You work as a scientist but one day you started staring at your computer screen in disbelief. The RSA-2048 encryption that had protected your research lab’s most sensitive data for decades (which is the same encryption that banks, governments, and tech giants rely on) had just been cracked in under 24 hours. But this wasn’t 2040. This was a simulation running on IBM’s latest quantum prototype, and the results were both fascinating and terrifying.
What you witnessed wasn’t science fiction; it was a glimpse into our near future, where quantum computers completely shatter the cryptographic foundation that our digital world rests upon. Welcome to the quantum threat, and it’s coming faster than most people realize.
Imagine the same technology used to provide the most advanced and stealth encryption is used to break it.
The Countdown Has Begun
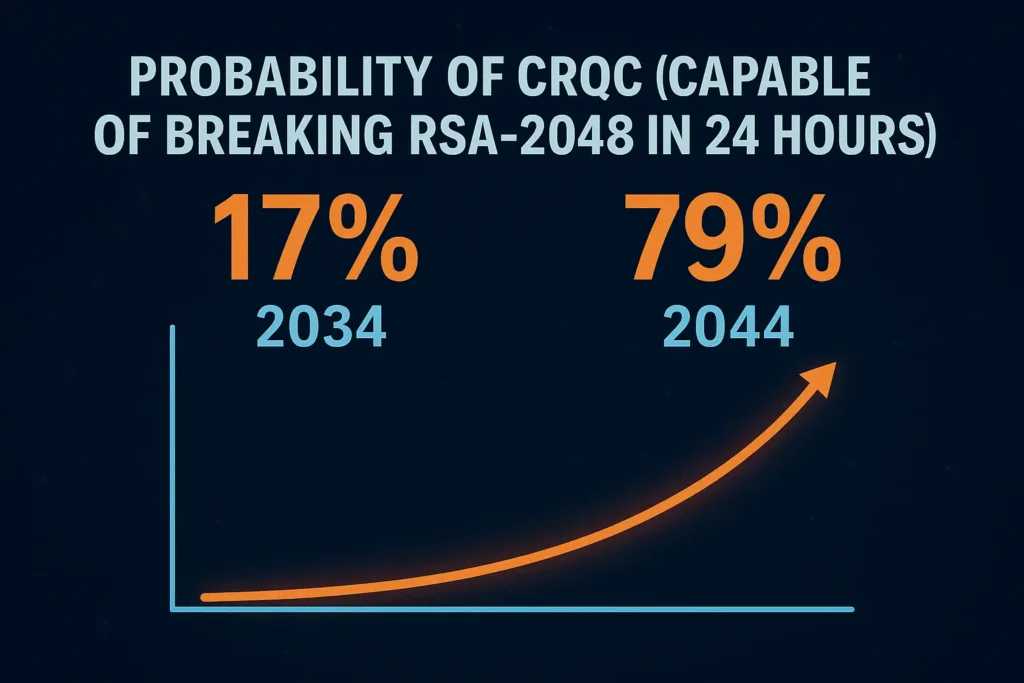
Let’s start with the numbers that should keep every CISO awake at night. By 2034, there’s between a 17% and 34% chance that a cryptographically relevant quantum computer (CRQC) would exist capable of breaking RSA 2048 in 24 hours. The probability increases to 79% by 2044.
For the contrast, it would take trillions of years based on the current computational powers to break RSA encryption. Compare that with days or weeks for quantum computers!
Think about what that means. In less than two decades, there’s nearly an 80% chance that the encryption protecting your bank account, medical records, and state secrets could be broken faster than you can finish your morning coffee.
Right now, NIST estimates that the current RSA 2048 bit technology used to encrypt sensitive and confidential data is enough to use till 2030.
But here’s the kicker: some experts predict that a device with the capability to break current encryption methods could appear within a decade.
The $50 Billion Revolution
The quantum computing industry isn’t playing around. The global market is expected to hit US$50 billion by the end of this decade, with quantum computing companies surpassing $1 billion in of revenues in 2025.
