When looking at the battle between Nessus VS OpenVAS for the best vulnerability scanner it may be hard to determine which to use and why. Both are really good and used all the time and in the information security world you likely need use one of these or something similar but one may have distinct advantages or disadvantages for you depending on what you need to use it for. We are here to help determine which is best for you and even have a comparison table to make it easy.
Technology these days have become a vital part of our lives. From our work to our entertainment, from facilities to our recreational activities, technology has taken over all of them and this is not only because it provides ease of access to us but also because it is way more efficient and disciplined than traditional ways.
Importance of Cybersecurity
With technology playing such a major part of our lives, the questions that comes to our minds are its safety and security. Is this technology really that secure what it claims to be? Is it really not harming our lives more than it benefits? Should we really be dependent on technology this much? The answers to these questions are not as straight-forward as expected. Almost every other day there comes out flaws and bugs in the applications that we were using frequently but on the other hand, many enterprises and tech companies invest billions for making the security of these technologies better and every day there is a break-through advancement in them.
Testing Technology
Speaking in terms of technological security, formally known as Cyber-security and many other names, the hot topic these days, among many others, is achieving the perfect or close to perfect automated testing of the security of this technology that can make sure that there are no flaws in any aspect of it. These tools are known as penetration testing tools or vulnerability assessment tools.
Introduction to Vulnerability Assessment System (VAS)
The main focus of this article would be the specifics of vulnerability assessment systems. These systems are not just tools that can be used for single feature testing but these are whole system of tools that test many aspects in one go. These Vulnerability Assessment System (VAS) reduce human effort in detecting and suggesting solutions for different vulnerabilities and flaws. Although, these VAS are not perfect but they are much better manager for managing these flaws than humans. Also note that these VAS do not cover any undiscovered or even all of the discovered and known flaws but instead these VAS covers most of the commonly known vulnerabilities and they also update their databases as quickly as possible for newly exposed vulnerabilities. Testing includes network scanning, hosts scanning, software patches and many more. Most of them use Common Vulnerabilities and Exposures or CVEs to run test cases for the vulnerability testing for different infrastructures. In this article, we will only discuss two prominent VAS, Nessus and OpenVAS, in detail.
Nessus and OpenVAS
Nessus is a vulnerability scanner by Tenable Networks while OpenVAS is an open-source vulnerability scanner, by Greenbone Networks GmbH, under the GNU General Public License. Both of these Vulnerability Assessment Systems (VAS) cover many different CVEs from the database of known vulnerabilities. Nessus is a proprietary tool and obviously is better in some ways than OpenVAS. Both VAS are used for managing vulnerabilities in small to large organizations and enterprises to ensure and keep their secure up to date in real time. Also, Nessus has a trial version which is free of cost for personal use in a non-commercial environment for a limited period of time and their paid packages starts from around $2500/year.
History of Nessus and OpenVAS
In the beginning, Nessus was an open-source project, but when Tenable Networks made this tool proprietary, the pentesters at SecuritySpace proposed GNessUs, which is a fork of the open-source Nessus, discussed it with pentesters at Portcullis Computer Security and then was announced by Tim Brown on Slashdot. This GNessUs was later named as OpenVAS.
Nessus in Detail
As discussed before, Nessus is a proprietary and premium vulnerability assessment system by Tenable Networks. Nessus offers many additional features other than basic testing features. It not only indicates the flaws and vulnerabilities that exist in the infrastructure but also suggest solutions for those detected vulnerabilities. The features and characteristics of Nessus are given below in more detail:
- CVE Coverage
Tenable Networks claims that the latest version of Nessus searches for more than 47,000 Common Vulnerabilities and Exposures (CVE)s which is quite promising compared to other vulnerability assessment tools.
- Less False-Positives
The company also claims that their tool has an industry’s lowest false-positive rate which is even less than that of six sigma accuracy. The false-positive is the scenario in which the tool indicates a flaw in an infrastructure but in fact that indication was false.
- Professional Tool
Professionalism is another key aspect of Nessus that has its advantage over OpenVAS.
- Vulnerability Fixing Suggestions
As mentioned before, Nessus also gives the facility of suggesting solutions suitable for fixing the existing vulnerabilities that have been detected by this tool.
- Ease of Use
Nessus, along with being simple and easy to use is at the same time professional and quite productive. Its ease of use makes it easy for novice users to learn quickly.
- Customer Support
Just as any of the professional and premium tool would offer, Nessus also offers customer support to extend their support for their product-users.
- Live Results
Nessus also offers real time visibility using scan data when the tool is updated.
- Scanning Efficiency
Nessus takes at maximum 24 hours to update their database for newly discovered vulnerabilities, making infrastructures secure and updated as shortly as possible.
