Delivery is an easy level box that is beginner friendly with assigned IP of 10.10.10.222. It requires creative thinking to solve it. It presents a helpdesk and a Mattermost instance. Creating ticket on helpdesk, mail is received to update the ticket that can be used to create Mattermost account. The Mattermost contains the important conversation disclosing SSH creds. These creds will be used to access the box and then privilege escalation will be done with some cool stuff.
nmap scan
First run nmap scan with following command
nmap -sV -sC -A -T4 -p- -oA nmap_scan 10.10.10.222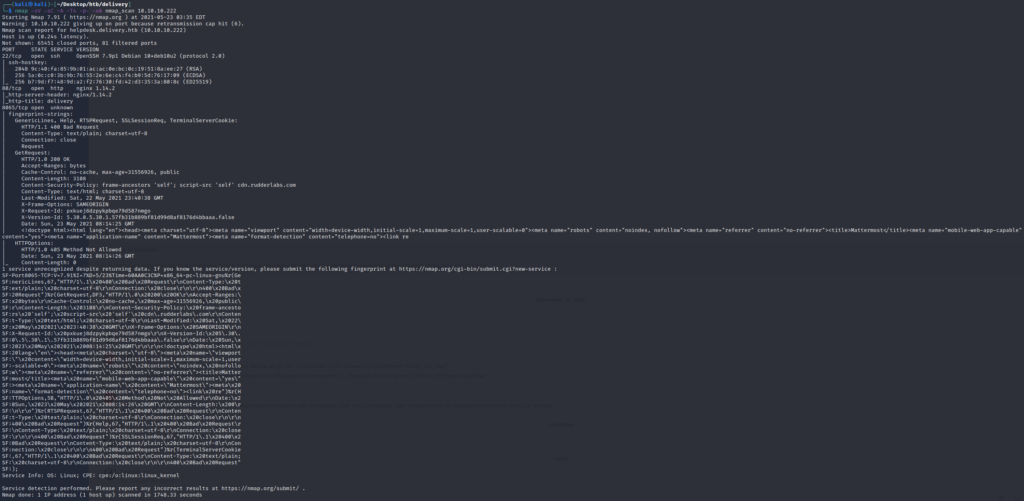
Delivery Website
Go through the web service associated with this IP
On the front page, there’s a link associated with HELPDESK (helpdesk.delivery.htb) pointing to an account. So we make an entry to our /etc/hosts file as follows

Now we can directly open the website with http://delivery.htb
Also there’s a CONTACT US button and clicking on the button we are navigated to http://delivery.htb/#contact-us
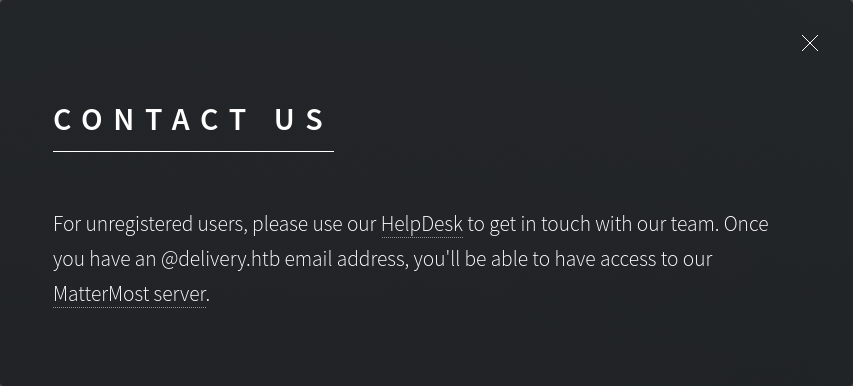
