Cuckoo sandbox is an open-source malware analysis system that can perform the dynamic and static analysis of PC files in real-time. It can gather the following information while running the malicious files in an isolated environment.
- API call information
- Network traffic information
- Memory dumps of target machines
- Newly generated files by the malware
- Deleted, downloaded, or modified files by the malicious code
- Windows screenshots during the malware execution on the target machine
The cuckoo droid is a project of the cuckoo sandbox system that provides similar features for Android malware analysis. It serves as an Android emulator to visualize the malicious behavior of Android applications.
How to Install Cuckoo Droid
In order to build a cuckoo droid malware analysis system, we need to integrate the cuckoo droid with cuckoo sandbox and android SDK (Software Development Kit) tools.
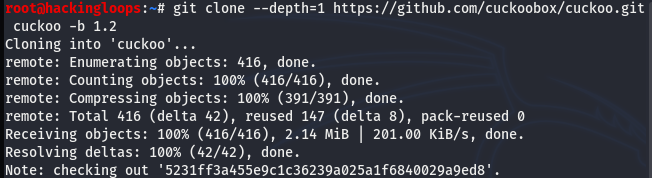
Cuckoo Sandbox and Cuckoo Droid Integration:- The cuckoo droid installation requires the cuckoo sandbox package to be cloned from the following Github repository.
git clone --depth=1 https://github.com/cuckoobox/cuckoo.git cuckoo -b 1.2
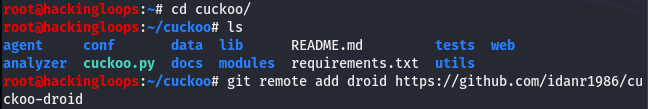
After downloading the sandboxed package, clone the cuckoo droid in the cuckoo directory using the following command.
git remote add droid https://github.com/idanr1986/cuckoo-droid
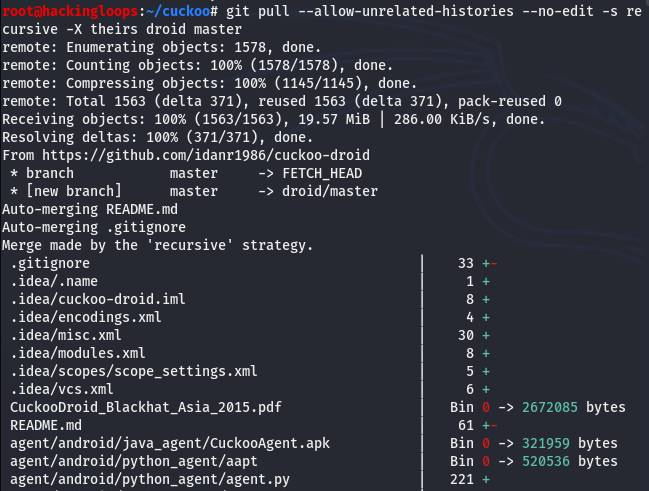
Update the local cuckoo droid repository using the following GIT PULL request.
git pull --allow-unrelated-histories --no-edit -s recursive -X theirs droid master
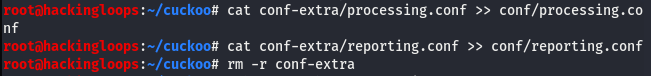
The cuckoo droid contains processing and reporting configuration files in the conf-extra folder. Extract these files to the conf directory and delete the original folder using the following commands.
cat conf-extra/processing.conf >> conf/processing.conf cat conf-extra/reporting.conf >> conf/reporting.conf rm -r conf-extra
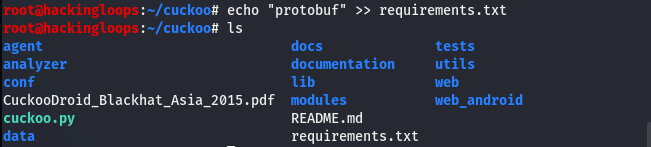
In the next step, generate the cuckoo droid requirements file using the following command.
