Picture this: Every morning, millions of employees across the globe wake up, grab their coffee, and log into systems that exist everywhere and nowhere at once. Welcome to the cloud era—where your office files live in cyberspace and your business runs on invisible servers scattered across the planet.
However, as organizations accelerate their digital transformation strategies, cloud security is not just a necessity—it’s a business imperative. As a result, this comprehensive analysis explores the most current cloud security statistics, threats, trends, and practices that are shaping the global business environment.
Today’s cloud landscape tells a fascinating story of paradox. We’ve achieved unprecedented connectivity and efficiency, yet we’re fighting an invisible war against threats that evolve faster than we can count them. Every statistic, every trend, every security measure reveals another chapter in humanity’s greatest digital migration story.
The question isn’t whether your business will face cloud security challenges—it’s whether you’ll be ready when they come knocking.
Global Cloud Security Statistics Overview: From Basement Servers to Sky-High Dreams
Remember when companies used to house their data in humming server rooms? Those days are as outdated as flip phones. Today’s businesses—whether it’s a startup in a garage or a Fortune 500 giant—have packed up their digital lives and moved to the cloud.
But here’s the twist in our story: This mass exodus to the cloud wasn’t just about convenience. It became a matter of survival. Companies that didn’t make the leap found themselves stuck in the digital stone age while their competitors soared ahead with lightning-fast access to data, seamless remote work, and costs that actually made sense.
The reliance on cloud technology has reached unprecedented levels, fundamentally transforming how businesses operate and secure their digital assets. The statistics reveal a landscape where cloud adoption has become nearly universal, yet security challenges continue to evolve at an alarming pace.
- 94% of businesses worldwide rely on some form of cloud infrastructure (IaaS, SaaS, or PaaS), indicating a deep-rooted shift from traditional on-premises computing.
- The global cloud security market is projected to reach $97.3 billion in 2025, up from $62.7 billion in 2022, signifying substantial investment in safeguarding digital infrastructure.
78% of enterprises have integrated security directly into their DevOps pipelines, promoting a proactive and automated approach to cybersecurity.
This widespread reliance is a double-edged sword: while cloud services enhance scalability, efficiency, and collaboration, they also introduce new vulnerabilities. The expansion of remote work, IoT ecosystems, and AI-powered applications continues to increase the attack surface in cloud environments, demanding constant innovation in security practices and policies.
Data Breach Landscape and Attack Vectors in Cloud Environments
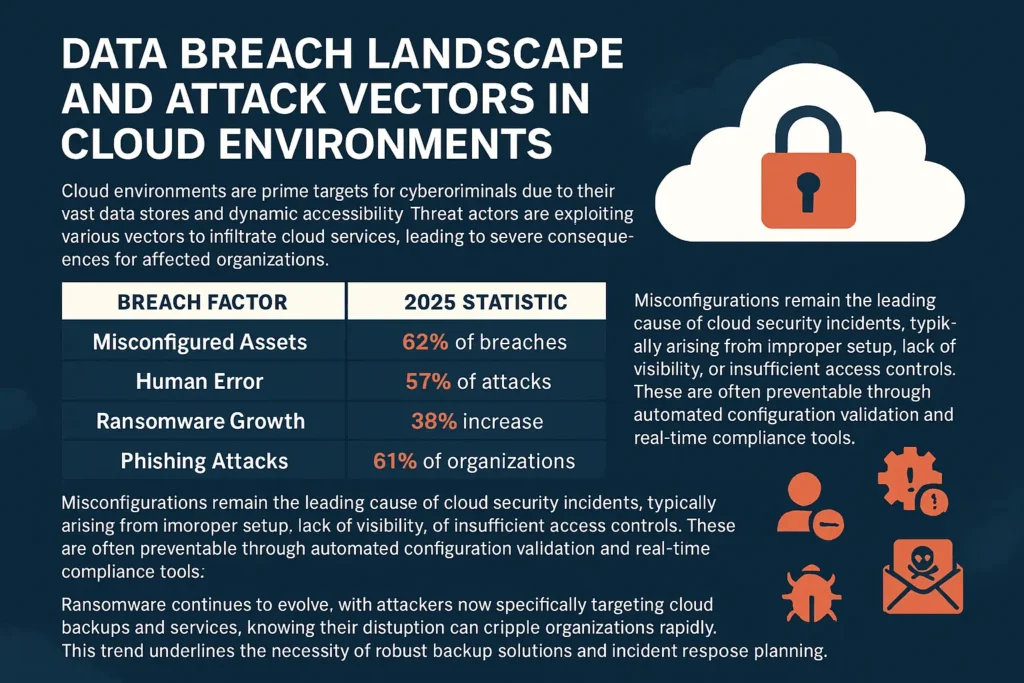
Cloud environments are prime targets for cybercriminals due to their vast data stores and dynamic accessibility. Threat actors are exploiting various vectors to infiltrate cloud services, leading to severe consequences for affected organizations.
