XeroSploit is a network penetration testing framework that performs various penetration testing activities, such as sniffing, network mapping, ports scanning, and simulating cyber-attacks including Denial of Service (DoS), HTML code injection, JavaScript Code injection, DNS spoofing, and manipulating web pages content (defacement).
XeroSploit Installation
XeroSploit is a Python tool that requires the following packages and tools to operate.
- hping3
- nmap
- build-essential
- libpcap-dev
- ruby-dev
- libgmp3-dev
- terminaltables
- tabulate
The required packages are installed automatically by installing the toolkit. However, it is recommended to install libpcap-dev and libgmp3-dev packages manually for smooth installation of Xerosploit.
sudo apt-get install libpcap-dev sudo apt-get install libgmp3-dev
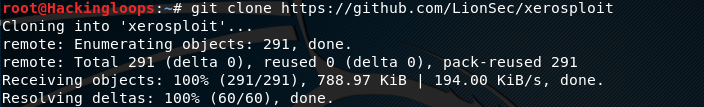
To install XeroSploit, proceed by cloning the toolkit using the following command.
git clone https://github.com/LionSec/xerosploit
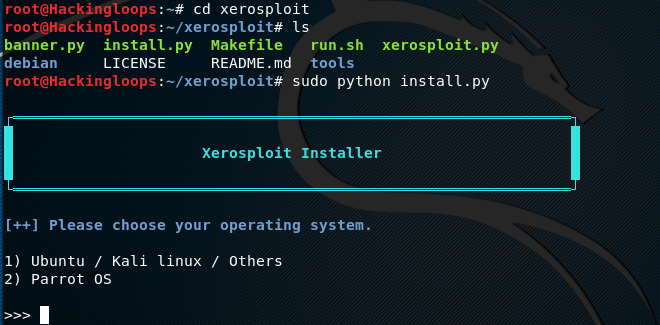
After cloning the toolkit, run the install.py file from the xerosploit directory.
cd xerosploit
sudo python install.py
Provide the system information to the toolkit when prompted by selecting the host OS to complete the installation process.
XeroSploit Interface
After successful installation of XeroSploit, the toolkit can be launched by typing the following command in the terminal.
sudo xerosploit
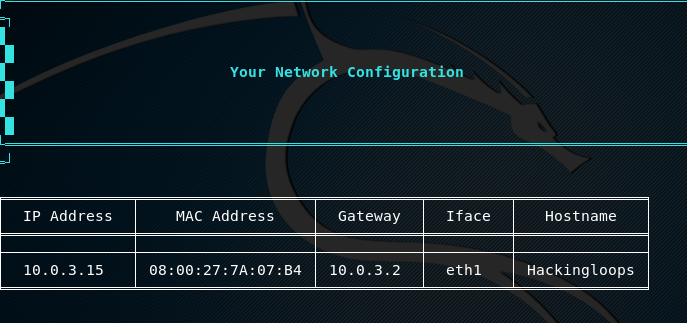
The toolkit fetches and displays the host operating system configuration information on the screen.
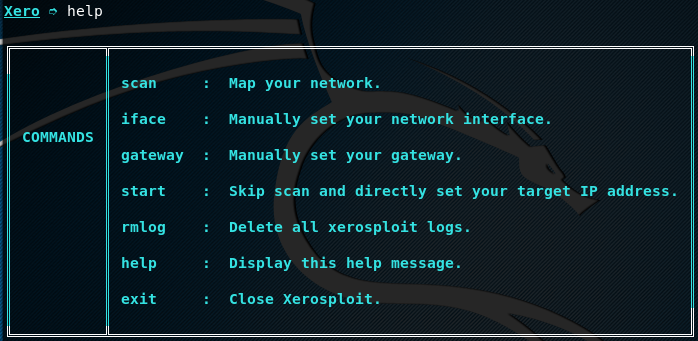
XeroSploit has a set of commands that can be viewed by typing the help command. The main available commands include scan, iface, gateway, start, and rmlog. The full list of commands can be seen in the following screenshot.
The scan command is used to map the target network and discovering all the network hosts. The iface command is used to manually set the host interface. The start command skips the scanning process and targets a given host IP address. By default, XeroSploit logs all the scanning data. However, the logs record can be removed by using the rmlog command.
How XeroSploit Works
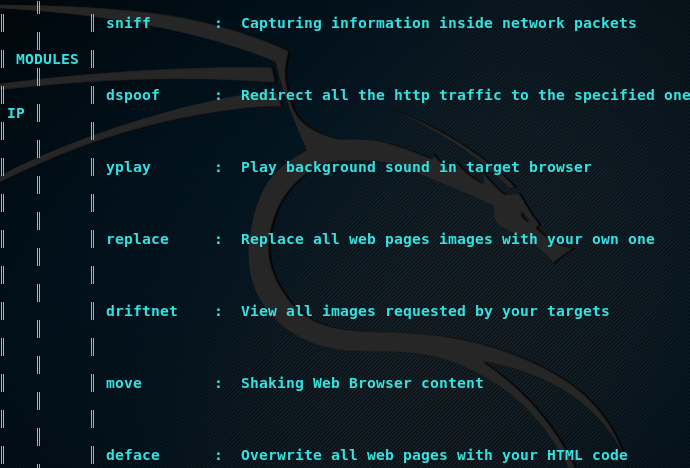
As mentioned above, XeroSploit can be used for network scanning, port scanning, sniffing, DoS attack, HTML injection, Java injection, DNS spoofing, web pages defacements, playing background audios in browsers, and capturing the images being explored by the victim. All these utilities can be performed by running the respective modules.
