YAWAST is a python based toolkit that does in-depth analysis (detailed information gathering) of target web applications. The toolkit also indicates common vulnerabilities found during the information gathering process. The basic checks performed by YAWAST can be divided into following categories.
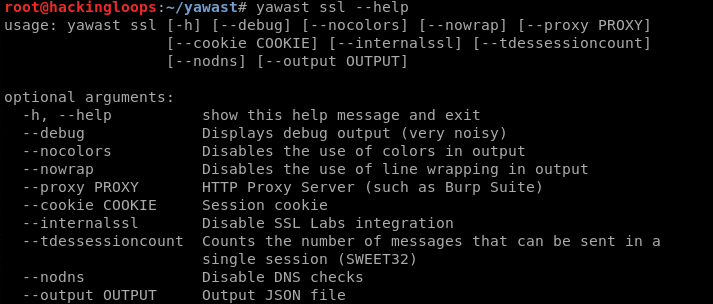
SSL/TLS information Gathering
YAWAST uses SSL Labs and SSLyze utilities to capture a long list of TLS/SSL related information and issues. The important TLS related information captured by YAWAST is as follows.
- Certificates
- Certificates chain
- CAA records
- Supported ciphers
Similarly, the significant SSL related information and issues captured by YAWAST are listed below.
- Self-signed certificates
- Expired certificates
- Signatures (SHA1, MD5)
- Cipher suites
- OpenSSL CVE vulnerabilities (2014-0224, 2016-2107, 2019-1559)
- LOGJAM vulnerability check
- HEARTBLEED vulnerability test
- GOLDENDOOGLE check
- FREAK test
- DROWN test
- SWEET32 check
DNS Information Gathering
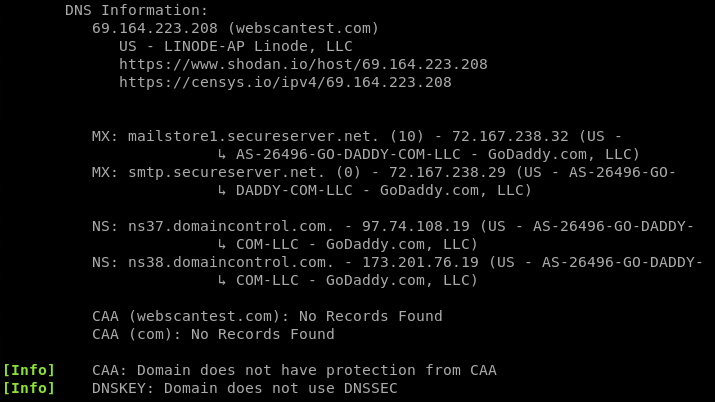
YAWAST can gather the following DNS related information.
- IP Address
- Ownership record
- Mail Exchange (MX) record
- Text (TXT) record
- Name Server (NS) data
- Certification Authority Authorization (CAA) record
- Subdomain information
- Service (SRV) record
MX record gives information about the mail servers working on behalf of domain name. TXT record may contain information about the sources outside the domain name. CAA record shows the authority responsible for issuing the certificate to the domain. Similarly, the SRV record is used to specify servers by host name and port numbers in DNS. This DNS information captured by YAWAST can be very handy in target enumeration (finding potential attack vectors).
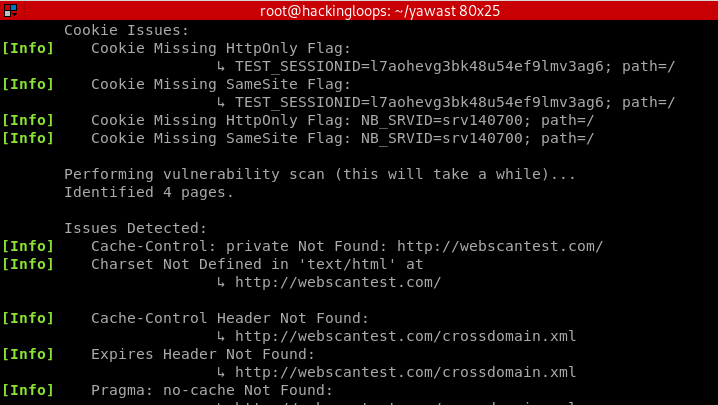
Common Vulnerabilities Scanning
YAWAST has the ability of finding different security flaws in target web applications. These security flaws can be categorized according to the technology in place, such as Generic, PHP, ASP.NET, Nginx Apache, and WordPress. Some common security flaws under these categories are mentioned below.
