
Maintaining Access Part 1: Introduction and Metasploit Example
Welcome back my fellow hackers! Today we’re going to be starting the topic of maintaining access. First, we’ll discuss the concept

Welcome back my fellow hackers! Today we’re going to be starting the topic of maintaining access. First, we’ll discuss the concept
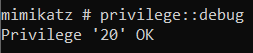
Credential dumping from a compromised target has never been more effortless until the release of the great tool Mimikatz. The

Welcome back my fellow hackers! Today we’re going to be entering some new territory. When we’re attempting to compromise a

Welcome back my fellow hackers! We’ve covered host discovery tactics before; specifically, we’ve covered ping scans and ARP scans. But