| Breach Factor | 2025 Statistic |
| Misconfigured Assets | 82% of breaches |
| Human Error | 57% of attacks |
| Ransomware Growth | 38% increase |
| Phishing Attacks | Affected 61% of organizations |
Misconfigurations remain the leading cause of cloud security incidents, typically arising from improper setup, lack of visibility, or insufficient access controls. These are often preventable through automated configuration validation and real-time compliance tools.
Human error, while harder to eliminate entirely, can be mitigated through continuous employee education, strict access policies, and behavioral analytics. Meanwhile, phishing and credential theft have become increasingly sophisticated, with attackers exploiting the trust model of cloud services and the ubiquity of remote access.
Ransomware continues to evolve, with attackers now specifically targeting cloud backups and services, knowing their disruption can cripple organizations rapidly. This trend underlines the necessity of robust backup solutions and incident response planning.
Industry-Specific Cloud Security Analysis
Healthcare Sector
- 94% of healthcare providers use cloud to store patient data, benefiting from enhanced accessibility and collaborative capabilities.
- 71% of breaches are due to inadequate encryption or improper handling of sensitive data.
- Financial losses from cloud-related breaches reached $11.2 billion globally, factoring in legal penalties, regulatory fines, and reputational damage.
Healthcare organizations must comply with stringent regulations like HIPAA and GDPR, and their failure to do so often results in severe consequences. Encryption and secure access control are crucial in safeguarding patient records and other health-related information.
Financial Services
- 30% surge in phishing attacks, mainly targeting employees with access to sensitive financial systems.
- 76% adoption of tokenization and Zero Trust models, minimizing exposure even when systems are compromised.
- 22% increase in compliance costs, driven by stricter regulatory frameworks and ongoing risk assessments.
As custodians of highly valuable financial data, banks and financial institutions face complex regulatory landscapes. Cloud solutions must therefore incorporate real-time risk monitoring and advanced fraud detection systems to remain compliant and secure.
Retail and E-Commerce
- 68% of sites hosted entirely on cloud platforms, offering flexibility and scalability during peak shopping seasons.
- 42% increase in credential stuffing attacks, exploiting reused passwords and weak authentication mechanisms.
- $5.4 billion in lost revenue due to security-related cart abandonment, highlighting the link between user trust and e-commerce performance.
Retailers must strike a balance between user convenience and security. Implementing Multi-Factor Authentication (MFA), secure payment gateways, and real-time fraud monitoring can mitigate risks and build consumer confidence.
Top Cloud Security Statistics and Threats
| Threat Category | Prevalence | Primary Impact |
| Misconfigurations | 62% | Data exposure, compliance violations |
| Phishing & Credential Theft | 61% | Account compromise, unauthorized access |
| Insecure APIs | 52% | Data breaches, manipulation of system operations |
| Ransomware | 38% | Business disruption, operational shutdowns |
| Insider Threats | 29% | Data exfiltration, sabotage |
| Supply Chain Attacks | 21% | Widespread compromise, loss of trust |
These threats emphasize the need for layered defenses, thorough access control, and automated monitoring systems. Insecure APIs, in particular, are becoming a major concern as organizations expose more services externally, requiring stronger authentication and monitoring protocols.