- Built-in scan templates
Nessus also have few pre-built scanning templates which scans for many different vulnerabilities in categorized templates, in one go and whole infrastructure can be tested varying upon different tests. Figure below show a screenshot of available built-in scan templates
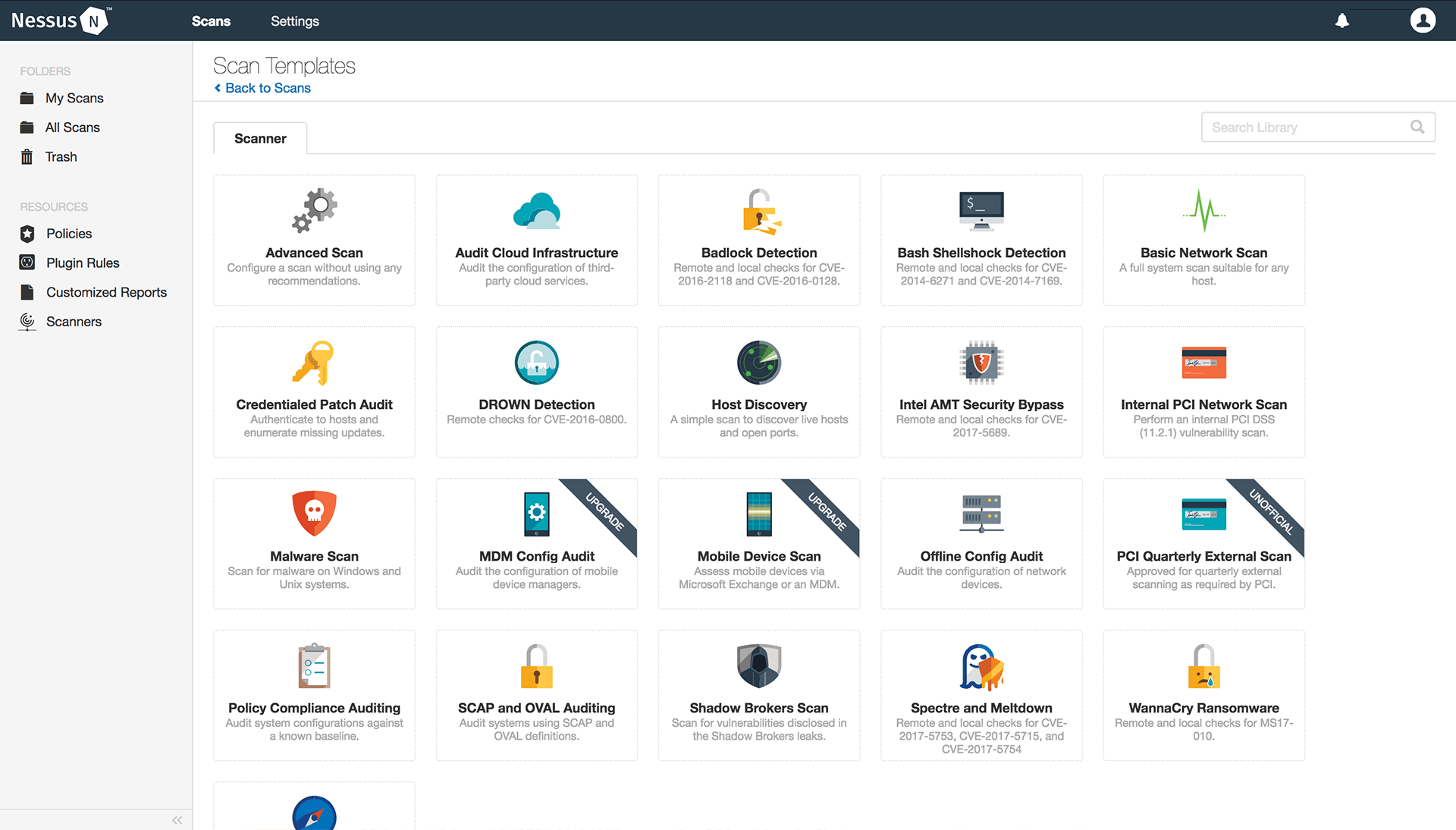
- Group Testing
Nessus also allows their users to make groups of vulnerability testing use-cases to facilitate them by providing custom grouping feature for scanning at a single click. Following screenshot shows group testing in Nessus.
