Raccoon is an open source web application tool used for reconnaissance and information gathering purpose. Raccoon can obtain DNS information, WHOIS details, TLS data, directories information, sub-domains record, Web Application Firewall (WAF) information, and open ports statistics. The DNS visual mapping is also provided by the tool through DNS dumpster utility. TLS is a transport layer security protocol used for providing end-to-end communications security. It contains information about the supported ciphers and certificates used by the web applications communicating with each other. Raccoon can extract this information along with the TLS version being used by the applications. Moreover, Raccoon can retrieve the following data from the target web applications.
- The type of Content Management System (CMS).
- The information about Web server hosting the web applications.
- Retrieval of Robots.txt and sitemap data (if exists).
- Extraction of fuzzable urls.
- Discovery of HTML forms.
- Email addresses record.
- Cookies information.
- s3 bucket vulnerability.
Raccoon Installation
Raccoon is a Python tool that requires Python 3.5 or higher to work. In order to install Raccoon, first we need to clone the tool from Github using the following repository path.
git clone https://github.com/evyatarmeged/Raccoon.git
In the next step, open the Raccoon directory to run the setup file as shown below.
cd Raccoon python setup.py install
Also run the requirements.txt file from the terminal to install the required dependencies.
Pip3 install –r requirements.txt
Besides the dependencies mentioned in the requirements.txt file, Raccoon requires asyncio library. Install asyncio using the pip command if it is missing.
pip install asyncio
Raccoon Working
Raccoon can operate from terminal by running main.py file from the source directory in the following format.
Python3 main.py [options] <target web application>
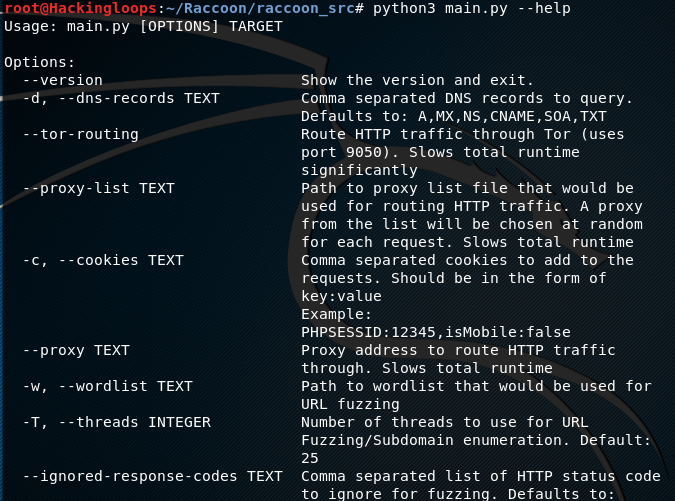
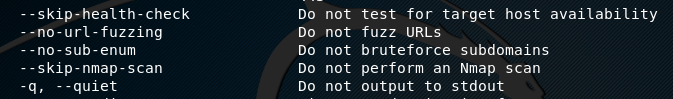
To view all the available options, type the following help command.
python3 main.py --help
Running full scan on the target web application without optional parameters can be achieved in the following manner.
python3 main.py <target web application>
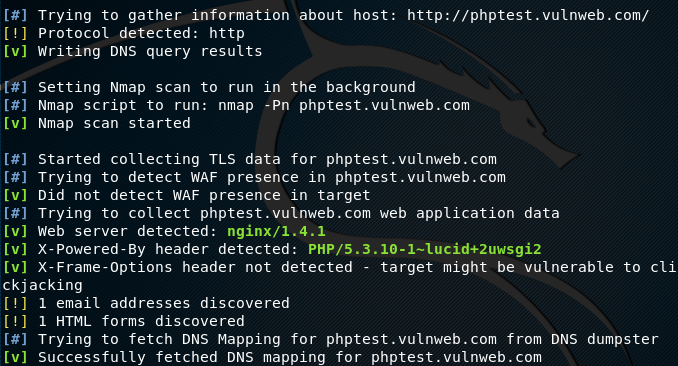
For example, we can run Raccon on the test website [phptest.vulnweb.com] in the following format.
python3 main.py http:// phptest.vulnweb.com
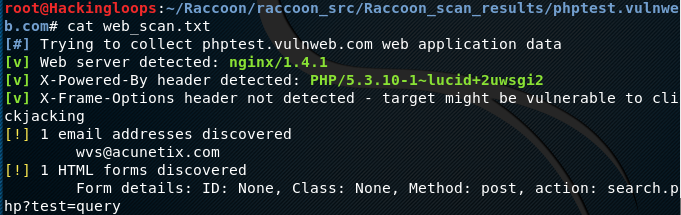
Raccoon starts fetching the information, such as DNS records, ports, TLS data, WAF information, server details, HTML forms, and email addresses. The tool also looks for vulnerabilities like X-Frame-Options header that can be exploited by the adversaries.
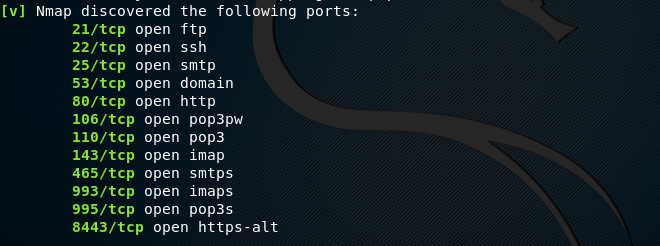
Raccoon uses Nmap to discover open ports and the associated services as shown in the following screenshot.
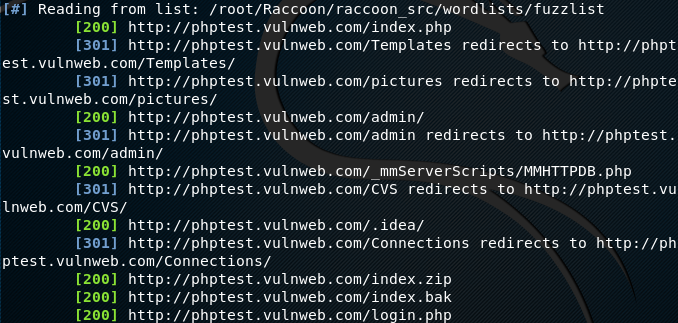
The fuzzing of urls is performed in the following format.
Raccoon stores the scanning results in a folder in the same directory. The results are stored in separate text files for each Raccoon utility.
We can analyze the text files data in the terminal using the cat option. For example, the web_scan.txt file data can be visualized in the terminal in the following manner.
cat web_scan.txt
Alternately, we can view the scan results by moving into the results folder and opening the desired text file.
We can refine the information gathering process by including or excluding certain tests from the scanning process by introducing the optional parameters. For instance, we can skip the url fuzzing test from the scanning process by declaring the no-url-fuzzing parameter.
python3 main.py no-url-fuzzing http:// phptest.vulnweb.com
Conclusion
Raccoon is a useful OSINT tool that can perform reconnaissance and information gathering tasks. The tool supports Tor and proxy settings to bring anonymity to the scanning process. The use of asyncio library improves the overall performance of the tool.