Security Technologies and Solutions
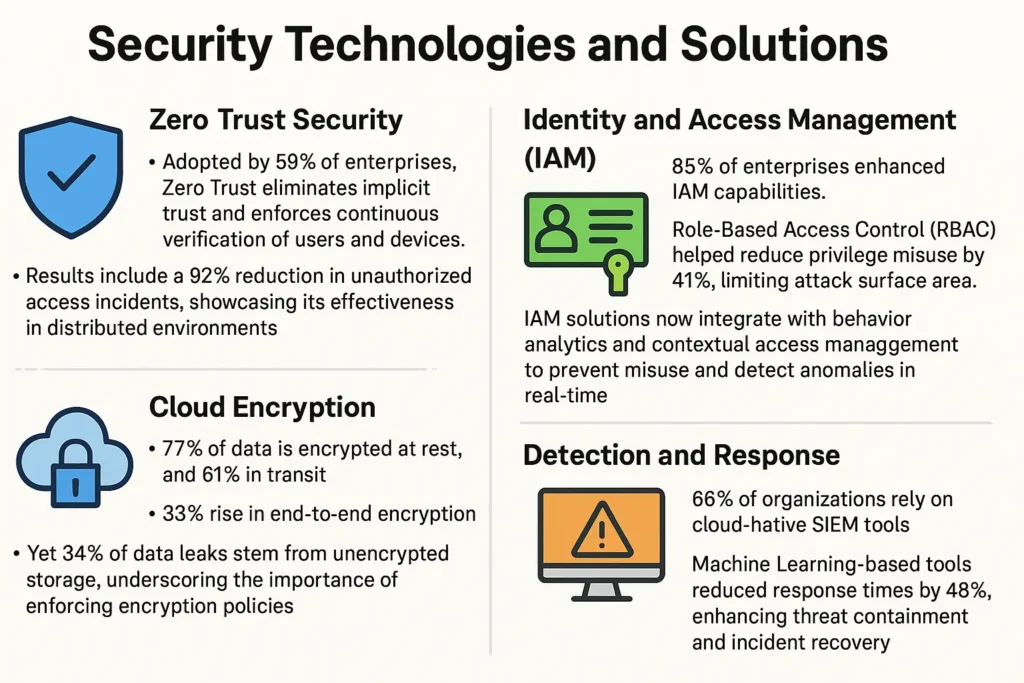
Zero Trust Security
- Adopted by 59% of enterprises, Zero Trust eliminates implicit trust and enforces continuous verification of users and devices.
- Results include a 92% reduction in unauthorized access incidents, showcasing its effectiveness in distributed environments.
Identity and Access Management (IAM)
- 85% of enterprises enhanced IAM capabilities.
- Role-Based Access Control (RBAC) helped reduce privilege misuse by 41%, limiting attack surface area.
IAM solutions now integrate with behavior analytics and contextual access management to prevent misuse and detect anomalies in real-time.
Cloud Encryption
- 77% of data is encrypted at rest, and 61% in transit.
- 33% rise in end-to-end encryption.
- Yet 34% of data leaks stem from unencrypted storage, underscoring the importance of enforcing encryption policies.
Detection and Response
- 66% of organizations rely on cloud-native SIEM tools.
- Machine Learning-based tools reduced response times by 48%, enhancing threat containment and incident recovery.
Regional Statistics
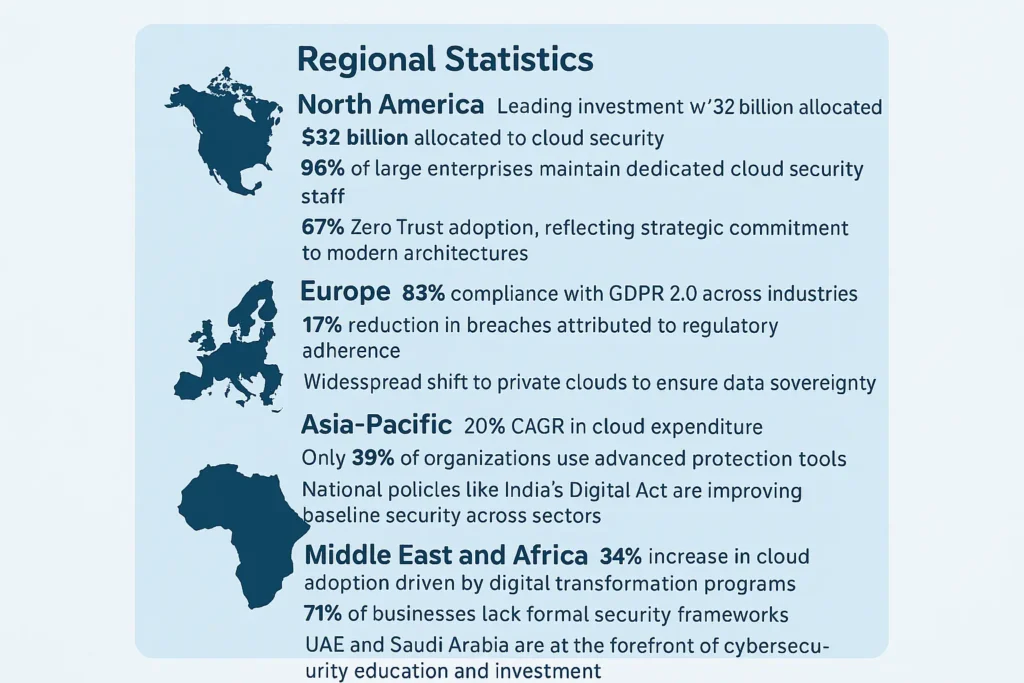
North America
- Leading investment with $32 billion allocated to cloud security.
