You didn’t think we meant your actual house did you? No the application house is absolutely something you must know about if you are in to hacking mobile devices. Below we walk you right through how to use the House application so let’s get into the details.
House is an open source runtime mobile application analysis toolkit powered by Frida. Frida is a cross-platform dynamic console framework that is used to perform different kinds of dynamic tests, such as function hooking and interception of function calls of android devices. Such assessments require tedious tasks of writing and injecting Frida scripts into the work environment either through Frida’s command-line tools or self-contained tools that support Frida’s client APIs. House toolkit simplifies such android assessments by offering a web GUI to the users and taking care of Frida scripts. The toolkit allows the users to automatically generate Frida scripts and perform the aforementioned android security assessments i-e function hooking, intercepting, enumeration, and monitoring tasks.
House Installation
House is an open source toolkit written in Python that can be cloned from Github using the following commands.
git clone https://github.com/nccgroup/house
pip install pipenv
pipenv install
pipenv shellor
mkvirtualenv --python=/usr/local/bin/python3 house
workon house
pip install -r requirements.txt
The requirements.txt file contains the following packages required by House to function.
flask
colored
frida
jinja2
requests
flask-socketio
flask-login
ipython
How House Works
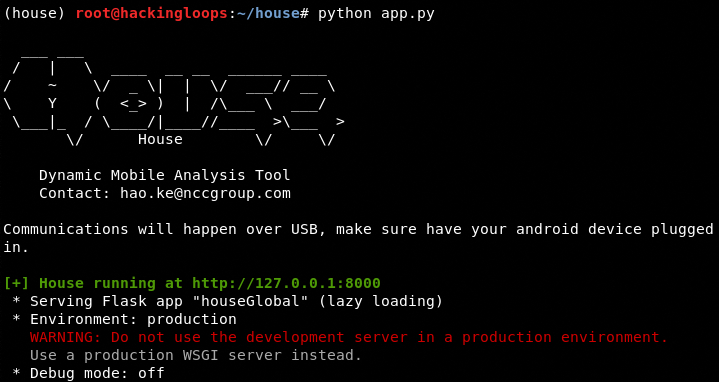
In order to assess the android device, make sure a rooted android device is plugged into the USB port of the OS running the House toolkit with Frida server running on the device. House toolkit can be set into operational mode by navigating to the tool’s directory and running the following command.
python app.py <PORT>
The default port used by the toolkit is 8000. The above command can be written in the following format.
python app.py 8000
Now open the web browser and type the following default address to open House dashboard.
127.0.0.1:8000
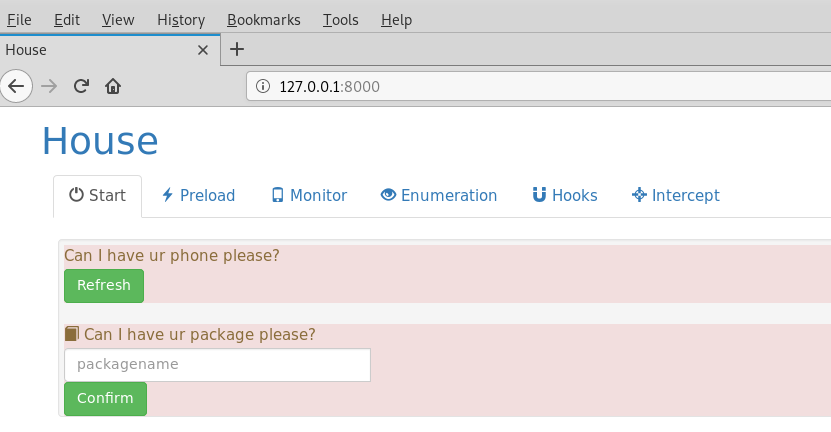
The following screenshot shows default House interface. The
The default start page of the toolkit shows the information about the connected android device. Run the following command in the terminal to confirm the running of the Frida server on the android device.
frida-ps -U
The –U argument represents the Universal Serial Bus (USB) of the OS. Frida server waits for the USB device to be picked up by the OS and read by the server. Once the Frida server is successfully spawned, the device status appears on the start page of the House toolkit. We can then perform the desired assessments of the connected android device. For instance, we can assess the android package by mentioning the package in the packagename field on the start page of House toolkit.
House Features
The House UI provides the following key features by automatically generating the Frida scripts and implementing them.
