The Kn0ck is an open-source penetration testing utility that can automate the process of information gathering, vulnerabilities scanning, and exploitation of networks and web applications. It renders the services of a number of third-party tools including Metasploit, NMap, Nikto, Arachni, and WPScan to perform the following information gathering and vulnerabilities scanning/enumeration functions.
- Do basic reconnaissance
- Launch Google hacking queries
- Enumerate open ports
- Check Sub-domain Bruteforce and hijacking possibilities
- DNS and zone transfer information gathering
- Enumerate Network File System (NFS) shares
- Check common web vulnerabilities
- Assess anonymous LDAP access check
- Enumerate SSL/TLS ciphers, protocols and associated vulnerabilities
- Check SNMP community strings, users, and services
- List SMB (users and shares) and null sessions (If you want step-by-step use this SMB Enumeration.)
- Check open X11 servers
- Capture screenshot of target hosts
Besides the aforementioned scanning features, the Kn0ck tool can test different network and web technologies to assess multiple Common Vulnerabilities and Exploits (CVE’s). The following are some examples of CVE’s and Remote Code Execution (RCE) vulnerabilities that can be traced using the Kn0ck tool.
- Apache Struts CVE-2018-11776
- Apache Tomcat CVE-2017-12617
- HeartBleed OpenSSL Detection CVE-2014-0160
- MS Windows SMB RCE MS08-067
- PHPMyAdmin Backdoor RCE
- JBoss Java De-Serialization RCEs
- Anonymous FTP Access
- Shellshock Bash RCE CVE-2014-6271
The scan results are automatically stored in different formats including Text, PDF, and HTML.
HOW TO INSTALL KN0CK TOOL
Installing the Kn0ck tool is a fairly simple process. The first step is to clone the source code from Github using the following command.
git clone https://github.com/telnet22/Kn0ck.git
The next step is to change the permission rules for the shell files.
cd Kn0ck chmod +x *.sh
The final step is to run the install.sh file using the following command.
./install.sh
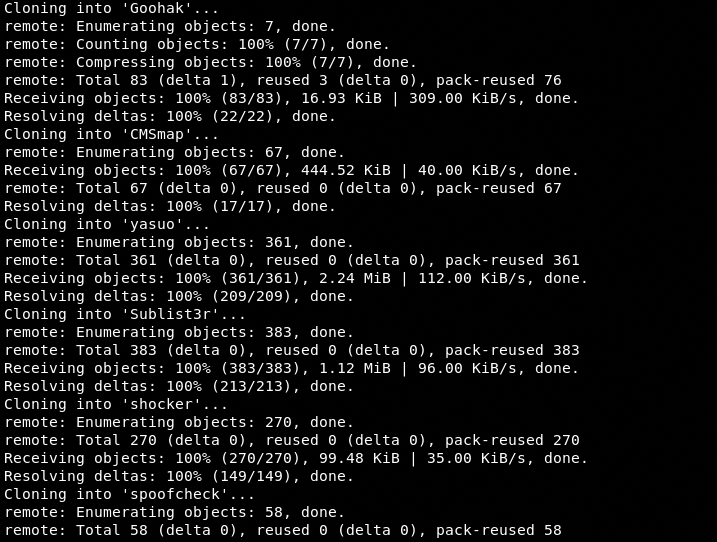
The installation process may take some time to automatically install all the dependencies including the third-party tools that are called during the scanning process. The following screenshot shows some example tools that are automatically cloned and locally installed by the Kn0ck tool.
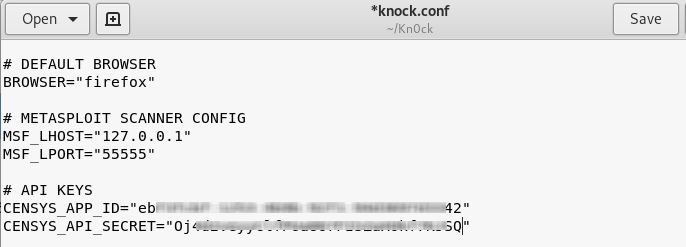
After the successful installation of the tool, we need to edit the kn0ck.conf file in the main directory. The file requires CENSYS ID and API keys to perform different scanning tests. Open the kn0ck.conf file and add the CENSYS API secrets as shown in the following screenshot.
