Fluxion tool can be used for auditing the Access Point (AP) security of wireless networks. The tool attempts to recover Wifi-Protected Access (WPA/WPA2) keys of the target networks by simulating man in the middle (mitm) attack. Fluxion tool presents two attack options namely (a) Handshake Snopper and (b) Captive Portal. The handshake snopper is used to capture the handshake data required to verify the wifi keys captured from the network users. The captive portal attack option creates evil twin access points to lure the users. A fake web server is started by Fluxion tool that prompts users to provide the wifi key in order to connect to the (fake) network. Fluxion tool verifies the user provided keys before they are allowed to connect to the (original) network.
Fluxion Installation
Fluxion operates on Linux OS with wifi card. The tool can be installed by downloading the source code from Github and installing the dependencies. If you need linux help check out our linux commands cheat sheet. The tool can be downloaded using the following command.
git clone https://www.github.com/FluxionNetwork/fluxion.git
After downloading the tool, navigate to the tool directory to install the missing dependencies using the following commands.
cd fluxion ./fluxion.sh –i
How Fluxion Works
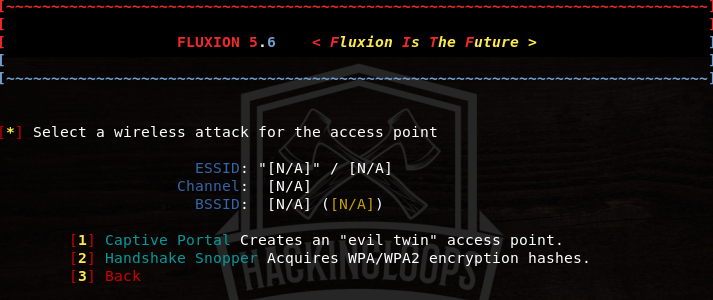
The following command launches Fluxion tool with Captive Portal and handshake snopper attack options as shown in the following screenshot.
./fluxion.sh
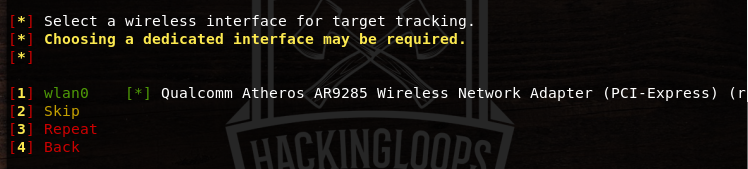
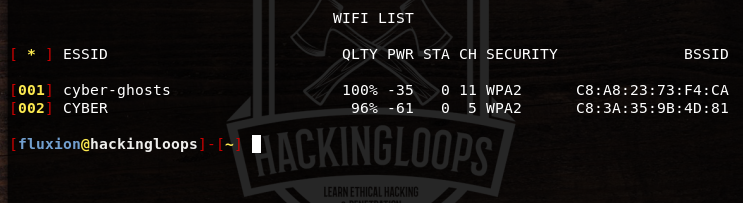
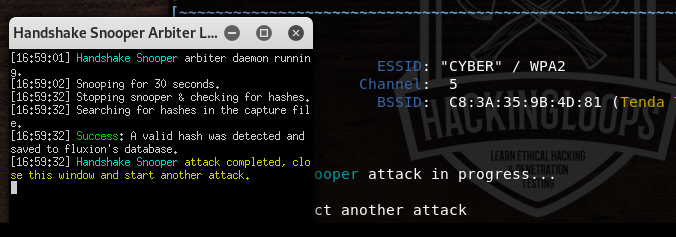
In the first instance, select the handshake snopper attack option in order to capture the handshake data. A wireless interface is required to search the target wifi networks in the range of host OS. Select the desired wireless interface from the available options.
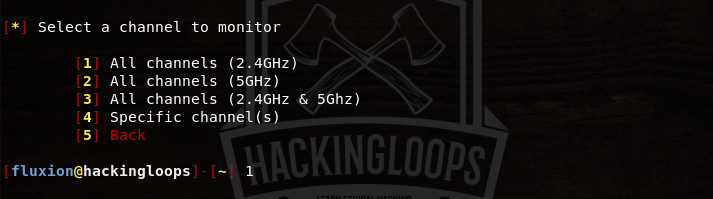
Fluxion can detect wifi networks operating between 2.4 GHZ – 5 GHZ range. Select the desired channel frequency to initiate the search process.
A list of available wifi networks is displayed on the screen. Select the target wifi network by typing its sequence number.
Once the handshake process is completed, close the handshake snopper windows and repeat the attack process for the captive portal attack.
