Malware objectives can be understood through cyber kill chain process. Cyber kill chain is a Swiss army knife for hackers and cybersecurity experts. The model consists of reconnaissance, weaponization, delivery, exploitation, installation, Command & Control (C2), and Objectives cycle. Hackers do reconnaissance to prepare relevant payloads and deliver to target systems. If the security measures are good enough, the malware may not proceed beyond delivery stage. On the other hand, if attackers manage to cross the exploitation step, it is relatively easier for them to go through the rest of Cyber kill chain and perform activities that support the malware objectives. In this article, we will learn about the possible actions of malware after successful delivery and exploitation in Windows operating system (OS). More specifically, we will analyze the behavioral and structural changes in Windows registry, processes, and files system of target OS.
Tools & Setup
When a payload successfully breaches the OS perimeters, we can expect changes in Windows Registry, files system, processes, threads, and network. Since our focus is the analysis of Windows Registry, malicious processes, and suspicious files on a Windows’ system, we require a virtual Windows machine with a sample malware, and the following analytics tools.
- Regshot
- Process Explorer
- Procmon (Process Monitor)
The sample malware can be downloaded from Dasmalwerk.eu database to execute and analyze the Windows activities. Our static malware analysis tutorial provides a complete walk-through about how to download and use malware for such experimental setups.
Window Registry Overview
Windows Registry is a database that contains information, options, and settings related to hardware and software(applications) installed on an operating system. Windows Registry uses the set of keys to manage these settings. These keys can be explored using the Windows utility called regedit.
There are five sets of Windows Registry keys as shown in the following screenshot.
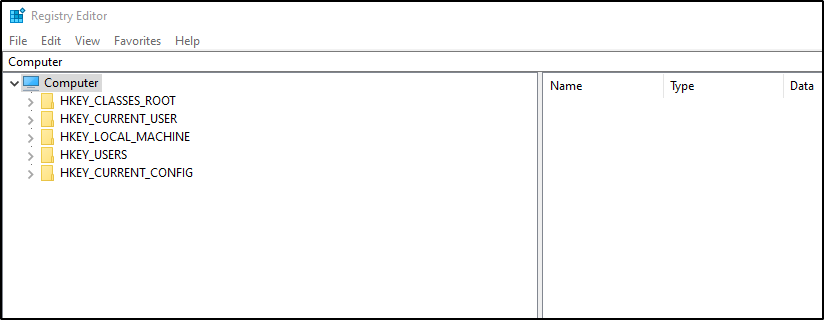
Windows Registry is a favorite target of majority hackers. Hackers can modify the existing keys or add new to the existing architecture to perform the malicious activities, such as hiding malicious programs behind legitimate applications, gaining persistence, etc.
Windows Registry Analysis
In this tutorial, we are using the Regshot tool for Windows Registry analysis. Regshot can detect changes in Windows Registry keys and values. The tool can compare the pre-malware and post-malware execution states of Windows Registry database. This capability helps in analyze what exact changes are made in Windows Registry by the malicious program. The tool can be downloaded from the following repository.
regshot download | SourceForge.net
After downloading, run the Regshot tool by clicking the Regshot executable file.
This opens the Regshot dashboard.

The buttons highlighted in the red dialog box are used to capture the Windows Registry images for comparison. First, we will click on the 1st shot button before running the malware. This action will capture and save the pre-malware execution state of Windows machine. After this, we will execute the sample malicious file. Now can capture the post-malware execution state by clicking on the 2nd shot button. Once both Registry states are captured, we can launch the compare button to analyze the changes. The comparison will automatically create a Text/HTML file showing all the Windows Registry manipulations made by the malware. For example, the current malware sample added 15 new Registry keys under different Windows programs.
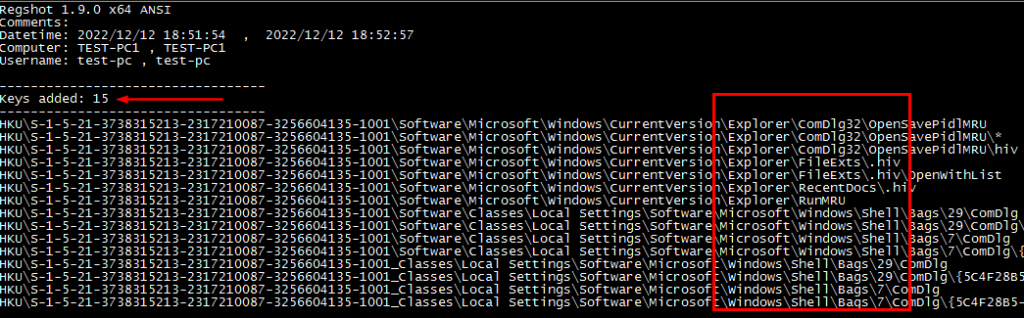
The malware added 50 new values to the Registry hives as shown in the following screenshot.