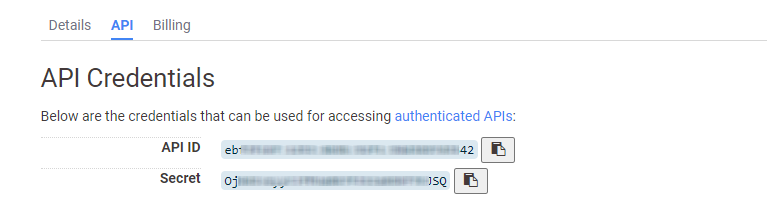
The Censys keys can be obtained from the API section in the Censys.io application.
PENTESTING USING KN0CK TOOL
After the tool is successfully installed, it can be launched from the terminal using the following command.
kn0ck <mandatory and optional parameters>
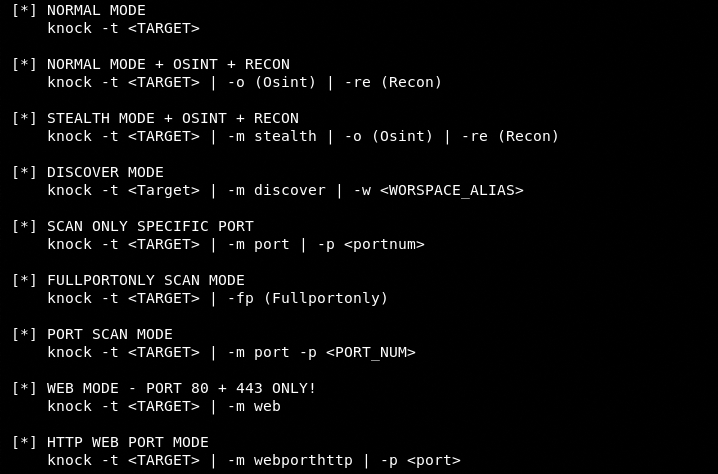
The following help command lists all the important parameters and syntax to run the Kn0ck tool in different modes.
kn0ck --help
The current Kn0ck tool version supports the following eight different modes for scanning and enumeration purpose.
- Normal ( for normal/basic scanning)
- Stealth (for quick and non-intrusive scanning)
- DISCOVER (for network scanning)
- PORT (for specific port scanning)
- FULLPORTONLY (for all ports scanning)
- WEB (for fully automated web scanning using port 80 and 443 only)
- WEBPORTHTTP (for full HTTP web scanning)
- WEBPORTHTTPS (for full HTTPS web scanning)
NORMAL MODE EXAMPLE
As we can see in the help menu, the normal or basic mode scan can be performed using the following simple syntax.
kn0ck –t <target host>
The above command performs all the scanning and enumeration tasks against the target host. To analyze the working and performance of the tool, we run the basic scan test against the following sample website.
kn0ck –t testphp.vulnweb.com
The tool performs a pre-test check to confirm the Kn0ck configuration (kn0ck.conf) and output directory (loot folder).
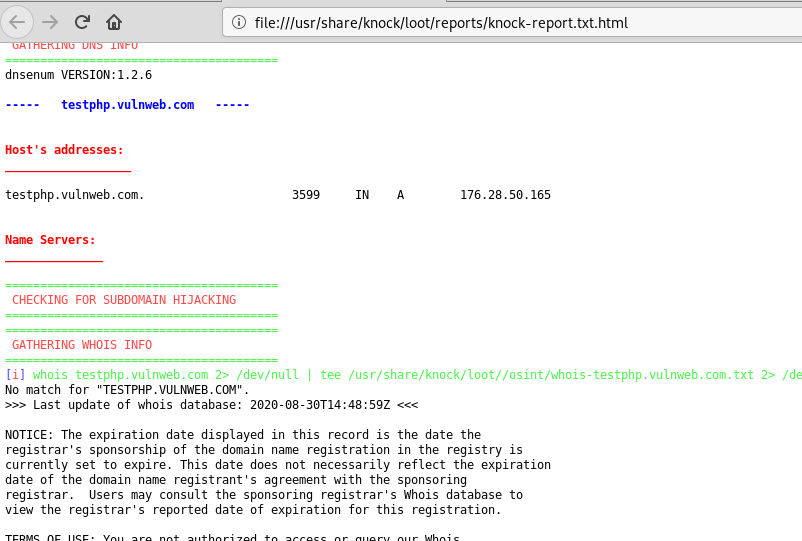
The Kn0ck begins scanning with the DNS and WHOIS information.