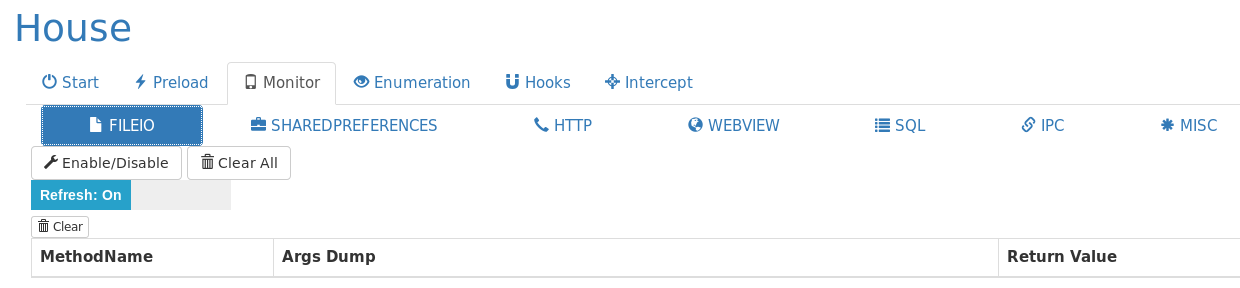
Monitor
House can monitor important android operations like FILEIO, IPC, Webview, SQL, HTTP etc. It can dynamically generate hook scripts from the templates.
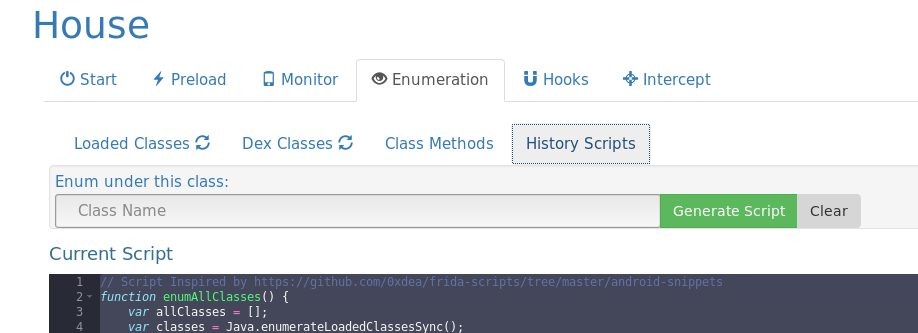
Enumeration
The toolkit can perform the following four types of enumeration.
Enumeration of all loaded classes
Enumeration of all classes in the DEX file
Enumeration of all methods in a given class
Enumeration of history scripts
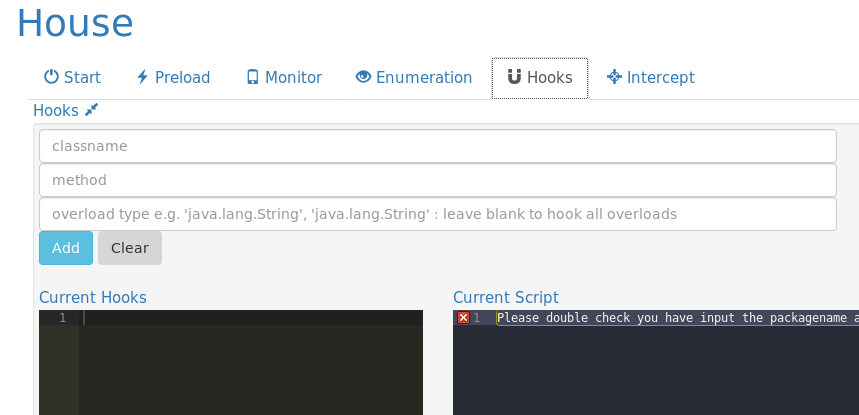
Hooks
House supports multiple functions tracing and tweaking of the generated scripts.
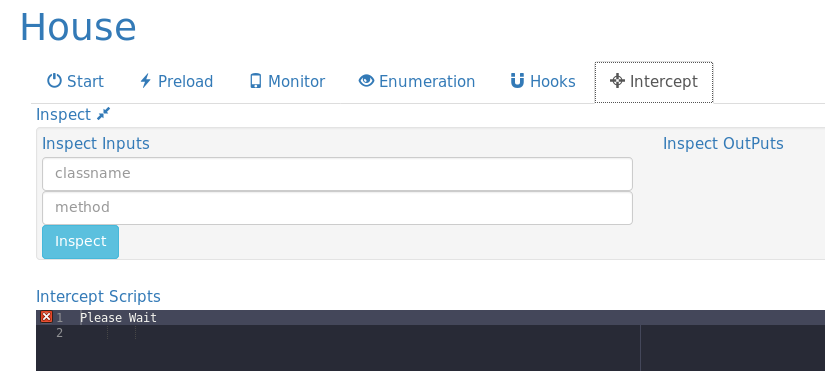
Intercept
Intercept is another important feature of House that allows the users to intercept the live function calls. The toolkit can make use of the hook snippets, interception UIs, and live REPL to inspect the live function calls and interdict them.
Conclusion
House toolkit simplifies the job of the security researchers by providing a web GUI that automatically generates the complex Frida scripts and performs the security assessment of android devices.