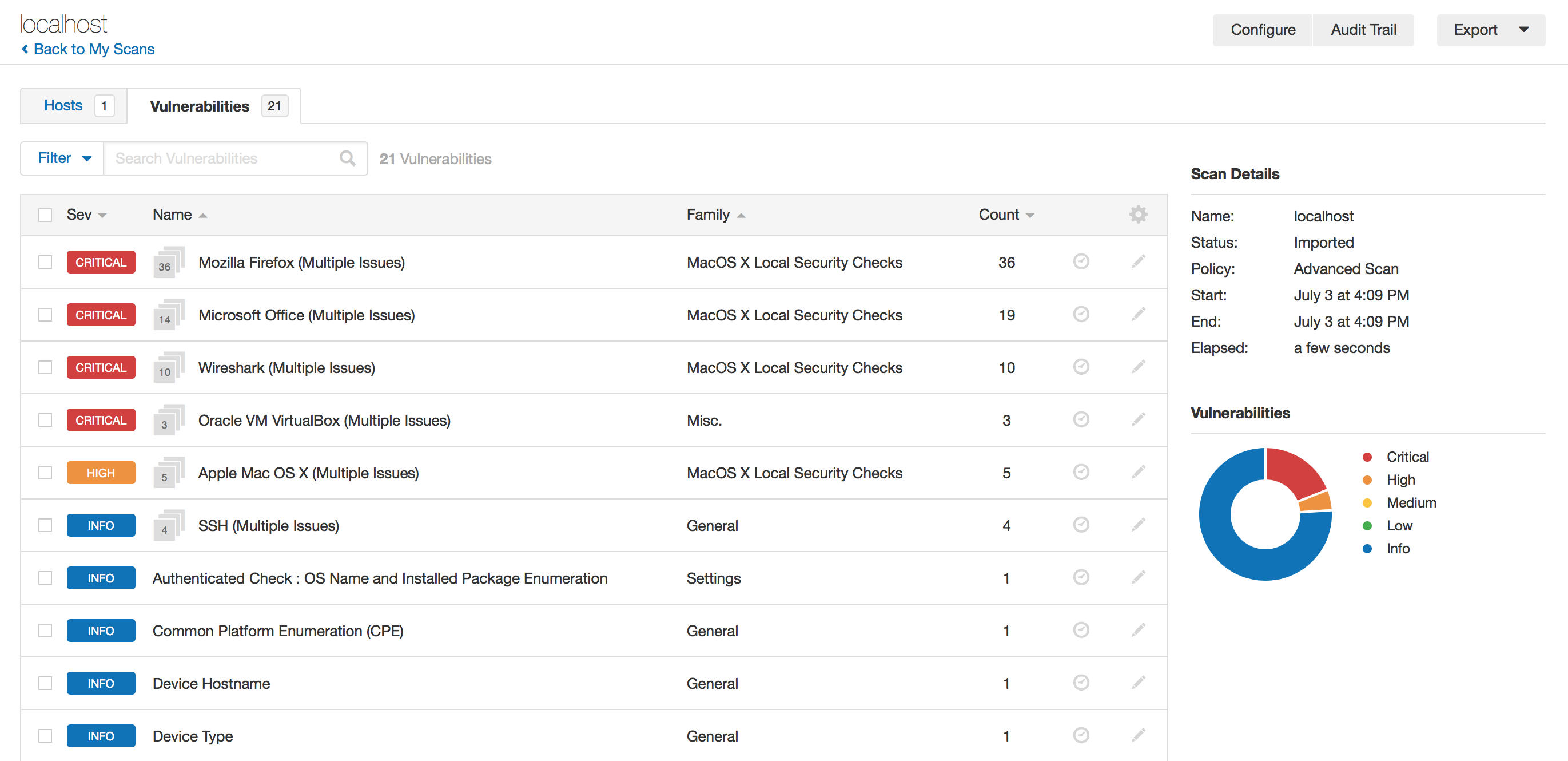
- Report Generation
This tool has a built-in functionality of generating reports of the vulnerabilities found and their severity, accordingly, for professional use. Along with that, the report also includes the suggested solution for the flaw that was found. Nessus also supports adding custom configurations for the format to be used in report generation. Screenshot below shows auto-generated report
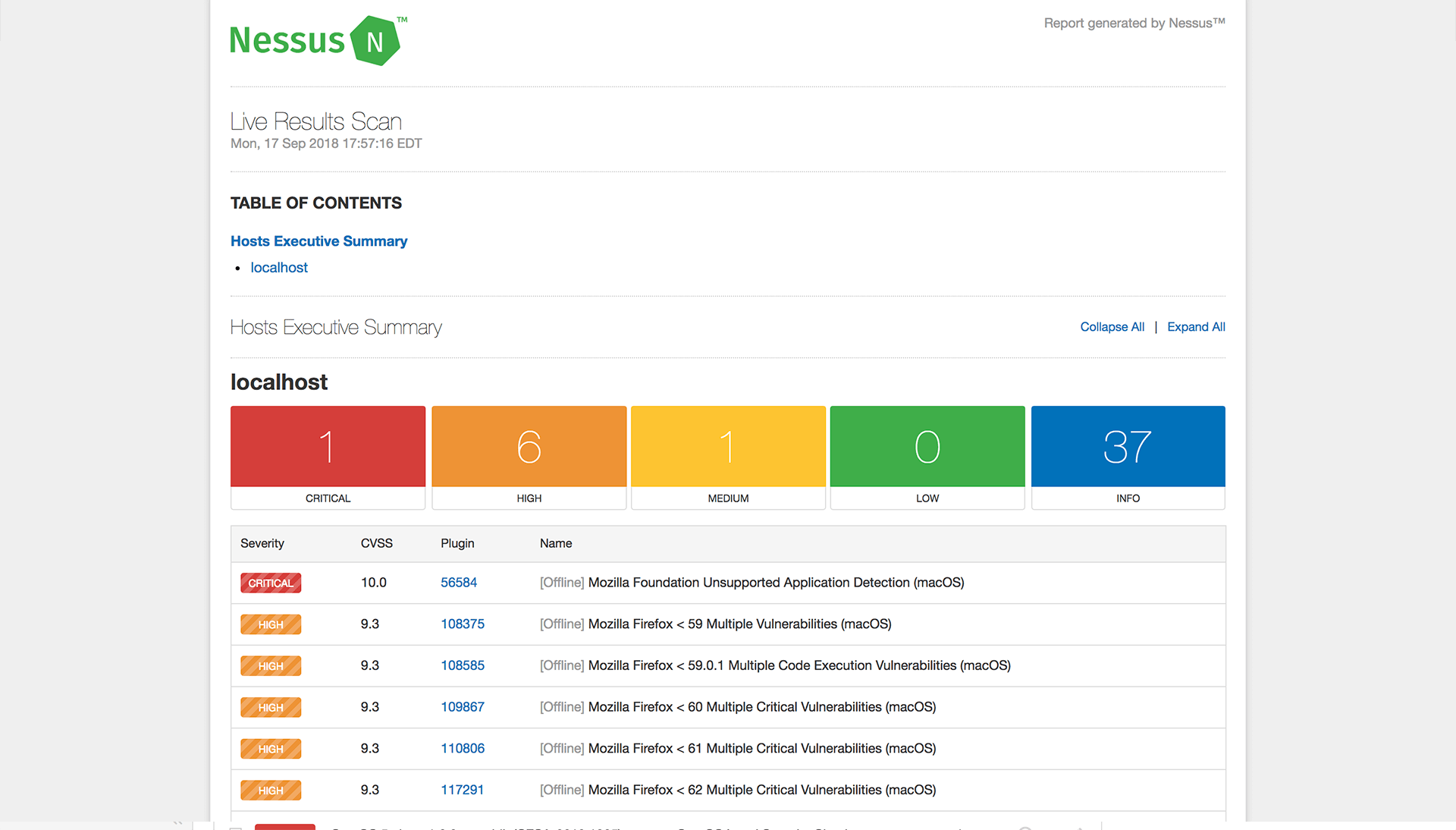
- OS Supportability
Nessus has support for Unix-based OSes (Linux, FreeBSD, Unix, etc.), Windows and MacOS.
Disadvantages
- Cost:
Nessus has a cost associated with it and this discourages small businesses with less capital to go for this option. Currently, the cost of the latest version of Nessus is starting from around $2,500/year, which is in most cases not viable for a small companies.
- Need of Expertise:
Nessus is an advanced vulnerability assessment tool and to utilize its features and cost to its full, expertise in this field is also required for best outcomes.
OpenVAS in Detail
OpenVAS is an open-source Vulnerability Manager (VM) and Vulnerability Assessment System (VAS), which means it is free to use and its source code is public as well. It is licensed under GNU General Public License. Although it is free but even then it is really good at its job and comes in the list of top 10 VAS. OpenVAS repository can be found at https://github.com/greenbone/. Some of the most prominent traits of this VAS are given below:
- Open-source and Free of Cost:
The best aspect of OpenVAS is that it is open-source and free of cost, and at the same time competent to the paid assessment systems that are present in the industry.