echo “protobuf” >> requirements.txt
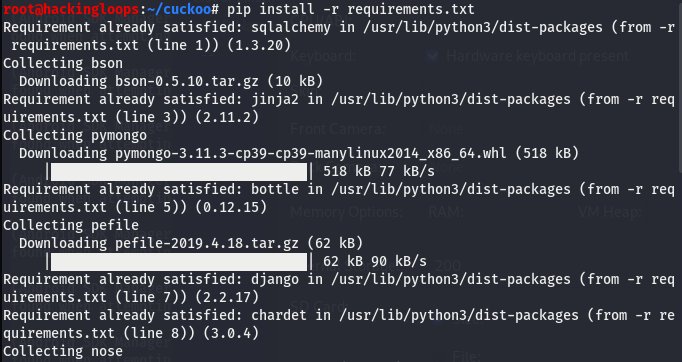
We can install the required modules mentioned in the requirements file using the following command.
pip install –r requirements.txt
Note: Cuckoo droid requires Python2 to operate in Linux operating system.
Android SDK Installation
The cuckoo droid requires the Android emulator, the adb (android debug bridge), and the avd (android virtual device) to operate as an Android malware analysis toolkit. Therefore, the following Android SDK packages must be installed on the host machine to link them with the cuckoo droid.
- Android SDK tools
- Android Platform-tools
- Android SDK platform
- ARM EABI
First off, download the SDK manager using the following path.
wget http //dl.google.com/android/android-sdk_r23.0.2-linux.tgz
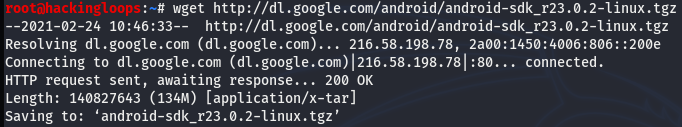
Note: We have downloaded Android-23.0.2 for this demonstration.
After downloading the SDK manager, unzip the package using the following command.
tar -zxvf android-sdk_r23.0.2-linux.tgz
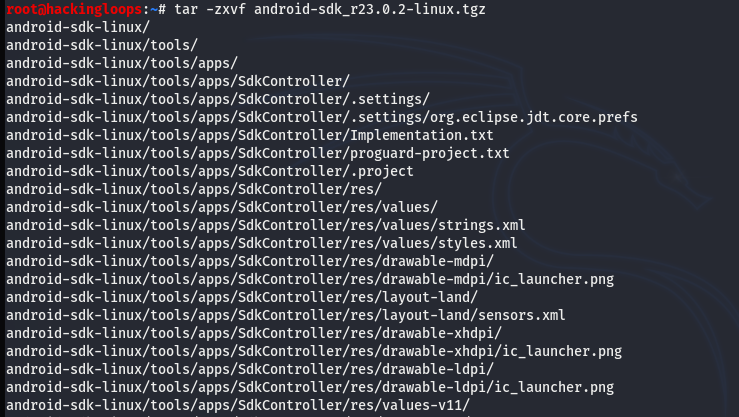
Navigate to the Android SDK directory and activate the Android SDK manager.
cd android-sdk-linux tools/android
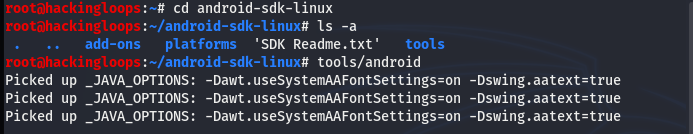
The above command loads the Android SDK manager with all the necessary Android tools and scripts.
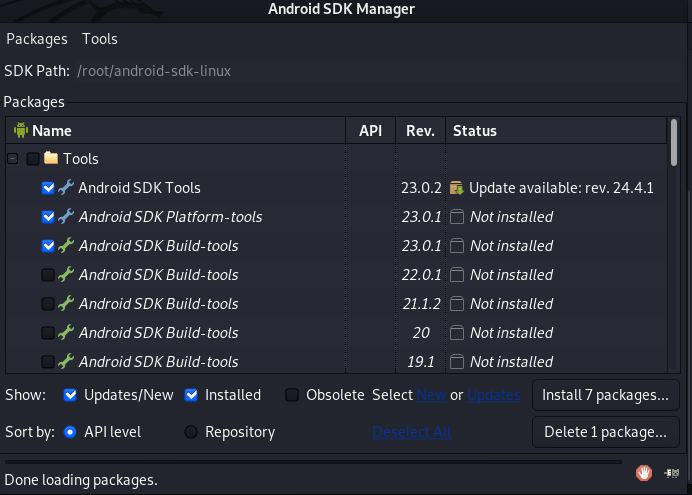
Select the aforementioned Android SDK tools and initiate the installation process from the dashboard. After installing the packages, expand the Tools section in the SDK manager toolbar as shown below.