To put this in perspective, that’s faster growth than the early internet boom. Major players like Amazon, IBM, Google, and Microsoft aren’t just dipping their toes in the quantum waters; they’re diving headfirst with billions in investments. Surging investment and faster-than-expected innovation could propel the quantum market to $100 billion in a decade.
PS: While you’re at it, you can read on how quantum computing and AI is soon going to dry out fresh water source given the immense heat these systems generate.
While quantum computers are racing toward cryptographic relevance, the cybersecurity world is sleepwalking into disaster. 62% of technology and cybersecurity professionals believe quantum computing will have a significant impact, yet many organizations remain unprepared.
The preparation gap is stark and concerning. 31% of advanced IT departments are preparing to invest in post-quantum cryptography by 2025, compared to 16% of average IT departments. This isn’t just a technology gap, it’s a survival gap.
This means that only one in six average IT departments are even thinking about preparing for it. It’s like knowing a hurricane is coming and deciding to reinforce your windows next year.
What’s Actually at Stake?
Picture this scenario: it’s 2035, and someone just cracked the encryption protecting:
- Every credit card transaction from the last 20 years
- All your “private” messages and emails
- Medical records for entire populations
- Corporate trade secrets and intellectual property
- Military communications and state secrets
- Cryptocurrency wallets and blockchain transactions
This isn’t fear-mongering, it’s pure mathematics. Current public-key cryptography relies on problems hard for classical computers to solve but trivial for sufficiently powerful quantum computers. It’s like having a lock that’s nearly impossible to pick with a standard lockpick but opens instantly with a quantum skeleton key.
The threat extends beyond just breaking encryption in real-time. There’s a terrifying concept called “Harvest Now, Decrypt Later” attacks. Adversaries are already collecting encrypted data today, knowing they can break it once quantum computers become available. Your encrypted communications from 2025 might be readable in 2035. Just because it is encrypted today doesn’t mean it won’t be decrypted tomorrow.
The Financial Sector Wakes Up
The financial industry, which has the most to lose from cryptographic collapse, is starting to take notice. The Quantum Financial Taskforce, led by the G20, has committed $1 billion by 2025 to ensure quantum resilience in global finance systems.
This shows that quantum threats could trigger a financial catastrophe that would the 2007-2008 financial recession look like a minor hiccup. Imagine if every secure transaction, every encrypted database, every protected communication suddenly became readable to anyone with a quantum computer. The trust that underpins our entire digital economy would evaporate overnight.
The Government Response: Playing Catch-Up
Recognizing the severity of the threat, governments worldwide are scrambling to respond. In August 2024, NIST (the National Institute of Standards and Technology) released the first three finalized post-quantum encryption standards, with a fifth algorithm called HQC selected in March 2025 as a backup for the main algorithm ML-KEM. If one post-quantum algorithm gets broken, having alternatives could mean the difference between a temporary inconvenience and a complete digital collapse.
But here’s the challenge: migrating to post-quantum cryptography isn’t like updating your phone’s software. It requires rebuilding fundamental infrastructure, rewriting protocols, and replacing hardware that was never designed with quantum threats in mind. We need to arm ourselves with quantum safe encryption and crypto-agility.
The Current Quantum Landscape: Closer Than You Think
While a cryptographically relevant quantum computer doesn’t exist yet, the progress is accelerating. Based on historical quantum volume trends, MITRE estimates that a quantum computer capable of breaking RSA-2048 encryption is unlikely to emerge before 2055-2060, though some experts believe this timeline is too conservative.
The conservative estimates provide some comfort, but in cybersecurity, betting on conservative estimates is like playing Russian roulette with digital civilization. Experts estimate that within 5-15 years, a cryptographically relevant quantum computer (CRQC) could break standard encryptions in under 24 hours.
What Makes Quantum Computers So Dangerous?
Classical computers process information in bits; ones and zeros. Quantum computers use quantum bits (qubits) that can exist in multiple states simultaneously, allowing them to perform certain calculations exponentially faster.
For most problems, this doesn’t matter much. But for the specific mathematical problems that underpin modern cryptography; like factoring large numbers or solving discrete logarithms, quantum computers are like bringing a supercomputer to a calculator fight.