Network Scanning Example
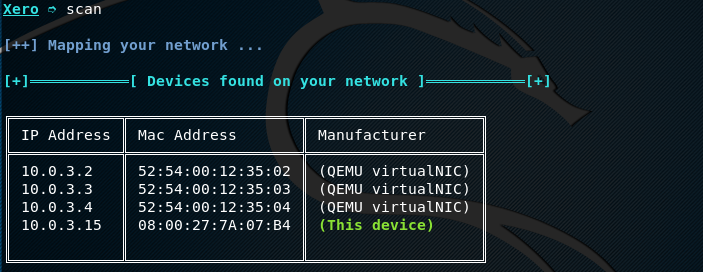
By typing the scan command in the terminal, XeroSploit scans and lists all the available hosts in the target network.
scan
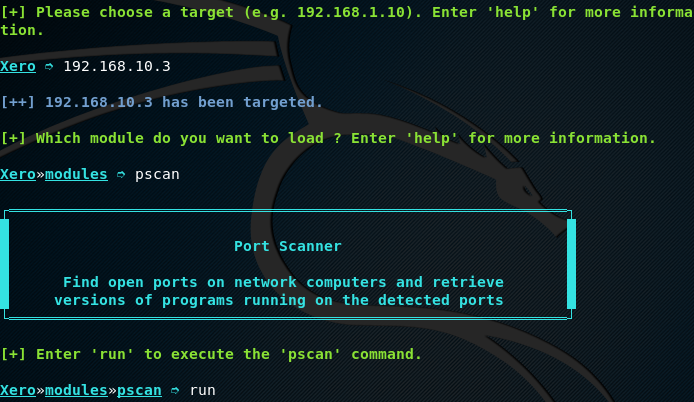
Once all the hosts are discovered, we can manually select a target host IP and run different modules to achieve the desired goals. Let’s suppose we want to scan all the ports of a target host 192.168.10.6 in the network. This can be achieved by typing the host IP (192.168.10.3) and port scanning command (pscan) in the terminal.
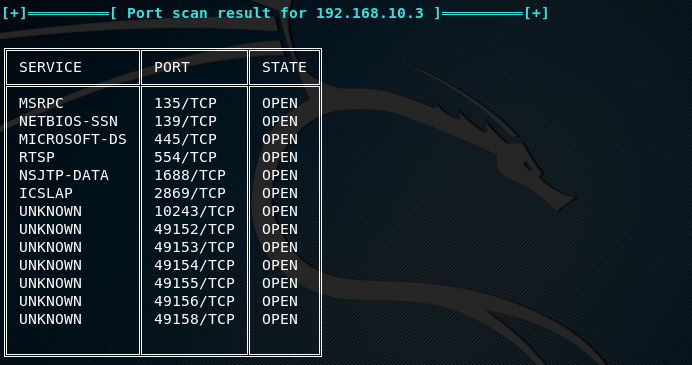
The results are displayed in a tabular format, showing the port number, port status, and running services.
DNS Spoofing Example
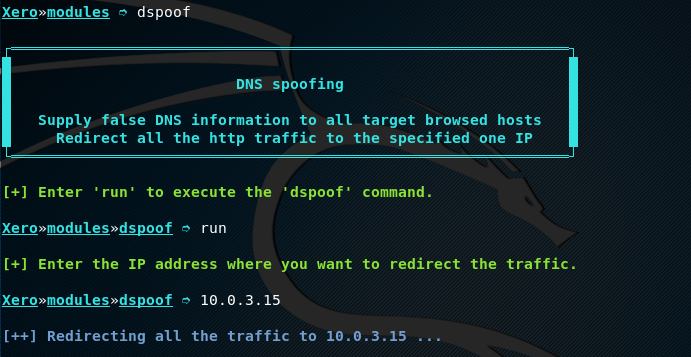
To initiate DNS spoofing utility, type following commands in the terminal.
dspoof run
The tool prompts for the target host IP address where all the traffic should be redirected. Provide the desired IP address as shown below.
This redirects all the http traffic to the provided IP address.
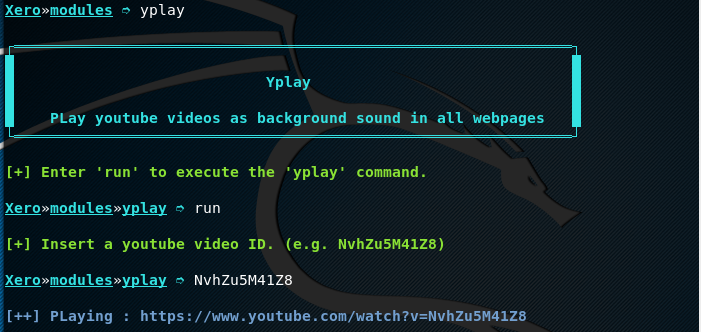
YPlay Example
Yplay is another utility of XeroSploit that allows playing the audio of a selected video in victim’s browser as a background voice. To run this utility, type the following commands.
yplay run
Provide the desired video link in the following format to run its audio as background in the victim’s browser.
We can run the other modules in a similar way by typing their names in the terminal and following the instructions. The complete list of modules can be found by typing the module help command.
Conclusion
XeroSploit is a decent penetration testing tool that can be used for scanning as well as simulating attacks in the network. Besides network penetration testing, XeroSploit can perform some web attacks, such as web pages defacement, capturing web images, and redirecting web traffic to a specific host.