Pythem is a network and web applications penetration testing framework that can perform various penetration tests, divided into following categories
- Network MITM and DoS
- Exploitation and Reverse Engineering
- Bruteforce
- Generic Utilities
Network MITM and DoS covers various attacks against networks and web applications including scanning, traffic sniffing, traffic redirecting, data analysis, spoofing, webcrawl, and denial of service attacks. Spoofing attacks include ARP spoofing, DNS spoofing, and DHCP spoofing. Scanning feature allows scanning the networks and applications to gather information like live hosts, open ports, and OS information. The data analysis is performed using a feature called Pforensics. Pforensics performs data packets capturing and analysis of the content shared in those packets between hosts. The webcrawl utility helps in finding server response for various potentially vulnerable links of the target web applications. Exploitation and reverse engineering allows exploiting network vulnerabilities related to TCP and standard input (stdin) communication channel. Bruteforce is another feature of Pythem that performs bruteforce attack on network hosts and web applications to harvest credentials. The generic utilities of Pythem include coding and decoding strings.
Pythem Installation Guide
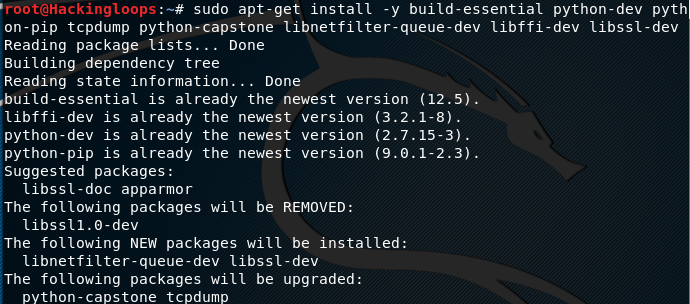
Pythem is a Python framework that works on Linux OS. The framework has the following dependencies that need to be installed before installing Pythem.
sudo apt-get install -y build-essential python-dev python-pip tcpdump python-capstone libnetfilter-queue-dev libffi-dev libssl-dev
It is recommended to update the system before installing these packages.
sudo apt-get update
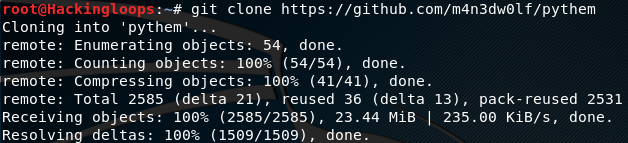
After installing the dependencies, clone Pythem framework using the following command.
git clone https://github.com/m4n3dw0lf/pythem
In the next step, move to the pythem directory to run the setup file to complete the installation process.
cd pythem python setup.py install
How Pythem Works
The following command opens the Pythem interface in the terminal.
./pythem
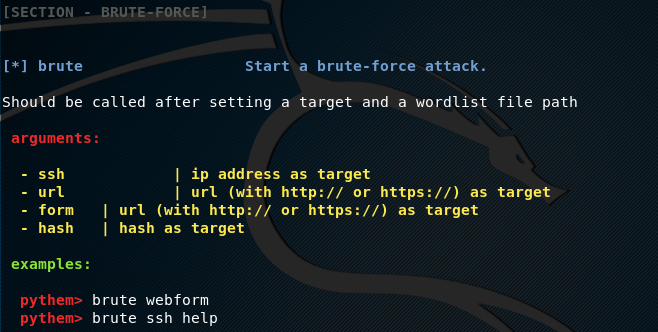
To showcase all the Pythem utilities, type the help command in the terminal
help
The help command shows all the Pythem utilities and their usage instructions, just like the following example screenshot.
Pythem Parameters
Pythem framework supports following parameters during network and web applications penetration tests.
target
interface
gateway
domain
file
filter
script
Each parameter has a specific use. For example the target parameter is used to define the host or target web application during the scanning or crawling process. The interface parameter is used to set the communication channel (wireless, Ethernet). Similarly, the file parameter is used in scenarios like bruteforce attacks where some files are used as an input parameter.
Web Application Example
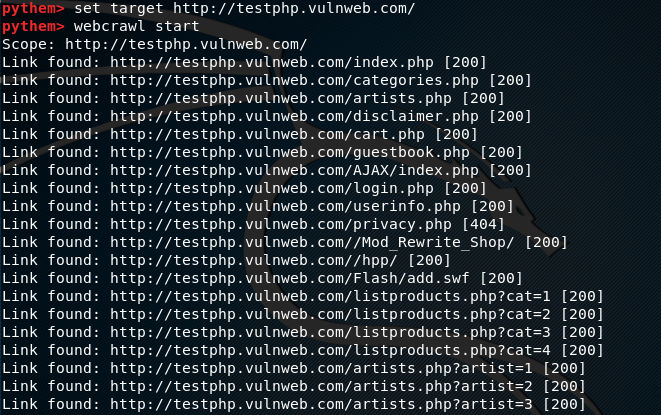
Let’s suppose we want to scan a target web application to find out potentially vulnerable links. This can be achieved by using the webcrawl option in Pythem. In order find out the syntax for webcrawl option, we can use the webcrawl help command in the following format.
webcrawl help
In order to define the target web application, we use target parameter in the following format.
set target <target web application>
To initiate the search process, use the start argument as shown below.
webcrawl start
The above command fetches all the links including the potentially vulnerable links as shown in the following screenshot.
The potentially vulnerable links can further be analyzed with other tools to exploit the target applications.
Network Example
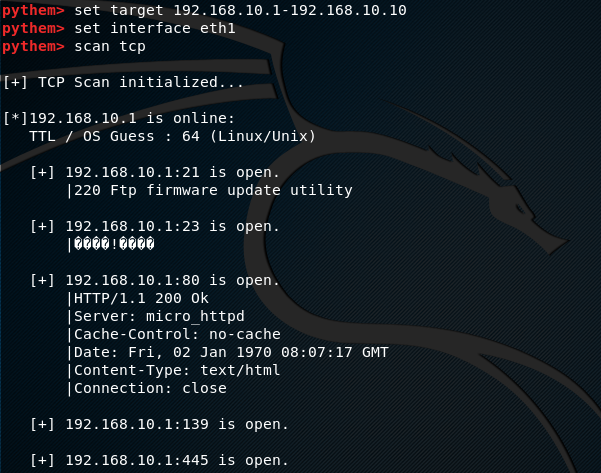
Let’s suppose we want to scan a network to find out all the live hosts, ranging between 192.168.10.1-192.168.10.10 IP addresses. The scan process should also gather information about the open ports for each live host in the network. This task can be achieved by using the Pythem scan feature. To scan the example network, we need to define the target IP range in the following format.
set target 192.168.10.1-192.168.10.10
We also need to define the interface (eth1 in our case) to view the scan details.
set interface eth1
Pythem scan feature supports three modes of scanning i-e tcp, arp, and manual scanning. We can use tcp mode using the following syntax.
scan tcp
The above command starts TCP scanning to find out the hosts status in given IP range. The framework also finds out some useful information like open ports, OS, and server information.
Conclusion
Pythem is a decent framework that can be used to scan and exploit network vulnerabilities. Apart from network penetration testing, the framework is capable of performing web applications penetration tests. However, if you’d like to try out tools directly made for web application pentesting you can also look at arachni and wascan as well.