
Maintaining Access Part 1: Introduction and Metasploit Example
Welcome back my fellow hackers! Today we’re going to be starting the topic of maintaining access. First, we’ll discuss the concept

Welcome back my fellow hackers! Today we’re going to be starting the topic of maintaining access. First, we’ll discuss the concept

Welcome back my fellow hackers! In the last installment, we built a fork bomb to introduce ourselves to the USB
Hello, my fellow hackers! Today we’re going to be covering a little bit of Wi-Fi hacking. Specifically, we’re going to
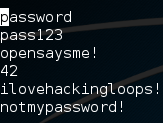
Welcome back my fellow hackers! Today we’re going to discuss the concept of brute force attacks by building our very