There are millions of mobile applications available for Android and iOS users. The download statistics of many of these applications are quite remarkable. However, the large number of downloads does not guarantee the safety of any application. For instance, the SHAREit is a famous data-sharing application with over one billion users. Recently, security researchers have found serious bugs in this app that could lead to severe mobile attacks. Finding security flaws and backdoors in mobile applications require knowledge, experience, and dedicated tools. In this article, we shall analyze one such tool called Mobile Application Security Framework (MobSF).
The Mobile Application Security Framework (MobSF) is an automated tool that can be used for mobile penetration testing, malware analysis, and security assessment of Android, iOS, and Windows applications. The tool can perform static and dynamic analysis of a variety of applications including the APK, XAPK, APPX, and IPA files.
How to Install MobSF?
The MobSF is supported by MAC, Linux, and Windows operating systems. The Linux users require the GIT, Python3.8+, and Java Development Kit (JDK8+) to install the framework and its dependencies. These packages can be installed using the following commands.
sudo apt install git sudo apt install python 3.8 sudo apt install openjdk8-jdk
The following dependencies must be installed before running the MobSF setup files.
sudo apt install python3-dev python3-venv python3-pip build-essential libffi-dev libssl-dev libxml2-dev libxslt1-dev libjpeg62-turbo-dev zlib1g-dev wkhtmltopdf
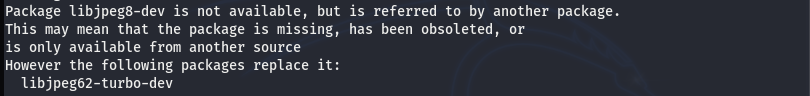
Note: The MobSF documentation mentioned the libjpeg8-dev library as a prerequisite. However, the Kali Linux users should replace the libjpeg8-dev with libjpeg62-turbo-dev package if they encounter the following installation error.
After meeting all the dependencies, clone the MobSF source code using the following command.
git clone https://github.com/MobSF/Mobile-Security-Framework-MobSF.git
Navigate to the tool’s directory and run the following setup file to install the framework.
cd Mobile-Security-Framework-MobSF
./setup.sh
The installation can take quite a while due to the large set of installation files and packages imported during the setup process.
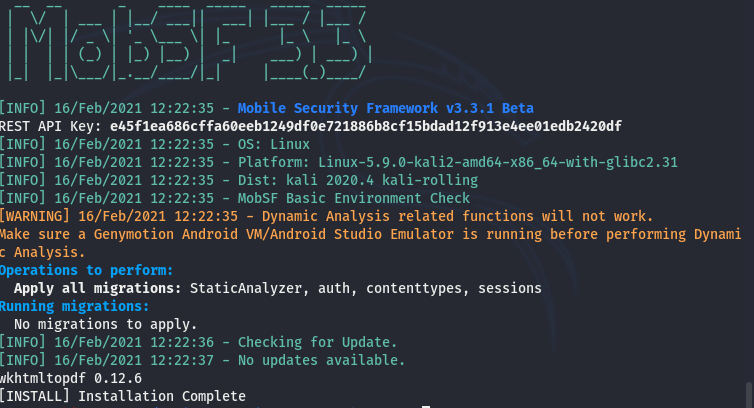
How MobSF Works?
The Linux users can run the MobSF framework using the following command.
./run.sh
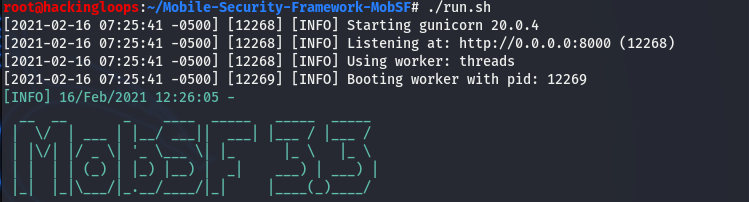
The above command opens the MobSF dashboard on the localhost server running at the default 8000 port. The default port can be replaced with the desired port using the following command.
