There are many crimes where computer technology is either a target or play the role of a facilitator. Phishing, identify theft, e-financial frauds, ransomware attacks, publishing online derogatory material, and e-money laundering are some examples. Digital forensics deals with such crimes to find the evidence from digital artifacts by following the standard digital Forensics procedure and the forensics toolkit is the way to accomplish this.
Although there are several models followed in digital Forensics investigation, the basic steps are identical for each model. These include identification, collection, analysis, interpretation, and documentation of the digital evidence in admissible form. To ensure the acceptability of the evidence, it is important to use Forensics tools that have worldwide acknowledgement. The FTK imager is one such digital Forensic tool that is used for data collection and evidence analysis. In this tutorial, we will do a detailed analysis of FTK imager by demonstrating the tool’s installation and core working process.
How to Install FTK Imager
FTK imager is a product of ACCESSDATA that can be downloaded from their official website.
To proceed with the download option, ACCESSDATA requires a valid email to send the download link to user’s mailbox so they can get started with the forensics toolkit.
After downloading the executable file, run the Wizard to begin the FTK installation process.
It can take some time to complete the installation process.
FTK Imager Dashboard Overview
After installing the forensics toolkit FTK Imager, open the tool from the start-menu, programs list, or Desktop shortcut created during the installation process. The following screenshot shows the FTK Imager dashboard.
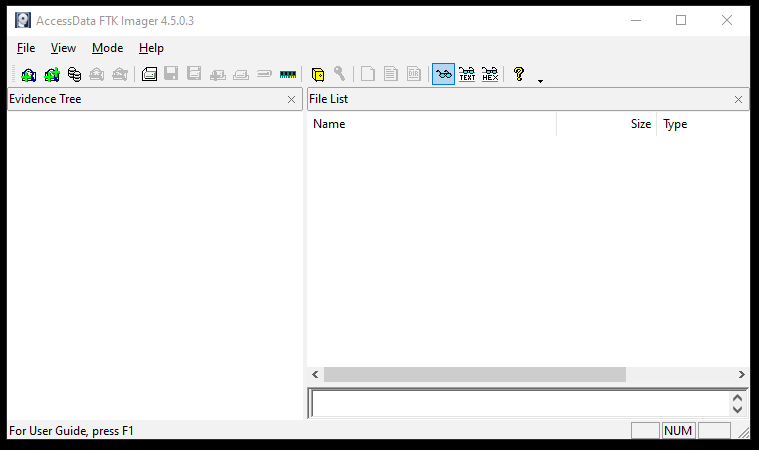
There are two sections of the tool. The left section (Evidence Tree) Shows all the potential evidence data. The right section (File List) gives an insight about each file selected in the Evidence Tree section. The top menu bar shows all tool options used for data extraction and analysis purpose.
How FTK Imager Works?
FTK imager can be used to perform multiple Forensic tasks, such as creating a disk image, capturing data in the OS memory, image mounting, or obtaining system protected documents, such as user credential (SAM) files. Let’s explore some of these features in detail.
How to Create FTK Disk Image: Creating an image of potential evidence is the most important task in digital Forensics. An image is created to acquire duplicate copies of the original evidence and preserve the original one. It is important to mention here that Forensic analysis is done on the duplicate copies (images) instead of original evidence. This is to ensure the integrity and availability of the original evidence whenever required. We can create disk image through File>Create Disk Image option as shown below.
