What is Cloud?
To understand cloud security, we first need to understand what is cloud infrastructure? How does it operate and what are the essential components?
At very basic, the cloud is a bunch of virtual machines running on various physical servers, 24/7 connected to the internet, maintained and managed by a provider. It allows the flexibility to manage your complete infrastructure with one click on the dashboard and choosing when to get charged unlike orthodox data centers where you have to sign annual contracts.
How can we secure Cloud Infrastructure and obtain Cloud Security?
So now the billion dollar question comes, what is cloud security and how can we do that? Just like any other security where you need to protect your property from unwanted intruders, likewise you want to protect your cloud infrastructure from unwanted guests.
Contrary to physical data centers where we can apply physical controls on top of logical segregations to product our digital assets, we can’t do that in the cloud. Because it’s cloud, it’s everywhere and always connected to the internet we need to decide logical controls based on our model.
Generally 3 models are offered as cloud services:
| Infrastructure as a Service (IaaS) | It offers clients the equipment and distant network structures to house the greater part of their figuring, down to Operating System. Suppliers just oversee center cloud administrations. Clients are entrusted with getting all that gets stacked on top of the OS, including applications, information, runtimes, middleware, and the actual OS. Moreover, clients need to oversee client access, end-client gadgets, and end-client organizations. IaaS models incorporate Microsoft Azure, Google Compute Engine (GCE), Amazon Web Services (AWS). |
| Platform as a Service (PaaS) | It provides a complete computing infrastructure, which enables the organisation to build various products like web applications, APIs, softwares etc. Platforms as a Service consists of entire development environment that is fully managed in the cloud and removes the hassle of maintaining any physical infrastructure. |
| Software as a Service (SaaS) | Software as a Service are developed applications hosted on 3rd party cloud providers that are accessed by end users on the internet. The SaaS users don’t have access to underlying infrastructure, and they just interact with the hosted applications. |
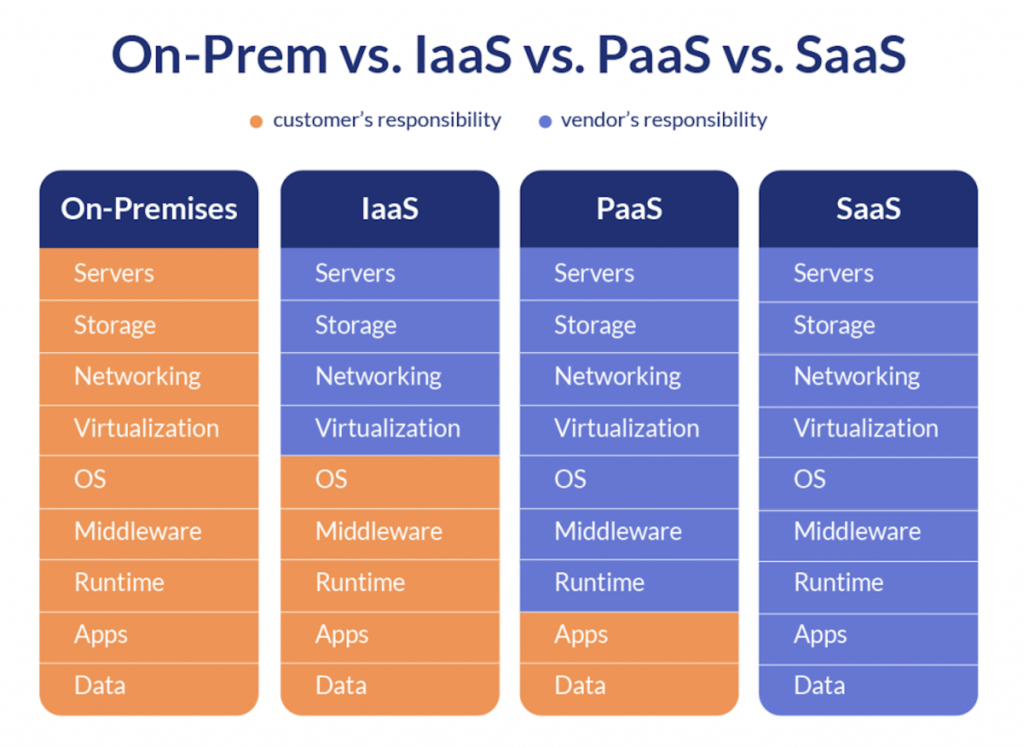
Depending upon the model of your cloud infrastructure, we decide what are the responsibilities of an organization and what are done by the cloud service provider. Generally below are the areas of focus when it comes to cloud security.