./run.sh 127.0.0.1:desired port here
We can analyze the desired mobile application by uploading the supported (APK, XAPK, APPX, and IPA) files to the MobSF dashboard. To analyze the MobSF working, we have used the vulnerable Androgoat APK file from the following Gihub repository.
https://github.com/satishpatnayak/AndroGoat
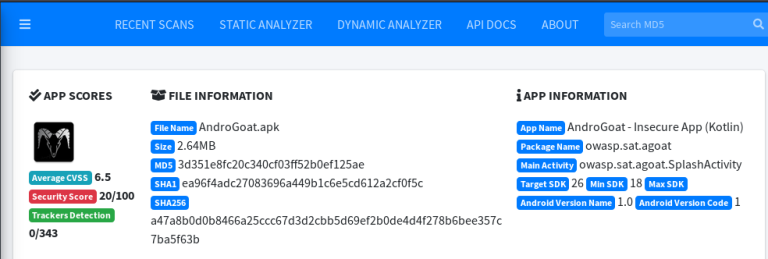
The Androgoat’s APK upload to the MobSF dashboard populated the different levels of statistics and graphs on the screen.
The following screenshot gives a top-level overview of the target APK file showing the risk score and development information about the application.
If we scroll down the results, we find different types of analytical information, such as Application signing record, permissions status, network security information, manifest files analysis, code review, NIAP (security policy enforcement) compliance results, and code de-compilation (reverse engineering) options. Screenshots from each set of aforementioned information gathered by the framework are shown below.
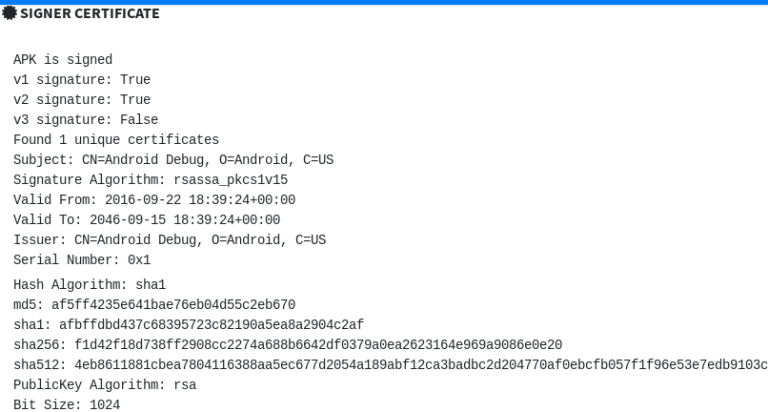
Application Signer Record
The application singing certificate gives detailed information about the supported hashes and encryption followed by the application.
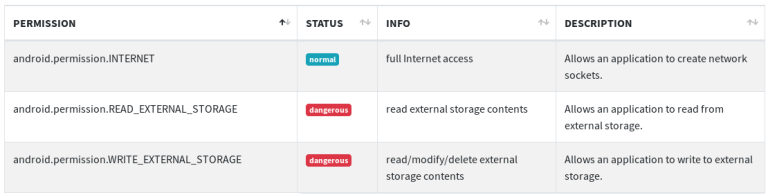
Allowed Permissions Status
The following image suggests that the application is granted dangerous read and write permissions.
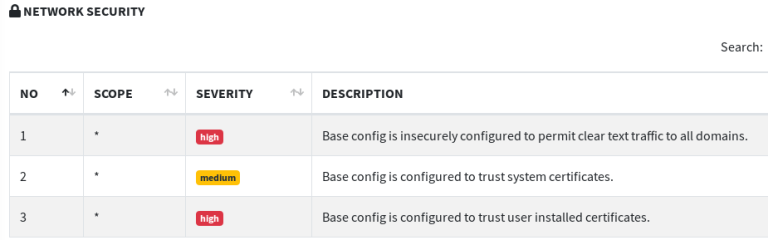
Network Security Information
Network security test reveals some dangerous vulnerabilities, such as sending clear text traffic and trusting user certificates without verification.
