One of the most controversial spyware recently pushed Apple for an emergency software update. “Pegasus”, an Israeli malware, was detected breaching the security system, jailbreaking and transmitting files remotely. The NSO Group developed the spyware, and as an update, Apple recently launched a new patch in iOS to fight Pegasus.
Shockingly, a list was found with information of over 50,000 high authority personnel including the Prime ministers, Judges, Journalists, human rights activists and other government figures. It is unsure if everyone on the list was compromised, maybe some are subject to the future. Cybersecurity experts and Black Hat hacker groups confirmed Pegasus by comparing previous data and its pattern.
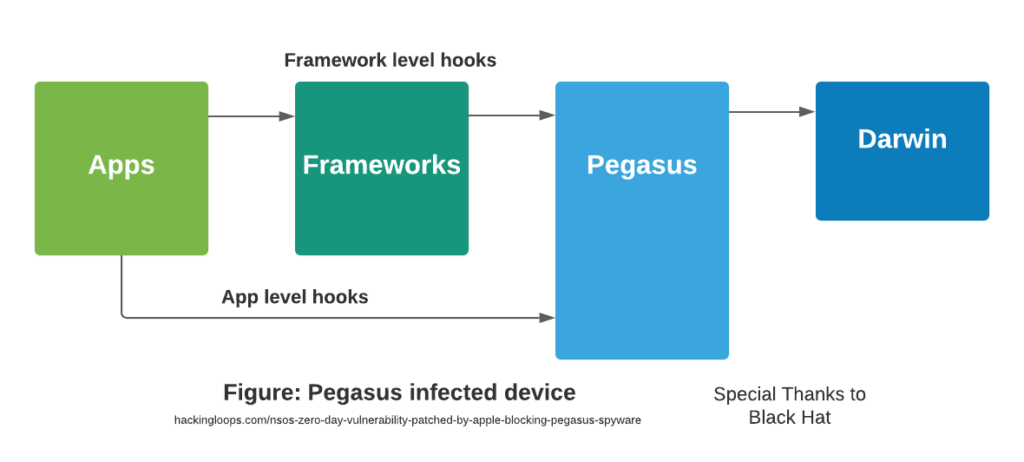
Security features block one app to look at other apps information in a sandbox environment. But with low-level access, Pegasus can jailbreak a device easily, and then it can collect data from apps or take control of lower-level applicants.
What is a Zero-Day Vulnerability?
Apple recently launched iOS 14.8 update to prevent zero-day vulnerability. The zero-day vulnerability is a flaw itself that carries unknown timing even for the developers. Software and hardware component can suffer from complicated problems concerning privacy without any noticeable difference.
In a zero-day vulnerability, developers have less time to react as the flaw took its jab, and it’s a race against time. Attackers release malware/spyware before a developer gets the chance to fix the issue or develop a patch, which is known as a “zero-day” vulnerability.
Citizen Lab experiments on security topics such as malware or spyware, and it came to their attention that the spyware can jailbreak iOS devices without a user touching the screen. Cyber threats such as spam, keylogging or hacking, occurs when users click on untrusted links unconsciously. But today, technology is so advanced that it doesn’t require user input or clicks; if the attacker knows the phone number, a text message is all it takes to get hacked.
