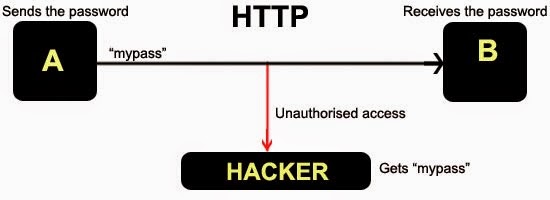
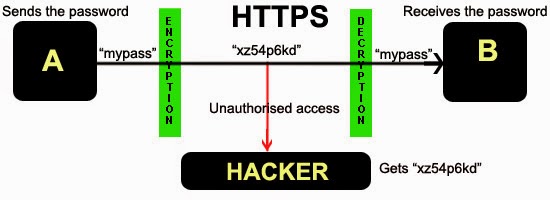
In April 2014, vulnerability in OpenSSL, the cryptographic Software library, was found code named HeartBleed.
[highlight]About OpenSSL:[/highlight] : OpenSSL is extensively used with web applications and web servers for the Implementation of SSL/TLS, hence responsible for the transmission of the data in encrypted form over web.

[highlight]HeartBeats in Open SSL: [/highlight]For SSL to work, your computer connects and transfers data in form of HeartBeats that are basically making the server aware that the client is up and running. These Heartbeats are small data packets sent back and forth between web servers and Clients to make sure the connection is still working. (Consider these heartbeats as the Keep-Alive Packets)
[highlight]Enter HeartBleed : [/highlight]
The servers could be fooled into sending system-stored data in response to a Heartbeat ping — data which could include passwords, encryption keys and other sensitive data.
This allows the Attacker to read the memory of the servers implementing OpenSSL. This unauthorized access to the memory gives attackers the Secret keys, allowing them to Decrypt on SSL connections, and deliver the usernames and passwords.
Heartbleed allows attackers to recover data blocks of up to 64 kb, which is sent in response to a malcrafted Heartbeat Request.
The number of such Heartbeats that an attacker can send to the vulnerable server is practically unlimited. Hence HeartBleed Vulnerability opens doors for hackers to get sensitive information about the users of a Vulnerable web Server implementing OpenSSL.
Another way of exploiting HeartBleed Vulnerability is to obtain the Private Key for the Digital Certificate of the Webserver (implementing OpenSSL with Heartbeat Plugin) , then using it in Man In the Middle Attack to Decrypt the HTTPS Traffic .
Two thirds of the Webservers have been affected by the HeartBleed Bug in OpenSSL including websites, email providers and Instant Messaging Services.
Open SSL Versions Affected by the Heartbleed Vulnerability: OpenSSL versions 1.0.1 through 1.0.1f contain the vulnerability.
Remediation of HeartBleed bug
- Update and Recompile Systems/Servers using the Vulnerable Versions of Open SSL without the Heartbeat extension.
- Replace all the certificates -regardless of issuer- on web servers (mitigate the risks of security breach).
- Reset passwords to SSL and code-signing management consoles.
Lastly, HeartBleed is not Vulnerability in SSL/TLS, but rather a bug in OpenSSL HeartBeat implementation. SSL/TLS is still the DE-FACTO standard for encrypting the data over HTTP/Internet, and SSL/TLS is not broken.
SSL/TLS is not broken, yet.