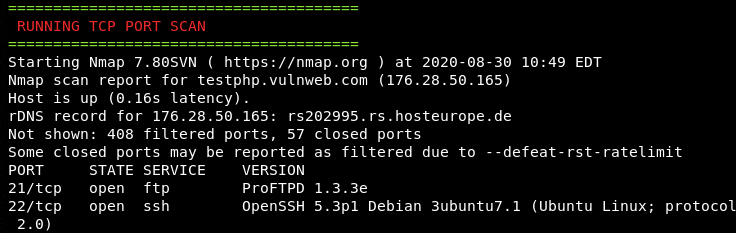
After getting the basic DNS and WHOIS information, the Kn0ck tool starts digging deeper into the target host by finding the open ports, running services, and version information.
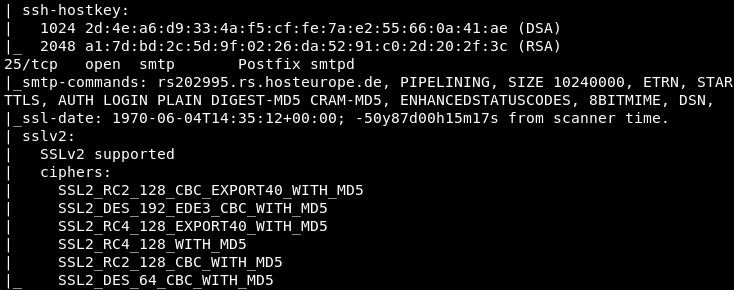
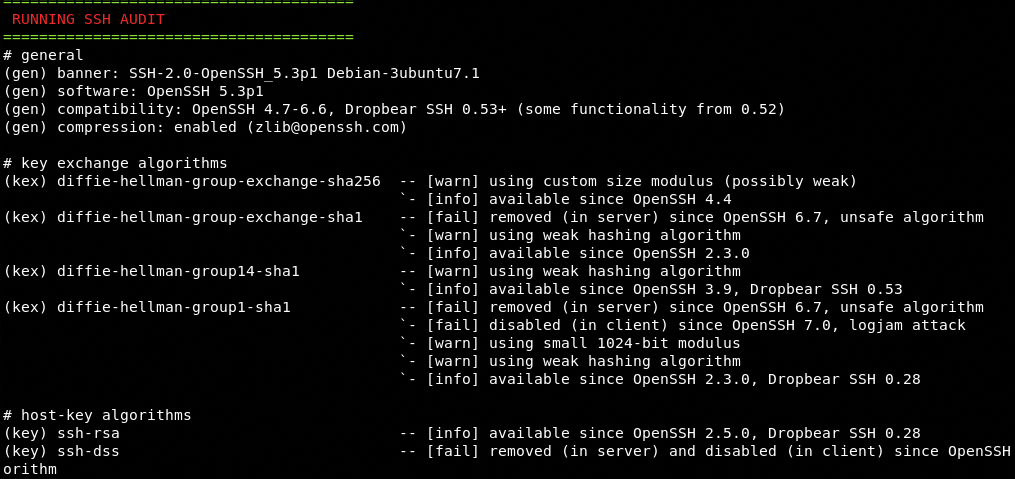
The services and version information at this stage is very crucial since some vulnerabilities are associated with certain ports and their versions. The host keys and supported cipher information is gathered in the following format.
