VPN is a good option for your Privacy but not a good option for your Anonymity as its only a single hop and your VPN provider may cooperate with law enforcement. TOR (The Onion Routers) mixes the traffic in a better way making it difficult for anyone to track you, but there are some point of failures in TOR like exit node can see your all of your traffic. And country like China has blocked TOR making it really hard for its citizens to use it for anonymity. In this situation, using combination of TOR and VPN can solve many problems for it users. There are two different scenarios in which a VPN can work with TOR network, both have their own PROS and CONS.
Tor over VPN
In this scenario, you connect to your VPN first and then you connect to the TOR Network. you can configure both TOR and VPN on any Computer or Server like Amazon EC2.
Pros
- If your Country or Organization restricts Tor, then you can hide that using a VPN.
- Tor entry node can’t directly see your IP.
- Your ISP can’t see that you’re using Tor, they only see that you’re using a VPN
Cons
- Un-Encrypted traffic is still vulnerable to malicious Tor Nodes
- Difficult to setup for non-technical person.
Setting Up
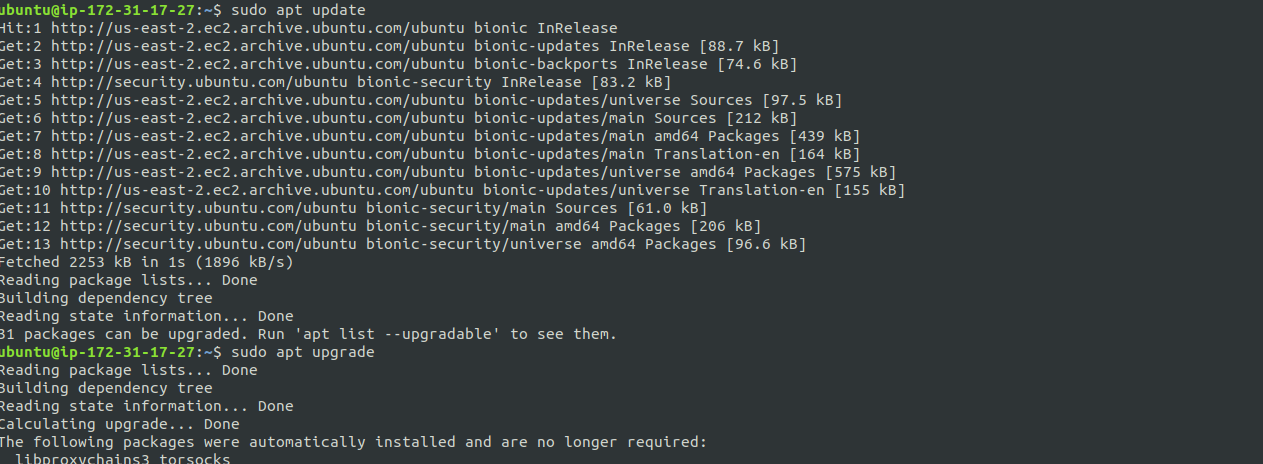
For the setup you’ll need AWS EC2 or any Server (Linux preferred). First you need to download some necessary packages and scripts for easy installation of Tor. Connect to your server and type
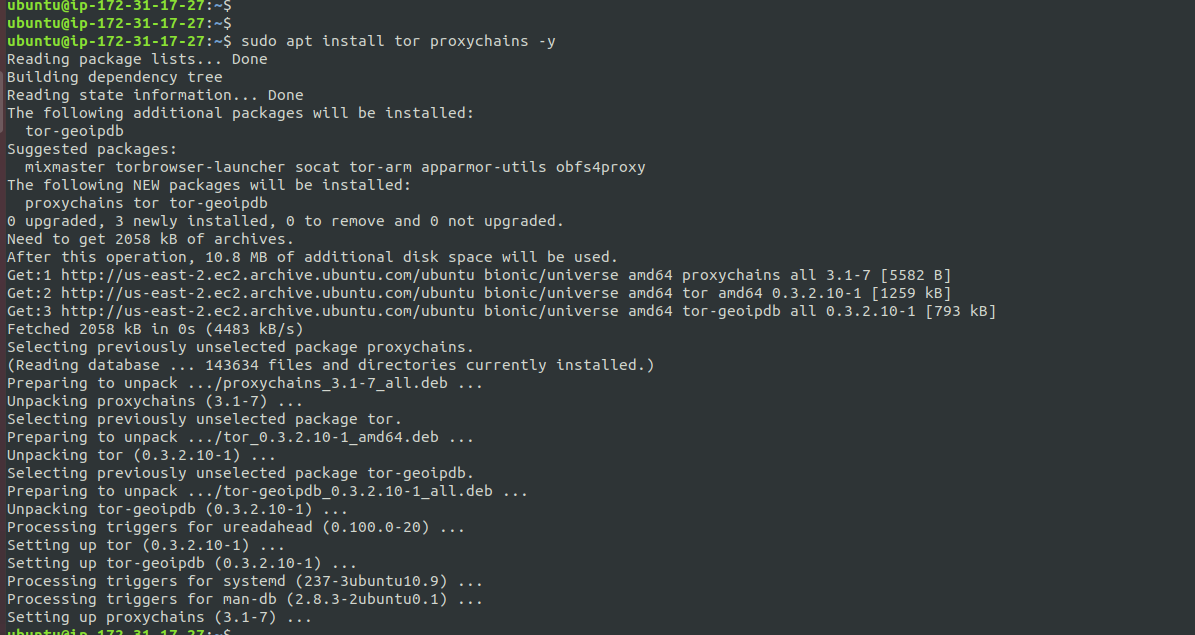
sudo apt update sudo apt install tor proxychains -y
Now run
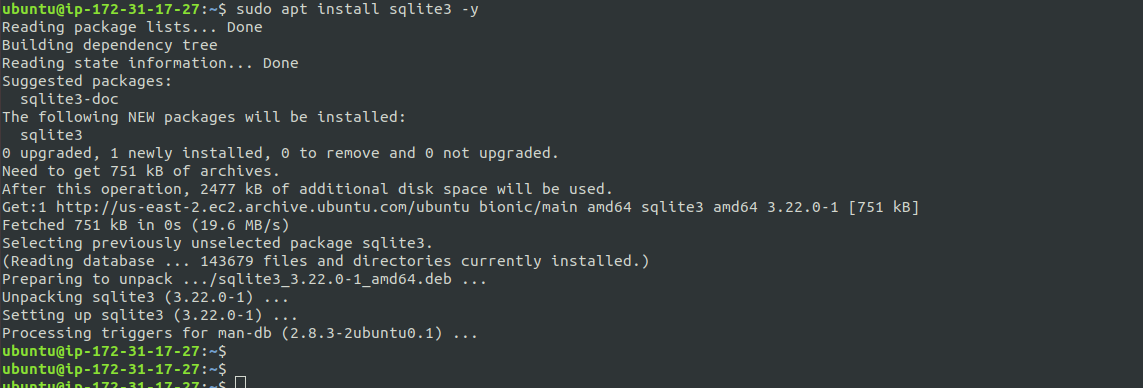
sudo apt install sqlite3 -y
Now we’ll use a script 4nonimizer to configure Tor on our server. Just type
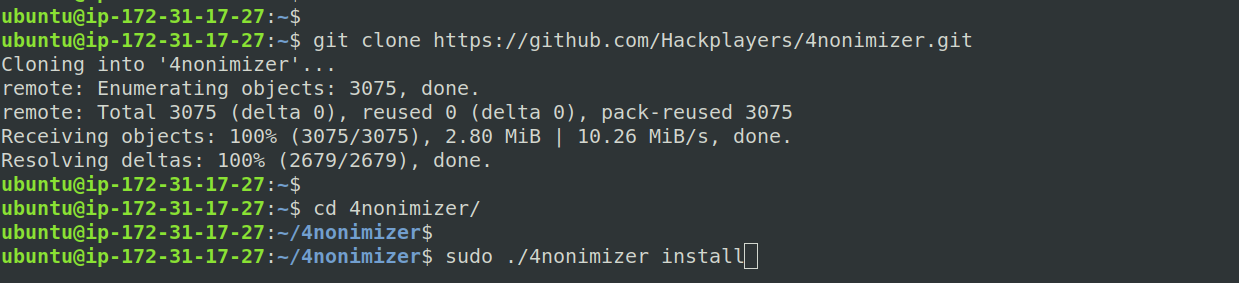
git clone https://github.com/Hackplayers/4nonimizer.git cd 4nonimizer/ sudo ./4noniminer install
It will automatically configure Tor and install necessary packages. Following is the list of command you can use for 4nonimizer.