Here we get the message that for unregistered users, use HelpDesk to contact the team. And once we have an @delivery.htb email address, we can access the MatterMost Server which is hosted on http://delivery.htb:8065
So far we have got following items of interest
- helpdesk (http://helpdesk.delivery.htb)
- We need to get an email address from here
- MatterMost Server (http://delivery.htb:8065)
Now we view page source and go through the code to find something of interest. First of all we check source code of front page
Here we see 2 article tags with IDs contact-us and elements. We have got the contact-us but there’s no navigation for element. So we go to http://delivery.htb/#elements and get the following page
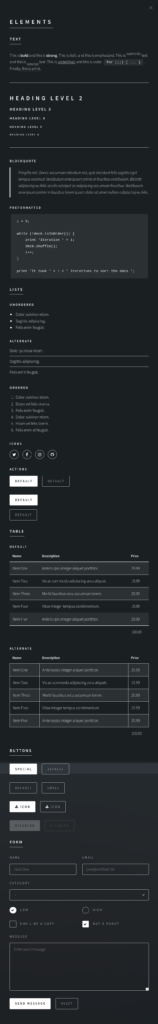
Here interesting thing is the messaging form at the end, and here we get in placehohlders some values
- Name: Jane Doe
- Email: jane@untitled.tld
And submitting the form with data, it gave 405 Not Allowed error. Going through the source code for this revealed that this form was posting data to http://delivery.htb/# It seems like a rabbit hole
Delivery Helpdesk
Now we go to http://helpdesk.delivery.htb and get the following page