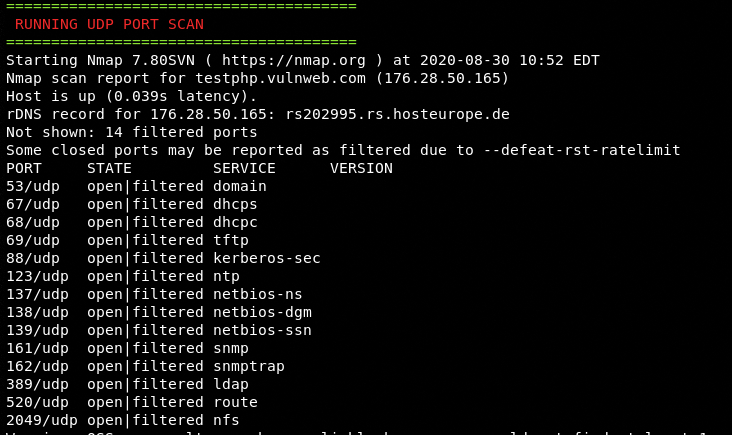
The UDP port scanning is also performed without the version information.
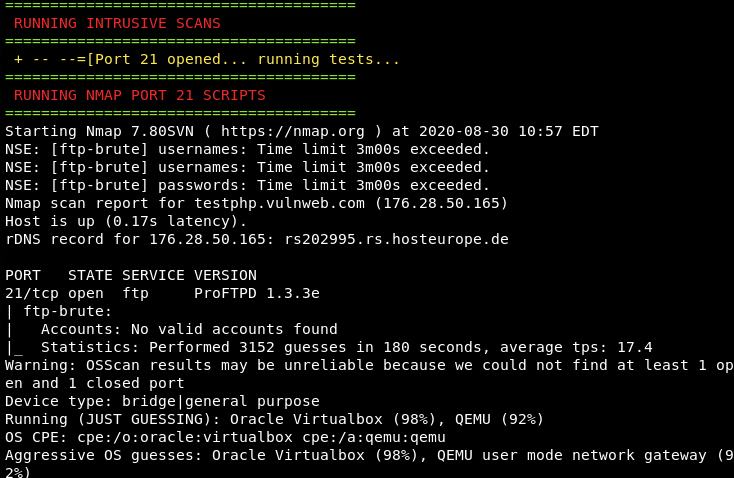
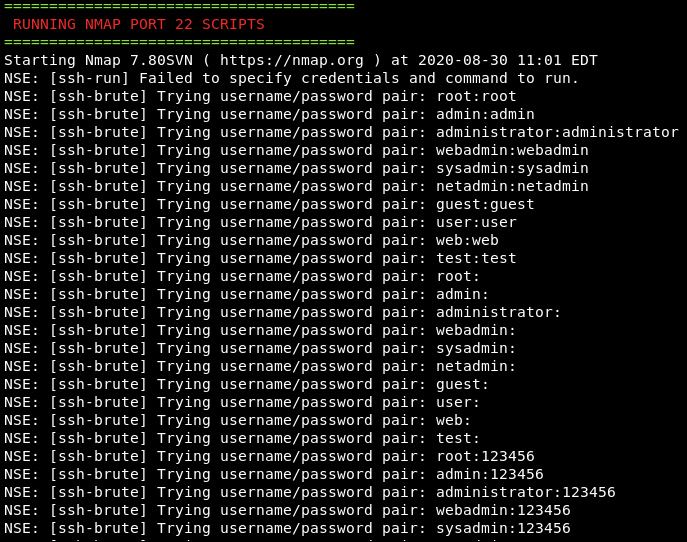
After completing the TCP/UDP scanning process, the Kn0ck tool performs the intrusive scanning to find vulnerabilities in the target host. The following screenshots show some of the intrusive scanning tasks performed by the Kn0ck tool.
