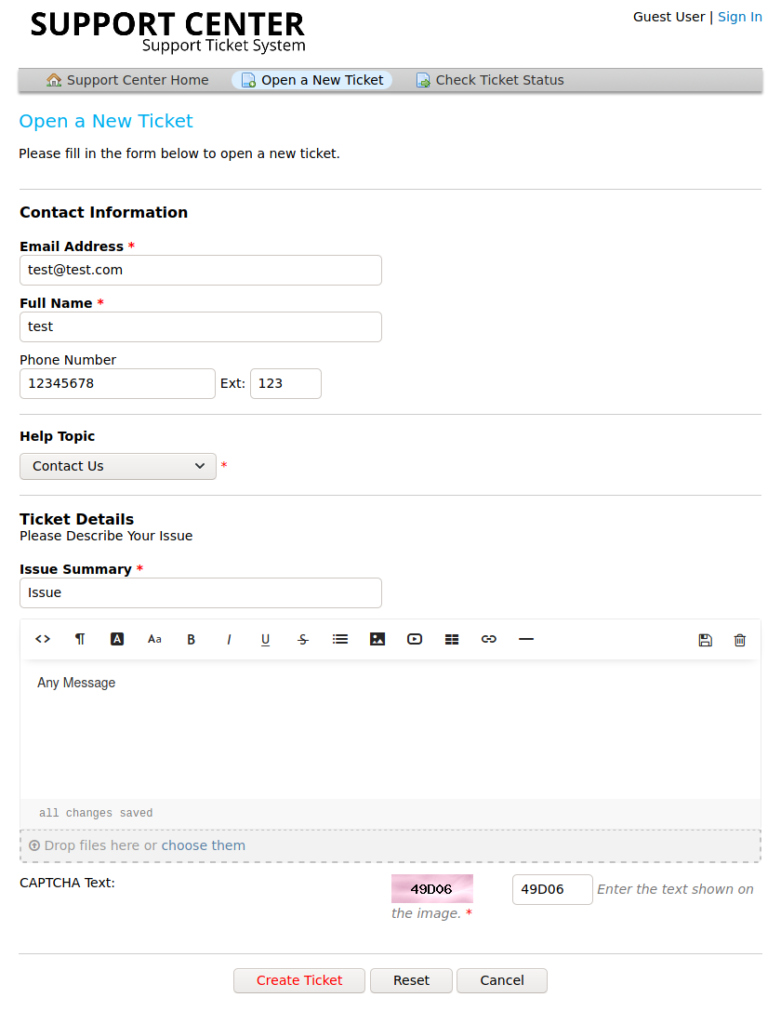
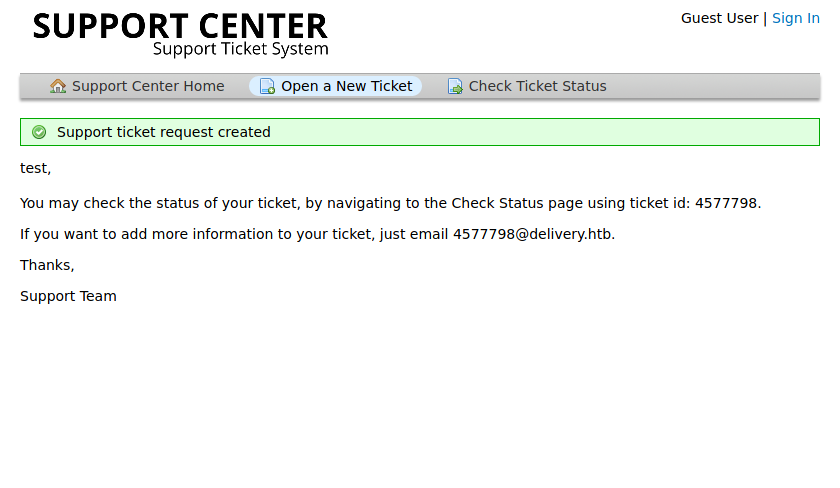
In this booming IT economy the opportunities are out-numbering candidates for those who are applying for cyber security. The covid 19 pandemic has added fuel to this accelerated demand. The report says that these jobs will increase by more than 30 percent in the coming 10 years. Entering into the world of cyber security demands continuous technology awareness and dedication. Here is the comprehensive guide for the beginner’s entry to cyber security.
Image Reference: linkedin
Understanding the process
To unlock a six-figure career in the ever-evolving landscape of technology, a strategic approach involves understanding the pivotal role of learning and continuous upgrading. The crucial first step is discerning the most sought-after roles and requisite certifications before embarking on the learning journey. A common pitfall is the reverse process—earning certifications without a clear direction—which often results in obtaining less in-demand certifications, a scenario marked by wasted time and energy. Thus, the key lies in identifying high-demand roles, assessing their income potential, and then acquiring the necessary skills to thrive in those fields.