Here we have following options available
- Sign in
- Open a New Ticket
- Check Ticket Status
So we first go to Sign in option
As we don’t have an account, we register for an account
Upon registration, we get the following message
We put a dummy email here and don’t have any access to the email. So for the time being, we move to the next option available i.e. Create a New Ticket
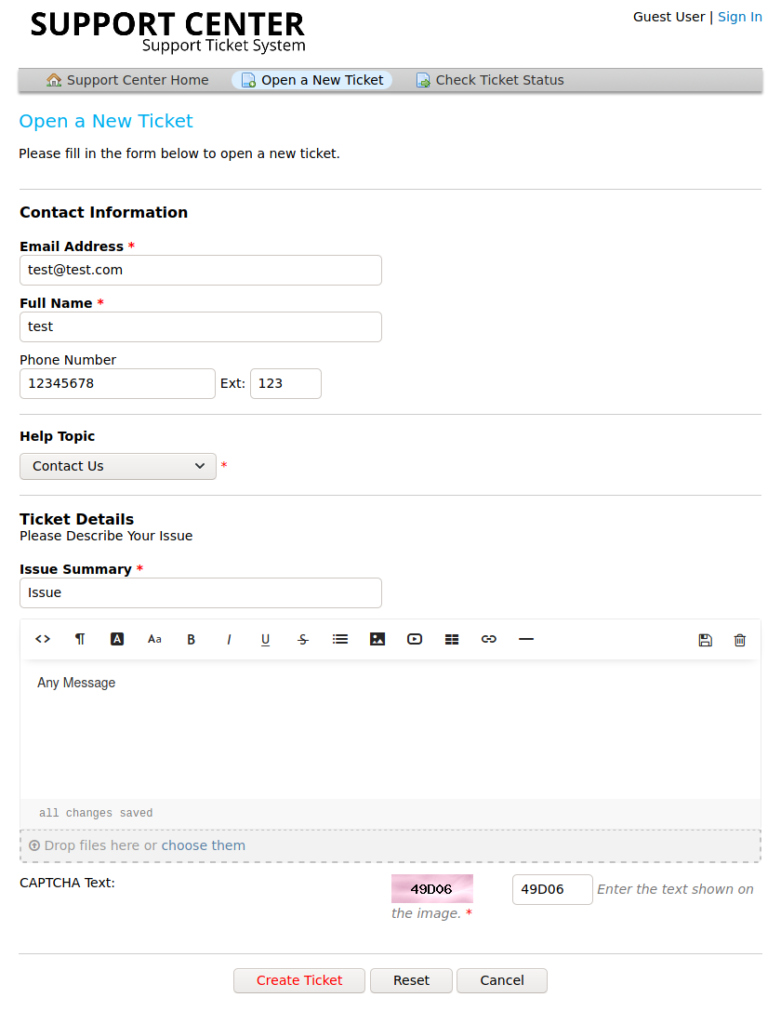
After creating the ticket we get the following feedback message
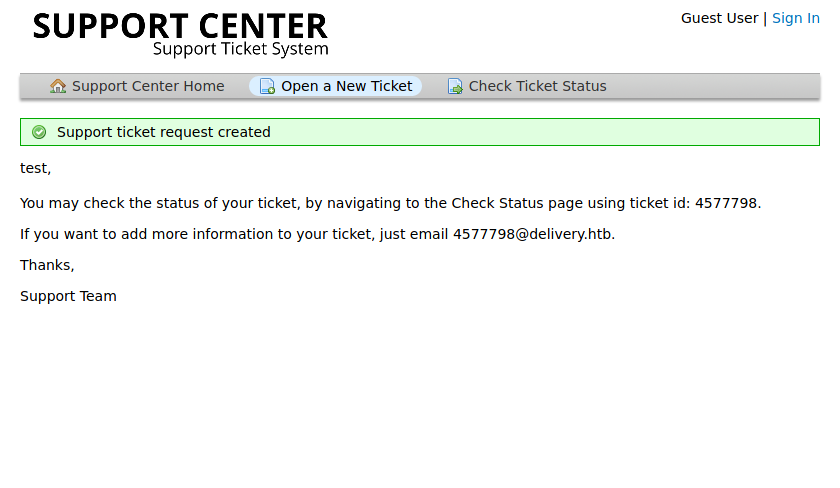
It has given us a ticket ID: 4577798 and an interesting support email: 4577798@delivery.htb
Now we go to Check Ticket Status to see if we get anything
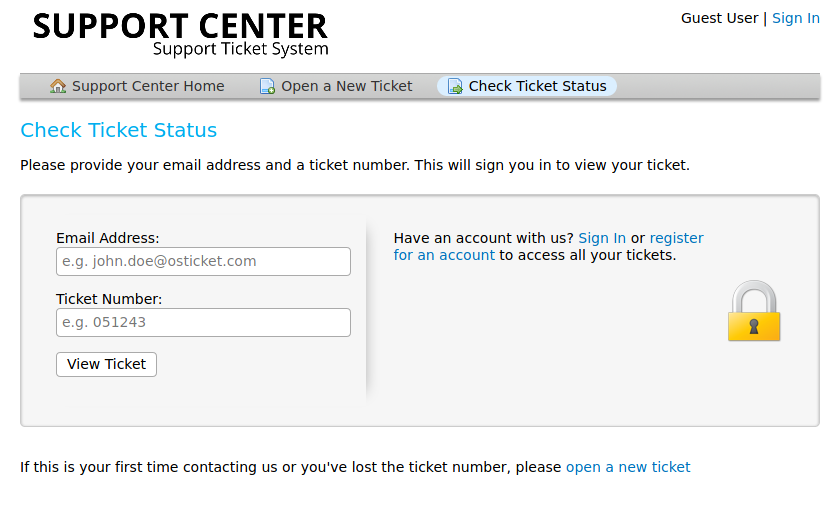
Here we get the form with 2 fields email and a ticket number. Put both inputs with the values we got from the Create Ticket feedback
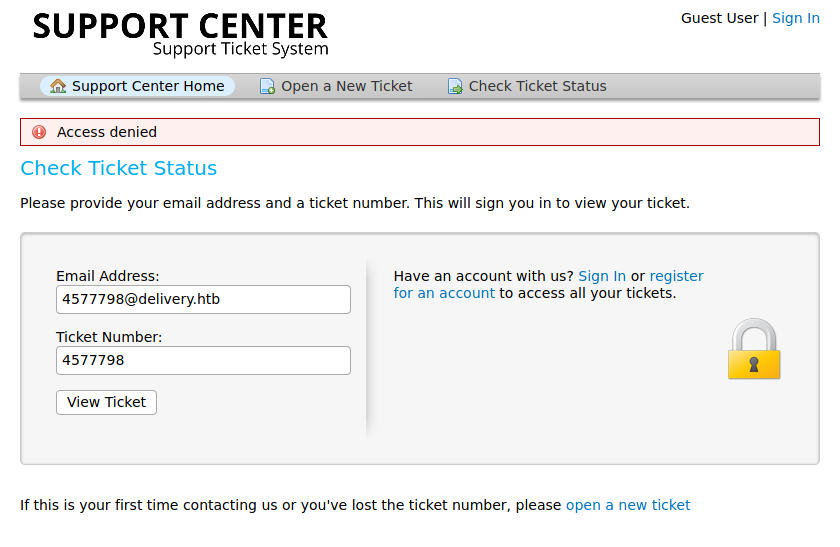
We get Access Denied ☹️
Try putting the email address that we used for registration
Now, we get access to the Ticket Status dashboard (I created a new ticket with email: demo@demo.com, name: demo, phone: 1234567890, ext: 123)