- 96% of large enterprises maintain dedicated cloud security staff.
- 67% Zero Trust adoption, reflecting strategic commitment to modern architectures.
Europe
- 83% compliance with GDPR 2.0 across industries.
- 17% reduction in breaches attributed to regulatory adherence.
- Widespread shift to private clouds to ensure data sovereignty.
Asia-Pacific
- 20% CAGR in cloud expenditure.
- Only 39% of organizations use advanced protection tools.
- National policies like India’s Digital Act are improving baseline security across sectors.
Middle East and Africa
- 34% increase in cloud adoption driven by digital transformation programs.
- However, 71% of businesses lack formal security frameworks.
- UAE and Saudi Arabia are at the forefront of cybersecurity education and investment.
Compliance and Regulatory Landscape
Around the world, lawmakers who once struggled to understand email are suddenly writing sophisticated cyber laws faster than hackers can adapt. In fact, From Brussels to Washington, regulators have finally realized that our digital world needs digital rules, and they’re not messing around. Meanwhile, we’re now witnessing the birth of a new era where compliance isn’t just about checking boxes—it’s about proving your business deserves to exist in cyberspace.
| Regulation | 2025 Updates | Impact |
| GDPR 2.0 | Enhanced penalties, cross-border data policies | Stronger enforcement in EU |
| CCPA 2025 | Broadened definitions of personal data | Greater business accountability |
| Digital India Act | Mandatory cloud security frameworks | Elevating APAC security standards |
- 72% of organizations revised policies to stay compliant.
- Non-compliance fines reached $2.4 billion, reflecting strict enforcement globally.
Cloud Security Technology Adoption Trends
| Technology | Adoption Rate | Benefit |
| Cloud Access Security Broker (CASB) | 69% | Granular control over third-party apps and services |
| Cloud Security Posture Management (CSPM) | 66% | Automated remediation of misconfigurations |
| Cloud Workload Protection Platforms (CWPP) | 53% | Runtime security for containers and workloads |
| Secure Access Service Edge (SASE) | 49% | Secure, remote access integration |
| Identity Threat Detection and Response (ITDR) | 38% | Real-time detection of identity compromise |
These tools are converging into unified platforms, enabling centralized monitoring, faster remediation, and policy enforcement at scale.
Persistent Challenges
| Challenge | Affected Organizations |
| Talent Shortage | 63% |
| Shadow IT | 43% |
| Visibility Gaps | 46% |
Lack of skilled professionals and the proliferation of unauthorized tools continue to undermine cloud security efforts. Bridging these gaps requires targeted hiring, internal training, and the adoption of unified monitoring solutions.
Best Practices for Cloud Security
Creating a bulletproof cybersecurity strategy starts with the fundamentals, beginning with enforcing Multi-Factor Authentication (MFA) across all systems to dramatically reduce the risk of credential theft.
Next, organizations must encrypt all data—whether it’s sitting in storage, traveling between systems, or being actively processed. Implementing Identity and Access Management (IAM) alongside Role-Based Access Control (RBAC) ensures that employees can only access what they absolutely need for their specific job roles.
Building upon these, access controls, adopting a Zero Trust Architecture takes security even further by eliminating any assumption of trust within your network. Meanwhile, regular penetration testing and comprehensive risk assessments should be scheduled consistently to identify vulnerabilities before attackers do.
Educating employees about phishing schemes and social engineering tactics transforms your workforce from potential weak links into your first line of defense. To support these human efforts, leveraging Security Information and Event Management (SIEM) and Security Orchestration, Automation, and Response (SOAR) platforms provides continuous threat monitoring and rapid incident response.