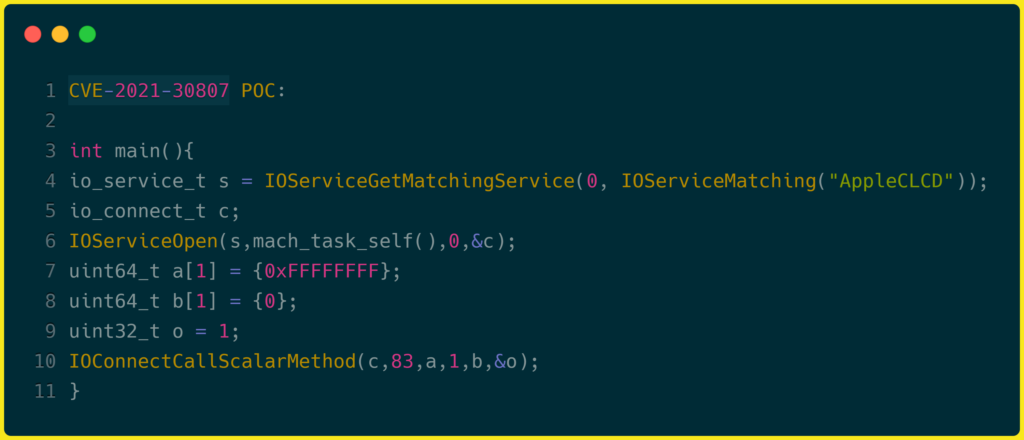
Among four in-the-wild zero-days iOS vulnerabilities, three are CVE-2021-21166 and CVE-2021-30551 in Google Chrome, CVE-2021-33742 in Internet explorer. And CVE-2021-30807 as follows:
Pegasus and its methodology
Pegasus is an espionage spyware software released by the NSO Group. The spyware is so powerful that it can remotely jailbreak any iOS device, read text messages, transmit media files, turn on camera and microphone to record audio, and get visual data simultaneously. It is developed to help government agencies track and spying on terrorists, detecting drug trafficking rings, helping children, etc. The spyware is pretty costly to acquire and only available for high authorities like a government. But recently it’s been found that worldwide journalists, many personals in the UAE, India, US and even President of France got affected by it. Guess what kind of damage it can cause as higher officials access national and even global trade secrets and military intelligence.
Pegasus uses three attacks in a chain which is called “Trident”. There is also a three-step process of how the spyware works. The stages begin after sending a spear-phishing “Single-use” link to the victim’s device, either clickable or non-required.
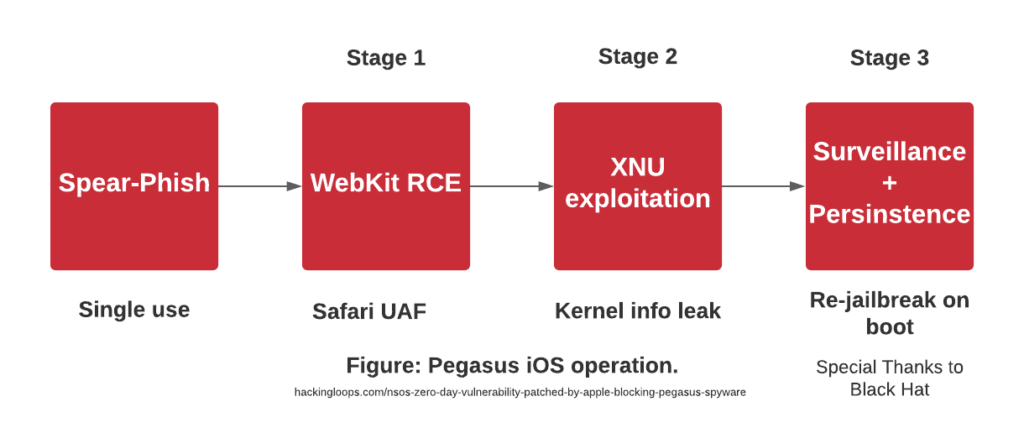
Firstly, WebKit RCE takes action on iOS. e.g., Safari UAF.
The second stage is interacting with information on the kernel level with XNU exploitation; in more straightforward terms, “jailbreaking” occurs.
Thirdly, surveillance and jailbreak occur again when the device reboots; scripts attach hooks and sync with the C&C server. Continuous sync of connectivity takes place whenever the attacker schedules to listen to the victim device or grab data.
“Hooks” can be installed on a jailbroken iOS device, and to install “hooks”, Cydia Substrate is used for injecting dynamic libraries in application or Cynject into the running process to collect live data. E.g., WhatsApp, Viber, Facebook, iMessage, and such application modules are injected with dynamic libraries to collect data.