The idea is to get knowledge to the extent where even if you dont have experience with a company, you can show your skills to the right employer. Here are the main things to focus:
- Knowledge of programming languages & other important topics
- Learning from dedicated cyber security platforms
- Getting certified to show your abilities
- Subscribing to platforms for updates in cyber world
- Preparing your profile for jobs
Getting Better with Basics
Fresh graduates or individuals that have less experience in T industry need to understand that only cybersecurity knowledge is not going to be enough. Many other important subjects come together to prepare an individual to perform better in cyber world. Here are few points that need to be considered even before starting cybersecurity training.
Networking Knowledge
For newcomers aspiring to venture into cybersecurity, a solid grasp of networking concepts is indispensable. Networking forms the backbone of digital communication, and understanding its principles is foundational for comprehending cyber threats and defenses. Proficiency in networking aids in identifying and mitigating security vulnerabilities, as many cyber attacks leverage weaknesses in network infrastructure. Whether analyzing traffic patterns, detecting anomalies, or implementing robust security measures, a thorough understanding of networking concepts is essential for navigating the intricacies of cybersecurity. In essence, it serves as a cornerstone for building a comprehensive skill set in the dynamic and evolving field of cybersecurity.
Hands-on Practice of Programming Languages
Commonly, there’s a misconception that a fundamental understanding of programming suffices for a cybersecurity career. However, a robust programming proficiency is crucial. In the cyber realm, tasks such as writing malware and conducting secure coding analysis require a deep comprehension of code. A solid programming foundation not only enables individuals to navigate these intricacies but also empowers them to excel in various facets of the cyber world.
Understanding of Database Systems
For newcomers in cybersecurity, a strong grasp of database systems is crucial. Databases house sensitive information and are frequent targets for cyber threats. Proficiency in these systems is essential for effectively securing critical assets, preventing unauthorized access, and responding to potential breaches. Understanding databases is key to formulating comprehensive security measures as threats often exploit vulnerabilities in these systems, making it an indispensable skill for cybersecurity professionals.
Learning from Dedicated CyberSecurity Platforms
Embarking on a journey to learn cybersecurity from dedicated platforms offers a transformative and comprehensive educational experience. These specialized platforms provide curated, up-to-date content that aligns with industry standards and real-world scenarios. Learning from experts in the field enhances the depth of understanding, and hands-on practical exercises hone practical skills crucial for addressing cyber threats. Whether it’s through immersive courses, certifications, or interactive labs, these platforms equip individuals with the latest knowledge and tools needed to navigate the constantly evolving landscape of cybersecurity. By choosing reputable platforms like these, learners not only gain valuable insights but also lay a solid foundation for a successful and impactful career in the dynamic field of cybersecurity.
Here are some platforms that provide training related to cyber security:
- Security Blue Team (Special defensive cybersecurity training provider)
- TCM Security (Special Offensive Security Training Provider)
- Offensive Security (Offensive Security Providers)
- EC-Council
- TryHackMe
- HacktheBox
TryHackMe and HacktheBox are one-of-a-kind platforms that provide training from scratch. HacktheBox platform provides labs to get hands-on practice.
Getting Certified for Better Visibility
Certifications are crucial for showcasing cybersecurity skills post-learning. They provide tangible proof of expertise in a constantly evolving field, offering a standardized measure for employers to assess capabilities. From globally recognized credentials like CISSP to specialized ones from platforms like Offensive Security, certifications convey a commitment to continuous learning and provide a competitive edge in the job market, establishing a credible foundation for a successful career in cybersecurity.
Here are a few certifications that are very important to show your skills to the outside world. One thing to note is that it is up to the individual which side he wants to proceed in his career i.e. red teaming, blue teaming, or others.
- Offensive Security Certifications by https://www.offsec.com/
- OSCP, OSWP, OSEP, OSWA, OSWE, OSED
- Elearn Security Certifications
- ejpt, ecppt, ewpt
- TCM Security Certifications
- PJPT, PNPT, PJMT, PJWT
- GIAC Certifications
- Security Blue Team Certifications
- BTL1, BTL2 and more
Cyber Security and Public Cloud
Mastering public cloud security is vital in today’s cybersecurity landscape. As organizations increasingly adopt platforms like AWS and Azure, understanding the nuances of these environments becomes essential. Cloud security poses unique challenges, requiring expertise in access controls, encryption, and compliance within a shared responsibility model. Proficiency in public cloud security is crucial for effectively safeguarding sensitive data, responding to threats, and ensuring secure cloud deployments. With the continual shift toward cloud computing, this knowledge is imperative for individuals aiming to fortify digital environments against evolving cyber threats.