Generic
- User enumeration
- Information disclosure
- X-XSS protection check
- Source control directories check
- Cookies security test
Apache
- Information disclosure (Modules, Versions, Certificates)
ASP.NET
- Information disclosure (server, version, registered handlers)
- axd, Elmah.axd check
- Debugging information
WordPress
- Version check
- WP-JSON user enumeration
YAWAST Installation
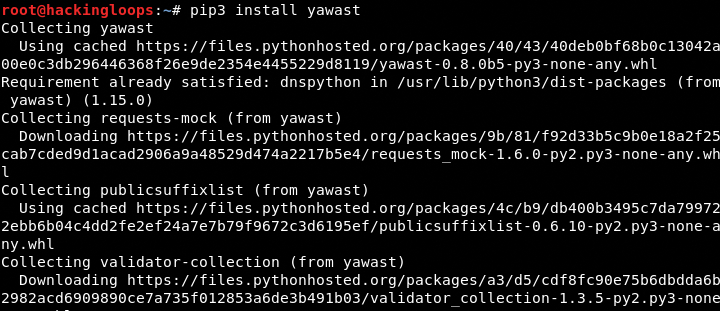
YAWAST is supported by Windows and Linux OS. Linux users can install the toolkit using the following commands.
pip3 install -U nassl pip3 install yawast
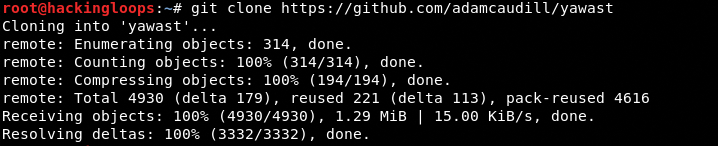
The above commands install the toolkit and all its dependencies. The other method of installing YAWAST is by cloning the toolkit from Github repository and running the installation file using the following commands.
git clone https://github.com/adamcaudill/yawast.git
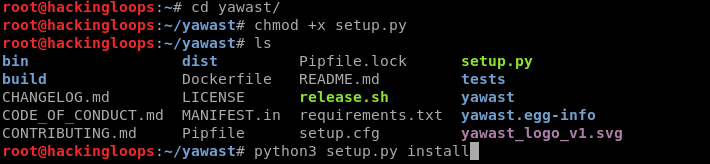
cd yawast chmod +x setup.py python3 setup.py install
Run the following command to install all the YAWAST dependencies.
pip3 install –r requirements.txt
How YAWAST Works
Following is the basic command format to run YAWAST toolkit.
yawast <positional arguments> <target web address> <optional arguments>
The positional arguments can be viewed using the following help command.
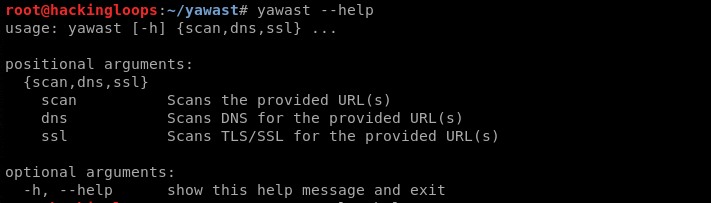
yawast --help
Currently, there are three positional arguments namely scan, dns, and ssl. The optional arguments for these positional arguments can be viewed using the following help commands.
