Welcome back everyone! In the past few articles, we covered the basics of Ruby and built our own port scanner. This was to solidify the mechanics behind port scanning. Now that we have that concept down, it’s time to move on to host discovery (otherwise known as network enumeration). Host discovery is as simple as it sounds, we’re going to discover hosts. Before we do that, we’ll need a definition as to what exactly a host is.
Well, a host is a computer connected to a network. It’s that simple. The idea of host discovery is the process of finding out what hosts are on the network. This is used when you don’t know where your target is. If you’re on the same LAN as your target, but don’t know their local IP address, you can implement one of the two tactics we’re going to cover here today in order to find them.

As I previously stated, we’re going to be demonstrating two different kinds of discovery tactics. We’re going to cover ping scans, and ARP scans. We’ll start with ping scans, as they are the easiest to understand, and then we’ll ease our way into ARP scans. Let’s get started with ping scans!
Tactic 1: Ping Scans
We briefly covered ping scans in the first recon article, but now we’re going to go a bit more in depth. A ping is when one host on a network sends an ICMP (Internet Control Message Protocol) request to another host. This request is used to determine if a connection can be established between the two hosts. It’s worth noting that many firewalls will block ICMP (ping) requests, so ping scans are not recommended.
But, if no firewalls are in place, we can systematically send pings to every IP address that may be on the network. We’re going to be using nmap to perform our ping scan. If you remember from the first article, we used the -sn flag to disable port scanning. which effectively launches a ping scan. We’re only going to be scanning for other hosts on our subnet. A subnet is a logical network that is a smaller part of a bigger network. A single network can consist of multiple subnets. Since we’re only scanning for hosts on our subnet, we need to know the subnet mask. We can find this information by looking at the output of the ifconfig (Interface configuration) command. We’re only going to view the last 10 lines of the output, as this contains the information we need:
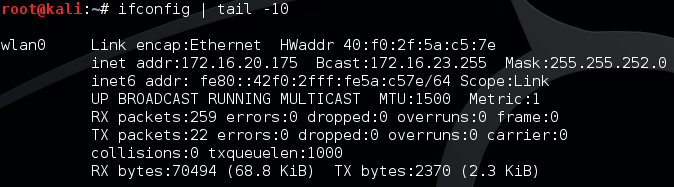
We can see that our local IP is 172.16.20.175 and our subnet mask is 255.255.252.0. Now that we have these, we can feed them into nmap to scan our subnet! Let’s take a look at the command we’re going to use to launch our scan:
![]()
Alright, we can see here that we’ve launched nmap, we’ve given the -sn flag to signify a ping scan, and we’ve given our local IP followed by our subnet mask represented in CIDR notation as /22. You may notice the > nmap.txt at the end of the command. This will make a new file called nmap.txt and will write all the output to it. Doing this means that we don’t have to scan more than once to see the results! Let’s take a look at the last 9 lines of the nmap.txt file and see some of our ping scan results:
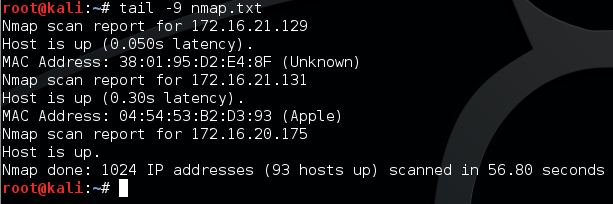
Here we can see that our ping scan returned quite a few hosts. There are many more in this file, but we’ve only viewed the last 3 results. Now that we know how a ping scan works, let’s move on to a more subtle way to scan for internal hosts, the ARP scan.
Tactic 2: ARP Scans
ARP (Address Resolution Protocol) is used to resolve an IP address to a MAC address. The IP address is the logical address of the host, and the MAC address is the address of the actual, physical NIC of the host. If we want to find what IPs are on the network, we can send out ARP requests to every IP and see which ones respond. My personally favorite tool for launching ARP scans is netdiscover, so we’re going to use that.
Since we already found out the subnet information earlier, we can use it here too. First, we need to find out what flags/switches netdiscover needs in order to scan. We can usually access a help page by giving the -h or –help flags. Netdiscover uses -h. We’re going to filter out any unnecessary output by using the grep command. We’re only going to display lines that contain the words “network” or “range”. Let’s take a look at this command and it’s filtered output:
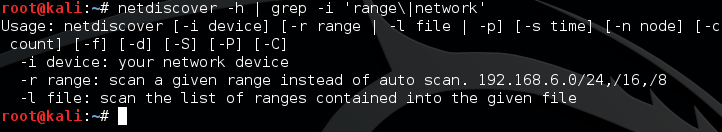
Here we can see the switches that we need to give. We need to give -i followed by the network device (interface) that we want to use, which in this case is wlan0. We also need to give the -r flag, followed by the range of IPs to scan. It’s important to note that netdiscover can only scan /8, /16, or /24 ranges. Since our last range was /22, we’re just going to move it up to /24. Now that we know what flags/switches and information we need, let’s take a look at the command we’ll use to launch our ARP scan:
![]()
Now, let’s execute this command, wait a few seconds, and look at the output:
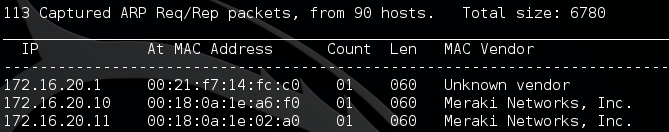
We can see here that netdiscover has successfully captured 113 ARP requests/replies. These packets contain all the information needed to see what hosts are on our network. Here we can only see the first three results, as there was much more.
We covered some pretty handy things here. We covered ping scans in depth, and then we covered the basics of ARP scans. Since ARP scans are preferred over ping scans, we’re going to need a deeper understanding of how they work, so we’re going to build our own ARP scanner! We’re going to build it in Python with the Scapy library. This means that the next few articles will teach the basics of Python and the basic usage of Scapy. I’ll see you there!

Leave a Reply