Following are the security certifications from different cloud providers:
- AWS Certified Security – Specialty
- Microsoft Certified: Azure Security Engineer Associate
- Professional Cloud Security Engineer
Staying Updated with Security News
Staying informed about the latest developments in cybersecurity is vital for professionals in the field. Regularly accessing reputable platforms ensures a comprehensive understanding of emerging threats, vulnerabilities, and industry trends. Some valuable platforms for staying updated include:
- Threatpost: Comprehensive coverage of threats and vulnerabilities.
- KrebsOnSecurity: Investigative journalism on cybercrime and incidents.
- The Hacker News: Trusted source for global cybersecurity news.
- CyberWire: Concise daily briefings and podcasts for professionals.
- Dark Reading: Insights into cybersecurity strategies and threat intelligence.
- Reddit’s netsec: Active community for discussions and diverse perspectives.
- Darknet Diaries has some real-life stories which is the best source of information about what is happening in the real world.
Also, following security professionals on social platforms helps a lot in enhancing abilities as people tend to share information on these platforms.
Learning Security Frameworks
Learning cyber security frameworks is crucial as they provide structured guidelines and best practices for designing, implementing, and managing effective security measures. These frameworks ensure a systematic and comprehensive approach to cybersecurity, helping organizations mitigate risks and enhance their overall security posture. Here are some key cyber security frameworks with brief descriptions:
NIST Cybersecurity Framework (CSF)
Developed by the National Institute of Standards and Technology, it provides a risk-based approach for managing and improving cybersecurity.
ISO/IEC 27001
An international standard specifies the requirements for establishing, implementing, maintaining, and continually improving an information security management system (ISMS).
MITRE ATT&CK (Adversarial Tactics, Techniques, and Common Knowledge)
A knowledge base that describes the actions and behaviors of cyber adversaries, aiding in the understanding and improvement of cybersecurity defenses.
Zero Trust Architecture
A security concept centered around the belief that organizations should not automatically trust anything inside or outside their perimeters and must verify anything trying to connect to their systems.
These frameworks offer structured approaches, enabling organizations to build robust cybersecurity programs and adapt to the evolving threat landscape.
Tools familiarization
Get accustomed to cyber security tools such as Wireshark and Metasploit for network analysis and penetration testing. Tools like OpenVAS and Nessus can be great starting points to learn about vulnerability and its identifying and strengthening process. Here is the list of tools that are good to be familiar with.
Wireshark: Network protocol analyzer for in-depth packet inspection.
Nmap (Network Mapper): Open-source tool for network discovery and security auditing.
Metasploit: Framework for developing, testing, and executing exploit code.
Burp Suite: Web application security testing tool for finding security vulnerabilities.
