ATSCAN is a web application scanner that can be used for information gathering and analyzing the security of web applications. The information gathering features include ports scanning, IP addresses and emails collection, and CMS detection. The vulnerability checks cover SQL, AFD, XSS, and LFI vulnerabilities assessment. The tool has inbuilt modules to perform these tasks. Mass dork search, mass exploitation, threaded scans, proxy options, random user agents, random engines are some of the features associated with ATSCAN tool.
ATSCAN Installation
To install ATSCAN, first of all clone the repository using the following command.
git clone https://github.com/AlisamTechnology/ATSCAN
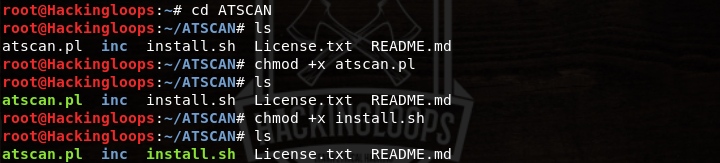
Navigate to the tool’s directory and change permissions for the following files.
cd ATSCAN chmod +x install.sh chmod +x atscan.pl
In the next step, run the installation file (install.sh) to complete the installation process.
./install.sh
How ATSCAN Works
The following command makes the tool up and running in the normal interface mode.
perl ./atscan.pl
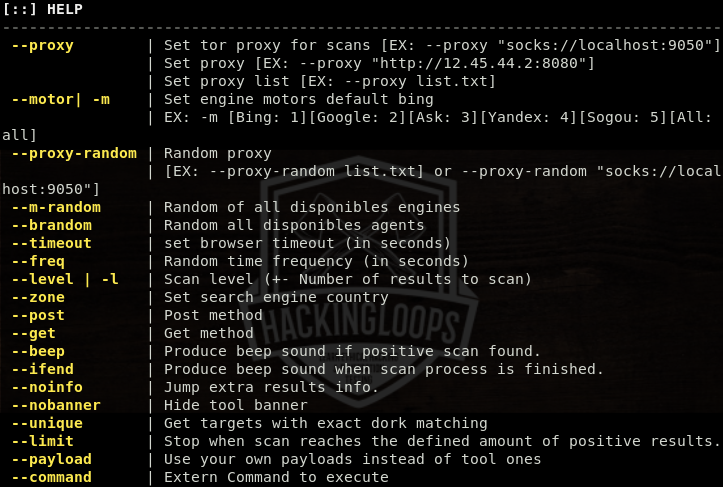
The help command shows all the mandatory parameters and optional arguments supported by ATSCAN.
atscan –h
The help section also shows the format of using the supported arguments. Following is a very basic format of using ATSCAN for scanning purpose.
atscan –t <target here> <optional arguments> <scanning option| module name here>
For example, we can run sql module in the following format to scan the target host.
atscan –t <target here> --sql
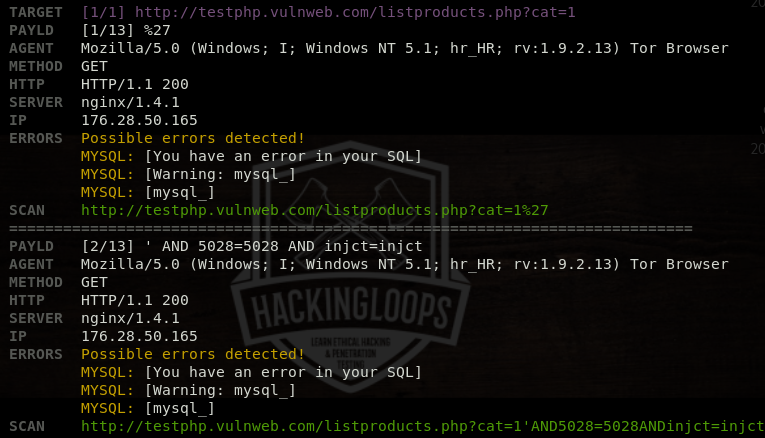
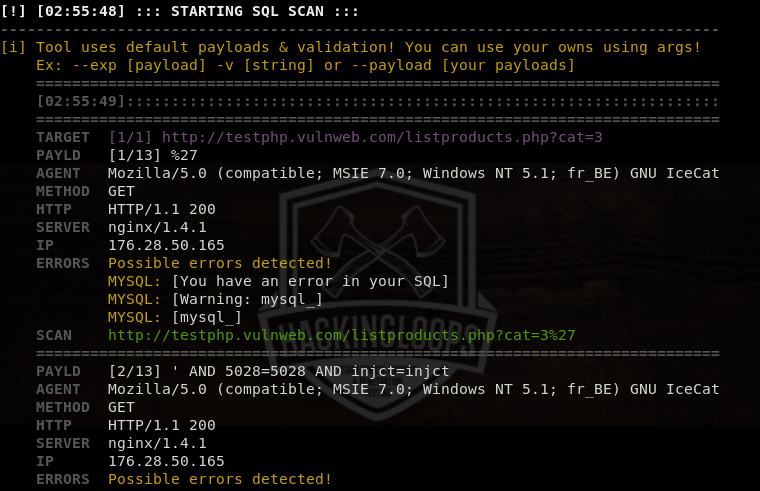
The tool analyzes the target url and displays the results in the following format.