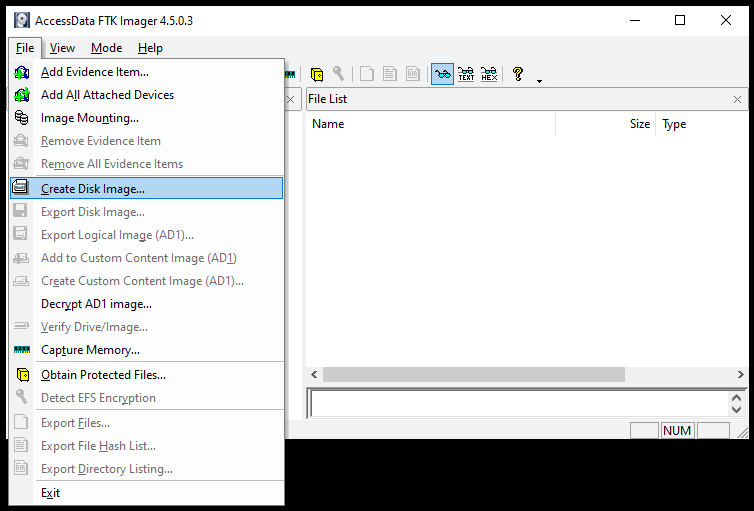
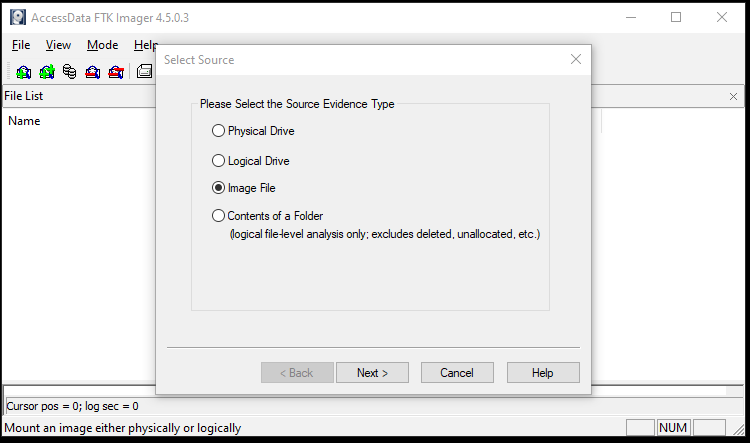
The tool asks to select the source evidence type to create the Disk image. FTK Imager supports the following Evidence source types
- Physical Drive
- Logical Drive
- Image File
- Folder Contents
- Femico Device
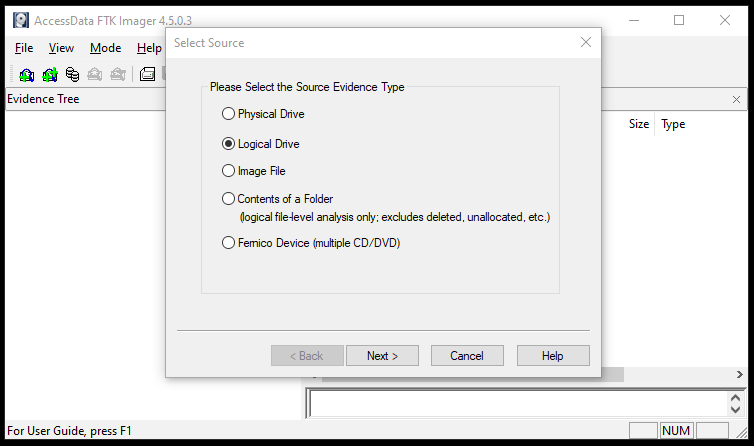
Physical drive can be any physical drive, device, or media containing the evidence. The logical drive is the logical space on the existing system. An image file can be an existing Forensic image file. Beside these, FTK Imager also supports the Folder content and CD/DVD media to create the image. In this tutorial, we create an image from the logical drive named as Hacking Loops.
