
What is a Pentest? – Simplified Guide
What is a penetration test? A penetration test, or a pentest for short, is an authorized simulated cyber attack against

What is a penetration test? A penetration test, or a pentest for short, is an authorized simulated cyber attack against
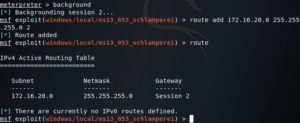
Today we’re going to be going over something I’ve been working on for a while, pivoting. First, we’ll discuss what
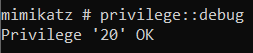
Credential dumping from a compromised target has never been more effortless until the release of the great tool Mimikatz. The
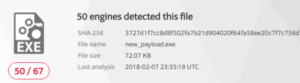
In this edition of our journey in learning how to use msfvenom we are going to talk about obfuscating payloads