 |
| Secure Sockets Lock Tutorial | What is SSL | SSL Hackers Guide |
A hacker can use different types of attacks such as Packet sniffing or ARP Poisoning to steal your sensitive information.
Secure Sockets Layer (SSL) is the most widely used technology for creating a secure communication between the web client and the web server. You must be familiar with http:// protocol and https:// protocol, You might be wondering what they mean. HTTP protocol is used for standard communication between the Web server and the client. HTTPS is used for a secure communication.
Cryptography
If two users want to have a secure communication they can also use cryptography to accomplish it
For example:
TFDVSF=Encrypted Text
SECURE= Decrypted Text
You might be wondering how i Decrypted it, Here i have used Algorithm=+ for the communication and the key is “1“, What comes after S is T so as you can see that S is converted into T, What comes After E is F to letter E from the word secure if converted into F and so on, To help you understand this more better I am adding a Video –
So If the hacker starts sniffing from between he will get Encrypted text and as the Hacker does not know the keys so he cant decrypt it, but if the attacker or hacker is sniffing from the starting point so he will get the key and can easily Decrypt the data.
Standard Communication VS Secure communication
Suppose there exists two communication parties A (client) and B (server)
Standard communication(HTTP)
When A will send information to B it will be in unencrypted manner, this is acceptable if A is not sharing Confidential information, but if A is sending sensitive information say “Password” it will also be in unencrypted form, If a hacker starts sniffing the communication so he will get the password.
This scenario is illustrated using the following figure –
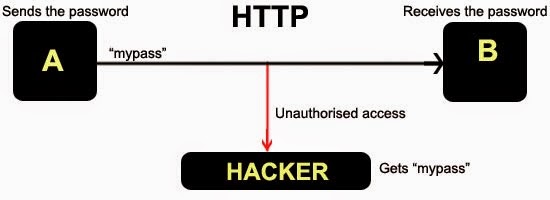 |
| Standard Communications HTTP |
Secure communication(HTTPS)
In a secure communication i.e. HTTPS the conversation between A and B happens to be in a safe tunnel, The information which a user A sends to B will be in encrypted form so even if a hacker gets unauthorized access to the conversion he will receive the encrypted password (“xz54p6kd“) and not the original password.
This scenario is illustrated using the following figure –
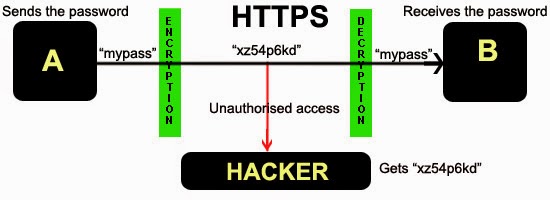 |
| Secure communication(HTTPS) |
How is HTTPS implemented?
A HTTPS protocol can be implemented by using Secure Sockets Layer (SSL), A website can implement HTTPS by purchasing SSL certificate.
Which websites need SSL Certificate?
The websites where a private conversation is occurred, Websites related to online transactions or other sensitive information needs to be protected needs to SSL Certificate.
How to identify a Secure Connection?
In Internet Explorer and google chrome, you will see a lock icon in the Security Status bar. The Security Status bar is located on the right side of the Address bar. You can click the lock to view the identity of the website.
If you are making an online transaction through Credit card or any other means you should check if https:// secured communication is enabled.
Source: RHA InfoSec

Hunter says
I amm regular visitor,how are you everybody?
This post posted att this web page is actually pleasant.