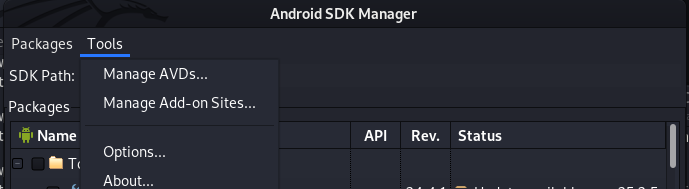
Click on Manage AVDs option to open the AVD manager dashboard
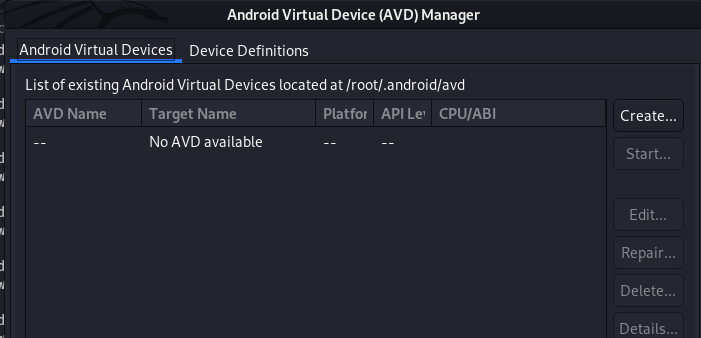
The dashboard shows all the available virtual devices created for the experiments. New devices can be created by clicking the create avd button in the side panel of AVD manager. We can set the following options for the dummy Android device.
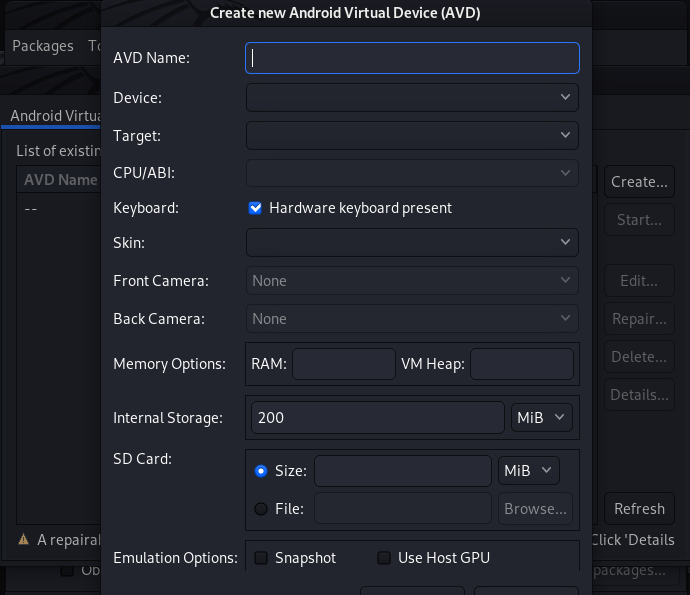
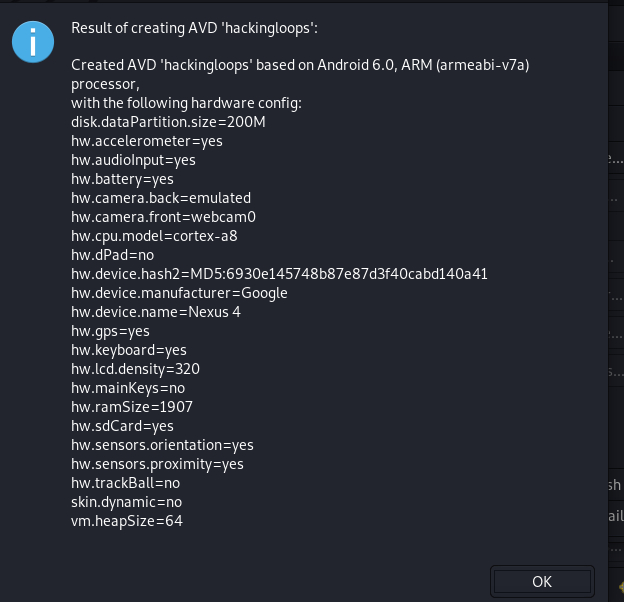
For demonstration purposes, we have created a virtual Android device with the following configurations.