A deep dive into the spyware
Pegasus spyware utilizes kernel level information for jailbreaking iOS devices and listens to applications in a sandbox. Earlier times, there was an option for remote jailbreaking just by visiting a website. Apple fixed the vulnerability, and it came from the same inspiration. CVE-2016-4655 is a vulnerbilt8iy that Infoleak used to acquire the kernel’s base address and bypass KASLR. It even checks OSUnserializeBinary methods along with bounds check for OSNumber and high bits number.
“is_io_registery_entry_get_property_bytes” triggers the script from sandbox where our culprit can stick to the registry and transmit data. The attacker sends a payload with a link, and once the link is visited, it takes the victim nowhere, and as the payload is dumped, the link is dead. Still, some are instructed to redirect the user to their geographical location of Google search or any other irreverent website.
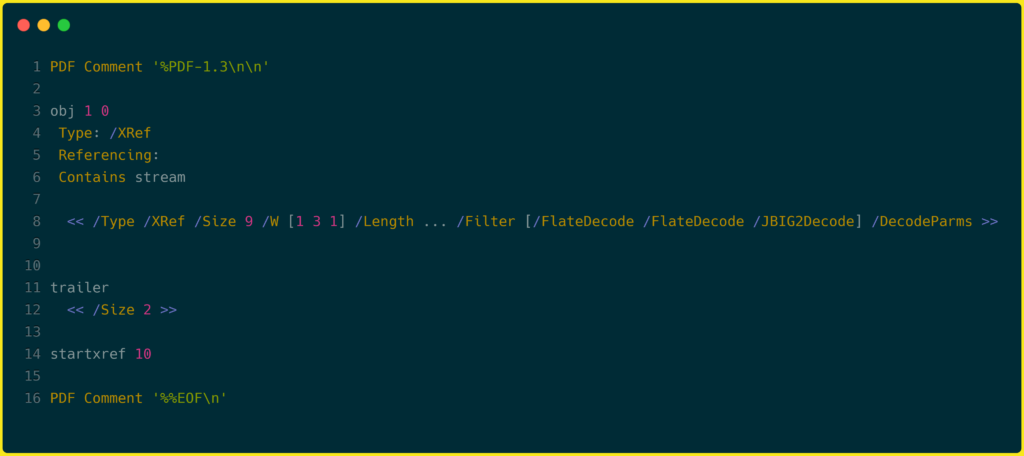
The payload consists of JavaScript and Objective-C code, and for each payload, encryption keys are different. The spyware components are hidden, like the system applications and services. We’ve seen applications that use dependency, which is not directly usable as an individual app but acts as a supporting role. In this case, the spyware follows the same method but in a deadlier way.
Payload files found:
- Files with “.gif” extension (27 copies)
- Adobe PDF files “.gif” extension (4 files, 34-character for two files, 97-character names for rest)
- pdfid tool of “.gif” extension (4 files)
One of the ways the spyware stays undetected is, it blocks the latest or upcoming software updates. Software updates come with security patches, performance tweaks and other improvements. Once the update is blocked, the exploited device remains in the same state. The spyware can also clear Mobile Safari history and cache so that even if a user is suspicious of what they click, there is no trace of it within the browser module.
The spyware uses SIP for remote server communication with the host and removes itself via self-destruct mechanisms. So even if it is possible to examine a device for traces, source data is removed along with encryption keys which makes tracking harder.
One of the fascinating features we found of the spyware is that it carries a check-in system. This again surprises us with how far technology has come. Suppose there is a problem with communication via SIP, server sync, or other functionalities. In that case, chances are the spyware is detected or being examined, and even it may not be the case, the Trident self-destructs. It prevents forensics from finding out details on the issue.
Citizen Lab calls the ForecedEntry “CASCADEFAIL” cause only a tiny portion of tracing is found as files self-destruct.
Latest findings
Citizen Lab and many other cybersecurity teams do extensive research on malware, spyware, and hacking-cracking tools similarly. They declared the ForecedEntry exploit on iPhone happened many times.