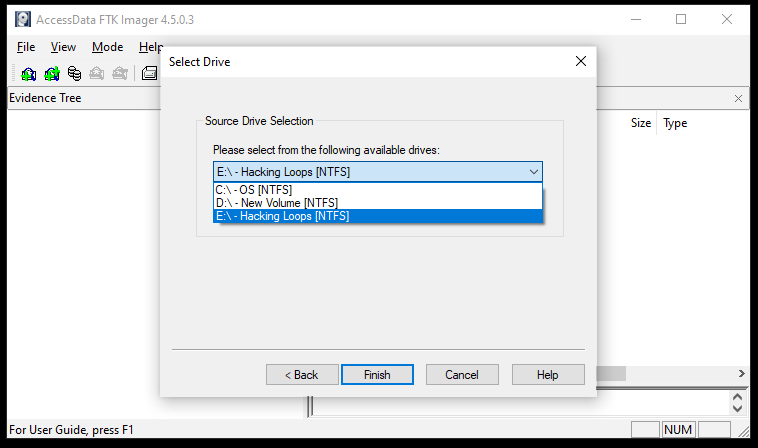
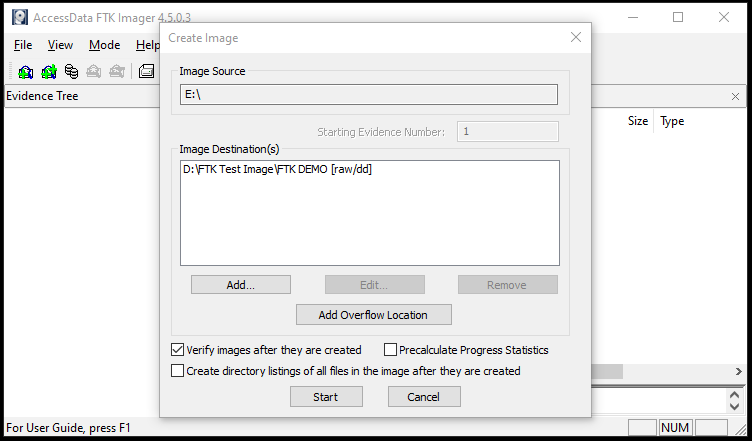
Once the source is selected, the forensics toolkit FTK Imager asks for destination path to create the disk image. The destination path must not be the same as the source path. This can be achieved by clicking on Add option from the pop-up window as shown below.
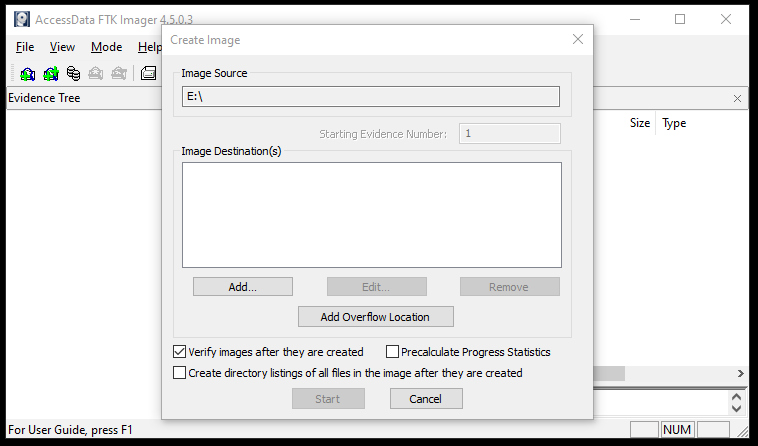
Before taking the destination path argument, the tool asks to select one of the following image formats for the target Disk image.
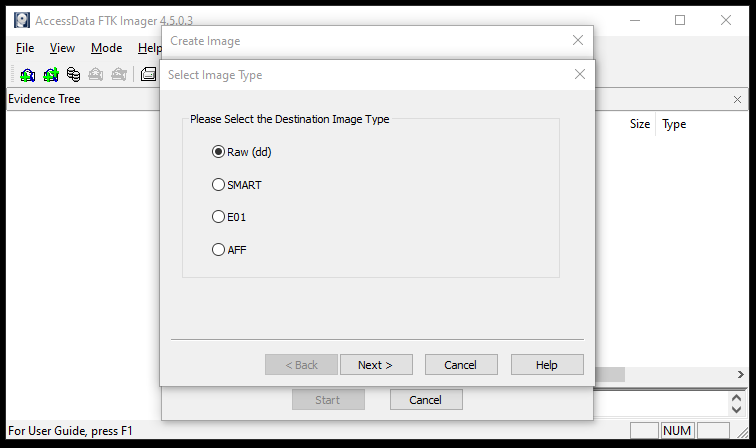
The Raw format is the bit-by-bit copy of the evidence without any alterations. The Smart format is Linux supported format. The E01 is the Encase image format. Encase is a famous digital forensics tool. The AFF is the Advanced Forensic Format supported by majority of the digital forensics tools. In the next step, provide evidence item information, such as case number, evidence number, examiner name, evidence description, and notes.