Usage: 4nonymizer <parameter> install: Install the script in run services uninstall: Disable run service and remove app directory change_provider: Change VPN Provider change_ip: Change IP from VPN current vpn_status: Check IP and provider VPN running update_vpns: Update all ovpn of VPNs start: Init the 4nonimizer service stop: Stop the 4nonimizer service stop_nonet: Stop the 4nonimizer service and shutdown network interfaces restart: Restart the 4nonimizer service update_app: Update this program via git privoxy: Install and configure privoxy with port 8118 (BETA) proxychains4: Install and configure proxychains4 for default in the system browser: Fire up a firefox browser with profile privoxy -> tor test_availability: Check peers availability and delete ovpn file if the IP/service is unreachable location: Now you can select a specific country or continent of the vpn peer enableboot: You can enable service in boot disableboot: You can disable service in boot enable_dnscrypt: Enable dnscrypt service disable_dnscrypt: Disable dnscrypt service
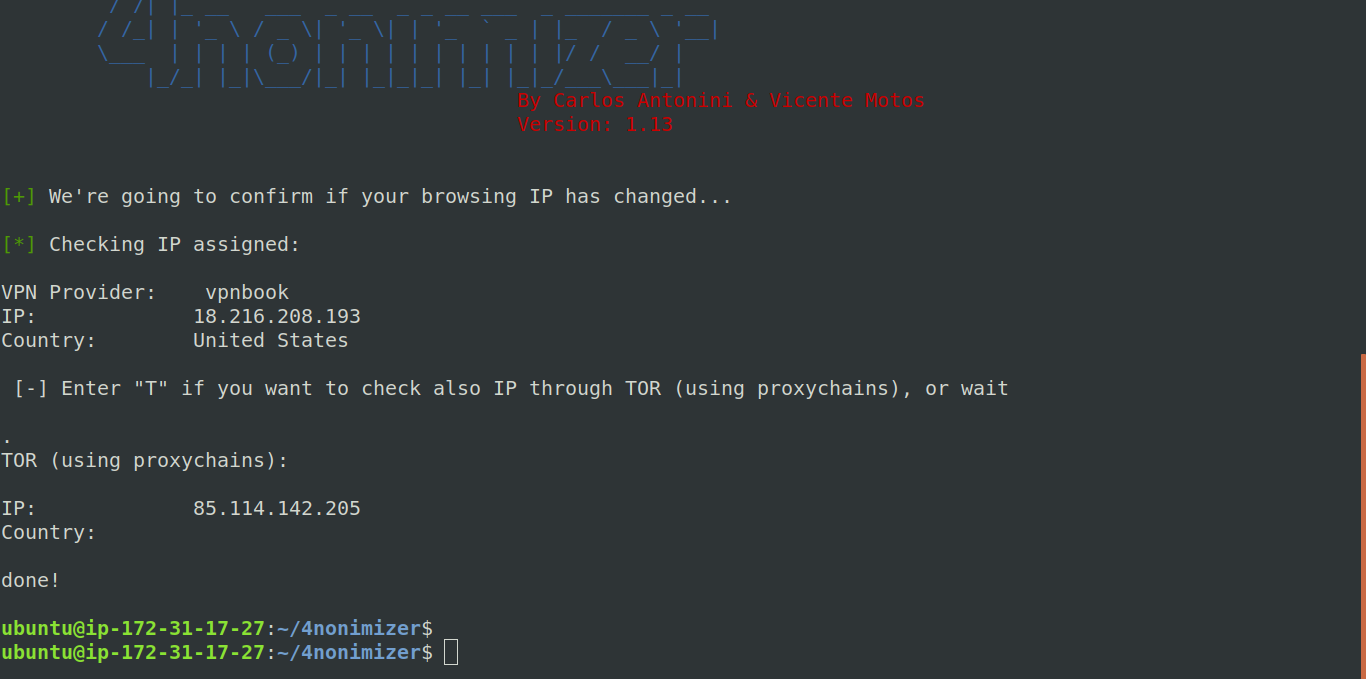
To check your IP on Tor, type this
sudo ./4nonimizer vpn_status
and type T
Now here’s how to setup an OpenVPN that you’ll be using to connect to Tor. Just select your port as “443” if you have a firewall restriction.
VPN over Tor
In this scenario, you first connect to Tor and then to your VPN. To setup VPN over Tor, you don’t need any Server or Cloud.
Pros
- Tor exit nodes can’t see your traffic as its encrypted by VPN.
- Your ISP can’t see your real IP.
Cons
- You can’t access Tor hidden services and directories.
- Not all VPN providers allow this setup.
- Slow connection.
- Guard nodes can see your real IP.
Setting up
You need to connect to Tor first, then you connect to the VPN. Just download Tor Browser Bundle and VPN connection pack. Then start the tor network and then initiate VPN connection. If you want to install Tor on Kali Linux and use a Kali Linux VPN be sure to view those specific tutorials.