Forced browsing is a type of web attack where the adversary tries to access web resources that are not referenced or displayed by the web application. These resources are usually hidden web directories and files that may contain interesting information from hackers’ perspective. Gobuster, Ffuf, and Feroxbuster are some useful tools with forced browsing capabilities. In this article, we are going to learn how to use the Feroxbuster for such attacks.
The Feroxbuster applies the brute-force technique combined with some powerful wordlists to explore the unlinked or hidden content from target web applications. The tool comes with a number of built-in filters and switches to get the best results.
How to Install Feroxbuster Tool?
There are multiple Feroxbuster installation options available for Linux distributions. One simple method is to download and install the (.Deb) package. Go to the Feroxbuster release page and download the latest (.Deb) version using the following (wget <latest .deb url>) command.
weget https://github.com/epi052/feroxbuster/releases/download/v1.11.0/feroxbuster_amd64.deb.zip
Unzip the downloaded package as follows.
unzip feroxbuster_amd64.deb.zip
The Feroxbuster (version 1.10.3) dependencies can be checked before installation using the following command.
dpkg -I feroxbuster_1.10.3_amd64.deb
The following command installs the Feroxbuster from its .Deb package.
sudo dpkg -i feroxbuster_1.10.3_amd64.deb
How Feroxbuster Configuration
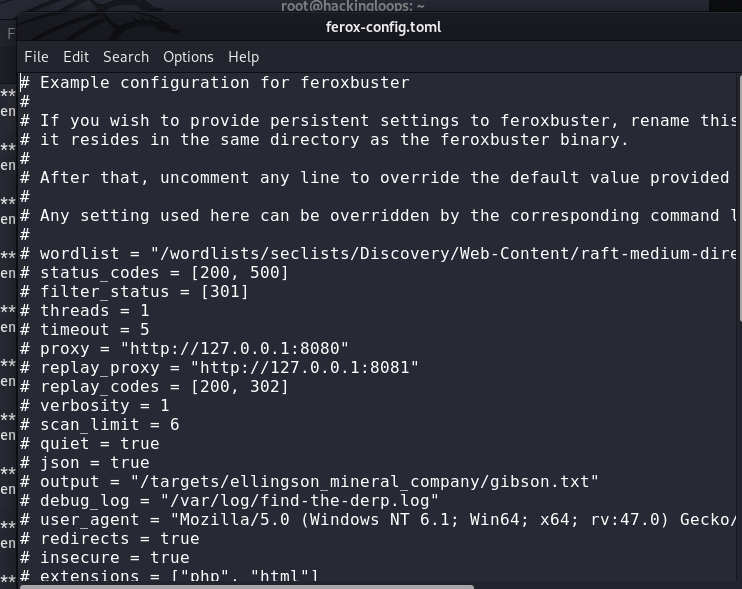
Feroxbuster has a (ferox-config.toml) configuration file at /etc/feroxbuster/ location. The following screenshot shows the default settings listed in the file.
The default configurations can be overridden by uncommenting the predefined settings in the file. The Feroxbuster uses the Seclists’ wordlists to carryout the Bruteforce operations. We can either define our own wordlist paths or use the default settings. The default configuration requires the Seclists files for brutecorce tasks. The Seclists is a collection of wordlists files containing usernames, passwords, web shells, data patterns, fuzzing payloads, etc.
The Linux users can install the Seclists using the following command.
apt -y install seclists
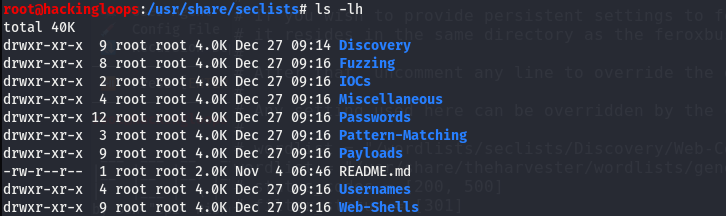
All Secists Wordlists Directories:
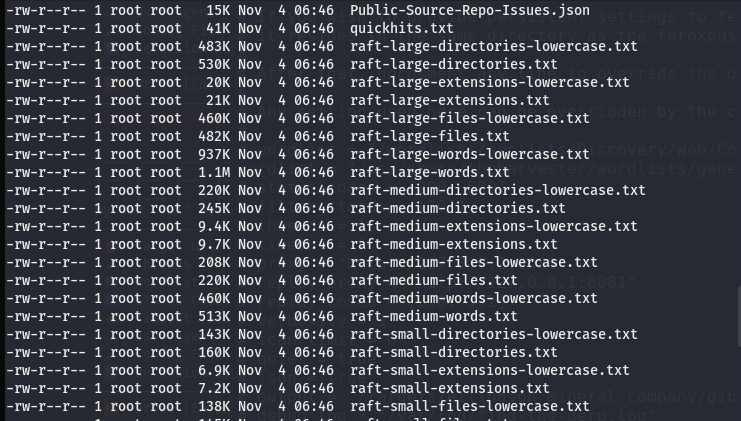
Web-Content Wordlists Files:
How Feroxbuster Works?