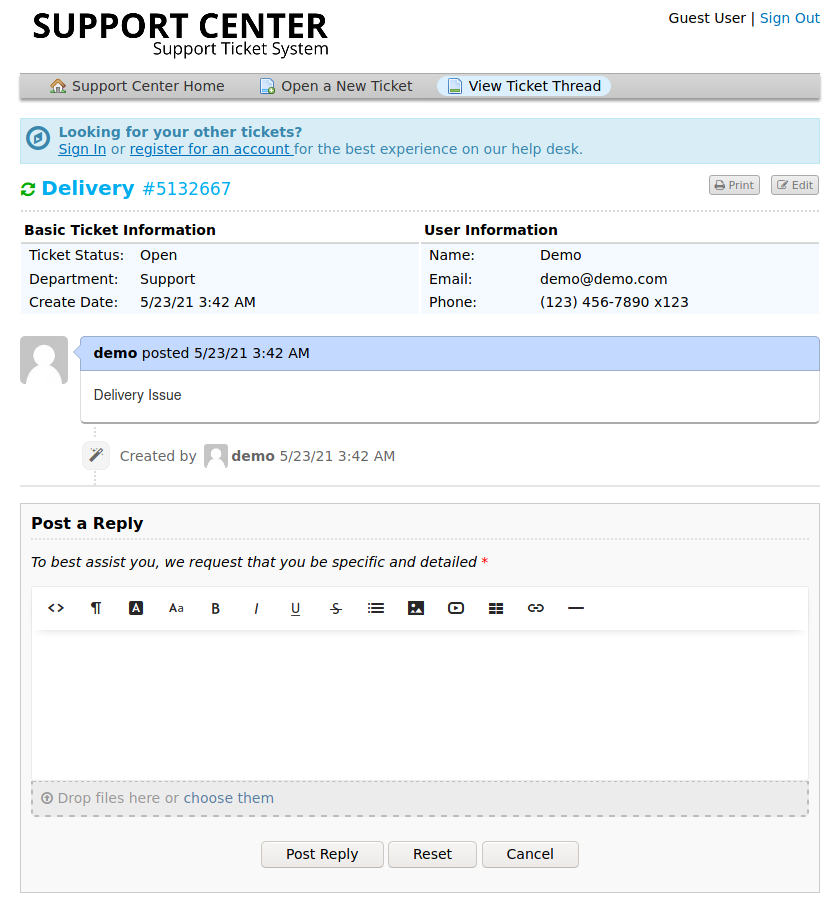
After going around this portal, I found nothing.
Delivery Mattermost
Let’s go to MatterMost server and register for an account with delivery.htb email
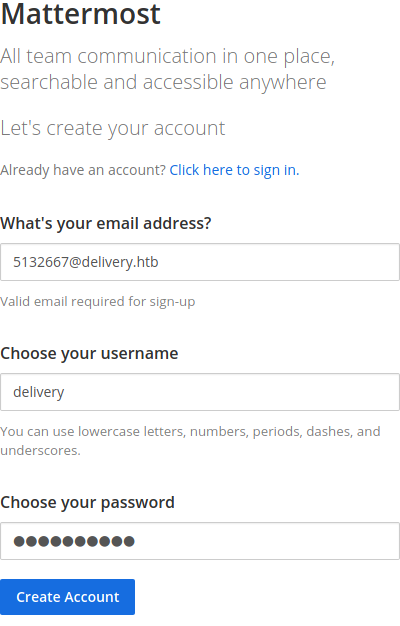
As soon we create the account, we are given feedback that a verification email has been sent to the provided email
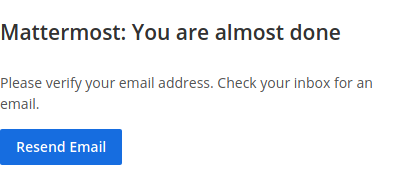
So we go back to the helpdesk and refresh the ticket thread and we get the verification link
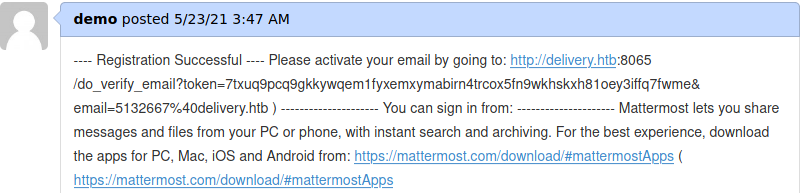
We can see that the verification link is in the first line up to 3rd line. So we copy that link and navigate to it
The email has been verified. Now we login to the MatterMost Server using the credentials email: 5132667@delivery.htb, password: Demo@12345
We can join Internal Team, So we click that and we get the following page
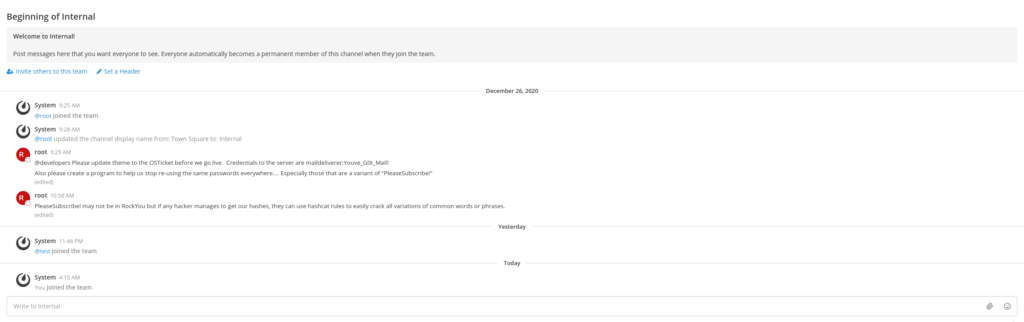
It looks like a conversation going on.
There’s a message from root that Credentials to the server are maildeliverer:Youve_G0t_Mail!
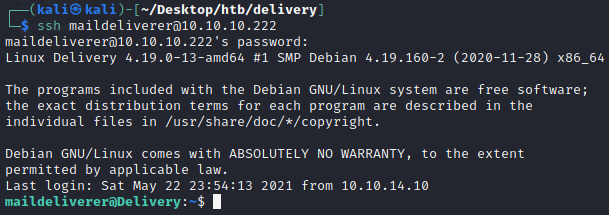
Also from nmap scan we know SSH is running on the system. So we try these credentials in SSH