The malicious program not only added new keys and values but also modified the existing Registry values.
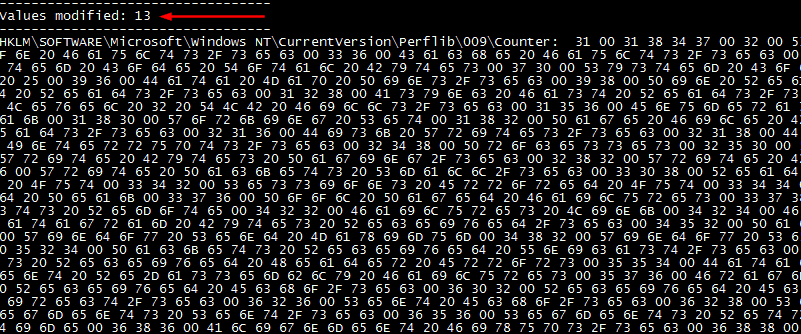
The execution of the current malware made a total of 78 changes to the existing Windows Registry structure. These huge number of changes show the importance of Windows Registry for hackers.
Processes and Files System Analysis
We can further explore malware behavior by analyzing the Windows processes. There are multiple tools available that can be used for this purpose. The most simple and advanced level tool is Process Explorer. We can download this tool from Microsoft using the following link.
https:// learn.microsoft.com/en-us/sysinternals/downloads/process-explorer

After downloading, unzip the tool and run the executable file. This action will open the Process Explorer dashboard as shown in the following screenshot.
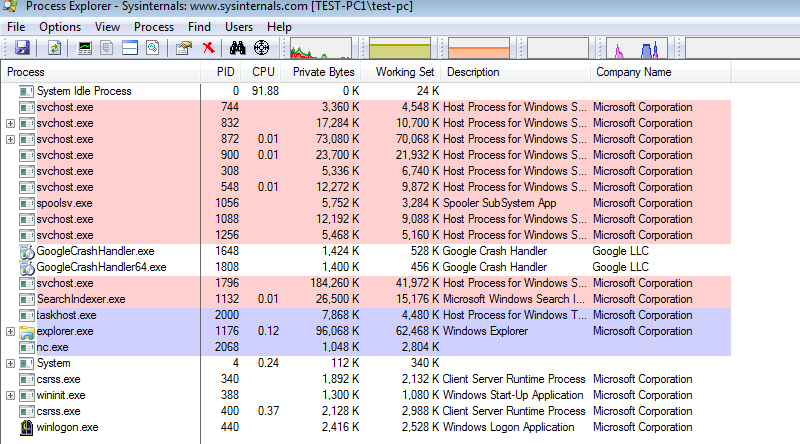
The left windowpane of the Process Explorer shows all the running processes. The right screen shows processes’ details, such as process id, process description, process volume (bytes), and the company/vendor name. Since malware may not necessarily appear in this list of processes with similar name, we must look for all processes that look suspicious.
How to Identify Malicious Processes
Although the analysis at this stage depends on the instinct and experience of the analyst, we can follow certain rules that can help us to identify malicious or potentially harmful processes. For instance, we can look at the processes that consume very high memory during their execution. We can look for processes with no description. Processes without verified publisher can also be interesting.
The Process Explorer offers multiple filters to narrow down the malicious or suspicious processes. These filters can be applied by navigating through view>select columns tabs.
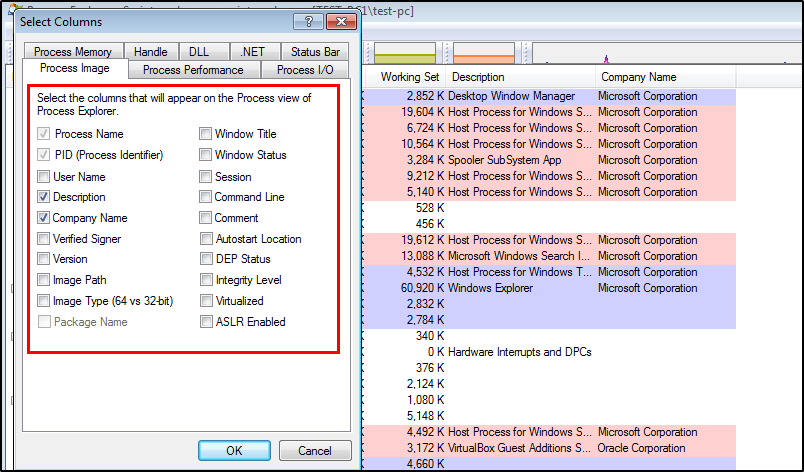
Command line, autorun location, and verified signer are important filter parameters as they can be very helpful. The command filter can identify the commands that launch the malicious process. The autorun path can tell us the exact path/origin of the process. Similarly, the signing authority can help in determining the source behind the running processes. A process without signing authority should be analyzed carefully.