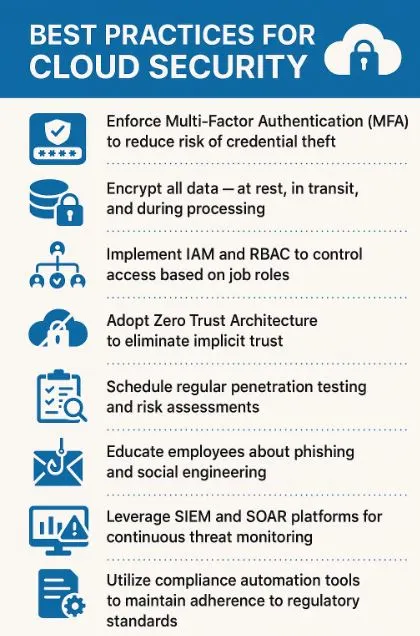
- Enforce Multi-Factor Authentication (MFA) to reduce risk of credential theft.
- Encrypt all data – at rest, in transit, and during processing.
- Implement IAM and RBAC to control access based on job roles.
- Adopt Zero Trust Architecture to eliminate implicit trust.
- Schedule regular penetration testing and risk assessments.
- Educate employees about phishing and social engineering.
- Leverage SIEM and SOAR platforms for continuous threat monitoring.
- Utilize compliance automation tools to maintain adherence to regulatory standards.
Future Outlook: Trends Beyond 2025
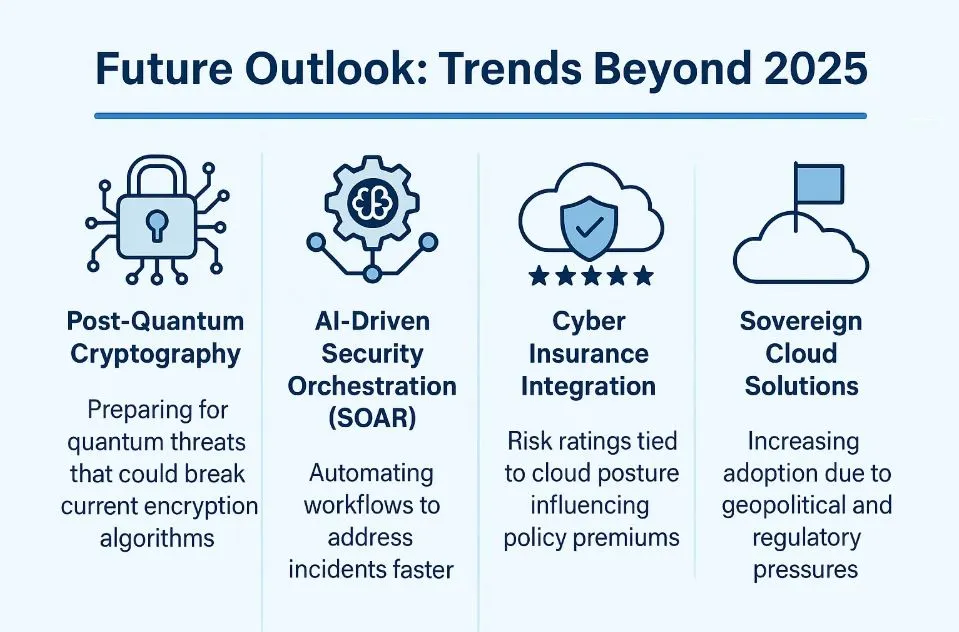
- Post-Quantum Cryptography: Preparing for quantum threats that could break current encryption algorithms.
- AI-Driven Security Orchestration (SOAR): Automating workflows to address incidents faster.
- Cyber Insurance Integration: Risk ratings tied to cloud posture influencing policy premiums.
- Sovereign Cloud Solutions: Increasing adoption due to geopolitical and regulatory pressures.
Cloud Security Statistics Conclusion
Stop thinking of cybersecurity as money down the drain. Start seeing it for what it really is: your investment in becoming unshakeable. Every dollar spent on security today is a dollar invested in your company’s reputation, your customers’ loyalty, and your ability to sleep soundly at night.
The roadmap is right here in front of you. The statistics don’t lie, the best practices work, and the cloud ecosystem is waiting for businesses brave enough to not just survive in it, but to own it completely.