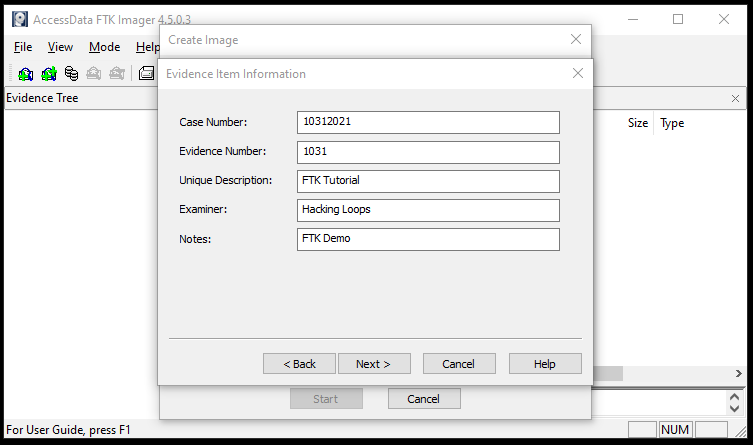
After filling the evidence item information form, the tool displays the pop-up window to provide the destination location and name for the image.
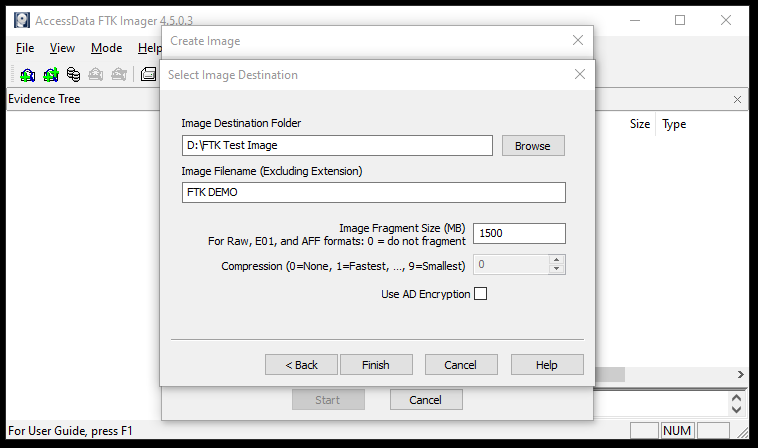
Click on the Start option to begin creating the image. Also select the image verification option to validate the image file after creation.
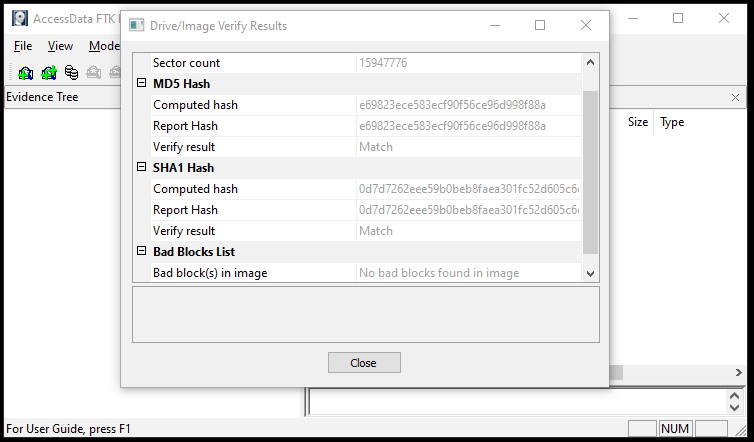
After successful creation, image hashes are automatically generated and compared with the source hash to validate the image.
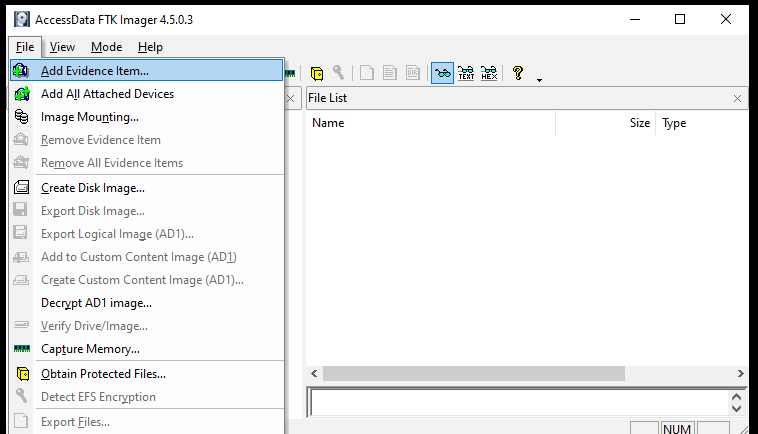
How to Analyze Evidence Image: Analyzing an FTK image is a pretty simple process. Click on Add Evidence File option from the File menu.