The algorithms that would run on these quantum computers aren’t theoretical. Grover’s algorithm can search unsorted databases quadratically faster. These are mathematical certainties waiting for the hardware to catch up.
The Post-Quantum Defense: Building Tomorrow’s Walls
Post-quantum cryptography is a defense against potential cyberattacks from quantum computers, with algorithms based on mathematical techniques that can be very old, such as elliptic curves, which trace their history back to ancient Greek times.
The defense strategy involves several approaches:
- Lattice-based cryptography uses problems related to finding short vectors in high-dimensional lattices—problems that appear to be hard even for quantum computers.
- Hash-based signatures rely on the security of cryptographic hash functions, which Grover’s algorithm can only attack quadratically (meaning you just need to double the key size for equivalent security).
- Code-based cryptography uses error-correcting codes as a foundation for security.
- Multivariate cryptography bases security on solving systems of multivariate polynomial equations.
- The diversity isn’t accidental. By using different mathematical foundations, cryptographers are hedging their bets. If one approach falls to quantum attack, others might still stand.
The Hybrid Approach: Best of Both Worlds
Many organizations are adopting a hybrid strategy, using both classical and post-quantum algorithms simultaneously. This approach provides security against both classical and quantum attacks while allowing for a gradual transition. The hybrid model also addresses another critical concern; what if the post-quantum algorithms have flaws we haven’t discovered yet? If one system fails, the other provides backup protection.
Analysts estimate the economic impact of quantum computing could reach trillions by the mid-2030s, but that impact includes both opportunities and threats. The organizations that prepare early will thrive in the quantum age. Those that don’t might not survive the transition.
The Geopolitical Dimension: The New Arms Race
The quantum threat isn’t just about criminals and hackers—it’s about nation-states and global power dynamics. Countries that achieve quantum supremacy first will have an enormous intelligence advantage, capable of reading their adversaries’ encrypted communications while protecting their own with quantum-resistant methods. This has created a quantum arms race, with nations pouring billions into quantum research. The implications extend beyond cybersecurity to national security, economic competitiveness, and global stability.
What Organizations Need to Do Now
Organizations can’t wait for the perfect post-quantum algorithms or for quantum computers to actually emerge. They need to start preparing now.
- Inventory current cryptography: Identify all the places your organization uses encryption.
- Develop crypto-agility: Design systems that can quickly swap out cryptographic algorithms when needed.
- Pilot post-quantum algorithms: Start testing NIST-approved algorithms in non-critical environments.
- Plan the migration: Develop a roadmap for transitioning to post-quantum cryptography.
- Train your team: Ensure your cybersecurity team understands quantum threats and post-quantum solutions.
- Monitor developments: Stay informed about both quantum computing progress and post-quantum cryptography evolution.
- The Individual Perspective: Your Digital Life in the Quantum Age
Every encrypted message you send today, every online transaction you make, every private document you store in the cloud—all could potentially be decrypted retroactively once quantum computers emerge. This doesn’t mean you should stop using digital services, but it does mean being aware that digital privacy has an expiration date unless we successfully transition to quantum-resistant methods. Consider using services from providers who are already thinking about post-quantum security. Look for mentions of quantum-safe cryptography in security policies. Support organizations that are being proactive about this challenge.
The Timeline Reality Check
The simulation we discussed earlier showed what’s possible, but when will it become probable? The honest answer is that nobody knows for certain. Quantum computing faces significant technical challenges, and progress could accelerate or stall based on breakthroughs in materials science, error correction, and quantum control. What we do know is that the threat is real, the timeline is uncertain but potentially short, and the consequences of being unprepared are catastrophic.
The New Digital Dawn
The organizations, governments, and individuals who recognize this transition and prepare for it will thrive in the quantum future. Those who ignore it or delay preparation risk finding themselves defenseless when the quantum revolution arrives.
The quantum threat isn’t coming, it’s already here, growing stronger in laboratories around the world. The question isn’t whether quantum computers will threaten current cryptography. The question is whether we’ll be ready when they do. Your digital future depends on how we answer that question today.