- user: maildeliverer
- password: Youve_G0t_Mail!
Delivery – User Flag
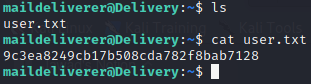
We have got the initial access. We look for the user flag and get it as follows
Privilege Escalation
Now for privilege escalation, we first check sudo permissions for this user
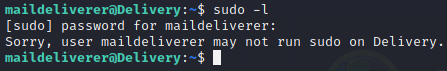
It looks like we don’t have any sudo permissions
Now we run linpeas
We get the following interesting items
- MatterMost is running and its path
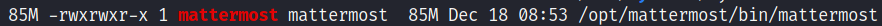
- Mysql is running
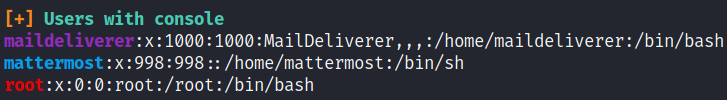
- 3 users with console
- Sudo version potentially vulnerable
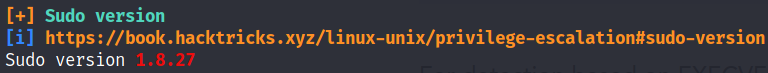
Now that we have all these items, we check sudo vulnerability, but unfortunately, it is not vulnerable
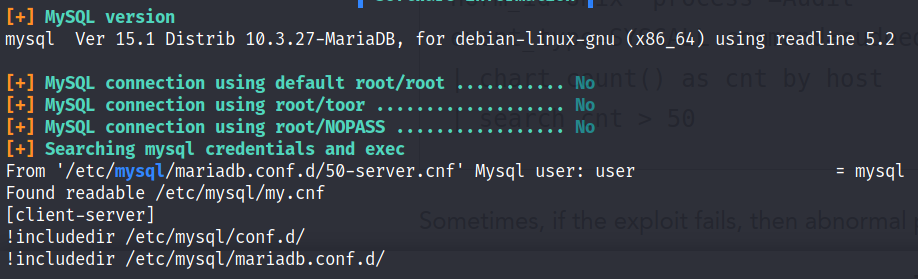
Then we check mattermost config file in /opt/mattermost/config/config.json and we find the SQL Settings as
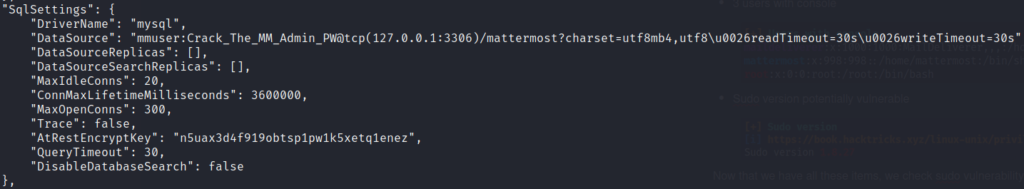
Here we get the SQL credentials
- user: mmuser
- password: Crack_The_MM_Admin_PW
So we login to mysql with these credentials as follows