SSH Audit
FTP Bruteforce Test
SSH Bruteforce Test
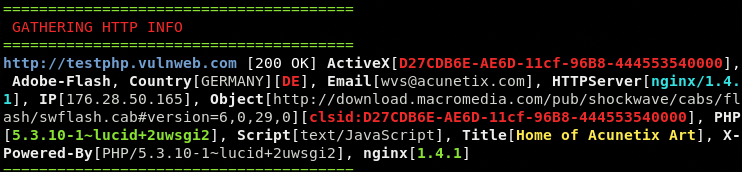
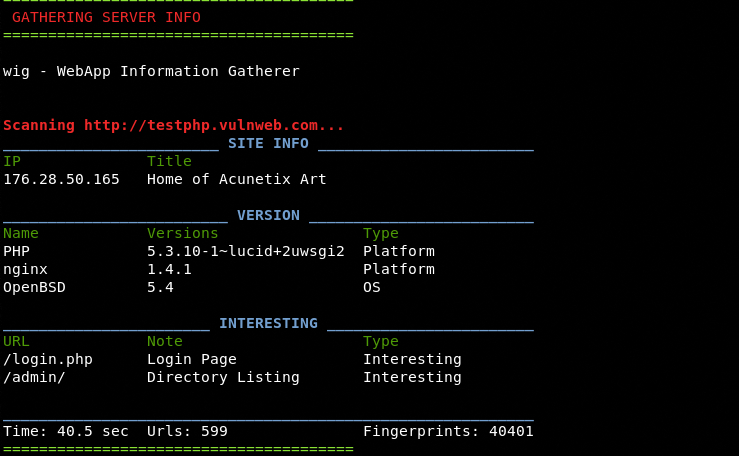
HTTP Information Check
Server Information
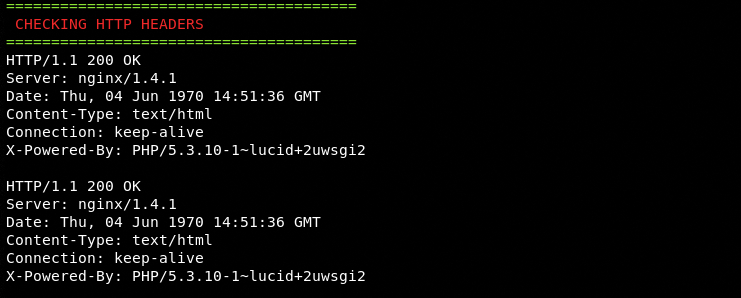
HTTP Headers Information
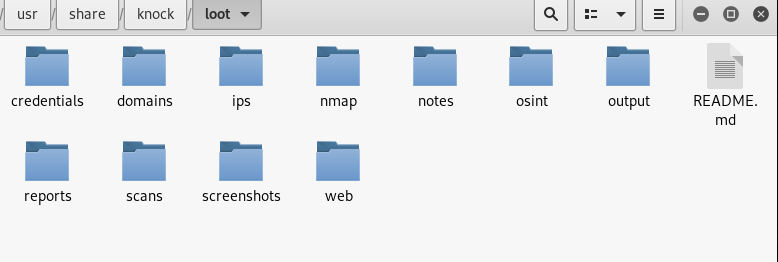
After completing the scanning process, the results are stored in /usr/share/kn0ck/loot/ directory. If we analyze the /loot/ directory, we can see a number of sub-folders, each having specific scan results.
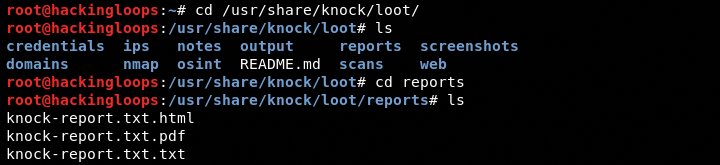
The reports section contains the scan results in three different formats as shown in the following screenshot.
cd /usr/share/kn0ck/loot/ cd reports/ls
Example of HTML Report
Conclusion
There are many penetration testing tools to automate the information gathering and vulnerability scanning process. However, there are only a few utilities like the Kn0ck tool possessing the auto-pwn feature to automatically identify the CVE’s and RCE’s in networks and web technologies.