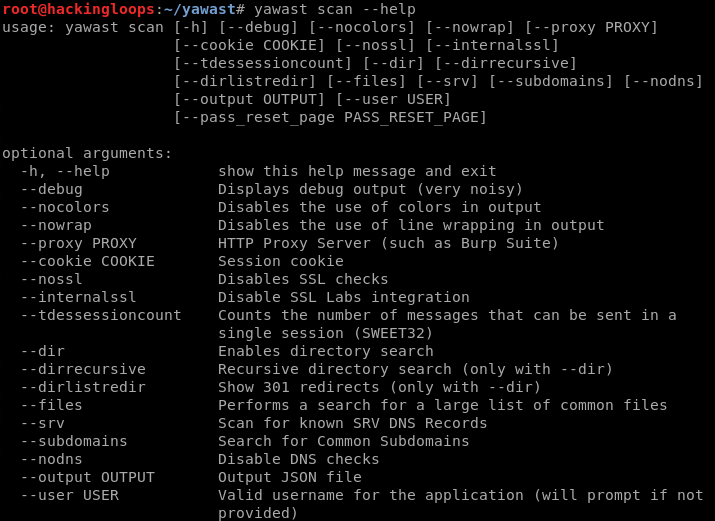
yawast scan –h
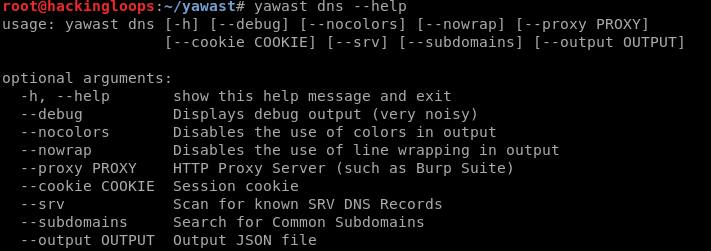
yawast dns –h
yawas ssl –h
The following scan command gathers target information along with issues mentioned in the scan category, such as session cookies vulnerabilities and header misconfiguration issues.
yawast scan <target web address>
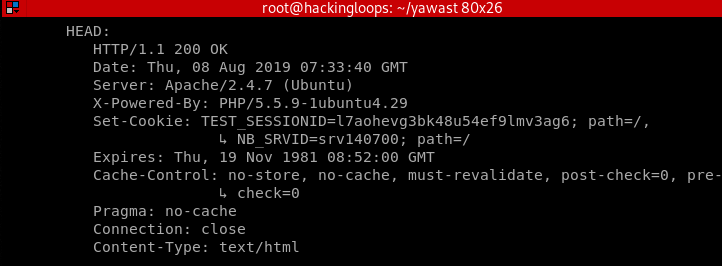
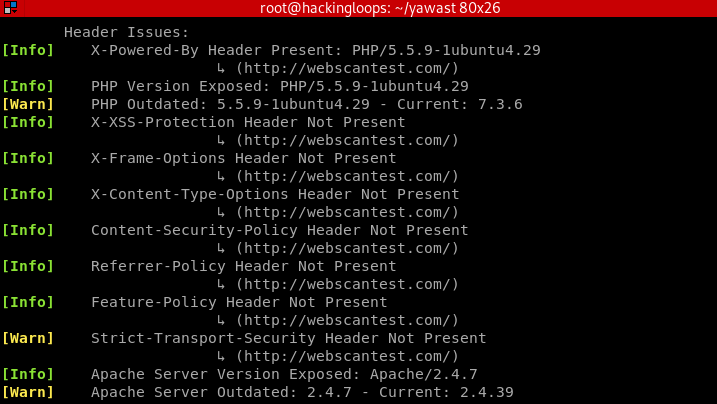
Header Information
The header screenshot shows a lot of header’s misconfiguration that can be exploited by the attackers.
Session Cookies Information
The DNS record and related misconfigurations can be seen using the following DNS command.
yawast dns <target web address>
Similarly, the SSL/TLS record and related vulnerabilities can be analyzed using the following SSL/TLS command.
yawast ssl <target web address>
Summary
YAWAST is a powerful web analyzer that can gather a lot of useful information about target web application. The security auditors can further explore the vulnerabilities based on the gathered information.