- Custom Configurable:
OpenVAS also provide the features of being configured by the product-users in line with their own requirements and desires. The screenshot below shows an example of the configuration panel in OpenVAS
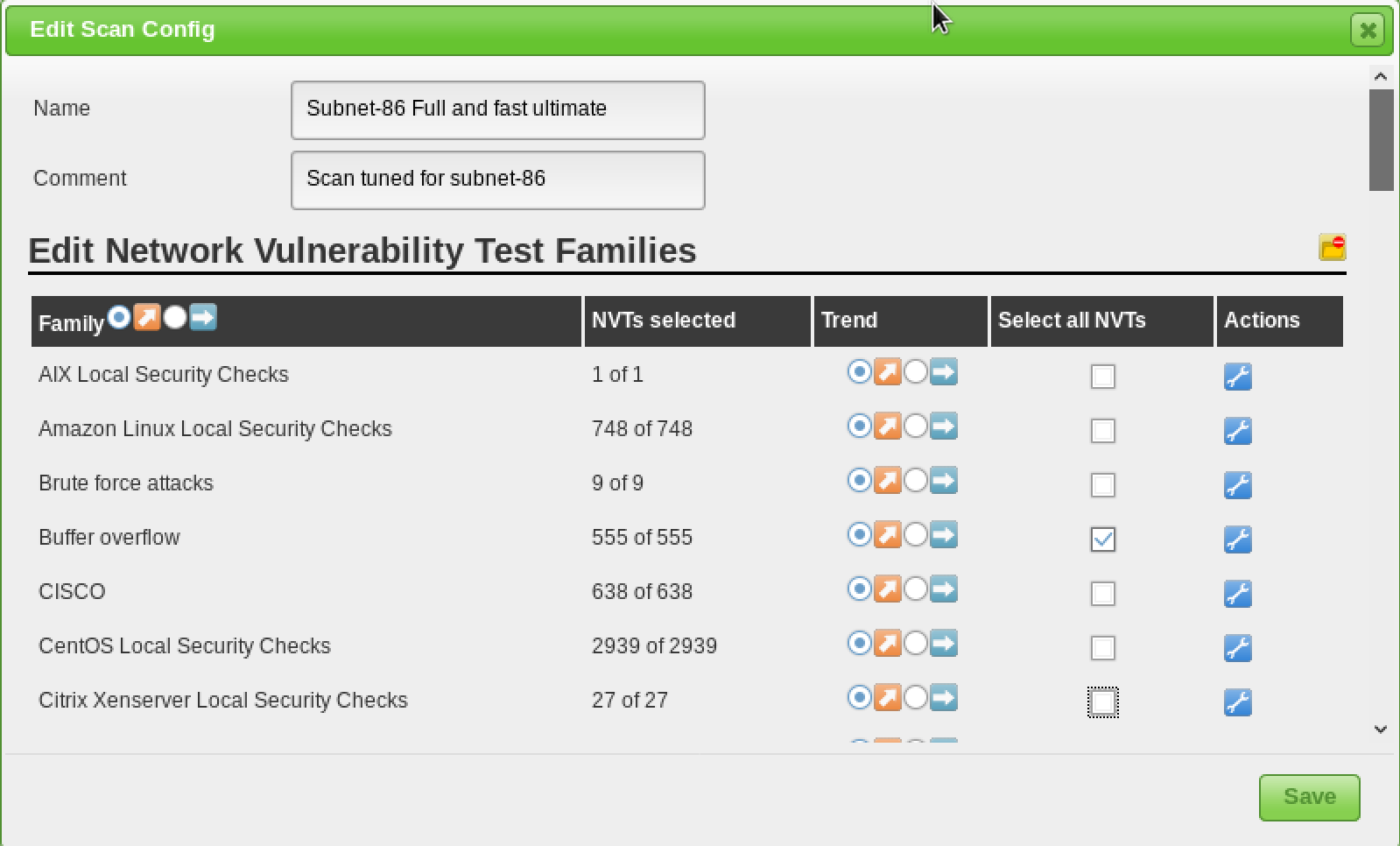
- Contributions
Being an open-source, the source code of openVAS is public and anyone can contribute to the tool, which makes the software itself more secure.
- CVE Coverage
OpenVAS has a Common Vulnerabilities and Exposures (CVE)s coverage of around 26,000, from which the vulnerabilities and bugs are searched and tested on the underlying infrastructure. Following screenshot shows an example of the scanned results
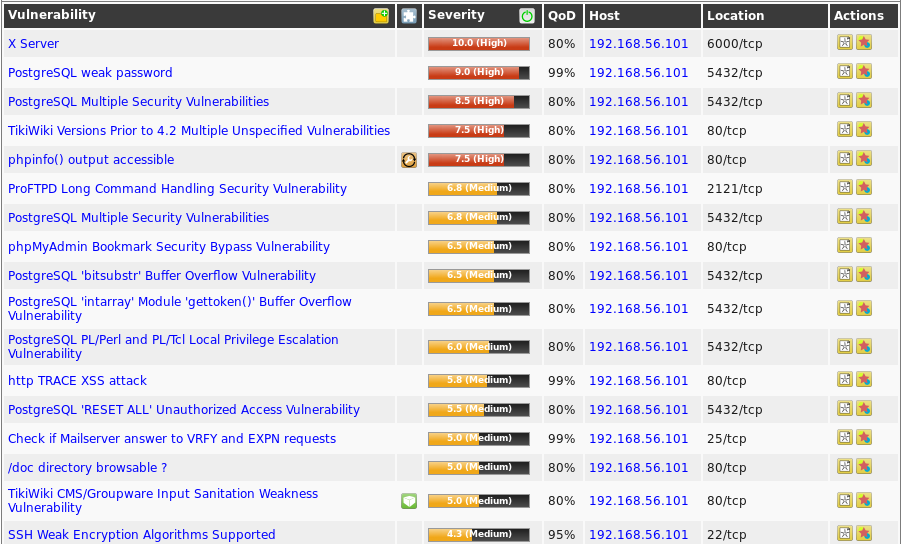
- Useful for Small Businesses
Most small businesses prefer OpenVAS because it is a cost-free product and is notable in the testing tools industry. Also, if you are still deciding to go for vulnerability assessment tool and yet not sure about it, you can give your thoughts a chance by try using OpenVAS without risking your investment.