Snort: Open-source intrusion detection and prevention system (IDS/IPS).
OpenVAS: Open Vulnerability Assessment System for scanning and vulnerability management.
Aircrack-ng: Suite of tools for wireless network security assessment.
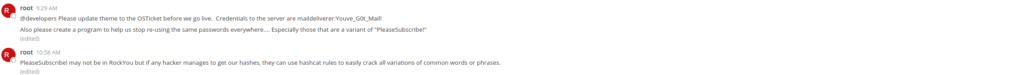
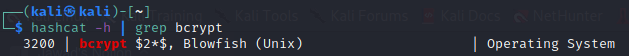
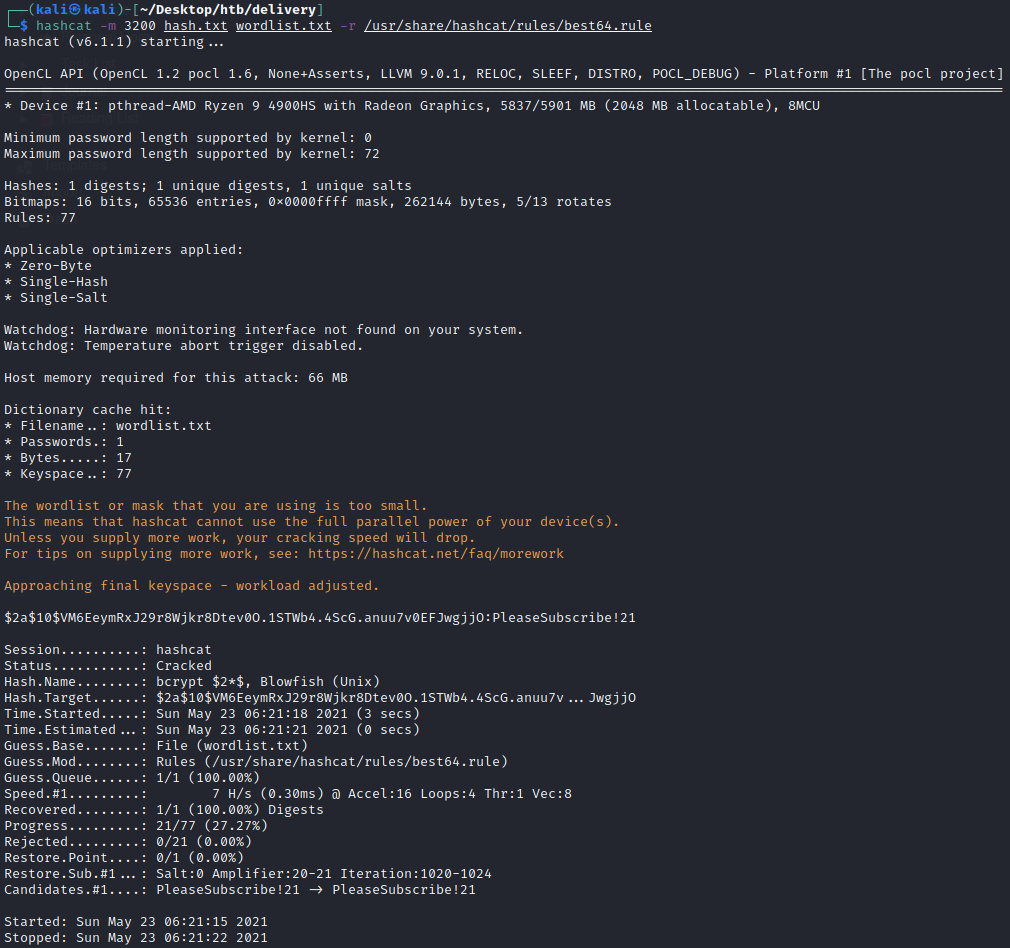
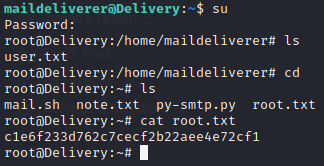
Hashcat: Advanced password recovery tool for cracking passwords.
John the Ripper: Password cracking tool for dictionary attacks.
Sysinternals Suite: Collection of advanced system utilities for Windows.
Tcpdump: Command-line packet analyzer for Unix and Linux.
Ghidra: Open-source software reverse engineering framework developed by the NSA.
Suricata: High-performance Network IDS, IPS, and Network Security Monitoring (NSM) engine.
Zeek (formerly Bro): Network security monitoring tool for packet analysis.
OSSEC: Open-source host-based intrusion detection system (HIDS).
ModSecurity: Open-source web application firewall (WAF) module for Apache and Nginx.
Volatility: Framework for analyzing memory dumps for incident response and forensics.
OWASP Zap: Open-source security testing tool for finding vulnerabilities in web applications.
SniffJoke: SSL/TLS man-in-the-middle attack tool.
YARA: Pattern-matching Swiss knife for malware researchers.
IBM Qradar/SIEM Solutions: For SOC-related jobs
Every tool mentioned above has its usage thoroughly documented in free online sources. A multitude of individuals actively contribute valuable information on platforms like YouTube, making it accessible for anyone seeking to learn about these tools. Whether it’s understanding the functionalities of Wireshark or mastering the intricacies of Metasploit, the wealth of knowledge available online facilitates continuous learning and skill development in the cybersecurity domain.
Create your Profile
Boost your online presence by actively engaging on social media, especially on platforms like LinkedIn. Dive into projects such as building a network, setting up a honeypot, creating a SEIM, or delving into malware analysis or coding. Completing these projects not only enhances your skills but also makes your portfolio stand out. Document your findings and any challenges faced during the projects. Share these insights on your LinkedIn profile and consider publishing them on platforms like Medium, LinkedIn, etc. Actively participate in discussion groups to brainstorm ideas and gain a fresh perspective. Being a visible and accessible figure in the cybersecurity community is key to continuous learning and professional growth.
Takeaways
Entering the cybersecurity domain demands a combination of education, hands-on experience, and unremitting adaptation. Foundational understanding, certifications, and practice form the foundation. Networking, ethical considerations, and soft skills are equally vibrant. Implementing endless learning, specialization, and mentorship leads the journey. By merging these elements, a vigorous entry into cybersecurity is constructed—a passage filled with challenges, growth, and the promise of protecting digital landscapes. Every industry has its limitations and benefits but the best of working in cyber security surpasses the limitations.