After configuring the Feroxbuster, we can run it using the following command.
feroxbuster -u <target URL> <optional flags>
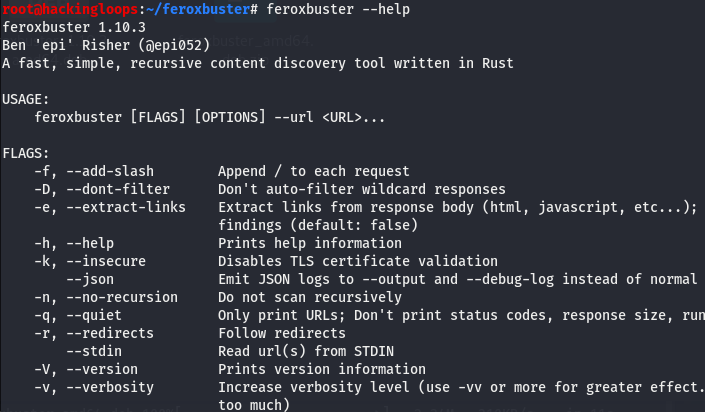
All the options and available flags can be explored using the help command.
feroxbuster --help
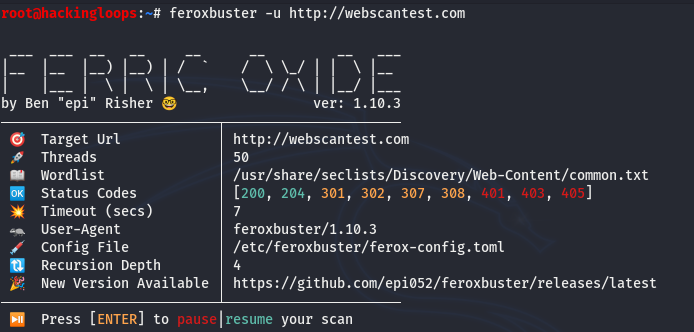
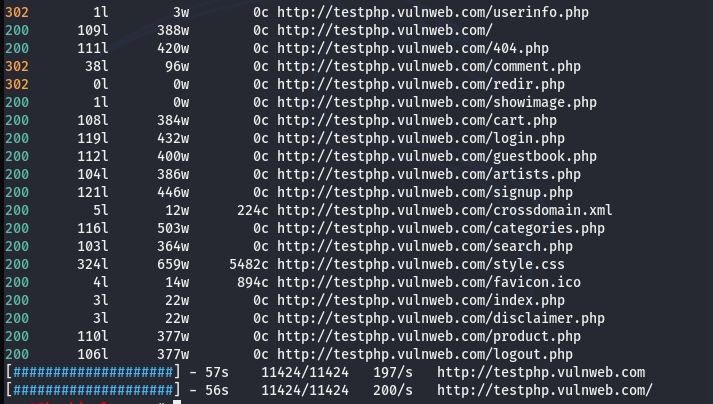
Following is a global forced browsing example without any flags used in the command.
feroxbuster -u http://webscantest.com
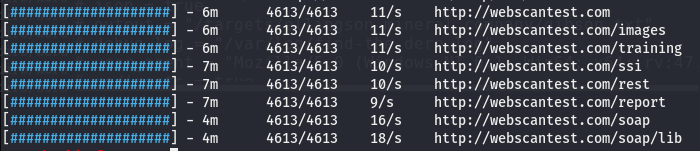
In the absence of additional parameters, the tool searches for all the traceable directories and fetches the results as shown in the following screenshot.