Besides the default interface, ATSCAN has an interactive interface with more customization features to tweak the scanning process. The following command runs ATSCAN in the interactive interface.
atscan –interactive
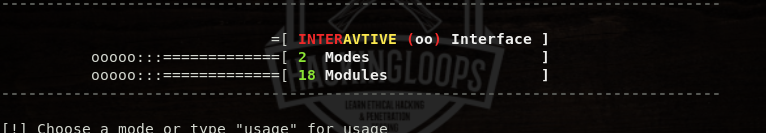
The options argument shows all the available modes in the interactive interface. The interactive interface currently has two modes and more than 15 scanning modules. The two modes are: (a) normal and (b) advanced scanning modes. We can select the desired mode by typing its name in the following format.
use <Mode Name>
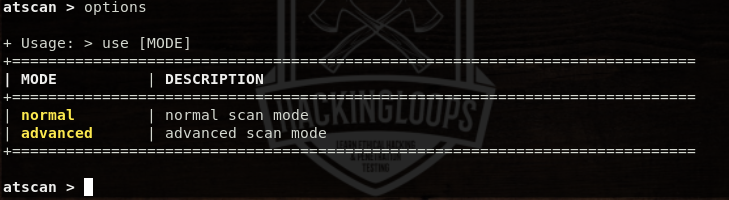
For example, we can select the advanced scanning mode as follows.
use advanced
The options argument shows all the available ATSCAN modules that can be used in the advanced mode. We can use multiple modules at once to get combined scanning results.
options
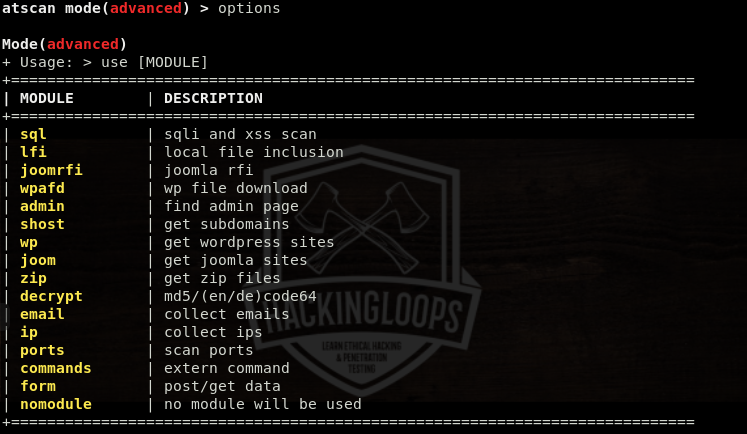
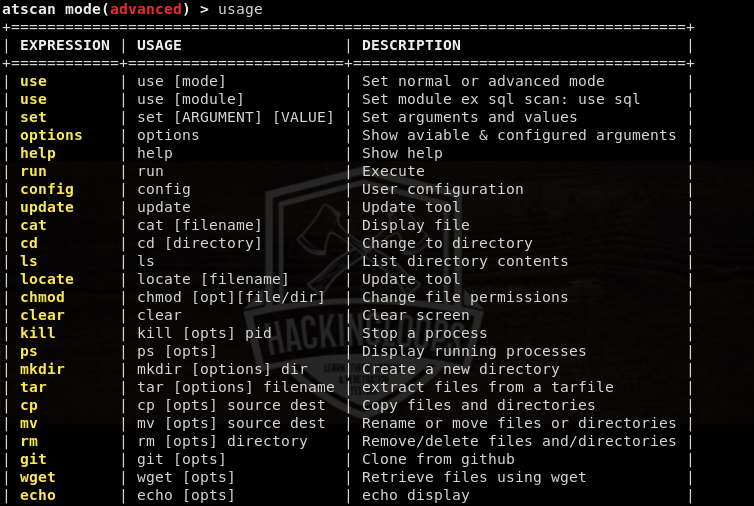
The usage command displays all the necessary arguments required to initiate the scanning process.