Identity & Access Management
IAM comprises policies, processes and technologies to govern and maintain the digital identity. With an IAM structure set up, IT teams can efficiently manage access to critical information in their environment .
SSO (Single Sign On), 2 Factor authentication, Privileged Access Management (PAM) are one of the key elements of any Identity and Access Management .
IAM frameworks can be sent on premises, given by an outsider seller through a cloud-based membership model or conveyed in a half breed model.
IAM Fundamentally consists of below components:
- How do we identify entities?
- How roles are defined and how they are assigned to digital entities?
- Managing roles of digital entities
- Assigning and maintain privileges for each roles and digital entities
Detection
- API Abuse
Since all cloud environments are controlled via APIs so it is recommended to monitor API calls and detect anomalies there. User activities, changes in cloud environments and billing information can be monitored via cloud APIs and an organization should monitor them to prevent any fraud. - Vulnerability Detection
Like in physical infrastructure, the cloud has various products running which are publicly exposed. Complete cloud environment, especially the publicly exposed one, should be monitored for potential vulnerabilities and properly alarming must be set up in order to notify the management so that they can either patch them or take alternative action to reduce the risk in their cloud environment. - Threat Detection
Multiple threat detection services should be set up in the cloud environment. All big cloud providers like Google and AWS come with their own default threat detection tools like Guard Duty(AWS) and Event Threat Detection(GCP). These services detect threats to a cloud environment based on various commonly known attacker tactics and techniques.
It includes various aspects of the cloud that can affect or may lead to affecting the cloud environments. Below are some of the detection mechanisms that can be used in cloud environments:
Network and Application Protection
Fine grained security policies should be set up on every network entry points, just like in physical networks. Networks should be configured properly so that it matches the business needs of the application.
Logical segregation via Security groups and Network Hardening should be in place in the cloud environment to ensure there is not a flat environment. Production environment should be segregated from the testing environment logically and properly firewalled.
Data Protection
Data protection in the cloud uses various methods to safeguard cloud-based information of enterprises. It should include all forms of data like data in-transit, at-rest and in-use.
Like contemporary protection techniques, data should be stored only when necessary and should be in encrypted format. SSL/TLS or secure tunnel should be used when delivering information from one point to another to ensure best practices for data in transit security.
Various security measures can be adopted depending upon the regulatory needs as well like GDPR, HIPAA, PCI-DSS etc. A complete data flow diagram of an organization should be maintained and we should categorize data based on their severity levels. And then necessary security measures should be taken to safeguard the data with more severity.
TL;DR
While above is only the tip of the iceberg, cloud security is much more than that. These points serve as pointers for the readers, and a high level summary of the topics that are generally discussed under the hood of cloud security. Naturally tools and techniques to implement above concepts vary drastically among cloud providers, but the core concept remains the same.
To summarise, we need to ensure proper IAM policies are in place, detection is configured to detect various anomalies in regards to malicious intent, protection of the data should be ensured by adopting the necessary security measures as per it’s state and orthodox concepts of network security should be applied, like network segregation, security group hardening, limiting public exposure etc. .We highly encourage our readers to deep dive into the concepts theoretically and then learn it by implementing in the test beds.

Leave a Reply