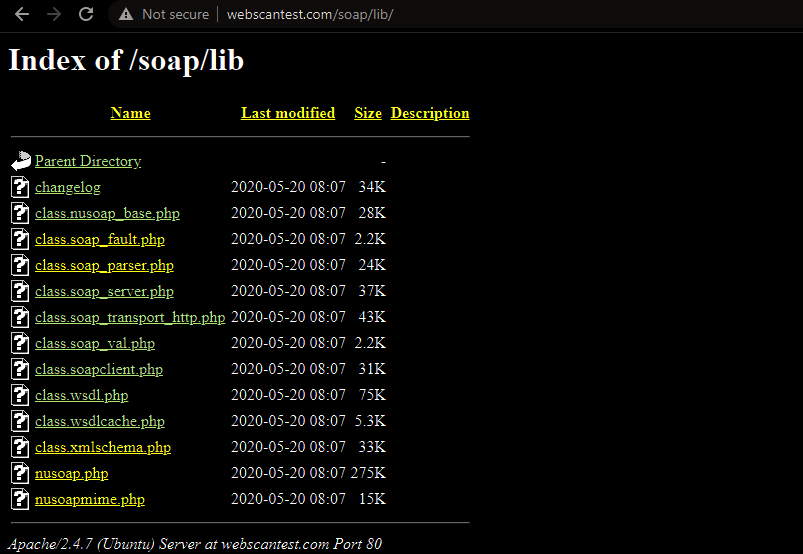
We can manually explore the discovered directories to find interesting files and content from the gathered resources. The following example screenshot demonstrates the discovery of unlinked SOAP (Simple Object Access Protocol) library with interesting content.
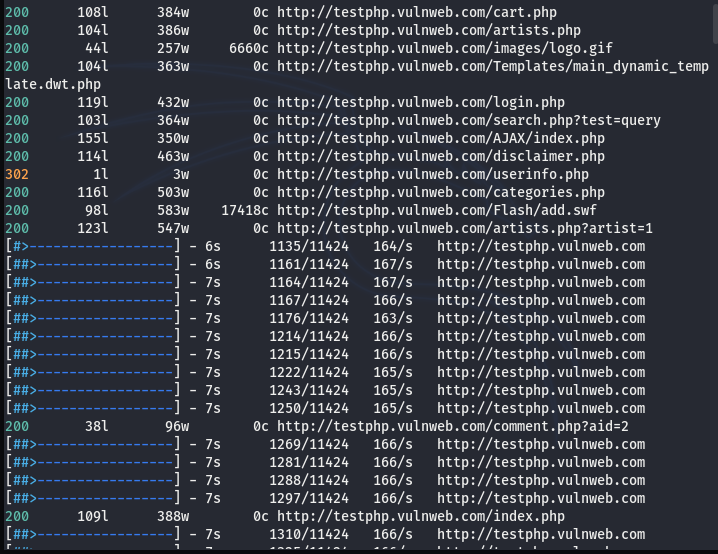
As mentioned earlier, the Feroxbuster has a number of optional arguments to finetune the browsing process. For example, we can force the tool to discover the directories and extract the links automatically using the following command.
feroxbuster -u http://testphp.vulnweb.com --extract-links
The Feroxbuster has an interesting filtered proxy feature. Instead of proxying everything, we can select certain response codes to go through defined proxies. For example, we can run a proxy for the 200 & 302 response codes using the following command.
feroxbuster -u http://testphp.vulnweb.com --replay-proxy http://webscantest.com:80 --replay-codes 200 302
FeroxBuster Filters Examples
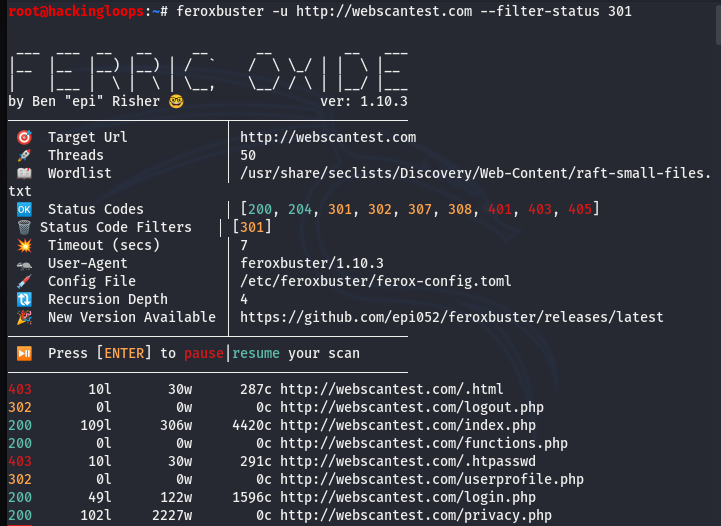
The Feroxbuster has a number of useful filters to modify or customize the scanning results. The tool supports all major web status codes for scanning purposes. We can drop certain status codes using the filter-status argument.