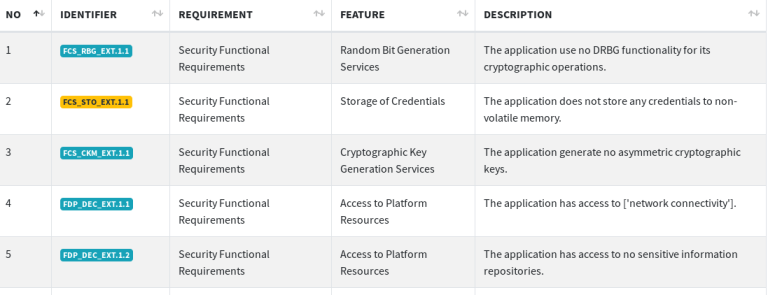
NIAP Test Results
The following screenshot shows a glimpse of app’s adherence to National Information Assurance Partnership (NIAP) security policy.
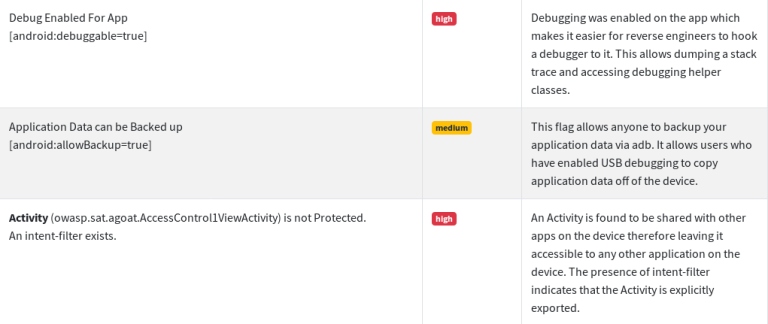
Manifest Analysis
The manifest file record also reveals the security flaws found in the target application.
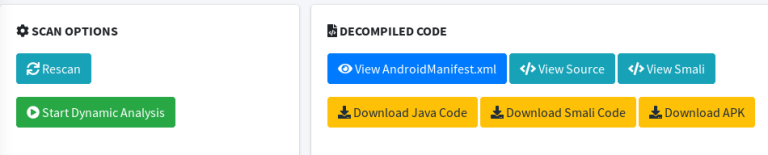
Besides the aforementioned analytical results, we can decompile the target files to get useful information about the backend code of the application. The following screenshot shows the available scan and decompile options.
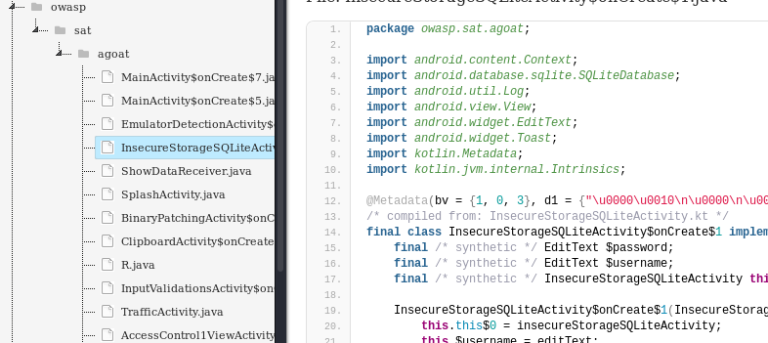
We can get the information about all the JAVA files through view source option.
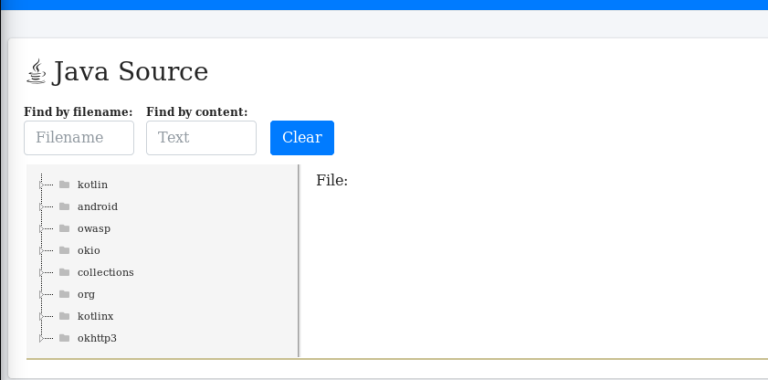
The code from each file can be viewed separately for further analysis.
Conclusion
Mobile applications debugging and security analysis is a complex job. The MobSF tool can make the job easy by automatically finding the security flaws, vulnerable codes, and risk factors of target mobile applications. It also supports integration with other penetration testing tools through REST API keys.

Leave a Reply