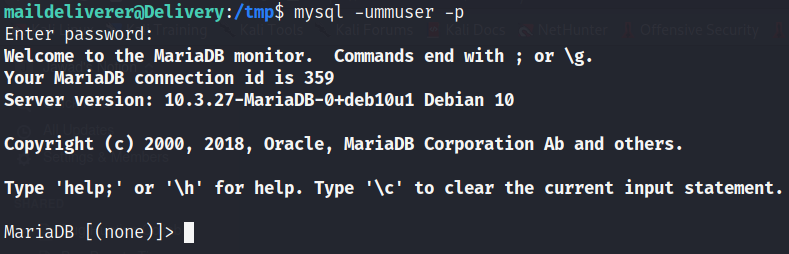
We have got access to the database
Now we check for root password if there’s any in it
First, we check all databases
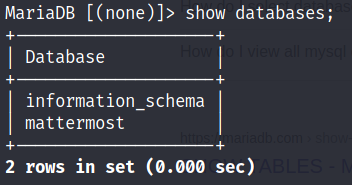
Use mattermost db as follows
Show tables as
We have a table Users. So we write a query to list all users. The result was very jumbled up but the root user was found and the final query for the root user was
SELECT username, password FROM Users;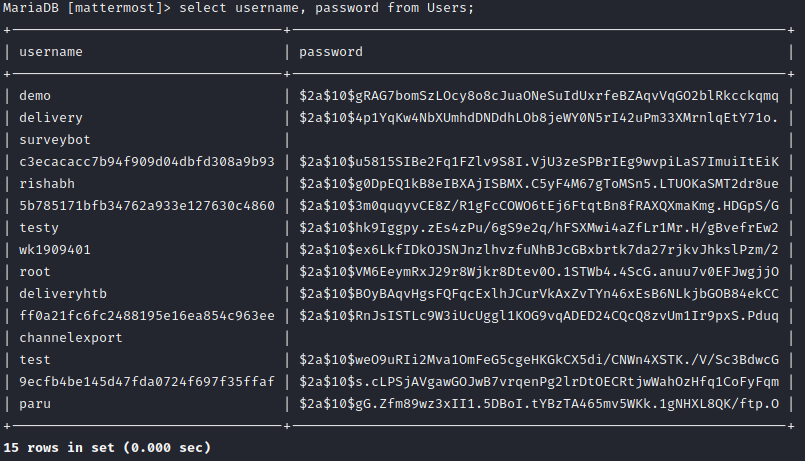
So we have the hash of root’s password as
$2a$10$VM6EeymRxJ29r8Wjkr8Dtev0O.1STWb4.4ScG.anuu7v0EFJwgjjOAlso from MatterMost dashboard conversation, the root user sent a message saying
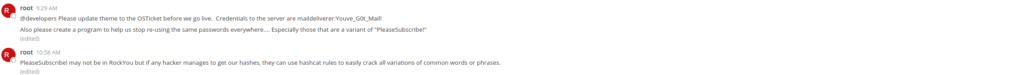
It says to create a program to stop re-using the same password specially those variants of PleaseSubscribe! and it may not be in rockyou but if hacker manages to get it, they may use hashcat rules to crack it
Cracking Password Hash
So we use hashcat rules to crack the hash. But before that we identify the hash type so that we may specify the hash mode in hashcat
Using hashid, we get to know that the hash is bcrypt.