- Detailed Documentation and Tutorials
Greenbone, the company of OpenVAS, has also provided proper and thorough documentation for the usage of this tool. Not only this, they have also provided video tutorials to assist the users of their tool in using it. Both the manuals and tutorials can be found at:
https://docs.greenbone.net/GSM-Manual/gos-5/en/.\
Disadvantages
- Covers Less Vulnerabilities Compared to Nessus
OpenVAS covers less CVEs and test cases for testing and assessment as compared to Nessus which covers approximately double of what OpenVAS covers. In short, OpenVAS would discover less vulnerability or it might have missed some flaws that Nessus would have detected.
- OS Support Limitation
Nessus has limited operating system support which is for Unix-based OSes (Linux, FreeBSD, Unix, etc.) only.
Additional Features
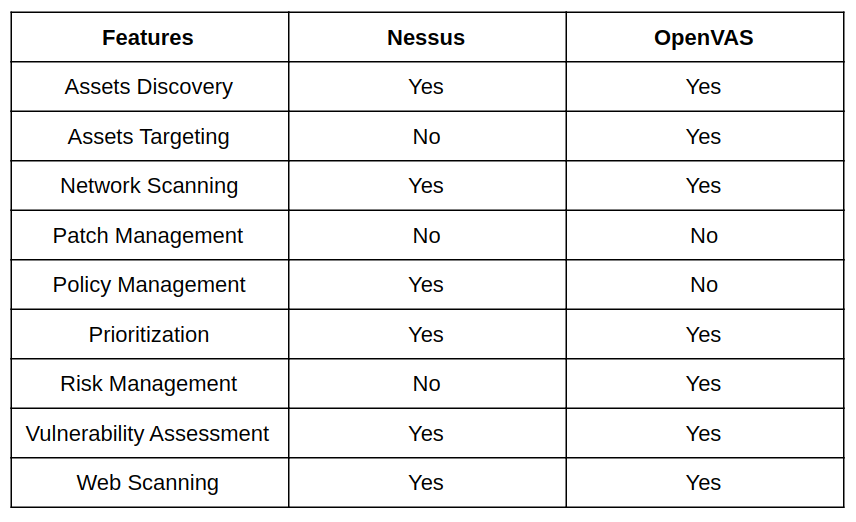
The table below also shows some of the features that Nessus and OpenVAS offers or not in comparison to each other
Concluding
With the end of this article after a detailed discussion, we have come to a conclusion that both Nessus and OpenVAS having different pros and cons have their own importance and are suitable in different environments depending upon the needs and scenario. If we summarize the article in a nutshell, we would say that Nessus is more suitable in cases where vulnerabilities needs to be scanned more deeply but it comes with a yearly cost and the company or user can bear this price, whereas OpenVAS is more suitable in an environment where the company or product-user needs a balance of security with minimal spending. Hope that this article provided a useful addition to your knowledge if it was new for you.