Select the evidence source type.
Since we have copied the image file on the hard drive, the tool asks for source drive selection.
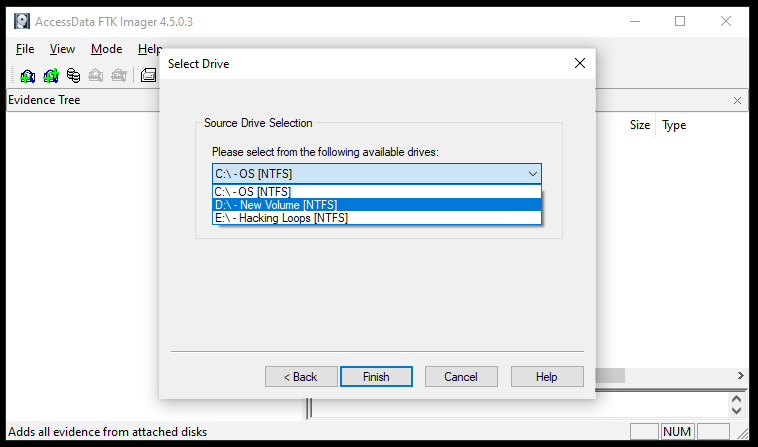
Click on the Finish button after providing the source file type and destination. The above action opens the evidence image in FTK as shown in the following screenshot.
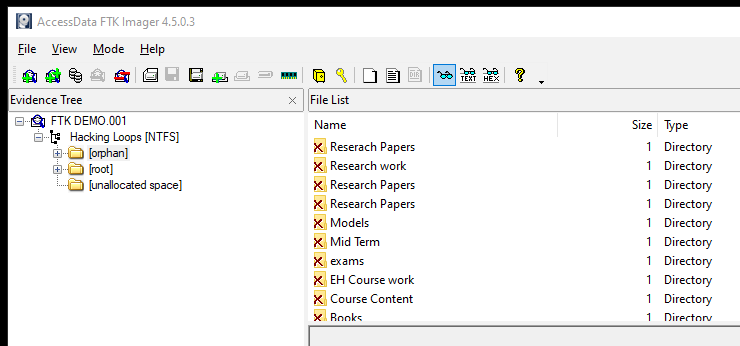
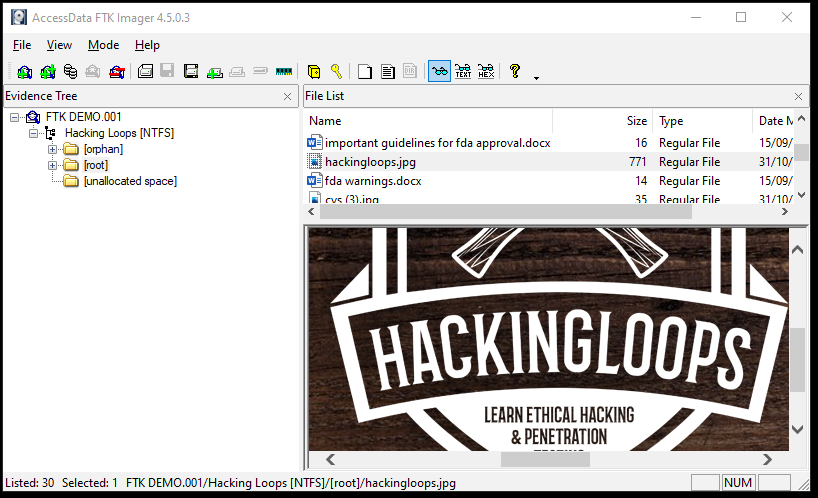
Explore the orphan and root directories to go through different files and documents of interest.