usage
For instance, we can select the sql module using the following arguments in the command line.
use sql
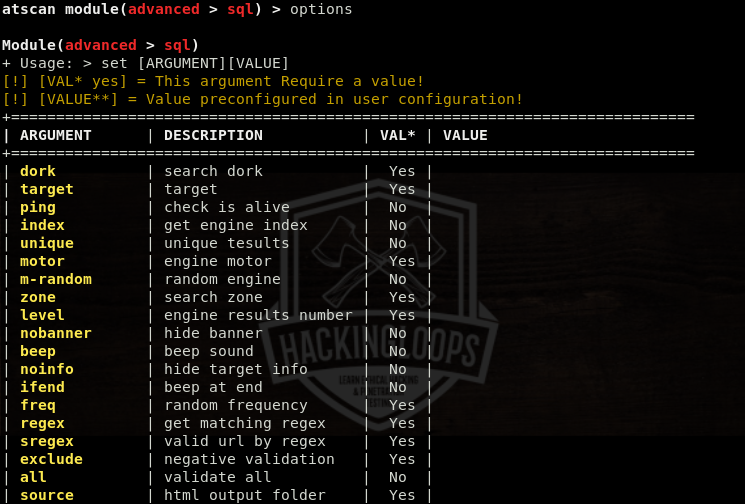
Typing the options, while running the sql module, shows list of arguments in a tabular format.
As we can see in the table, some arguments require values. We can define the values using the following set command.
set <argument> <value>
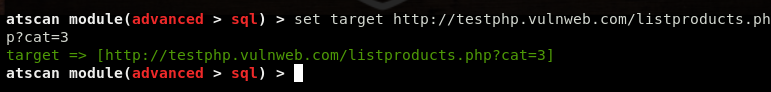
For example, we can set the target value in the following format.
set target http://testphp.vulnweb.com/listproducts.php?cat=3
The <value> column is omitted for the arguments that don’t require any value.
set <arguments>
For example, we can set the ping argument without any value using the following command.
set ping
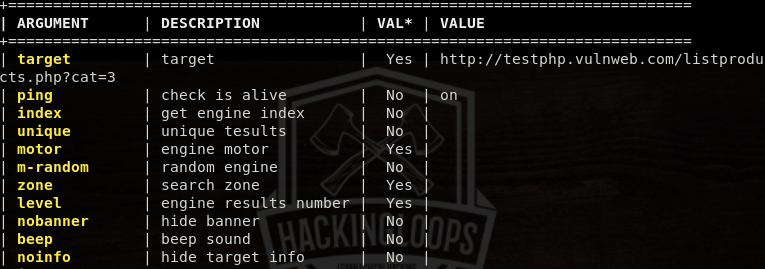
The options command shows the updated arguments table with the defined values for the selected arguments.
options
After configuring the selected module, run the tool and wait for the scanning results.
run
We can set custom payloads for SQL injections in the arguments section. If payload value is not defined, the tool randomly uses the in-built (default) payloads to determine the database security of the target host. If target host is vulnerable, the results are displayed on the screen.
Conclusion
ATSCAN is a decent web application tool with multiple scanning features. The tool offers normal interface for quick evaluation of target applications and interactive interface to fully customize the scanning process.