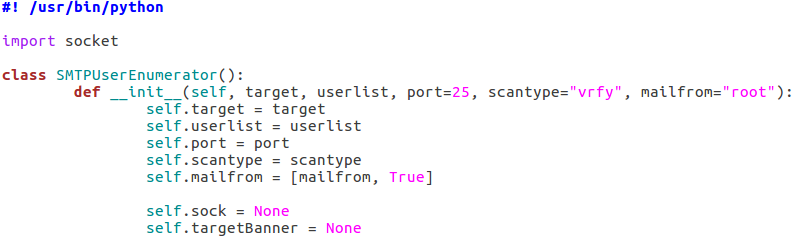
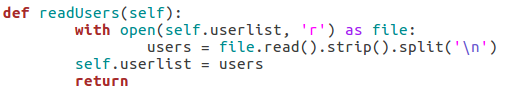
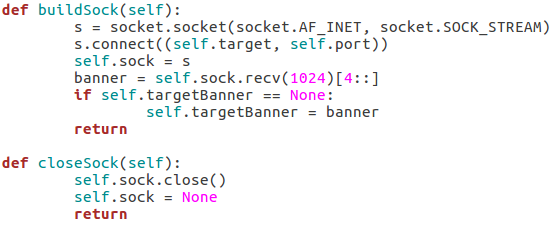
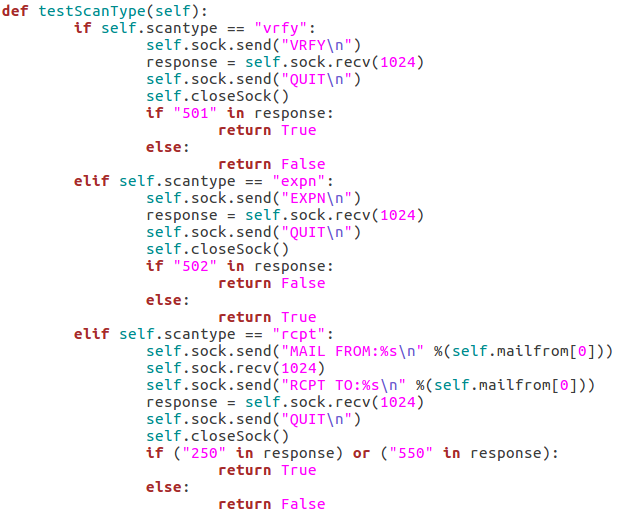
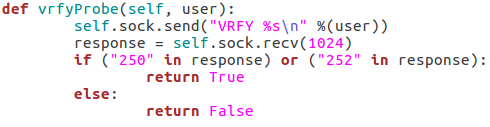
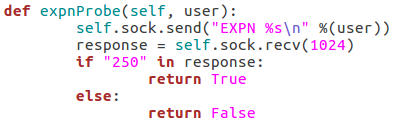
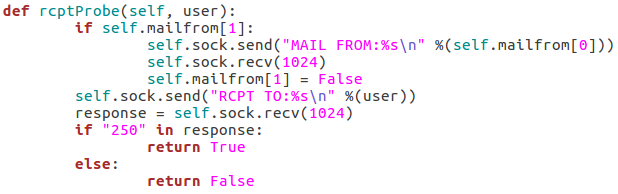
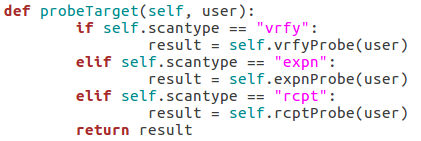
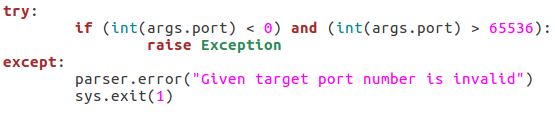
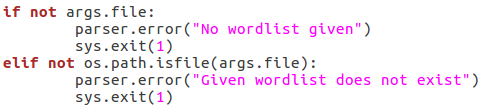
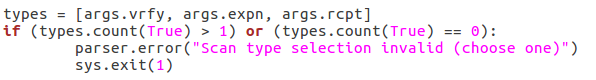
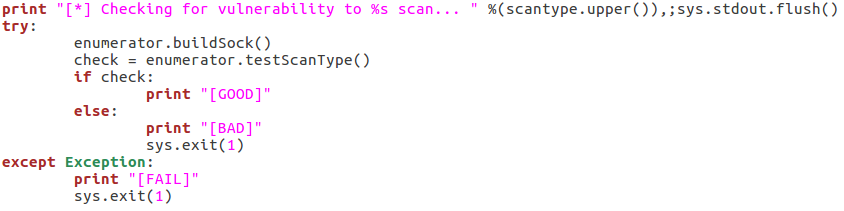
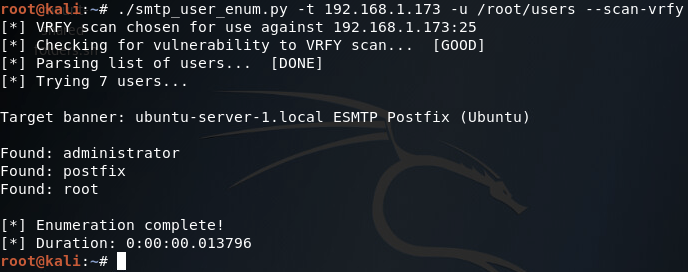
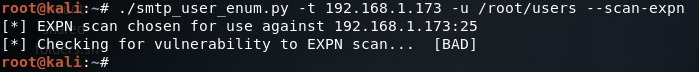
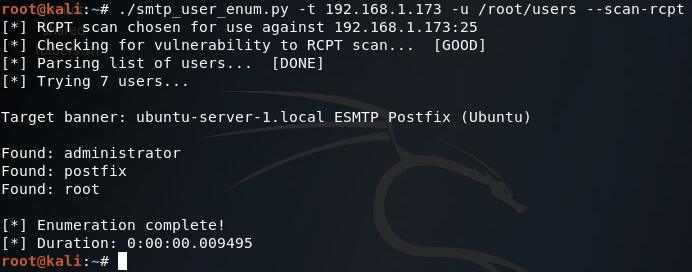
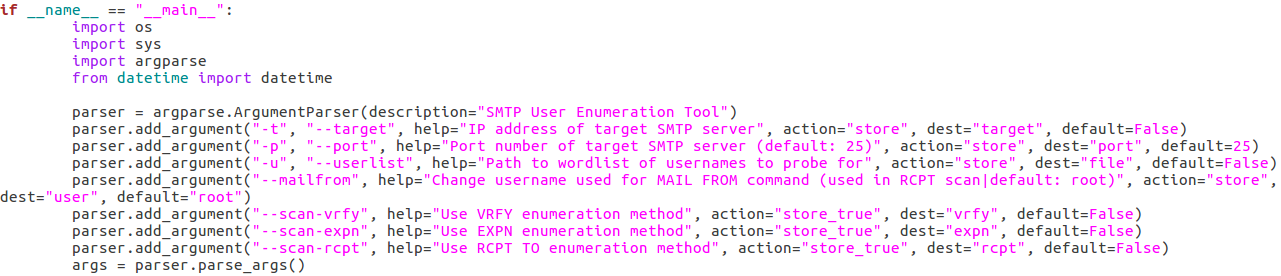 Here we can see that we have seven arguments available when using this script. Firstly, we have the target IP address and port number, then there’s the file path to the word-list containing the usernames to probe for. There is also a switch for each scan type (one of which must be supplied) and finally there is an optional flag to specify the username/e-mail address to use with the RCPT TO method.