Now in hashcat we need to provide mode for bcrypt so we find mode for bcrypt as
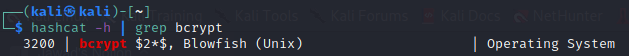
So 3200 is the mode for bcrypt. Now we put hash in hash.txt, PleaseSubscribe! in wordlist.txt and use the rule best64
So combining all this we get the following output
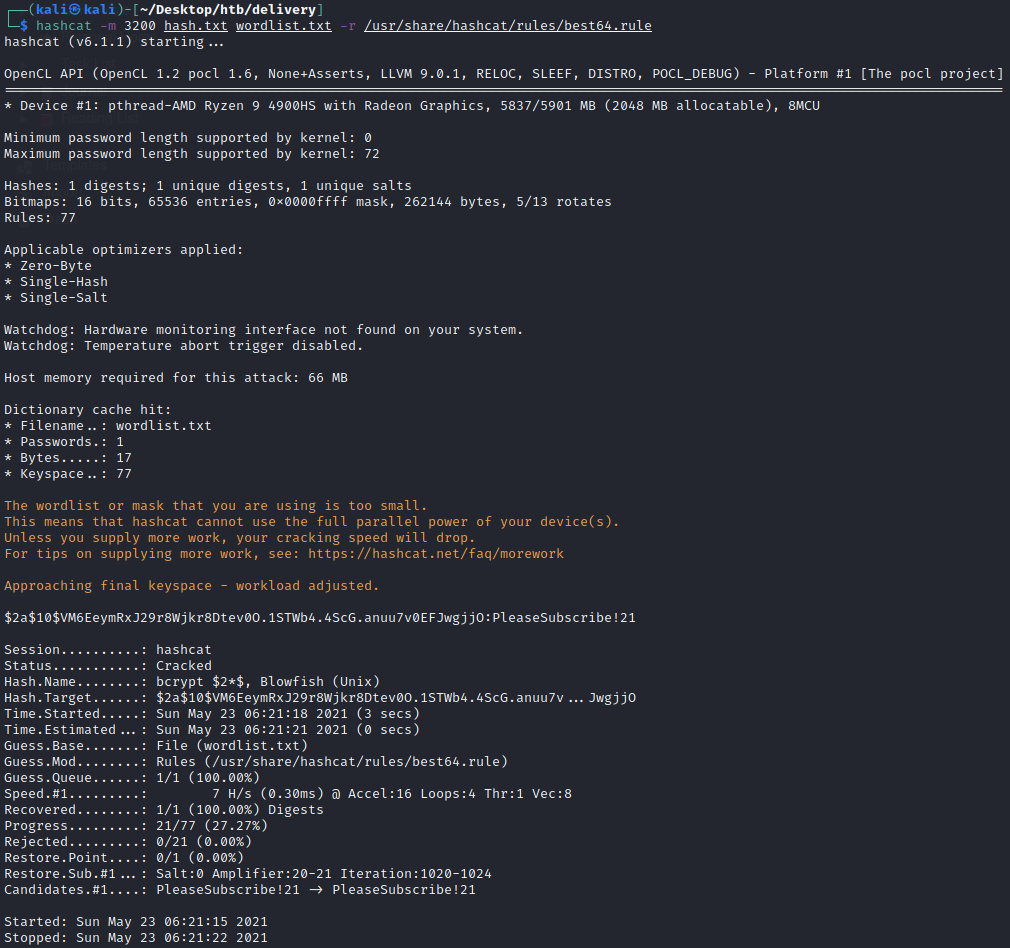
The password is PleaseSubscribe!21
Delivery – Root Flag
We use it to login to root user and get flag
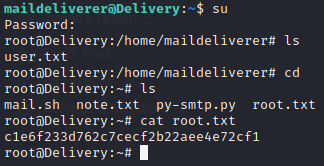

Leave a Reply