
What and who Is a Pentester? Role, Skills, and Career Path
In conversations regarding network or infrastructural security, the word “pentester” often pops up. But who really is a pentester, and

In conversations regarding network or infrastructural security, the word “pentester” often pops up. But who really is a pentester, and
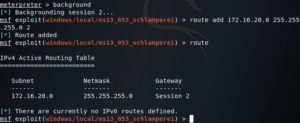
Today we’re going to be going over something I’ve been working on for a while, pivoting. First, we’ll discuss what

Let’s be honest — the Linux terminal can feel intimidating at first. It’s that mysterious black window filled with commands
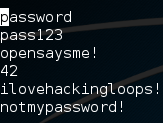
Welcome back my fellow hackers! Today we’re going to discuss the concept of brute force attacks by building our very