Here we can see that we have seven arguments available when using this script. Firstly, we have the target IP address and port number, then there’s the file path to the word-list containing the usernames to probe for. There is also a switch for each scan type (one of which must be supplied) and finally there is an optional flag to specify the username/e-mail address to use with the RCPT TO method.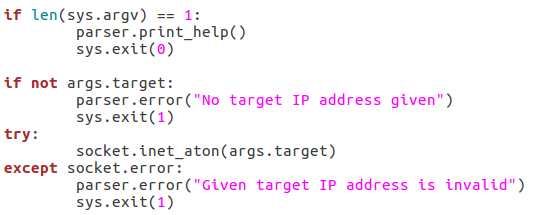

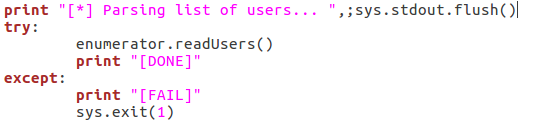
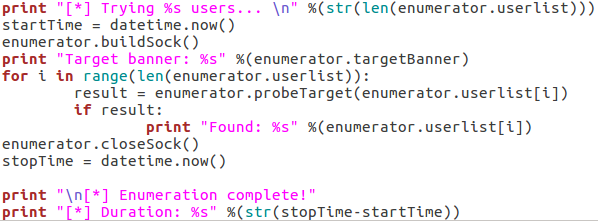
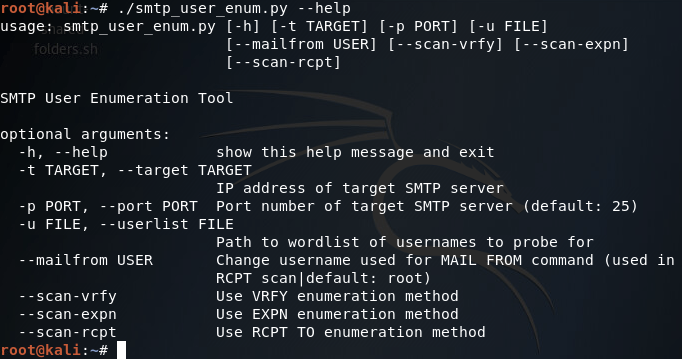
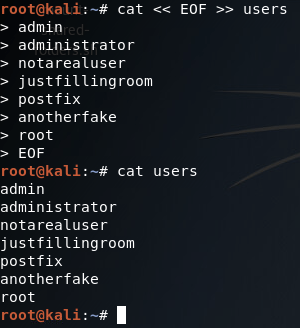

 There are some simple commands that can be entered into a command prompt that will display the contents of your ARP tables on a per-interface basis. For Windows users, simply open a command prompt and enter the following command:
There are some simple commands that can be entered into a command prompt that will display the contents of your ARP tables on a per-interface basis. For Windows users, simply open a command prompt and enter the following command: