Arachni is an open source framework that is used to evaluate the web applications security by performing active and passive security analysis. The active security checks include detection of SQL injection, blind SQL injection, NoSQL injection, CSRF detection, code injection, LDAP injection, path traversal, OS command injection, XPATH injection, remote file inclusion test, XSS, and DOM XSS attacks analysis. For manual review of SQL injections review the SQL injection cheat sheet. The OS command injection is analyzed against nix, BSD, IBM AIX, and Windows system. The XPATH injection analysis is performed for Generic, PHP, dotNET, Java, and libXML2 scripts. Similarly in the passive security tests, Arachni searches for files, folders, and signatures. These include backup files, backup directories, forms, credit card data, .htaccess files misconfiguration, cookies, and files containing policies and other legal data. Besides vulnerability analysis, Arachni can perform fingerprinting based on operating systems, web servers, frameworks, and programing languages. The operating systems must be Linux, UNIX, BSD, Solaris, and Windows OS. The supported web servers are Apache, Nginx, IIS, Tomcat, Jetty, and Gunicorn. The frameworks identified by Arachni are ASP .Net, Rails, Rack, CakePHP, Django, CherryPy, Symfony, JSF, and Netty. Similary, the supported programming languages are PHP, Python, Java, ASP, ASPX, and Ruby.
Arachni Installation
Arachni is a Ruby framework that is supported by all major platforms including Linux and MAC.
The Linux users can clone the tool from Github by running the following code.
git clone git://github.com/Arachni/arachni.git
Arachni has few dependencies that can be installed by moving into the Arachni directory and executing the following commands.
cd arachni gem install bundler bundle install --without prof rake install
Arachni Working
Arachni has GUI as well as CLI execution options. In Linux, Arachni can be executed through command line interface using the following command.
./arachni
Arachni can be used to scan all or specific vulnerabilities in target web applications. The following command scans target web application (phptest.vulnweb.com) for all types of vulnerabilities.
./arachni http://phptest.vulnweb.com
The tool searches all the links, forms, cookies, headers, JSON files, and XML data to find vulnerabilities in the target web application. The potential vulnerabilities are highlighted as they are found during the scanning process.
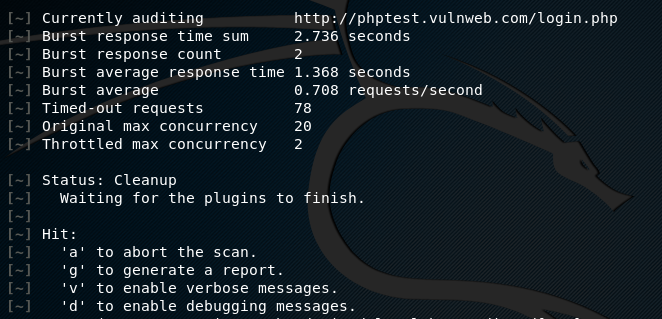
The full scan option may take a lot of time. The operation can be aborted any time by pressing the return key and selecting one of the options available on the following screenshot.
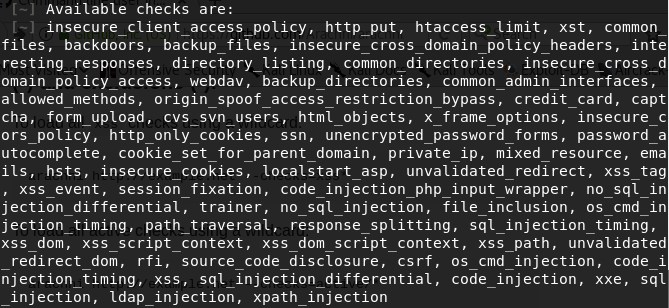
We can also customize the scanning process by selecting specific vulnerabilities tests shown on the following screenshot.
For instance, we can apply time based SQL injection by using sql_injection_timing check as follows.
./arachni http://phptest.vulnweb.com –checks= sql_injection_timing
In order to run all SQL checks, we need to apply the wildcard option in the following format.
./arachni http://phptest.vulnweb.com –checks= sql*
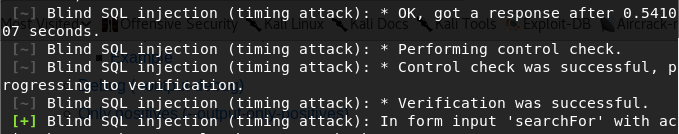
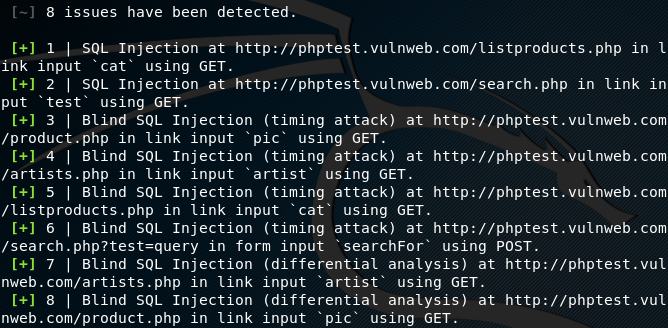
The tool runs all the SQL injection checks to find parameters that can be used as injection points by the adversaries. Arachni uses specific payloads to validate and enumerates the vulnerable links as shown in the following screenshot.
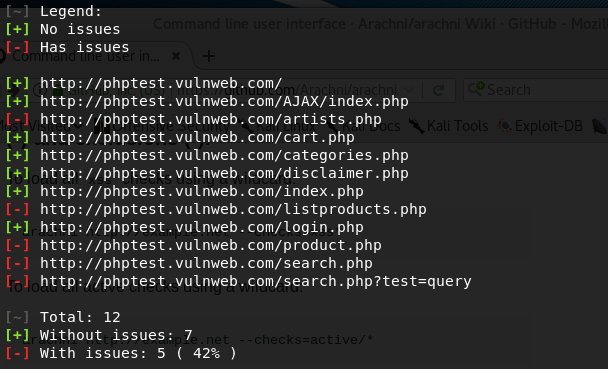
A summary of vulnerable and safe links is generated at the end of scanning process.
A complete scanning report is also generated at the end of scanning process. The scanning report can be obtained into different formats including AFR, XML, HTML, JSON, YAML, Marshal, and Text format.
We can also exclude specific checks from the scanning process. For example, we can exclude all XSS vulnerability tests from the scanning process using the following command.
./arachni http://phptest.vulnweb.com –checks= *, -xss*
Conclusion
Arachni is a useful open source scanner that can audit links, forms, user interfaces, templates, cookies, JSON files, and XML data of all modern and classic web applications. The tool can analyze a number of high level vulnerabilities with custom scanning options.