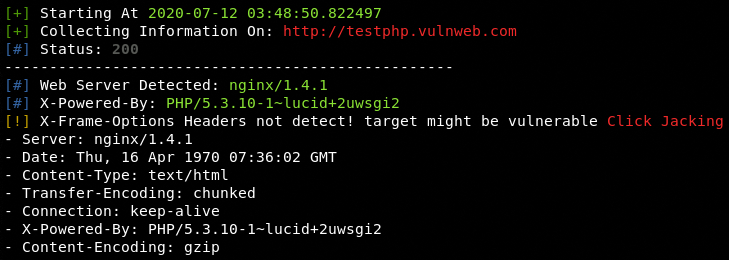
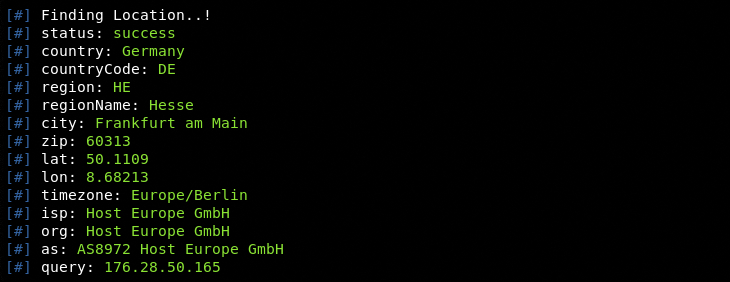
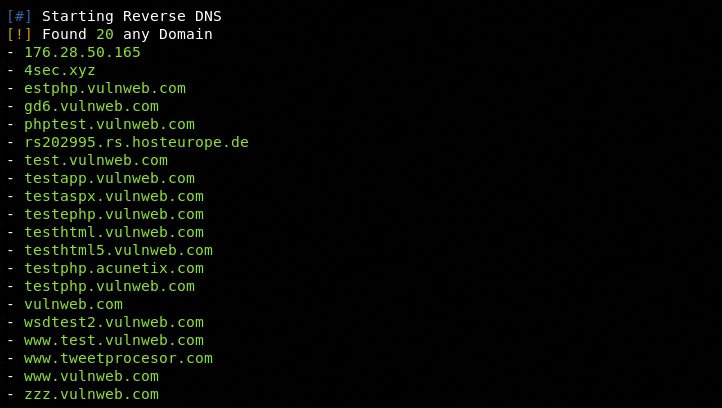
The following screenshots show the reconnaissance results from the ReconT python tool.
Headers Information
WHOIS Record
Subdomains Enumeration
Ports Information
Conclusion
FinalRecon and ReconT tools can automate the reconnaissance process to reduce the time spent on information gathering tasks. Both tools require very little input from users to fetch a handful of information about target hosts through publically available resources.