Files System Analysis
When a malware infects a machine, it can create, modify, or delete the files on target operating system. Process Monitor (procmon) is another useful tool that can monitor these changes. The tool can be downloaded from the following link.
www.learn.microsoft.com/en-us/sysinternals/downloads/procmon
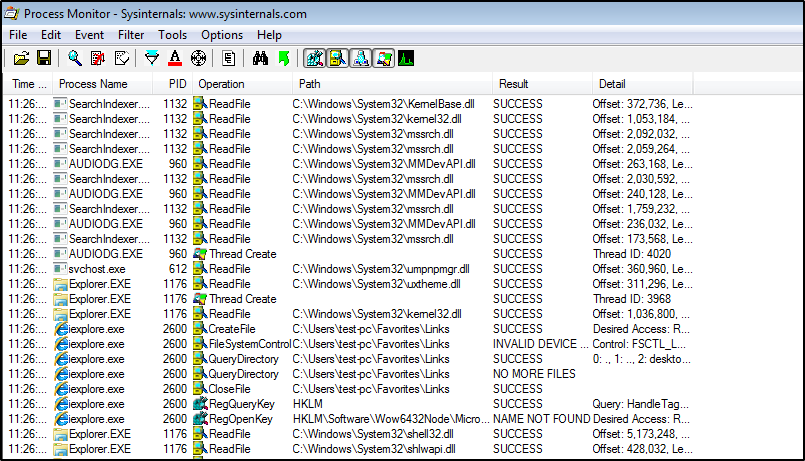
The Process monitor tool captures all active events and display them on the screen.
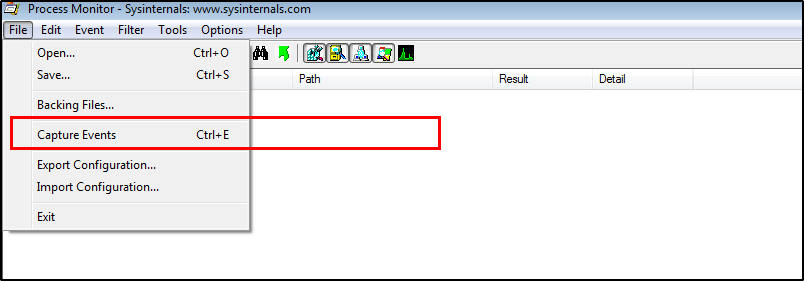
We can clear the current events from the dashboard using the clear screen option.

Now we can restart the events capturing and run the malware.
Soon after executing the malware, stop the events capturing process.
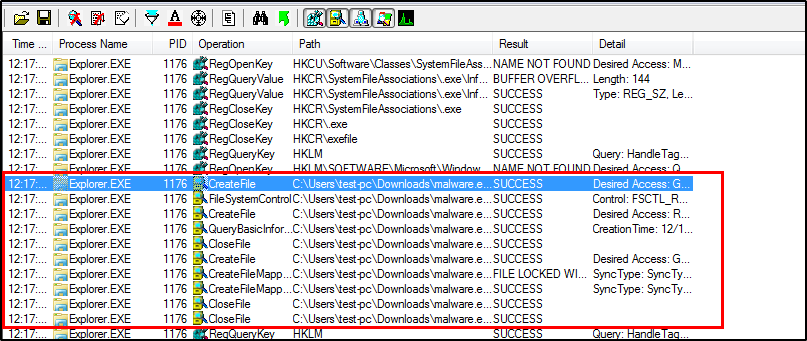
This action will capture most of the processes that are related to malware activities. We can find the malware related processes through Edit>Find option. The following screenshot shows changes related to files system, such as creating and closing files. The processes detail column shows the files access rights for the malware.
Conclusion
Static malware analysis provides limited hints about malicious programs. We can determine the true functionality and goals of a malware through dynamic analysis. The dynamic analysis is only possible by running the malicious programs in controlled environment. The tools like Regshot can be handy to determine the Windows Registry activities of the malware. The Regshot tool may fail in scenarios where we encounter fileless malware. In such situations, the Process Explorer and Process Monitor tools can become handy

Leave a Reply