Tidos Framework is an open source toolkit that performs all the major penetration testing tasks, such as reconnaissance, scanning, enumeration, and vulnerabilities analysis. All the tasks are performed in phases using the built in modules. The total number of modules exceeds 100, with majority used for reconnaissance and vulnerability analysis.
How to Install Tidos Framework
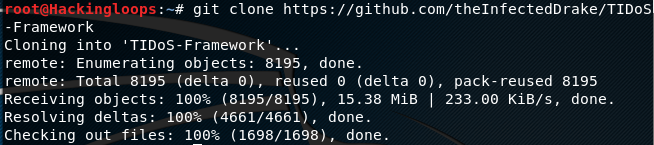
Tidos is a python framework that can cloned from Github using the following command.
git clone https://github.com/theInfectedDrake/TIDoS-Framework
After cloning the toolkit, move to the Tidos framework directory to install the dependencies as follows.
cd TIDoS-Framework chmod +x install ./install
How Tidos Works
The following command not only runs the Tidos framework but also prompts for the target web application to unlock the penetration testing features.
python tidos.py
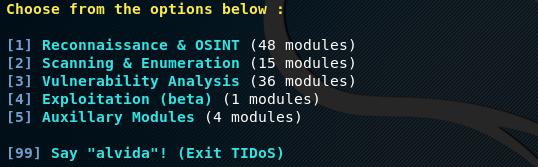
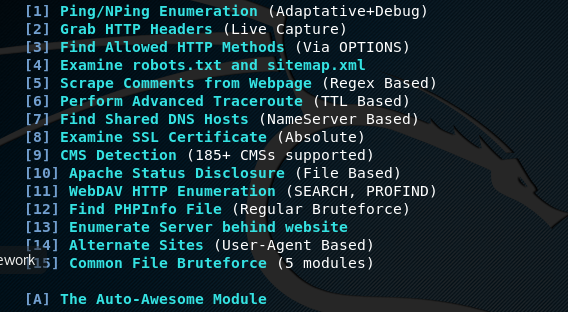
If the target web application is up and running, Tidos displays the penetration testing options (phases) as shown in the following screenshot.
Following is a brief description of each phase that can be performed using the Tidos framework.
Reconnaissance and Open Source Intelligence
The reconnaissance and open source intelligence is divided into three sub-phases namely (a) Passive Footprinting, (b) Active Reconnaissance, and (c) Information disclosure. Passive footprinting involves all the passive information gathering techniques, such as WHOIS Lookup, DNS configuration, subnet enumeration, reverse IP lookup, archived data, and gathering information available in search engines and social profiles like LinkedIn. Tidos can run all these scanning options automatically or it can do manual scanning by selecting the desired option. Similarly, the active reconnaissance scanning option involves all the scanning techniques that require interaction with the target web application like pinging the target web server. The complete list of active reconnaissance options can be seen in the following screenshot.
The information disclosure option scans the target web application for sensitive data that is available in plaintext format. The data can be the credit card information, social security numbers, phone numbers etc.
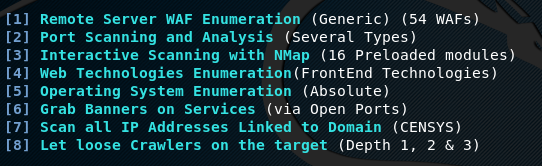
Scanning and Enumeration
Scanning and enumeration phase provides useful information about the target application, such as web application firewall information, open ports enumeration, Banner grabbing, and information about the front end technologies.
For example, if we select banner grabbing option, Tidos framework pings target web application through different ports to get server information, hosting information, encryption technique, compression algorithms, and other useful information that can be helpful to the adversaries.
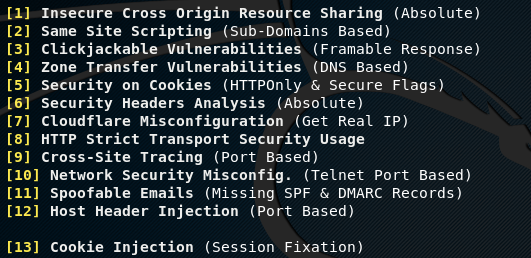
Vulnerability Analysis
Vulnerability analysis is the most important utility of Tidos framework. Using this utility, one can perform basic and critical vulnerabilities assessment of the target web applications. In basic vulnerabilities assessment, Tidos checks if the target web application is vulnerable to vulnerabilities like clickjacking, zone transfer, cookie injection, cross site tracing, and few other vulnerabilities mentioned in the following screenshot.
The critical vulnerabilities analysis option allows scanning of the target web application against a number of high risk vulnerabilities, such as SQL injections, Cross Site Scripting (XSS), Local File Inclusion (LFI), Remote File Inclusion (RFI), OS Command injection, XPath injection, PHP code injection, cross site request forgery, and Xpath injection. Tidos applies different techniques to perform the critical vulnerabilities assessments. For example, to scan the target web application for SQL injection vulnerabilities, Tidos toolkit uses error and blind based techniques with manual and auto mode. In manual mode, the user has to provide the parameters to the toolkit to scan the target web application. In auto mode, the toolkit automatically tests the target web application using cookie error based and user-agent error based injection techniques. However, the manual mode is more effective than the auto mode.
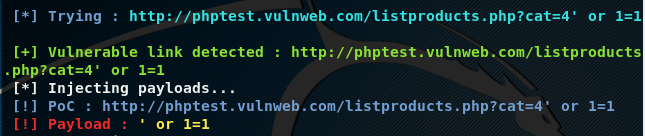
For instance, if we scan the following test url for SQL injection using the error based + manual mode technique, the toolkit runs different payloads to see if the target possesses any SQL injection vulnerability.
http://phptest.vulnweb.com/listproducts.php?cat=4
If the target is vulnerable, the toolkit shows different possible ways of exploiting the SQL vulnerability in the target web application.
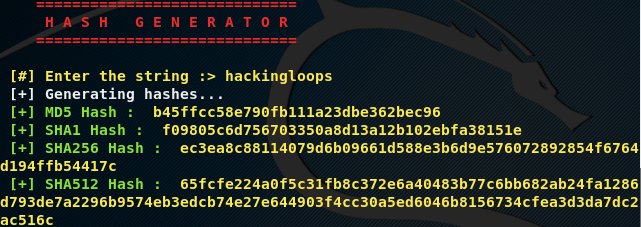
The other Tidos utilities include the exploitation and Auxillary modules. The exploitation feature of the toolkit is still under development and therefore less effective as compared to the reconnaissance, scanning, and vulnerabilities assessment features. The Auxillary module has the features like data encoding, hash function, and Meta data extraction of the images used in forensics. Following screenshot shows hash generating functionality of the toolkit. The toolkit generates MD5, SHA1, SHA256, and SHA512 hash values for a given string.
Conclusion
Tidos Framework is a handy toolkit that is designed according to the penetration testing life cycle. The toolkit can help the penetration testers in finding security flaws in web applications (websites, servers, web apps).