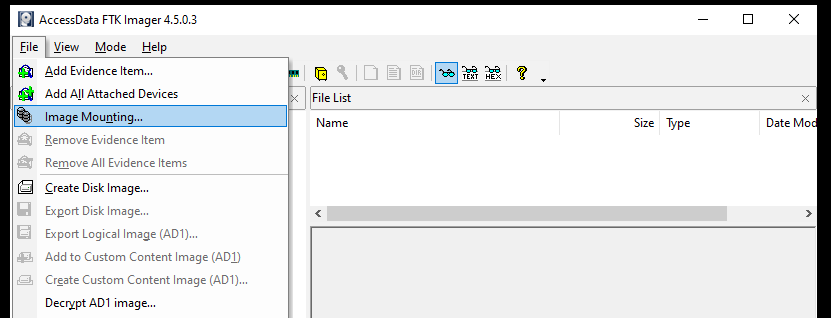
How to Mount an Image: Click on the Image Mounting option from the File menu.
Select the image file from the source location. Also select the mount type and method. FTK imager allows mounting an external image file to the system as Physical and logical drive.
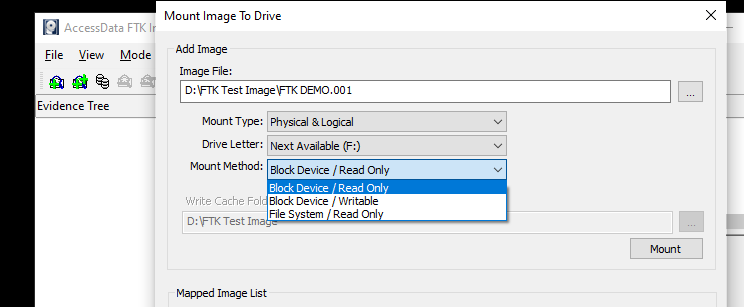
The FTK imager also offers write blocker feature to the image file by selecting the Block Device / Read Only from the available list of options. This feature blocks any modification the image file mounted as a logical drive to the current operating system.
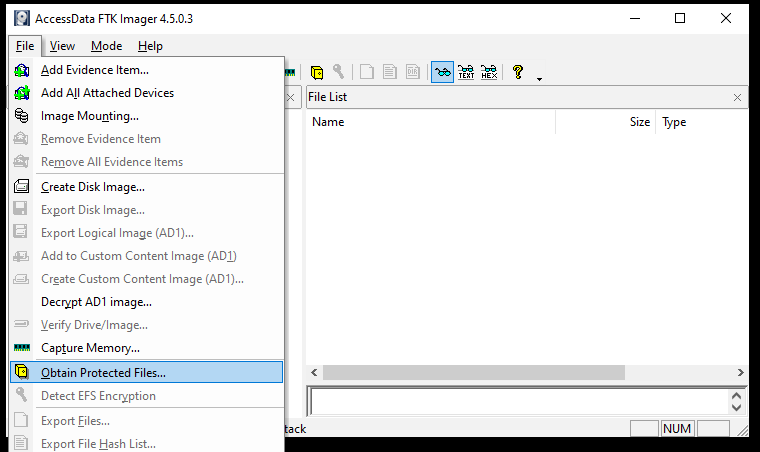
How to Extract Protected Files Using FTK Imager: FTK Imager has a unique feature of extracting protected directories like SAM files from a live system. These files are not easily accessible to the users. Click on the Obtain Protected Files option in order to get the protected files.
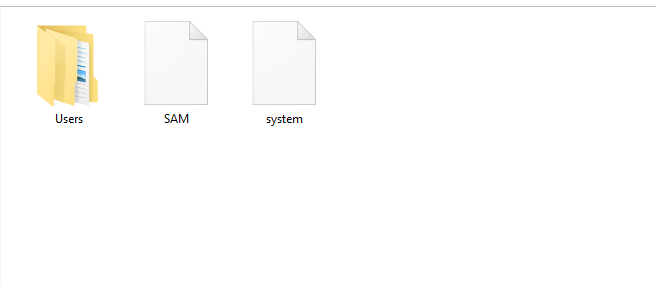
The FTK Imager extracts all the protected files in the following format. The SAM files can be passed on to the hash cracking tools like Hashcat and John the Ripper to crack the secret credentials.
Conclusion
FTK Imager is one of the few Digital Forensic tools that has rich Forensic features with worldwide acceptance. The tool is not only good in making images of the potential evidences but also useful in analyzing the evidence image files.

Leave a Reply