feroxbuster -u http://webscantest.com --filter-status 301
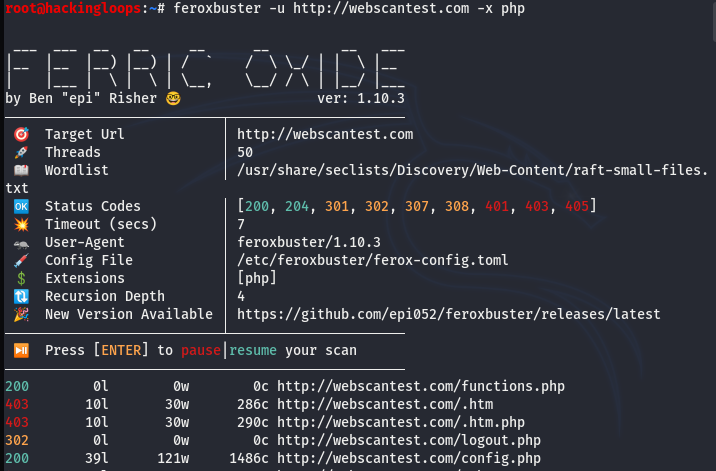
We can program the tool to display certain file extensions while scanning, using the respective (-x) flag.
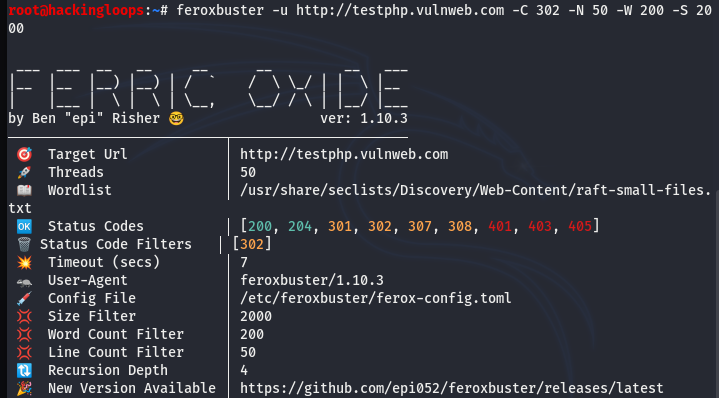
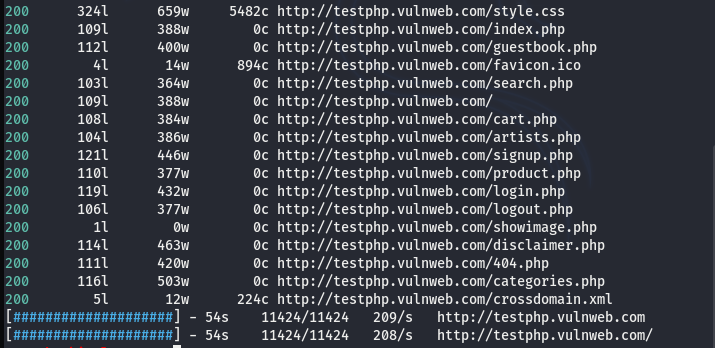
The Feroxbuster allows the use of multiple filters in a single command. In particular, we can filter certain response codes (-C), page size (-S), lines (-N), and words (-W) to exclude from the scanning process. For example, we can drop the content with the following defined values from the final results.
Status Code (-C)= 302
Number of Lines (-N)= 50
Number of Words (-W)= 200
Byte Size (-S)= 2000
The record shows no results containing the aforementioned filtered values.
CONCLUSION
The Feroxbuster is a fast and easy to use content discovery tool. The reply-proxy, rich filters and the ability to scan multiple targets in parallel are the strong features of the Feroxbuster. The tool, however, lacks some interesting features in other similar tools. These features include virtual host scanning, DNS scanning, time delay options, and wordlists-STDIN support.