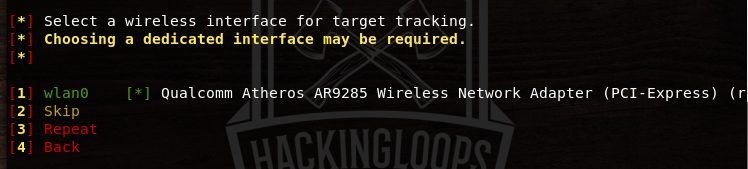
Select a wireless or Ethernet interface for the access point when prompted.
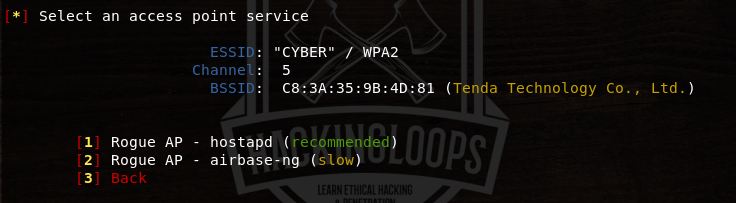
Currently, Fluxion offers two types of rogue access points namely hostapd and airbase-ng.
Select the desired rogue AP option from the list and allow the tool to scan the target wifi network. The tool searches for the hash values previously captured with the handshake process.
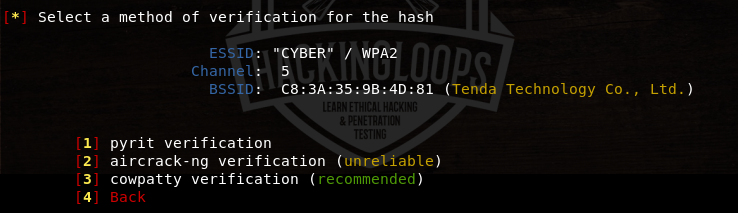
We can either continue with the found hash value or rescan the network to obtain the new hash values. However, it is recommended to continue with the first option i-e with the existing hash values. The tool also requires verification of the hash values. There are few options to verify the hash values. Select the recommended verification option as shown in the following screenshot.
SSL certificate is required to create a secure connection between the target users and the captive portal’s web server. Create the SSL certificate before moving on to the connectivity options for the rogue access point.
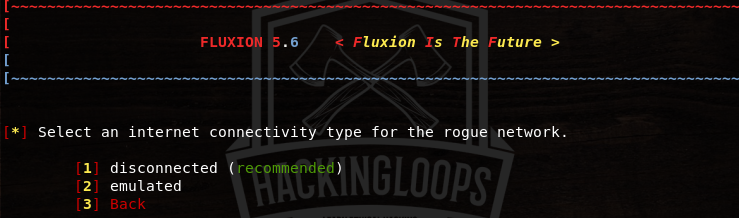
There are two connectivity options available to lure the network users. Either emulate the internet connection or de-authenticate the existing users to capture the WPA/WPA2 keys.
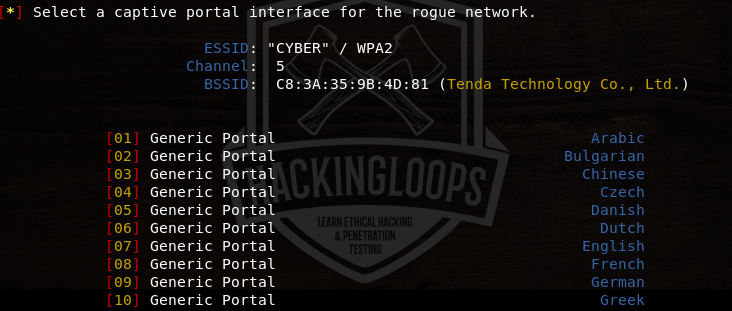
In the last step, select the captive portal interface for the rogue access point. There are a number of interface options available in the tool.
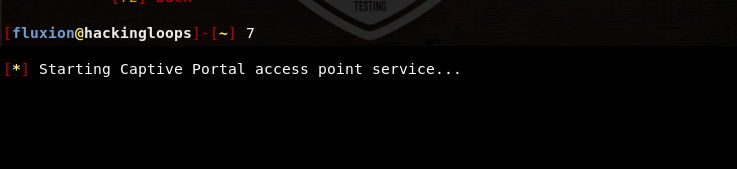
Once the desired captive portal interface is selected, the captive portal service is started by the tool that captures the keys from the network users.
The network users observe connectivity issue caused by Fluxion server. The users are asked to enter the wifi key (WPA/WPA2) in order to gain internet connection. The network keys provided by the users are captured by the captive portal web server.
Conclusion
Fluxion can test the wifi security without launching the bruteforce attack. The tool can capture WPA and WPA2 wifi keys. The verification process blocks the fake keys, often provided by the network users.