Forensic teams found traces of Pegasus on Saudi Journalists and activists worldwide, and it is a matter of concern. After analyzing the phone of a Saudi activist who was infected with Pegasus, Citizen Lab discovered a zero-day-zero-click exploit against iMessage via ForecedEntry. It is tough to push updates frequently without breaking the system or causing trouble in the existing environment.
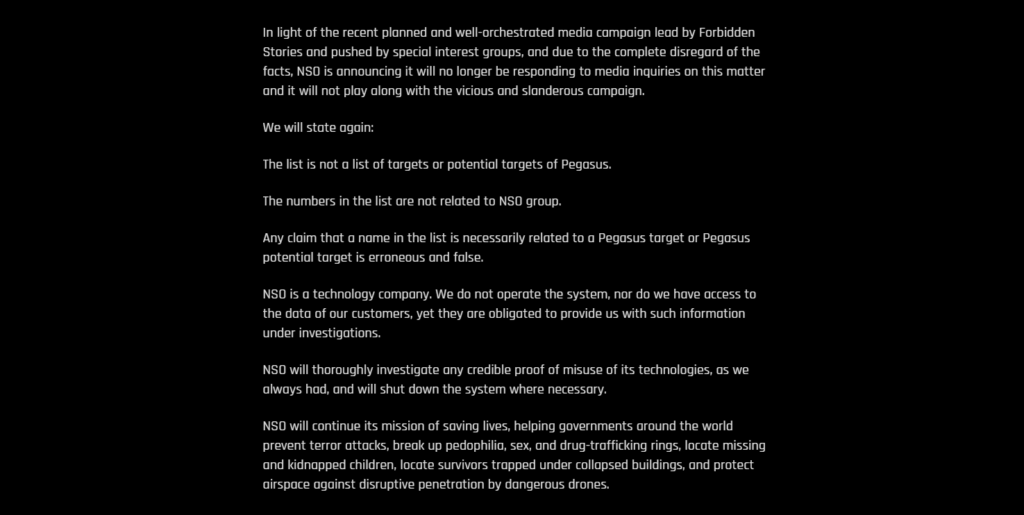
Every encrypted key differs from the source pushed with the payload, and it is hard to block such a system permanently. Though the Israeli NSO group often declined that the spyware they sell is only to authorized entities for helping the government, seeing this happening at such a scale, we are unsure of the legal consequences. NSO Group recently said:
Vulnerability CVE-2021-30860 describing as “processing a maliciously crafted PDF that may lead to arbitrary code execution.”
The binary or running applicants hide as system services, and to anyone who takes a high interest in these services, there is a high chance that even they can’t identify it from regular services.
There are many techniques to gather data via Pegasus spyware:
- Remotely access microphone, listen and record data.
- Remotely record video from the camera.
- Mobile data, sim card and network information.
- GPS location.
- Wi-Fi or router password gathering via keychain.
- Remotely access files in the device.
- Real-time surveillance.
A briefing by Apple’s head of security engineering and architecture by Ivan Krstić confirmed the fix “after identifying the vulnerability used by this exploit for iMessage, Apple rapidly developed and deployed a fix in iOS 14.8 to protect our users.”
His comment on the spyware “Attacks like the ones described are highly sophisticated, cost millions of dollars to develop, often have a short shelf life, and are used to target specific individuals.”
Summary
As the exploit is notoriously dangerous, keeping the devices updated to the latest version is recommended. Saar tweeted that one of the vulnerabilities was discovered in March, which is four months old. Apple failed to disclose information to the public or concerned entities in time, so the news exploded. He found a memory corruption issue in the IOMobileFrameBuffer, a kernel extension to manage screen frame buffer.
Citizen Lab calls it “despotism-as-a-service” on the latest findings. Apple released their 13th update this year alone to fix iOS and macOS zero-day vulnerabilities.
Google’s Project Zero vulnerability research came across seven zero-days for Apple and three among them are new. In 2021, 22 zero-days were discovered, almost 33% of them targets iOS, followed by the most threatened zero-day target, Chrome. App Tracking Transparency (ATT) future bug patches along with vulnerability blocking updates are on the way.