We can boot the newly created Android device by clicking the start avd option on the screen.
We can set the SDK tools’ path in the profile extension (.profile) to manage the emulator and virtual devices from the terminal. Open the user profile page through following command to setup the path for all important SDK tool packages.
gedit .profile path=”path to desired SDK tools”$path
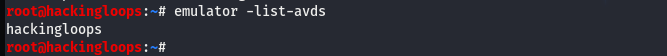
We can type the following –avd-list command to validate the path defined in the .profile extension.
emulagtor –list-avds
Cuckoo Droid Configuration
The following conf folder in the cuckoo directory contains all the configuration files to be modified by the user.
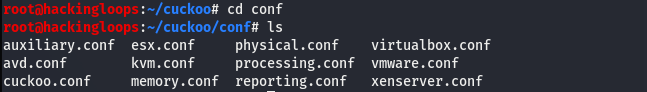
The cuckoo.conf and avd.conf are the core configuration files that require some name and path modifications.
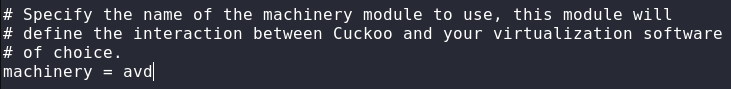
cuckoo.conf configuration: Open the cuckoo configuration (cuckoo.conf) file to modify the virtualization software type and result server IP address as shown in the following screenshots.
Default Virtualization Software = virtualbox
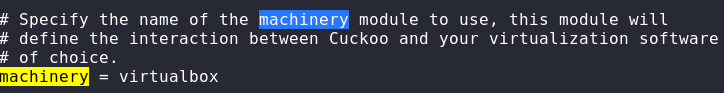
Modified Virtualization Software = avd
Default result server IP = 192.168.56.1
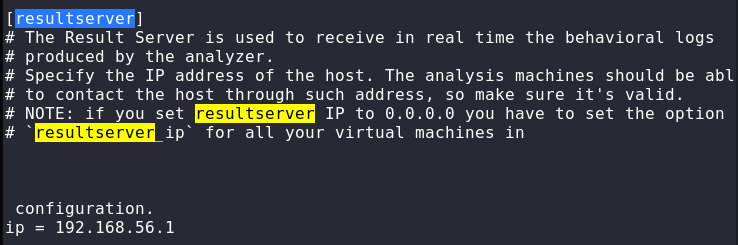
Modified result server IP = 127.0.0.1

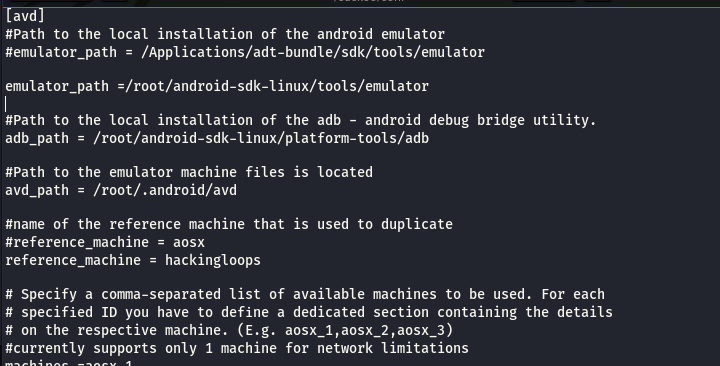
avd.conf configuration: The avd.conf file requires the emulator, adb (android debug bridge), and avd (android virtual device) path settings. All these packages are available in the SDK manager folder. Open the avd.conf file and update the emulator_path, avd_path, and adb_path accordingly.
Besides the aforementioned configurations, there are some optional settings like enable/disable external sniffer in the auxiliary configuration file. After updating the configurations, navigate to the cuckoo directory and run the main (cuckoo.py) Python file to start analyzing the desired virtual device.
Conclusion
The cuckoo droid can be helpful in analyzing Android applications in real-time. The framework is capable of performing the static and dynamic analysis of suspicious Android apps. A complete security audit with a cuckoo droid can be helpful to determine the risk factor of target mobile applications.